当前位置:网站首页>[redis] hash type
[redis] hash type
2022-06-29 01:58:00 【Riding a snail chasing a missile '】
List of articles
Hash type
Hash type , Also called hash , Its value It's an unordered Dictionary , Be similar to java Medium HashMap.
Compared with String Type serializes the object to Json character string , It is not very convenient to modify a field ; and Hash Structure can store each field in the object independently , You can do this for a single field CRUD:
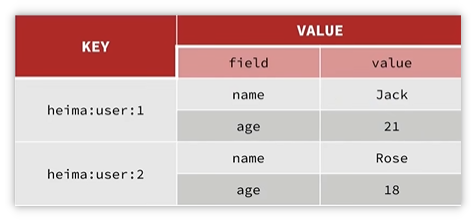

The basic general commands are shown in the figure above , Here is a detailed introduction !
1.1 HSET & HGET & HMSET & HMGET

HSET key field value: Add or modify hash type key Of field ValueHGET key field: Get one hash type key Of field ValueHMSET: Batch add multiple hash type key Of field ValueHMGET: Get more than one in batch hash type key Of field Value

You can see Hash Type implements a further layer of structured storage
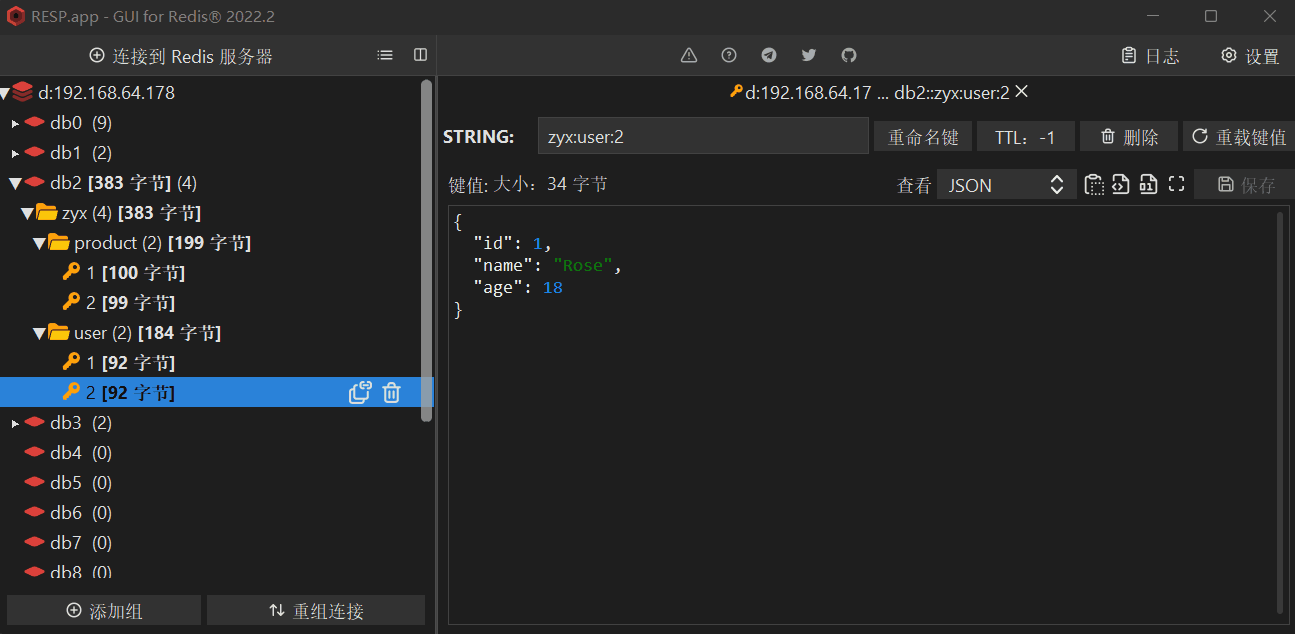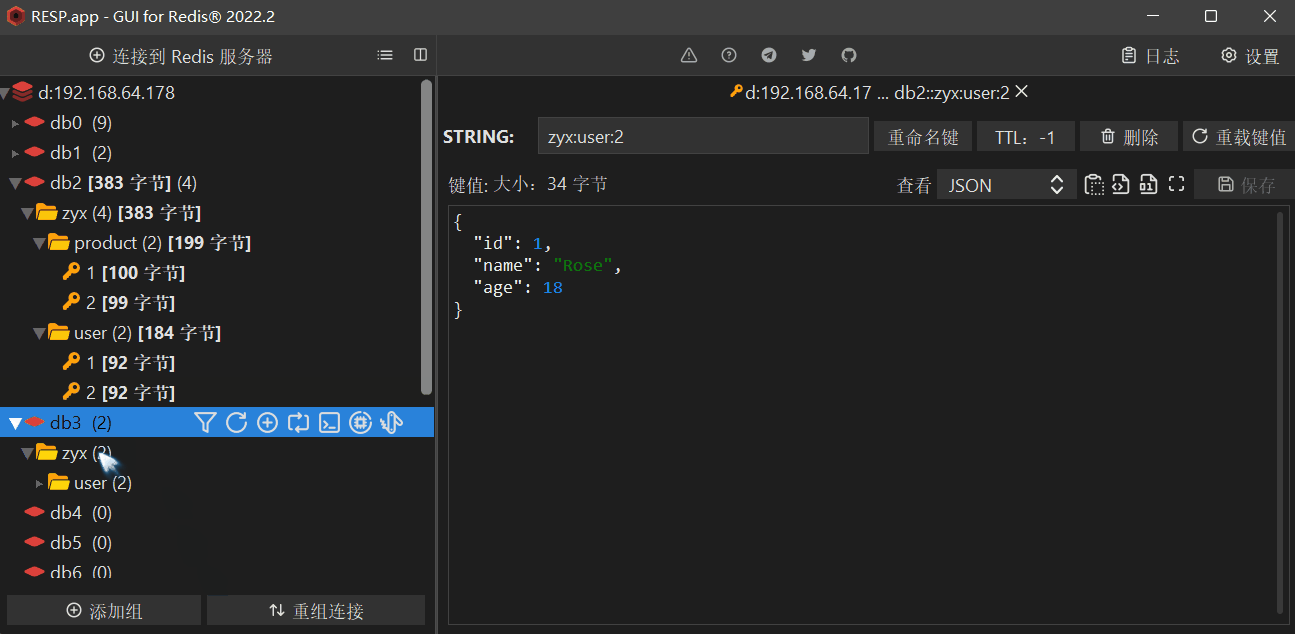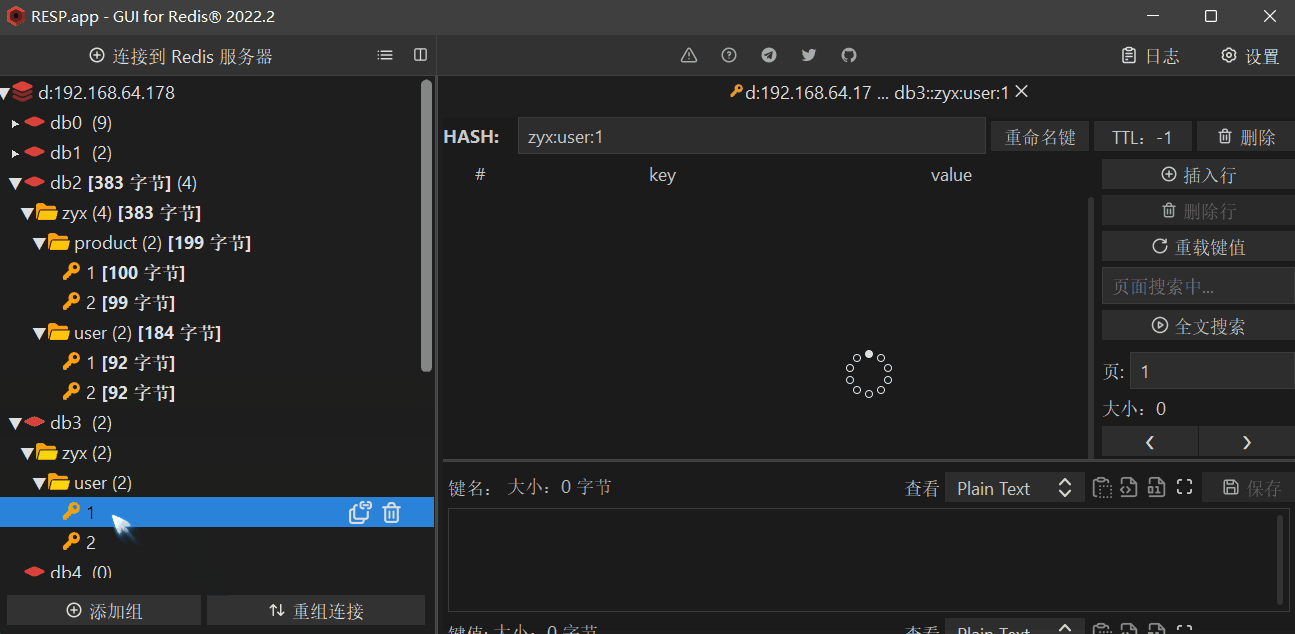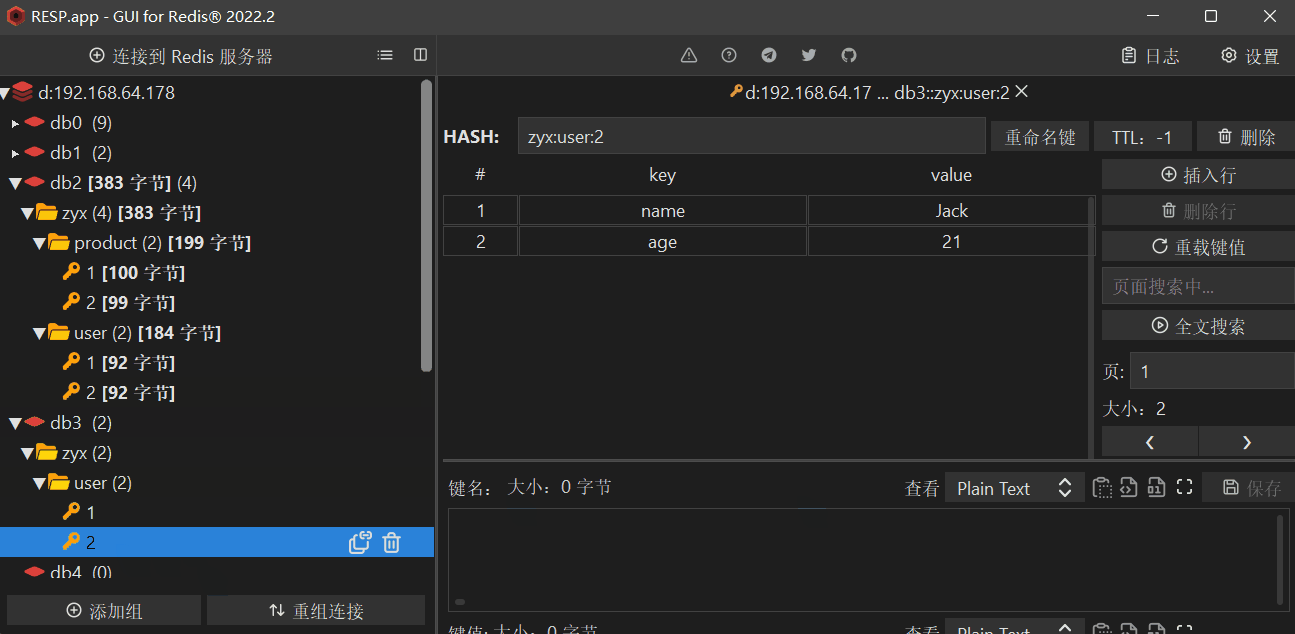
In batch processing, the attribute implementation for a single object is each field

1.2 HGETALL & HKEYS & HVALS

HGETALL: Get one hash Type of key All of them field and valueHKEYS: Get one hash Type of key All of them fieldHVALS: Get one hash Type of key All of them value

1.3 HINCRBY & HINCEBYFLOAT

HINCRBY: The number stored at the field in the hash stored at the increment key . If the key does not exist , A new key containing the hash will be created . If the field does not exist , Set the value to before performing the operation 0.HINCEBYFLOAT: In specified increments , The specified field stored at the key and representing the hash of the floating-point number increment. If the increment value is negative , The result is that the hash field value decreases , Not incremental . If one of the following occurs , Returns an error : This field contains a value of the wrong type ( It's not a string ); The current field content or the specified increment cannot be parsed as a double precision floating-point number .

1.4 HSETNX

Only if the field does not already exist , Will be stored in key to value The field in the hash at is set to . If the key does not exist , A new key containing the hash will be created . If the field already exists , Then this operation is invalid .
- 1 If the field is a new field in the hash and the value is set .
- If a field already exists in the hash and no action is taken , Then for 0.

1.5 HSTRLEN & HLEN

HSTRLEN: Get one hash Type of key The length of the medianHLEN: Get one hash Type of key All of them field Size

边栏推荐
- Oculusrifts and unity UI interaction (1) - Overview
- Test a CSDN free download software
- How to become a senior digital IC Design Engineer (5-1) theory: clock technology, reset Technology
- 指南针手机股票开户哪个券商更安全更方便?
- Pat grade a real problem 1165
- Tiflash compiler oriented automatic vectorization acceleration
- SAP ui5 beginner tutorial Part 23 - sorting sort and grouping Group trial version of list control
- Why is it recommended that you choose the self research company as much as possible
- Is the ETF fund reliable and safe
- Research on VB multi-layer firewall technology - state detection
猜你喜欢

HBuilder左侧工具栏不见了
![[high concurrency, high performance and high availability of massive data MySQL practice-10] - Implementation of mvcc in InnoDB](/img/dc/a30ccd9943e668aef8c874980a4975.jpg)
[high concurrency, high performance and high availability of massive data MySQL practice-10] - Implementation of mvcc in InnoDB

ASP. Design and implementation of net+sql online alumni list

Near consensus mechanism

How to manage device authorization

I have summarized some experiences from the whole process of R & D platform splitting

独家分析 | 软件测试关于简历和面试的真实情况

【Redis】数据介绍 & 通用命令 & String类型

Analysis of parsing principle of OData metadata request response in SAP ui5 application

Typescript (7) generic
随机推荐
[TS] type alias
[C language] Fibonacci sequence and frog jumping steps (the most detailed elementary frog jumping steps)
Mysql database password modification
OculusRiftS与Unity.UI的交互(1)-总览
Uniapp notes
How to encrypt anti copy program
How to become a senior digital IC Design Engineer (6-7) digital IC Verification: debug skills
独家分析 | 软件测试关于简历和面试的真实情况
How to manage device authorization
利用kubernetes資源鎖完成自己的HA應用
如何成为一名高级数字 IC 设计工程师(4-3)脚本篇:C 语言实现的文件读写操作
When you complain about the roll, others have quietly begun to prepare for the golden three silver four
【Redis】Set类型
Secondary encapsulation of storage (sessionstorage/localstorage) using TS
如何成为一名高级数字 IC 设计工程师(6-7)数字 IC 验证篇:DEBUG 技巧
大三下期末考试
Typescript (6) function
Fundamentals of scala (3): operators and process control
Scala 基礎 (三):運算符和流程控制
Magic Quadrant of motianlun's 2021 China Database