当前位置:网站首页>Step by step how to perform data risk assessment
Step by step how to perform data risk assessment
2022-08-05 02:48:00 【software testnet】

Every business needs to protect the security and privacy of its sensitive data,以避免数据泄露、Intellectual property theft and others may result in fines、Litigation and business failure.
What is data risk assessment,为什么它很重要?
A data risk assessment is a review of how a business protects its sensitive data and what improvements might be needed.
Businesses should regularly perform data risk assessments,as a form of auditing,Can help identify information security and privacy control deficiencies and reduce risk.在数据泄露(无论是有意还是无意)之后,A data risk assessment needs to be performed,to improve control and reduce the likelihood of similar leaks in the future.
Perform data risk assessments5个步骤
The following five steps can be used to create a comprehensive data risk assessment.
(1)存储敏感数据
检查端点、云计算服务、storage media and other locations,to find and log all instances of sensitive data.The data list should include any characteristics that may affect risk requirements.例如,The geographic location where data is stored affects applicable laws and regulations.
Determine who is responsible for each instance of sensitive data,so that you can interact with them when necessary.
(2)Assign a data classification to each data instance
Organizations should define data classifications for all sensitive data,例如“受保护的健康信息”和“个人身份信息”.These definitions should indicate that for each sensitive data type,Which security and privacy controls are mandatory and recommended.
Even if the data is already classified,Also recheck regularly.The nature of data changes over time,And there may be new classifications that apply to related data.
(3)Prioritize which sensitive data to evaluate
Businesses may have large amounts of sensitive data,So much so that it is not feasible to review all the data during each assessment.如有必要,The most sensitive data needs to be prioritized、The most demanding data or the longest unassessed data.
(4)Check all relevant security and privacy controls
Auditing protects sensitive data usage、Storage and Transfer Controls.Its common audit steps include:
·Validate the principle of least privilege.Confirm that there are only necessary human and non-human users、服务、Administrators and Third Parties(For example business partners、contractors and suppliers)to access sensitive data,And they only have some necessary access rights,例如只读、读写等.
- Ensure that all policies restricting data access are actively enforced.例如,Businesses may restrict access to certain sensitive data based on the following factors:
- 用户的位置
- 数据的位置
- 其他时间
- 一周中的某一天
- The user's device type
- Make sure all other necessary security and privacy controls are in use.Common tools to reduce risk include:
- Data loss prevention software
- 防火墙
- 加密
- 多因素身份验证
- 用户和实体行为分析.Identify data retention violations.Determine if there is any data that should be destroyed to comply with the data retention policy.
(5)Document all security and privacy control deficiencies
While identifying security and privacy flaws falls within the scope of a data risk assessment,But fixing them falls outside the scope.It is reasonable for the assessment to include the following:
- The relative priority of each defect.
- A recommended course of action to address each deficiency.
These recommendations provide a roadmap for better data security.Risk matrices can be based on the severity and likelihood of occurrence of potential consequences,Help find and prioritize issues.
How to use data risk assessment results
Business leaders should develop strategies,to mitigate security and privacy flaws identified in data risk assessments,Also consider remediation recommendations and prioritize high-risk issues.
最终,The output of the data risk assessment should be the main input to the enterprise risk management and mitigation plan,Helps make smarter decisions,This helps to improve data protection.
边栏推荐
- 使用二维码传输文件的小工具 - QFileTrans 1.2.0.1
- 语法基础(变量、输入输出、表达式与顺序语句)
- 【Daily Training】1403. Minimum Subsequence in Non-Increasing Order
- Note that Weifang generally needs to pay attention to issuing invoices
- Likou - preorder traversal, inorder traversal, postorder traversal of binary tree
- Is your data safe in this hyperconnected world?
- The usage of try...catch and finally in js
- ARM Mailbox
- 倒计时 2 天|云原生 Meetup 广州站,等你来!
- QT MV\MVC结构
猜你喜欢
链表的简单描述及代码的简单实现

The 20th day of the special assault version of the sword offer
View handler stepping record
QT语言文件制作
【 2 】 OpenCV image processing: basic knowledge of OpenCV

Regular expression to match a certain string in the middle

Quickly learn chess from zero to one
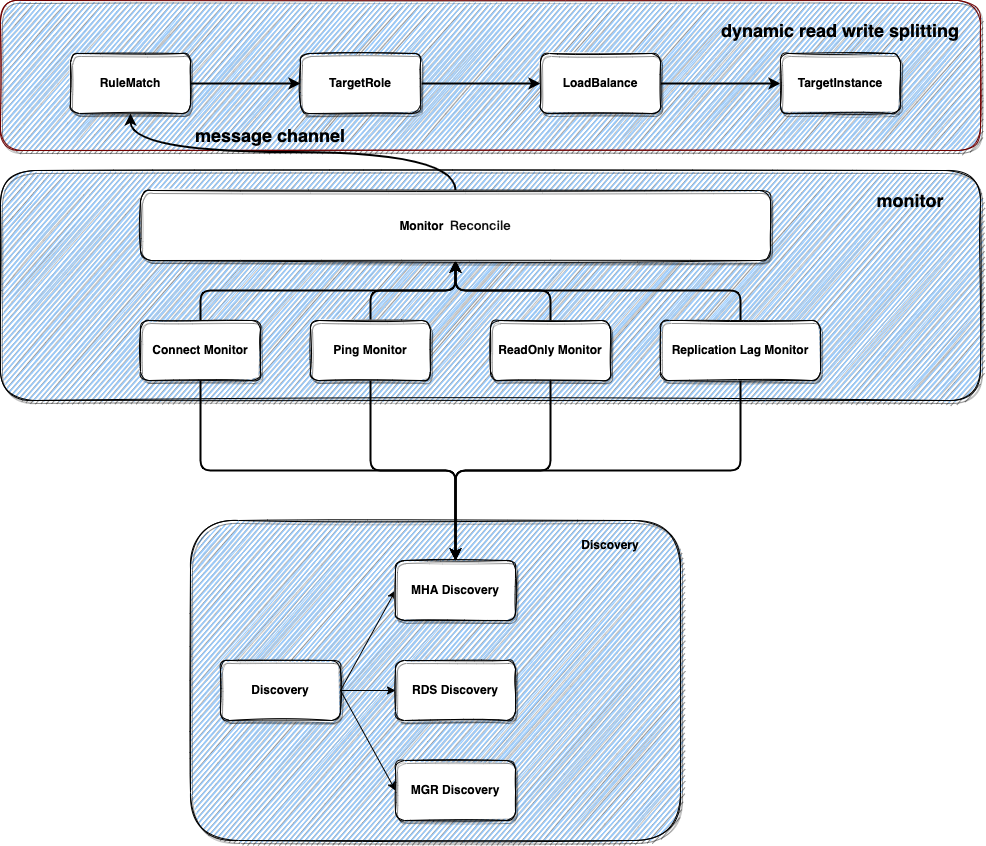
Pisanix v0.2.0 released | Added support for dynamic read-write separation
The Tanabata copywriting you want has been sorted out for you!
甘特图来啦,项目管理神器,模板直接用
随机推荐
Data to enhance Mixup principle and code reading
云原生(三十二) | Kubernetes篇之平台存储系统介绍
Cloud Native (32) | Introduction to Platform Storage System in Kubernetes
虚拟内存原理与技术
The usage of try...catch and finally in js
2022-08-04: Input: deduplicated array arr, the numbers in it only contain 0~9.limit, a number.Return: The maximum number that can be spelled out with arr if the requirement is smaller than limit.from
C language diary 9 3 kinds of statements of if
CPDA|How Operators Learn Data Analysis (SQL) from Negative Foundations
Syntax basics (variables, input and output, expressions and sequential statement completion)
Likou - preorder traversal, inorder traversal, postorder traversal of binary tree
The design idea of DMicro, the Go microservice development framework
正则表达式,匹配中间的某一段字符串
tree table lookup
数据增强Mixup原理与代码解读
Semi-Decentralized Federated Learning for Cooperative D2D Local Model Aggregation
22-07-31周总结
程序员的七夕浪漫时刻
(11) Metaclass
C student management system Insert the student node at the specified location
What should I do if the self-incrementing id of online MySQL is exhausted?