当前位置:网站首页>Text组件新增内容通过tag_config设置前景色、背景色
Text组件新增内容通过tag_config设置前景色、背景色
2022-07-05 22:05:00 【Moxianzhe】
Text组件新增内容时,可以通过tag_config给特定的字符串设定前景色、背景色等属性。
self.text1.tag_config('red',foreground = 'red',background = 'yellow') #消息列表分区中创建标签,ys2样式2的前景色为red
self.text1.insert(END,str(msg) + '\n','red')边栏推荐
- 等到产业互联网时代真正发展成熟,我们将会看待一系列的新产业巨头的出现
- Leetcode simple question ring and rod
- [Yugong series] go teaching course 003-ide installation and basic use in July 2022
- 华为云ModelArts文本分类–外卖评论
- ICMP 介绍
- Poj 3237 Tree (Tree Chain Split)
- Summarize the reasons for 2XX, 3xx, 4xx, 5xx status codes
- Talking about MySQL index
- Experienced inductance manufacturers tell you what makes the inductance noisy. Inductance noise is a common inductance fault. If the used inductance makes noise, you don't have to worry. You just need
- Huawei game multimedia service calls the method of shielding the voice of the specified player, and the error code 3010 is returned
猜你喜欢
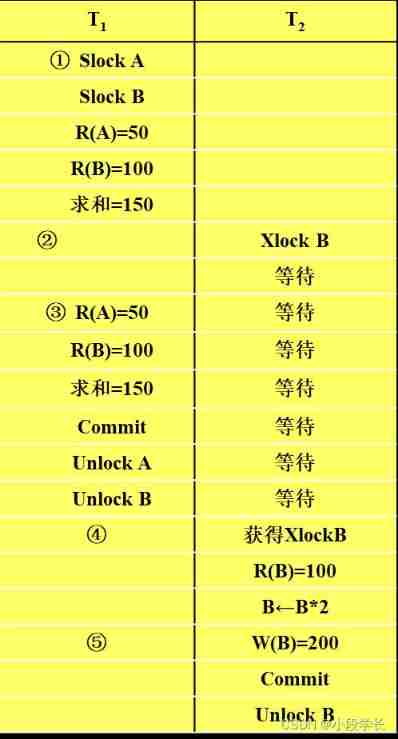
Blocking protocol for concurrency control

Storage optimization of performance tuning methodology
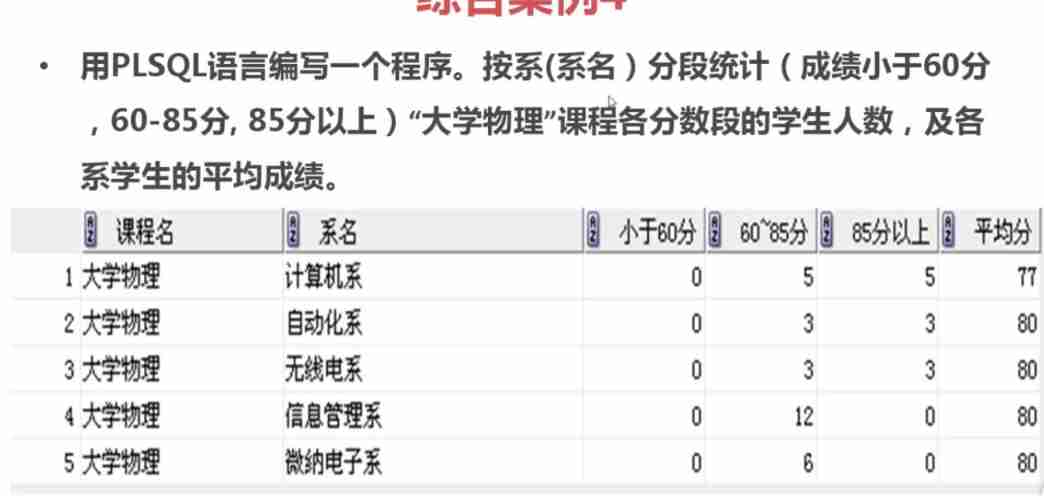
Pl/sql basic case
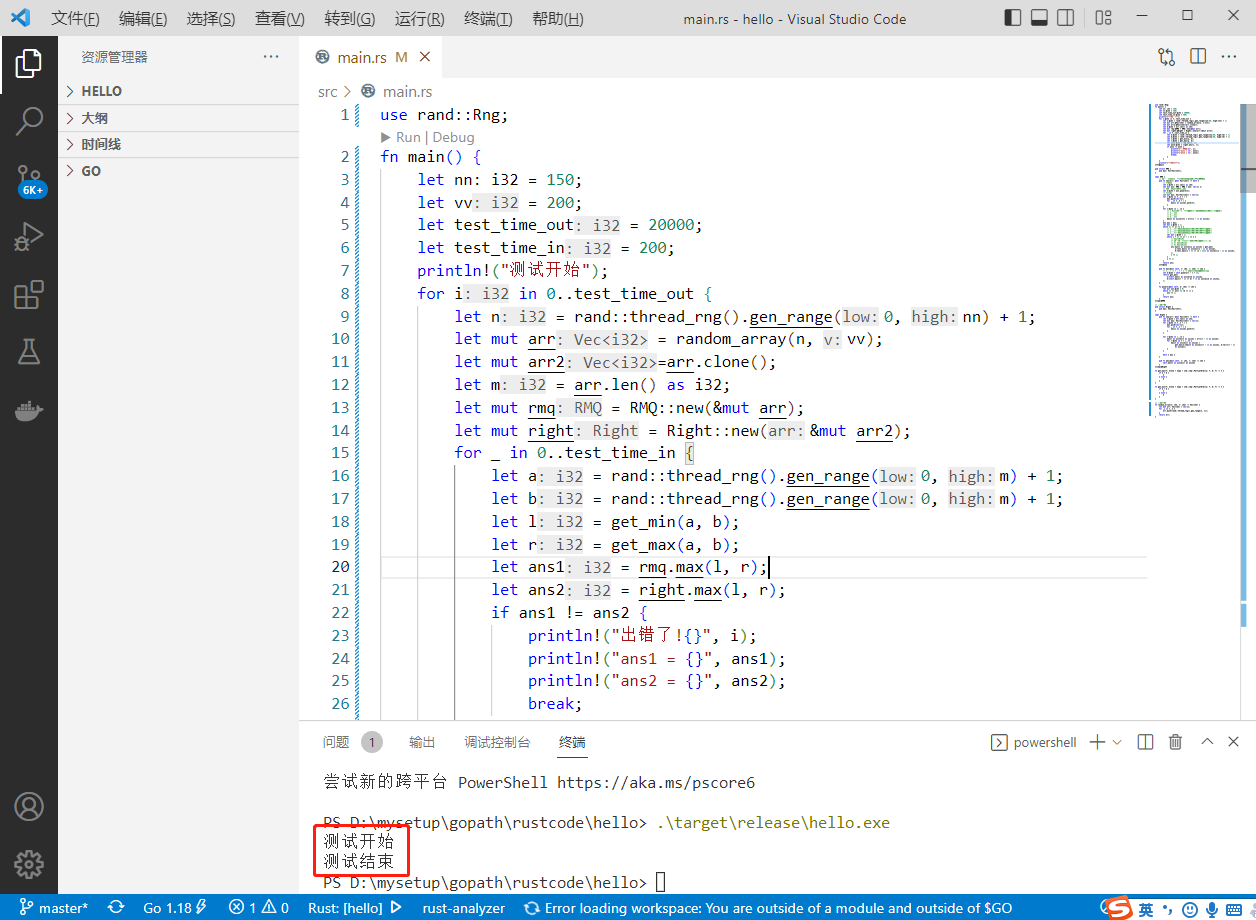
2022-07-05:给定一个数组,想随时查询任何范围上的最大值。 如果只是根据初始数组建立、并且以后没有修改, 那么RMQ方法比线段树方法好实现,时间复杂度O(N*logN),额外空间复杂度O(N*
![[Yugong series] go teaching course 003-ide installation and basic use in July 2022](/img/9d/7d01bc1daa61f6545f619b6746f8bb.png)
[Yugong series] go teaching course 003-ide installation and basic use in July 2022

PyGame practical project: write Snake games with 300 lines of code

A trip to Suzhou during the Dragon Boat Festival holiday

database mirroring
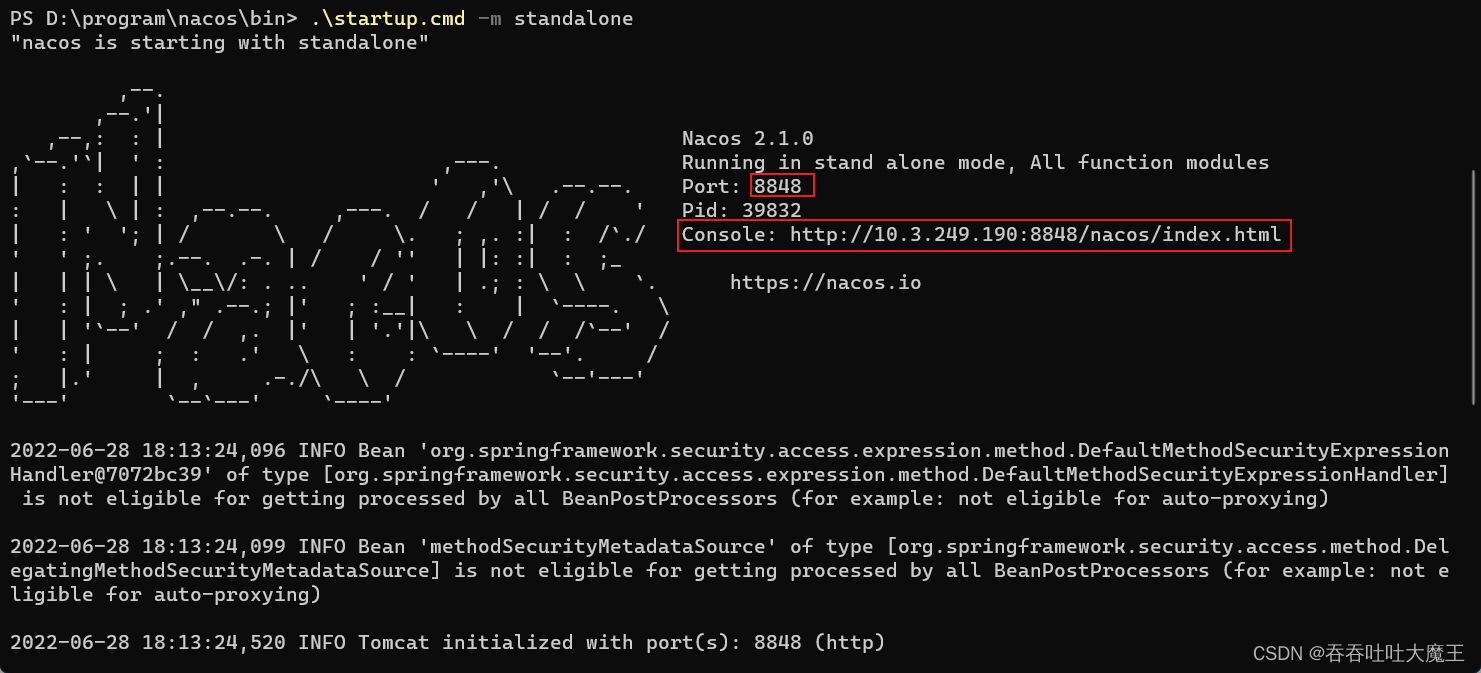
Getting started with microservices (resttemplate, Eureka, Nacos, feign, gateway)

The real situation of programmers
随机推荐
Huawei game multimedia service calls the method of shielding the voice of the specified player, and the error code 3010 is returned
[Yugong series] go teaching course 003-ide installation and basic use in July 2022
Installation of VMware Workstation
如何开发引入小程序插件
【愚公系列】2022年7月 Go教学课程 003-IDE的安装和基本使用
About the writing method of SQL field "this includes" and "included in" strings
U盘的文件无法删除文件怎么办?Win11无法删除U盘文件解决教程
Interprocess communication in the "Chris Richardson microservice series" microservice architecture
Serializability of concurrent scheduling
Ad637 notes d'utilisation
Stored procedures and stored functions
华为快游戏调用登录接口失败,返回错误码 -1
Drawing HSV color wheel with MATLAB
Learning of mall permission module
Experienced inductance manufacturers tell you what makes the inductance noisy. Inductance noise is a common inductance fault. If the used inductance makes noise, you don't have to worry. You just need
boundary IoU 的计算方式
database mirroring
How to add new fields to mongodb with code (all)
Overview of database recovery
An exception occurred in Huawei game multimedia calling the room switching method internal system error Reason:90000017