当前位置:网站首页>[chaosblade: delete pod according to the tag, pod domain name access exception scenario, pod file system i/o failure scenario]
[chaosblade: delete pod according to the tag, pod domain name access exception scenario, pod file system i/o failure scenario]
2022-07-07 08:59:00 【Fairy Xiao Xiaole】
Delete according to label POD
The goal is : stay chaosblade In the namespace , Yes redis-master-68857cd57c-dzbs9 Pod The local 6379
Port add 3000 Millisecond access delay , The delay time fluctuates up and down 1000 millisecond .
delay_pod_network_by_names.yaml Content :
apiVersion: chaosblade.io/v1alpha1
kind: ChaosBlade
metadata:
name: delay-pod-network-by-names
spec:
experiments:
- scope: pod
target: network
action: delay
desc: "delay pod network by names"
matchers:
- name: names
value:
- "redis-master-68857cd57c-dzbs9"
- name: namespace
value:
- "chaosblade"
- name: local-port
value: ["6379"]
- name: interface
value: ["eth0"]
- name: time
value: ["3000"]
- name: offset
value: ["1000"]
obtain Pod name
$ kubectl get pod -l app=redis,role=master -o jsonpath={
.items..metadata.name}
modify delay_pod_network_by_names.yaml Medium name Value of field .
Start simulation :
$ kubectl apply -f delay_pod_network_by_names.yaml
View simulation configuration details
kubectl get blade delay-pod-network-by-names -o yaml
Observations : You can see the visit experiment pod 6379 The delay of the port is 3s about , Results in line with expectations .
# Get the experiment pod ip
$ kubectl get pod -l app=redis,role=master -o jsonpath={
.items..status.podIP}
10.42.69.44
# Entry observation pod
$ kubectl exec -it redis-slave-6dd975d4c8-2zrkb bash
# stay pod Install in telnet
$ apt-get update && apt-get install -y telnet
# Test time
$ time echo "" | telnet 10.42.69.44 6379
Trying 10.42.69.44...
Connected to 10.42.69.44.
Escape character is '^]'.
Connection closed by foreign host.
real 0m3.790s
user 0m0.007s
sys 0m0.001s
Stop the experiment
Carry out orders :kubectl delete -f delay_pod_network_by_names.yaml
Or delete blade resources :kubectl delete blade delay-pod-network-by-names
Pod Domain name access exception scenario
The goal is :Pod Exception in accessing the specified domain name .
obtain pod The content of the name is the same as .
dns_pod_network_by_names.yaml Content :
apiVersion: chaosblade.io/v1alpha1
kind: ChaosBlade
metadata:
name: dns-pod-network-by-names
spec:
experiments:
- scope: pod
target: network
action: dns
desc: "dns pod network by names"
matchers:
- name: names
value:
- "redis-slave-6dd975d4c8-lm8jz"
- name: namespace
value:
- "chaosblade"
- name: domain
value: ["www.baidu.com"]
- name: ip
value: ["10.0.0.1"]
Carry out orders
$ kubectl apply -f dns_pod_network_by_names.yaml
Check the experiment status
perform kubectl get blade dns-pod-network-by-names -o json command , Check the experiment status .
Observations
# Enter the experiment pod
$ kubectl exec -it redis-slave-6dd975d4c8-lm8jz bash
# Ping www.baidu.com
$ ping www.baidu.com
# No response
You can see that you can access the specified domain name www.baidu.com abnormal , Results in line with expectations .
Stop the experiment
Carry out orders :kubectl delete -f dns_pod_network_by_names.yaml
Or delete blade resources :kubectl delete blade dns-pod-network-by-names
Pod file system I/O Failure scenario
The goal is : to kubernetes Of pod Inject file system I/O fault .
Be careful : This scenario needs to be activated --webhook-enable Parameters , To use this function , Please be there. chaosblade-operator Add... To the parameter
–webhook-enable, Or specify : for example helm Add... During installation --set webhook.enable=true Appoint .
Prerequisite
Deployed in the cluster chaosblade-admission-webhook• Need to inject fault volume Set up
mountPropagation by HostToContainer•pod The following is added above annotations:chaosblade/inject-volume: “data” // Need to inject fault volume name
chaosblade/inject-volume-subpath: “conf” //volume Mounted subdirectories
The deployment of test pod
chaosblade webhook Will be based on pod Of annotation, Inject fuse Of sidecar Containers :
1.chaosblade/inject-volume Indicate the fault that needs to be injected volume name, For example, in the example data.2.chaosblade/inject-volume-subpath To specify volume
Subdirectory of the mount path . In the example above ,volume The mount path of is /data, The subdirectory is conf, It's in pod Inside , Inject I/O The exception directory is
/data/conf.3. Specify the fault that needs to be injected volume You need to specify the
mountPropagation:HostToContainer, The meaning of this field can be referred to the official documents Volumes[3].
# The deployment of test pod
$ kubectl apply -f io-test-pod.yaml
# see sidecar Whether the injection is successful
$ kubectl get pod test-7c9fc6fd88-7lx6b -n chaosblade
NAME READY STATUS RESTARTS AGE
test-7c9fc6fd88-7lx6b 2/2 Running 0 4m8s
pod_io.yaml Content :
apiVersion: chaosblade.io/v1alpha1
kind: ChaosBlade
metadata:
name: inject-pod-by-labels
spec:
experiments:
- scope: pod
target: pod
action: IO
desc: "Pod IO Exception by labels"
matchers:
- name: labels
value:
- "app=test"
- name: namespace
value:
- "chaosblade"
- name: method
value:
- "read"
- name: delay
value:
- "1000"
- name: path
value:
- ""
- name: percent
value:
- "60"
- name: errno
value:
- "28"
Carry out orders
$ kubectl apply -f pod_io.yaml
Check the experiment status
perform kubectl get blade inject-pod-by-labels -o json command , Check the experiment status
Observations
# Enter the experiment pod
$ kubectl exec -it test-7c9fc6fd88-7lx6b bash
# stay pod Read the files in the specified directory , If not, you can create a new
$ time cat /data/conf/test.yaml
cat: read error: No space left on device
real 0m3.007s
user 0m0.002s
sys 0m0.002s
# Because there's a problem , Show that 3s Delay of
# Because it's set up 60% It's abnormal , There are still successes
$ time cat /data/conf/test.yaml
123
real 0m0.004s
user 0m0.002s
sys 0m0.000s
File read exception , Results in line with expectations .
In this case , We are right. read The operation injects two exceptions , The abnormal rate is percent 60:
Yes read Operation increased 1s Delay of .• Yes read The operation returned an error 28.
Here is only one type of experiment , See official documents for more types of experiments [4].
Stop the experiment
Carry out orders :kubectl delete -f pod_io.yaml
Or delete blade resources :kubectl delete blade inject-pod-by-labels
Delete the test pod:kubectl delete -f io-test-pod.yaml
边栏推荐
- Screen automatically generates database documents
- C language for calculating the product of two matrices
- Shell script for changing the current folder and the file date under the folder
- Why choose cloud native database
- Simulation volume leetcode [general] 1706 Where does the ball meet
- selenium自动化集成,八年测试经验软测工程师,一篇文章带你学懂
- 模拟卷Leetcode【普通】1567. 乘积为正数的最长子数组长度
- 2022-07-06 Unity核心9——3D动画
- Output all composite numbers between 6 and 1000
- Personal deduction topic classification record
猜你喜欢
Greenplum6.x搭建_环境配置

LeetCode 736. Lisp 语法解析
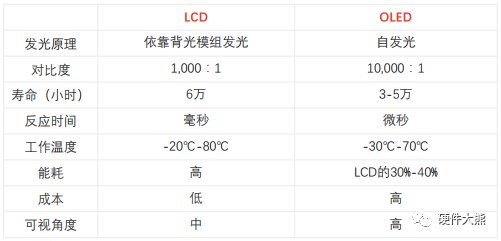
面板显示技术:LCD与OLED
Explain Huawei's application market in detail, and gradually reduce 32-bit package applications and strategies in 2022

Expérience de port série - simple réception et réception de données
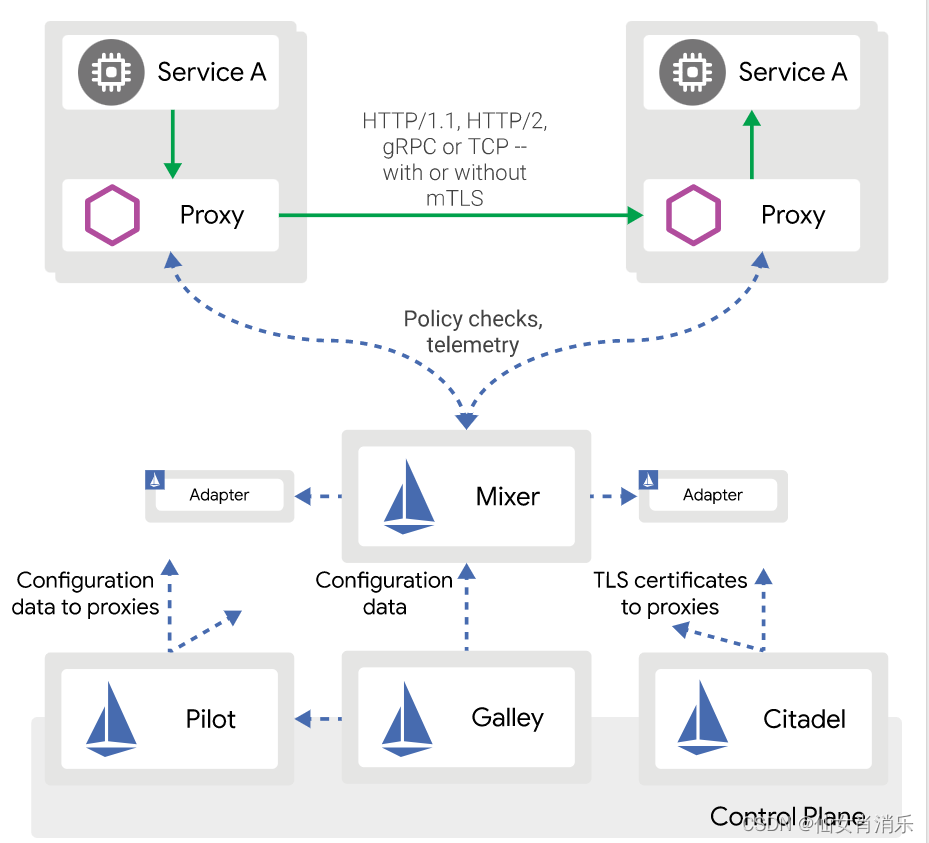
【istio简介、架构、组件】
Screen automatically generates database documents

LeetCode 715. Range 模块

硬核分享:硬件工程师常用工具包
2022-07-06 unity core 9 - 3D animation
随机推荐
数字三角形模型 AcWing 275. 传纸条
Common operating commands of Linux
端口复用和重映像
Esp32-ulp coprocessor low power mode RTC GPIO interrupt wake up
cmake命令行使用
Simulation volume leetcode [general] 1557 The minimum number of points that can reach all points
NCS Chengdu Xindian interview experience
Count the number of words C language
模拟卷Leetcode【普通】1609. 奇偶树
OpenGL 3D graphics rendering
Panel display technology: LCD and OLED
Interpretation of MySQL optimization principle
let const
RuntimeError: Calculated padded input size per channel: (1 x 1). Kernel size: (5 x 5). Kernel size c
Several common database connection methods
Synchronized underlying principle, volatile keyword analysis
求有符号数的原码、反码和补码【C语言】
ESP32-ULP协处理器低功耗模式RTC GPIO中断唤醒
Pointer advanced, string function
【Istio Network CRD VirtualService、Envoyfilter】