当前位置:网站首页>Iptables foundation and Samba configuration examples
Iptables foundation and Samba configuration examples
2022-07-04 13:08:00 【Brother Xing plays with the clouds】
- iptable Basic concepts
- Iptables Watch chain rules
- iptables The process of transmitting packets
- iptables Command format
- iptables Common options OPTIONS explain
- Common commands COMMANDS explain
- Common parameters PARAMETERS explain
- Use MATCH EXTENSIONS Extension module
- other
- Take an example to build samba The server
- To configure samba The server
- add to samba Account
- close SELinux A firewall
- To configure iptables
- First, check the current rules
- Add rules to enable samba Port used
- See the added rules
- Save the current rule and enable samba
iptable Basic concepts
iptables The firewall consists of two parts , Located in user space iptables Modules and are located in kernel space netfilter modular . The user space module provides insertion 、 Modify and remove the rules in the packet filter table , The kernel module performs actual filtering , So the more accurate name should be iptables/netfilter.
- surface (tables): Provide specific functions ,iptables Built in 4 Tables , namely filter surface 、nat surface 、mangle Table and raw surface , They are used to realize Packet filtering , Network address translation 、 Package refactoring ( modify ) and Data tracking processing .
- The rules (rules): In fact, it is the pre-defined conditions of network administrators .
- chain (chains): Is the path of packet propagation , Each chain is actually one of many rules Checklist , There can be one or more rules in each chain . When a packet reaches a chain ,iptables It starts with the first rule in the chain , See if the packet meets the conditions defined by the rules . common 5 A chain , namely INPUT、OUTPUT、FORWARD、PREROUTING and POSTROUTING.
Iptables surface 、 chain 、 The rules :
iptables The process of transmitting packets
iptables Command format
iptables Common options OPTIONS explain
Common commands COMMANDS explain :
- -A, –append chain: Add a rule to the end of the chain
- -D, –delete chain: Delete a rule
- -I, –insert chain [rulenum]: Given rule Number , Insert rules on the selected chain
- -R, –replace chain rulenum: Replace a rule
- -L, –list [chain]: View the list of rules for the specified table and chain
- -F, –flush [chain]: Delete [ Appoint ] All rules in the table
Common parameters PARAMETERS explain :
- -p Protocol type : You can specify the protocol to which the rule applies , namely TCP、UDP and ICMP etc.
- -s source address : The address can be hostname, It can also be IP etc.
- -d The goal is IP Address
- -j action
- –line-numbers: and -L Use it together , Show rules rulenum Number
- -n: Output in digital form IP Address and port
Use MATCH EXTENSIONS Extension module
- -m, –match module_name: Enable the expansion module , Such as state、tcp 、udp、multiport 、string 、addrtype 、mac etc.
- iptables -m module_name -h: Check the help information of the extension module ; Such as :
iptables -m mac -h
other
- If do not have -t Options , Default table by filter surface
- The default is saved in /etc/sysconfig/iptables In file
- service iptables save: Save the changed iptables
Take an example to build samba The server
To configure samba The server
modify /etc/samba/smb.conf file , First, add the directory to be shared :
[workspace] writable = yes path = /root/If you plan to make symbolic links accessible , It's in smb.conf Of [global] part , Add the following configuration :
follow symlinks = yes wide links = yes unix extensions = noadd to samba Account
smbpasswd -a smbpasswd -eclose SELinux A firewall
# sed -i 's/SELINUX=enforcing/SELINUX=disabled/' /etc/selinux/config # setenforce 0 # rebootTo configure iptables
First, check the current rules :
[[email protected] ~]# iptables -L --line-number Chain INPUT (policy ACCEPT) num target prot opt source destination 1 ACCEPT all -- anywhere anywhere 2 ACCEPT icmp -- anywhere anywhere 3 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh 4 ACCEPT tcp -- anywhere anywhere tcp dpt:http 5 ACCEPT tcp -- anywhere anywhere tcp dpt:https 6 ACCEPT udp -- anywhere anywhere udp dpt:bootpc 7 ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED 8 DROP all -- anywhere anywhere Add rules to enable samba Port used
After checking , To add to 8 In front of rule number , otherwise samba It doesn't work :
iptables -I INPUT 8 -p udp -m multiport --dport 137,138 -j ACCEPT iptables -I INPUT 8 -p tcp -m state --state NEW -m multiport --dport 139,445 -j ACCEPTSee the added rules
[[email protected] ~]# iptables -L --line-number -n Chain INPUT (policy ACCEPT) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 2 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 3 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 4 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 5 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443 6 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:68 7 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 8 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW multiport dports 139,445 9 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 137,138 10 DROP all -- 0.0.0.0/0 0.0.0.0/0Save the current rule and enable samba:
# Preservation rules service iptables save # Enable smb: service smb restart # send smb Randomizer start chkconfig smb on You can also use iptables -F Delete rule completely
边栏推荐
- Introduction to the button control elevatedbutton of the fleet tutorial (the tutorial includes the source code)
- C language: find the length of string
- CANN算子:利用迭代器高效实现Tensor数据切割分块处理
- 模块化笔记软件综合评测:Craft、Notion、FlowUs
- Apache server access log access Log settings
- Leetcode day 17
- 面向个性化需求的在线云数据库混合调优系统 | SIGMOD 2022入选论文解读
- ArcGIS uses grid processing tools for image clipping
- Building intelligent gray-scale data system from 0 to 1: Taking vivo game center as an example
- Fundamentals of container technology
猜你喜欢
C fonctions linguistiques
从0到1建设智能灰度数据体系:以vivo游戏中心为例
面向个性化需求的在线云数据库混合调优系统 | SIGMOD 2022入选论文解读

Building intelligent gray-scale data system from 0 to 1: Taking vivo game center as an example
AI 绘画极简教程

PostgreSQL 9.1 soaring Road
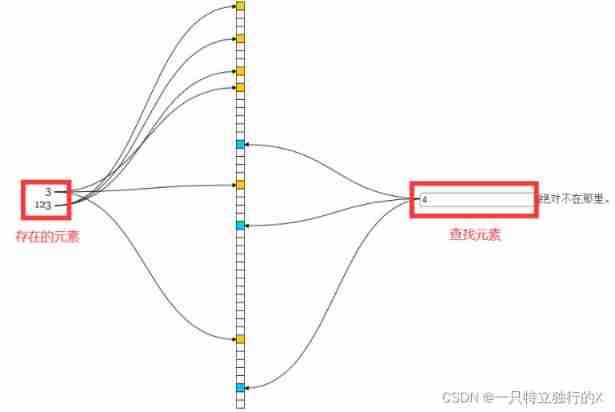
Understand bloomfilter in one article
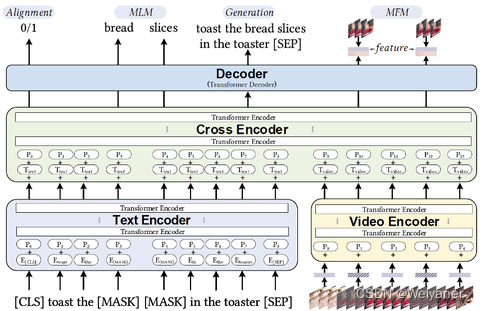
美团·阿里关于多模态召回的应用实践
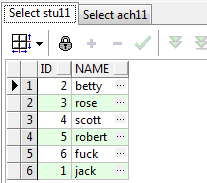
Solution: how to delete the information of Jack in two tables with delete in one statement in Oracle
![[data clustering] section 3 of Chapter 4: DBSCAN performance analysis, advantages and disadvantages, and parameter selection methods](/img/e6/2b46d72049ea50f89d0234eab88439.png)
[data clustering] section 3 of Chapter 4: DBSCAN performance analysis, advantages and disadvantages, and parameter selection methods
随机推荐
C#/VB.NET 给PDF文档添加文本/图像水印
Peak detection of measured signal
一个数据人对领域模型理解与深入
Valentine's Day confession code
BackgroundWorker用法示例
Can Console. Clear be used to only clear a line instead of whole console?
面试官:Redis 过期删除策略和内存淘汰策略有什么区别?
读《认知觉醒》
Langue C: trouver le nombre de palindromes dont 100 - 999 est un multiple de 7
DC-5靶机
C language: find the length of string
Master the use of auto analyze in data warehouse
游戏启动后提示安装HMS Core,点击取消,未再次提示安装HMS Core(初始化失败返回907135003)
【AI系统前沿动态第40期】Hinton:我的深度学习生涯与研究心法;Google辟谣放弃TensorFlow;封神框架正式开源
使用 NSProxy 实现消息转发
mysql三级分销代理关系存储
Deploy halo blog with pagoda
golang 设置goproxy代理的小细节,适用于go module下载超时,阿里云镜像go module下载超时
AI painting minimalist tutorial
runc hang 导致 Kubernetes 节点 NotReady