当前位置:网站首页>STM8S-----option byte
STM8S-----option byte
2022-08-04 02:34:00 【kick the player】
Option Byte ( O p t i o n B y t e )
The configuration word of the STM8S is similar to the Fuse bit of the AVR.It is used to configure the port's multiplexing function and read protection and other operations.Different from the fuse bit of AVR, the clock configuration of STM8S is not in Option Byte, and there will be no embarrassment that the chip is directly locked after writing STM8S.Option bytes are used to configure hardware features and memory protection status and are located in a specific memory array on the same page
.The option byte can be modified in ICP / SW IM mode or in I AP mode, that is, the configuration word can be written through STlink, or the option word can be written through the program
When the second function of the port needs to be enabled, it needs to be consideredOption byte programming, otherwise it will not be able to achieve the desired function of the program
For example: S TM8S has a buzzer controller B E E P, the corresponding port of this B E E P is PD 4. But PD 4 has two multiplexing functions, it can be
1.AFR7 = 1, BEEP buzzer output
2.AFR7 = 0, Tim2 compare output 1 is Tim2_CC1
Users must choose one of these two functions, only one.So how do you make PD 4 a B E E P output?The answer is to configure AF R 7 as 1 by setting the Opt ion by t e
option word, and use PD 4 to output the signal of BEE P, otherwise, PD 4 will output the signal of Tim 2 _ C C 1.
Of course, with any configuration, users can still use PD 4 like normal IO.
Optio n Byte In addition to being able to configure the multiplexing function of the port, it can also set the chip's read protection when the ROP byte in the option byte is programmed as '0 x AA'.In this case, regardless of whether the write protection is in effect, reading or modifying the FLASH program memory and DATA area in ICP mode (using the SWIM interface) is prohibited.Even if no protection is considered completely unbreakable, the STM8's read-protect feature provides a very high level of protection for a general-purpose microprocessor.That is to say, the way to prevent others from copying your program can be to program the ROP byte to enable read protection, then the other party cannot read your Flash data from STM8 no matter what
边栏推荐
- Example: 036 is a prime number
- 什么是SVN(Subversion)?
- Example 035: Setting the output color
- 2022广东省安全员A证第三批(主要负责人)考试题库及模拟考试
- Flink原理流程图简单记录
- html select tag assignment database query result
- The browser
- Zabbix set up email alert + enterprise WeChat alert
- Priority_queue element as a pointer, the overloaded operators
- priority_queue元素为指针时,重载运算符失效
猜你喜欢
Snake game bug analysis and function expansion
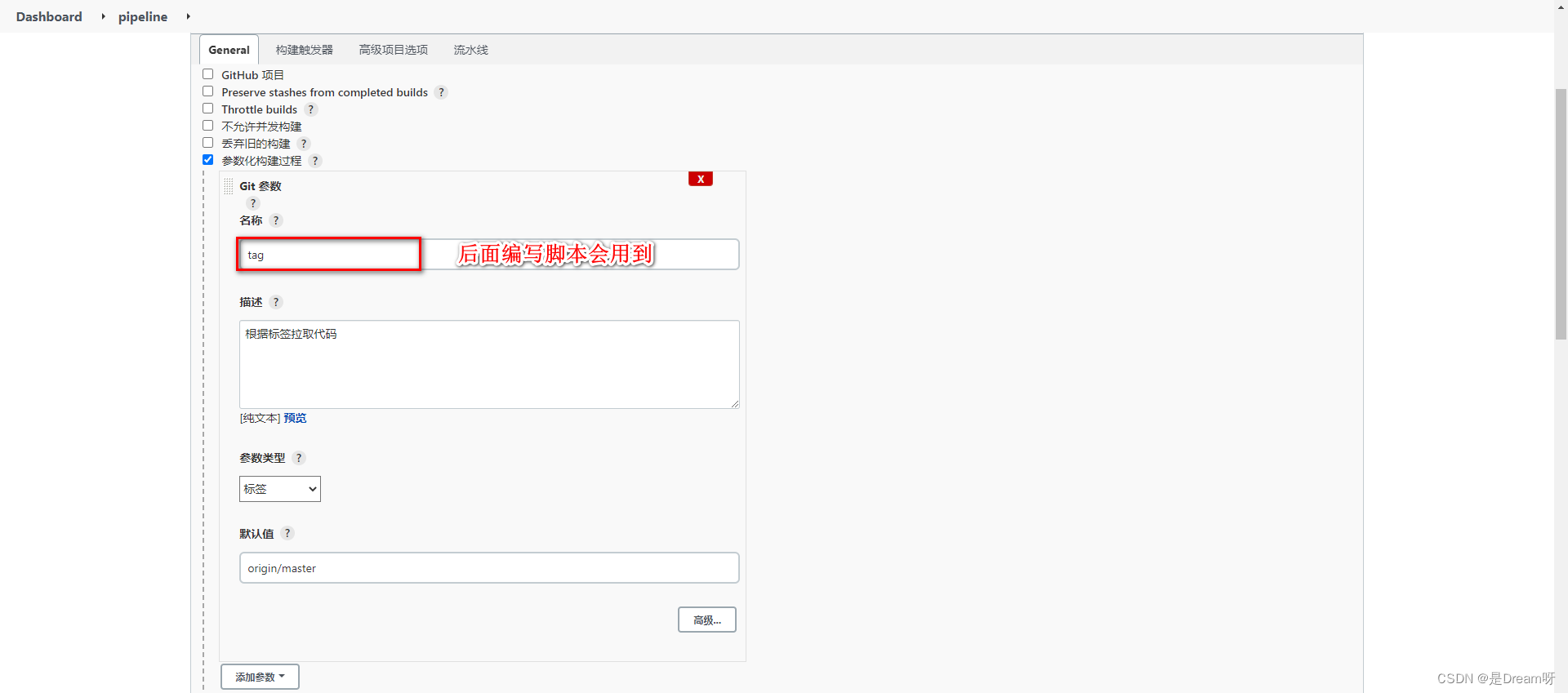
【云原生】DevOps(六):Jenkins流水线
cdh6.x 集成spark-sql
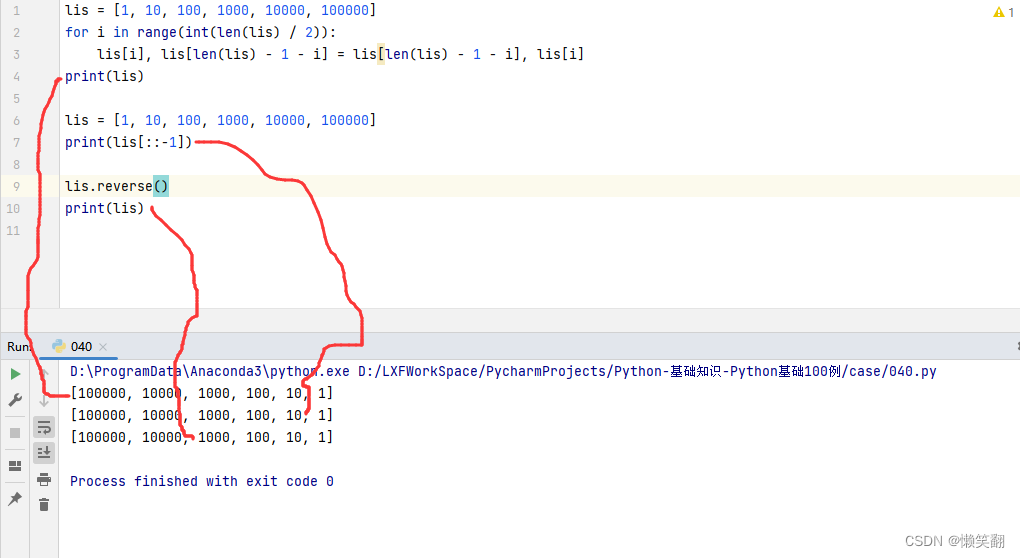
实例040:逆序列表
架构实战营模块三作业

Example 040: Reverse List
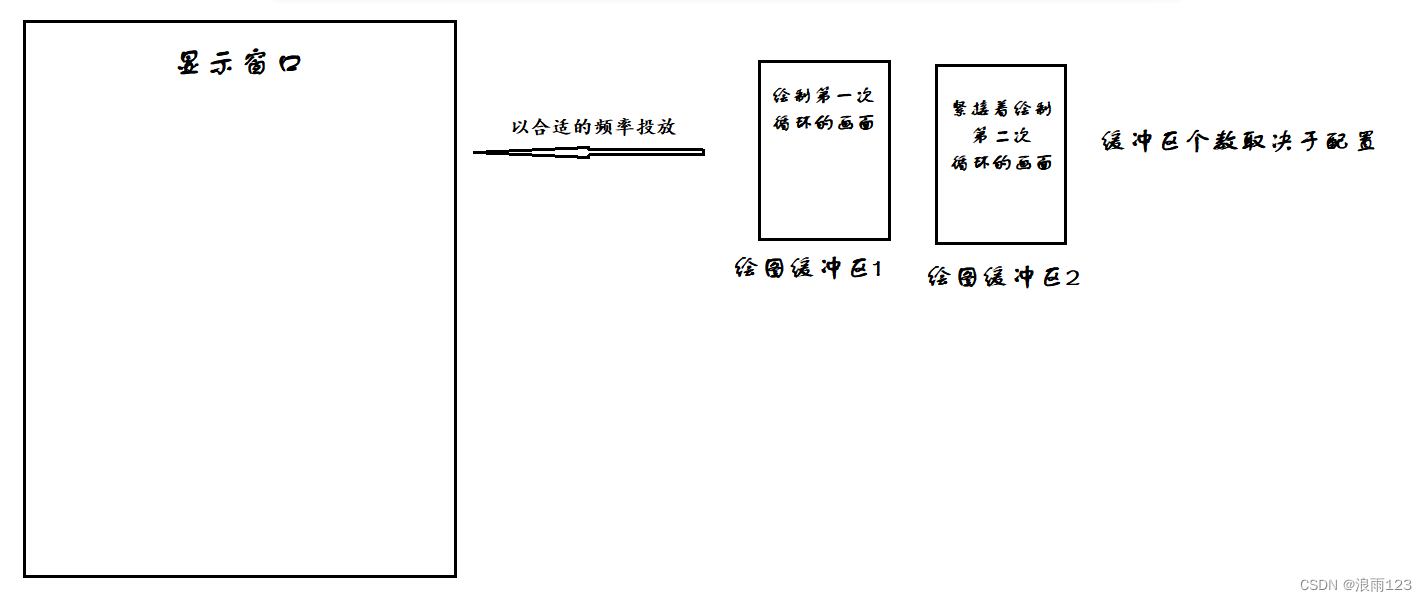
C语言--环形缓存区
Flask框架初学-05-命令管理Manager及数据库的使用
mpf5_定价Bond_yield curve_Spot coupon_duration_有效利率_连续复利_远期_Vasicek短期_CIR模型Derivatives_Tridiagonal_ppf

Continuing to invest in product research and development, Dingdong Maicai wins in supply chain investment
随机推荐
【云原生】DevOps(六):Jenkins流水线
There are n steps in total, and you can go up to 1 or 2 steps each time. How many ways are there?
Continuing to invest in product research and development, Dingdong Maicai wins in supply chain investment
深度学习(三)分类 理论部分
STM32-遥感数据处理
【原创】启动Win10自带的XPS/OXPS阅读器
What is the source of flinkcdc consuming mysql binlog data without sqltype=delete
Zabbix设置邮件告警+企业微信告警
Parquet encoding
Variable string
香港服务器有哪些常用的型号
The idea of the diagram
esp8266-01s刷固件步骤
LeetCode:899. 有序队列【思维题】
C program compilation and predefined detailed explanation
Simple sorting (summer vacation daily question 14)
如何读取 resources 目录下的文件路径?
FileNotFoundException: This file can not be opened as a file descriptor; it is probably compressed
DDTL: Domain Transfer Learning at a Distance
Download install and create/run project for HBuilderX