当前位置:网站首页>2022 Guangdong provincial competition - code information acquisition and analysis flag
2022 Guangdong provincial competition - code information acquisition and analysis flag
2022-07-04 04:59:00 【Beluga】
Encoding information acquisition
Need data package to be private
1. From the target server FTP Upload and download wire0078.pcap, Analyze the file , Find out the area where the key information belongs , Use the area name as Flag Submit .
First look at the target ftp What's up
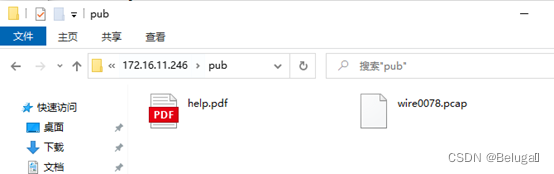
One packet and one help.pdf, Both come down
First look at the packet

a pile USB Data flow , You can't do it without help , Open up decisively help

Open this thing and find it is USB Description document , But so many pages , One by one, it is certain that the game is over
the reason being that USB, The most important thing is the mouse and keyboard , It must be possible to analyze the keyboard ( Because lose flag You can't rely on the mouse ), Search the keyboard directly (keyboard)

In the 17 Corresponding columns were found in search terms , Then follow the data packets one by one
The first question of the topic is the area of key information , The answer is wireshark Key information areas

Flag:Leftover Capture Data
2. Analyze the file , Find out the key information , Take the effective packet length as Flag Submit .

This is the blue one , length 8 Bytes
Flag:8
3. Analyze the file , Find out the key information , Will be the first 5 The key part of the effective information is 16 Hexadecimal value as Flag Submit .
Attention is valid information , Data packets here are all 0 It's time to release the key , It's invalid , Pay attention to finding the right one is not all about 0 My bag

So it's actually the first 10 individual ( Ahead 20 At the beginning, press shift)
Flag:0x2F Pay attention to capitalization F
4. Analyze the file , Find out the key information , Will be the first 10 The key part of the effective information is 16 Hexadecimal value as Flag Submit .
Same as the last question , It's No 21 A package
Flag:0x22
5. Analyze the file , Find out the key information , Will find the Flag Worth submitting .
Combine the characters of each package into flag The answer is right
Flag:pr355_0nwards_a2fee6e0
边栏推荐
猜你喜欢
Niuke Xiaobai monthly race 49

Simple g++ and GDB debugging

Unity 接入天气系统

Maui introductory tutorial series (5.xaml and page introduction)
Zhongke panyun-d module analysis and scoring standard
附件六:防守工作簡報.docx

Technology Management - learning / practice

Beipiao programmer, 20K monthly salary, 15W a year, normal?

STM32F1与STM32CubeIDE编程实例-74HC595驱动4位7段数码管

每日刷题记录 (十二)
随机推荐
VSCode的有用插件
Introduction and application of rampax in unity: optimization of dissolution effect
LeetCode136+128+152+148
中科磐云—模块A 基础设施设置与安全加固 评分标准
网络设备应急响应指南
How do good test / development programmers practice? Where to go
Rollup各组件作用
《Cross-view Transformers for real-time Map-view Semantic Segmentation》论文笔记
【MATLAB】通信信号调制通用函数 — 傅里叶逆变换
PostgreSQL 正式超越 MySQL,这家伙也太强了吧!
【MATLAB】MATLAB 仿真数字带通传输系统 — ASK、 PSK、 FSK 系统
【MATLAB】通信信号调制通用函数 — 低通滤波器
Zhongke Panyun - 2022 Guangxi reverse analysis ideas
Flutter 调用高德地图APP实现位置搜索、路线规划、逆地理编码
由于使用flash存放参数时,擦除掉了flash的代码区导致进入硬件错误中断
【MATLAB】MATLAB 仿真 — 低通高斯白噪声
Acwing game 58
记几个智能手表相关芯片 蓝牙芯片 低功耗
海力士EMMC5.0及5.1系列对比详解
laravel 中获取刚刚插入的记录的id