当前位置:网站首页>Why is your money transferred? This article tells you the answer
Why is your money transferred? This article tells you the answer
2020-11-09 14:35:00 【Yijing Technology】
The content of this article is , Mainly about CSRF.
01 What is? CSRF?
CSRF, Full name Cross-site request forgery, Translation is cross site request forgery , It refers to the use of the identity authentication information of the victim that has not been invalidated (cookie、 Conversation, etc ), Trick them to click malicious links or visit the page containing the attack code , To... As a victim without the victim's knowledge ( The identity authentication information corresponds to ) The server sends the request , So as to complete the illegal operation ( Such as transfers 、 Change the secret, etc ).
CSRF The attack principle is as follows :
■ The user opens the browser , Access to login trusted A Website
■ After the user information has been verified , The server will return a cookie To the browser , Users log on to the website A success , Can send request to website normally A
■ The user did not exit the website A, In the same browser , Open a dangerous website B
■ Website B After receiving the user's request , Return some malicious code , And make a request to visit the website A
■ After the browser receives the malicious code , Without the user's knowledge , utilize cookie Information , To the website A Send a malicious request , Website A Will be based on cookie The information processes the request with the user's authority , Lead from website B The malicious code was executed . It's too official , Simply put, it's through construction URL What caused the attack was CSRF, With the target cookie To carry out our attack .
02 Why did your money get transferred ?
Now there are Zhang San and Li Si transferring money .
1、 Zhang San gives Li Si 100 block , The operation to be performed is :
xxx/transfer.php?from= Zhang San &money=100&to= Li Si
Note that Zhang San doesn't close the page .
2、 Hackers want to transfer money to themselves , The operation to be performed is :
xxx/transfer.php?from= Zhang San &money=100&to= hackers
Obviously it will fail , This is because Zhang San will log in to the system through cookie, Put your own session Pass it to the background server . At this point, the system checks the current session Identity in , He turned it down when he found it was incorrect .
3、 Hackers continue to think of ways , Use bad websites to induce :
The links to the website are very colorful , Let Zhang San can't stop , So I click on the induction link A. At this point, the information returned to the hacker is :
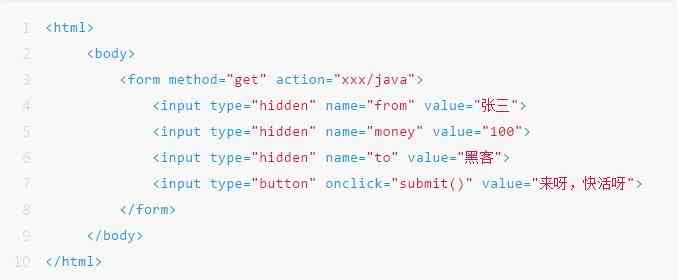
If Zhang Sangang had just transferred money to Li Si , And the page hasn't been closed yet , Just click on this link , The above operation will be performed . This is because the hacker's identity at this time is Zhang San's information , The bank didn't know it was Zhang San , So he accepted the request .
03 How to dig CSRF Loophole
CSRF It is used to operate beyond authority , The vulnerability is in a place where there is permission control , Its structure URL perhaps get Submit , Can be measured .
Black box
Open the page of non static operation , Grab the bag to see if it exists token, without token, Request this page directly , No referer, If the returned data is the same , That means it's very likely that CSRF There's a leak .
White box
Read the code to see if there is validation in the core file token and referer Related code . You can search for token keyword .
Using tools —— Semi automatic detection CSRF
Use CSRFTester course
https://www.sogou.com/link?url=DSOYnZeCC_p8qT7bQ6Ez_IrwkGJvRRLdYQYE4_vHjb03UFOatHCO_d9GQw9zhM_U
Download address :http://www.mediafire.com/file/3j9kbyd3rtardq5/CSRFTester-1.0-src.zip/file
If you're zero based , I want to study systematically and deeply CSRF Loophole , It is highly recommended that you sign up for the training camp specially designed for Xiaobai by Hetian Wangan students ——3 God 《 Compulsory training camp for hackers 》, Limited time benefits for all fans , Only 2 Cents You can sign up for .
The cycle of the training camp is 10 month 21 Japan -10 month 23 On the afternoon of Sunday 3 Point to 4 spot , The teacher will start from 0 The foundation takes you to learn CSRF, Friends can directly scan the code to sign up !

This course offers
▲ The course will be replayed forever , For you to watch over and over again , We can know the new firmly
▲ After class shooting range assignment of supporting courses : The teacher explains the key points of homework regularly 、 difficulty , Make sure the trainees really grasp the knowledge they have learned !
▲ Q & a service , A high quality learning community , Sharing cutting edge knowledge within class groups , Walking with a group of people , You can go further .
Scan the code to get the learning materials and range address
This course is suitable for students who want to learn how to hack , Learning process , Students must not give up , Study on time in three days , At the same time, in the process of learning, we should take notes with pictures and texts , The most important thing is to practice , practice , practice , So after class, the actual combat assignment of the shooting range must be completed on time .
04 Hackers learn to collect exclusive information package
If you have signed up for this course , Want more hacker learning tools and learning materials , Scan the QR code below and send the application screenshot to get .( I hope the students who have received the materials , Can really use the data , Instead of going straight into the cold !)
meanwhile , If you want to see if you're suitable for entry hackers , You can also scan QR code , We have a complete testing system to help you .

Scan code to get learning materials
版权声明
本文为[Yijing Technology]所创,转载请带上原文链接,感谢
边栏推荐
- MES系统在行业应用里区别于传统式管理
- spark学习(二)--作业调度和shuffle解析
- Embedded assembly in IOS
- Idea rest client, yes, I haven't opened postman yet
- c语言(循环链表)实现贪吃蛇的基本功能
- JS判断对象类型方法_typeof怎么用_instanceof怎么用_constructor怎么用_Object.prototype.toString()怎么用
- 解密未来数据库设计:MongoDB新存储引擎WiredTiger实现(事务篇)
- 彩虹排序 | 荷兰旗问题
- 靠“小抄”进字节:拿到这份模板,薪资能翻倍
- 面试了一位33岁Android程序员,只会面向百度编程,居然要25k,被我一顿怼
猜你喜欢

你的钱为什么会被转走,这篇文章告诉你答案

Flink 系例 之 Reduce

iOS中的内嵌汇编

The use of Android studio Aidl

Rongyun has completed several hundred million RMB round D financing, and will continue to build global cloud communication capability

乘风破浪的技术大咖再次集结 | 腾讯云TVP持续航行中

Rainbow sorting | Dutch flag problem
Full link stress testing of moral integrity -- the evolution of corpus intelligence
从汇编的角度看pdb文件

写给我自己的一封信
随机推荐
Rainbow sorting | Dutch flag problem
面试了一位33岁Android程序员,只会面向百度编程,居然要25k,被我一顿怼
Android NDK development and actual combat WeChat official account 2-D code detection
iOS中的内嵌汇编
堆重启_uaf_hacknote
要我说,多线程事务它必须就是个伪命题!
国际顶刊Radiology发表华为云最新联合成果,AI辅助检测脑动脉瘤
除了解析域名,DNS还能干吗?
Do programmers pay too much to work overtime? Should programmer's salary be reduced? Netizen: let go of other hard pressed programmers
Hadoop学习(三)-YARN
spark学习(二)--作业调度和shuffle解析
要我说,多线程事务它必须就是个伪命题!
为什么我强烈建议要定制开发小程序,这些好处你需要了解
「代码整洁之道-程序员的职业素养」读书笔记
大厂面试系列(二):并发编程
导师制Processing网课 双十一优惠进行中
CCF BDCI hot topic: privacy information recognition in unstructured business text information
Hadoop learning (3) - Yarn
岗位内推 | 微软亚洲研究院智能多媒体组招聘计算机视觉算法实习生
JS判断对象类型方法_typeof怎么用_instanceof怎么用_constructor怎么用_Object.prototype.toString()怎么用