当前位置:网站首页>Go deep into the underlying C source code and explain the core design principles of redis
Go deep into the underlying C source code and explain the core design principles of redis
2022-07-05 18:58:00 【bingtanghulu_ six】
Catalog
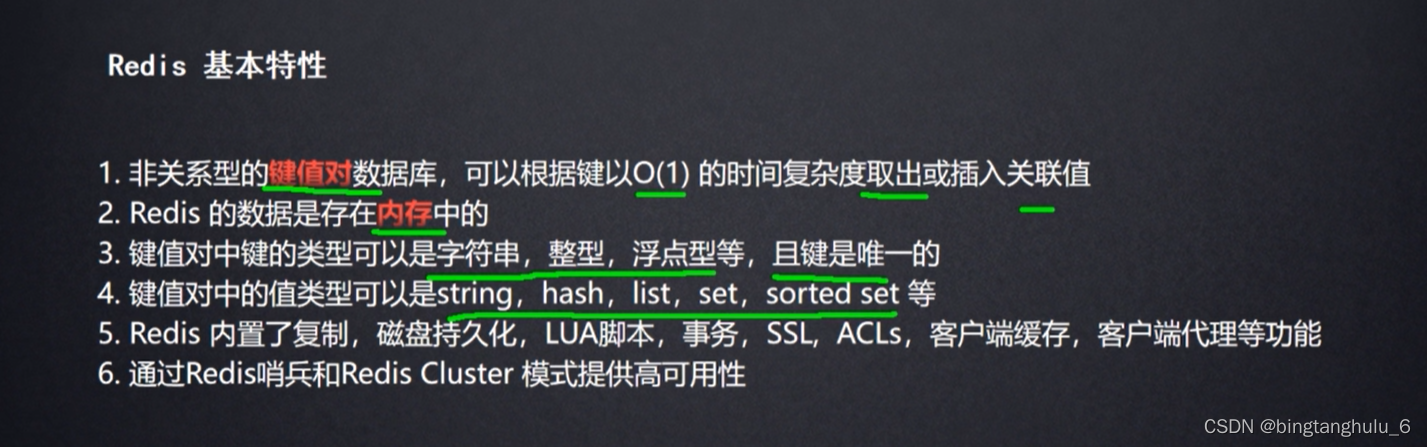
1.redis Basic characteristics
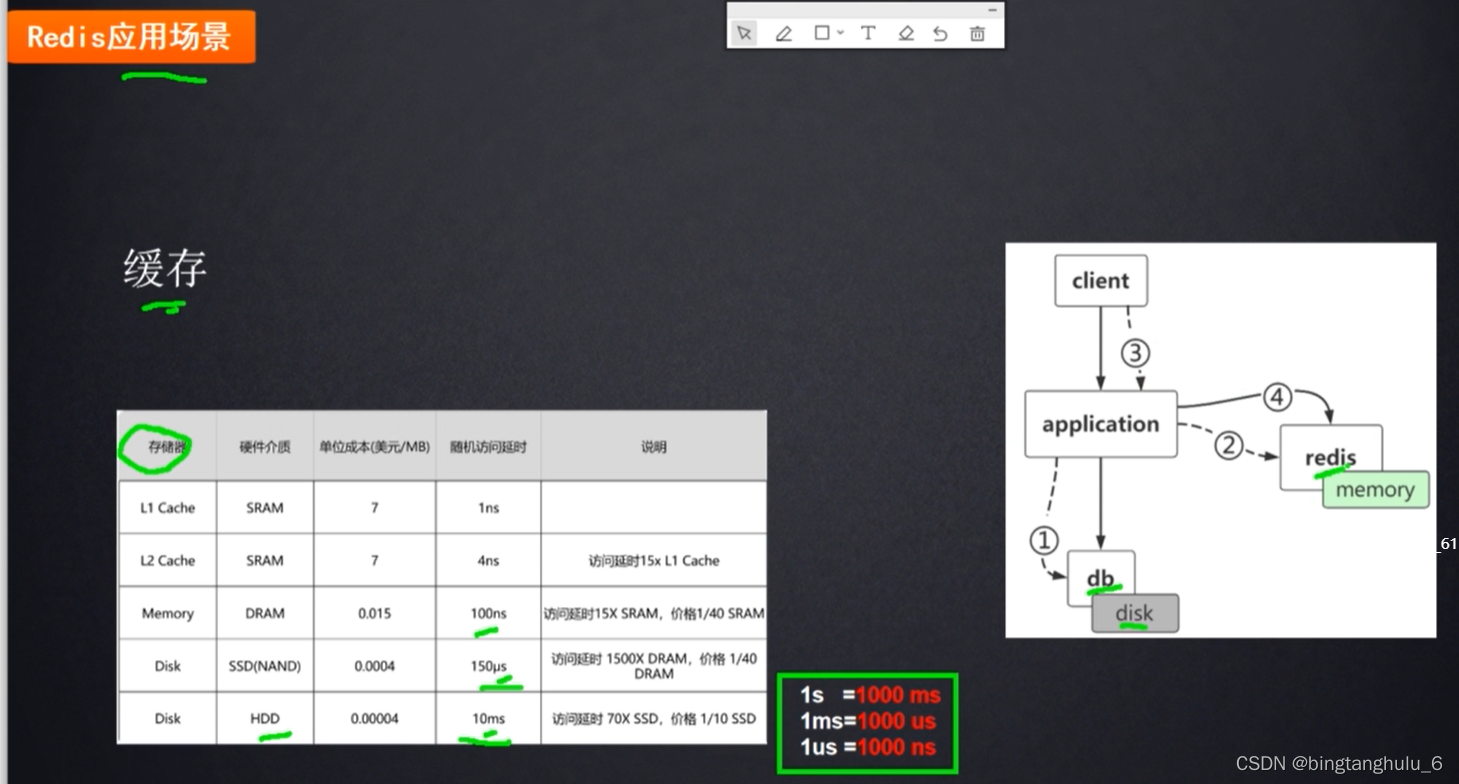
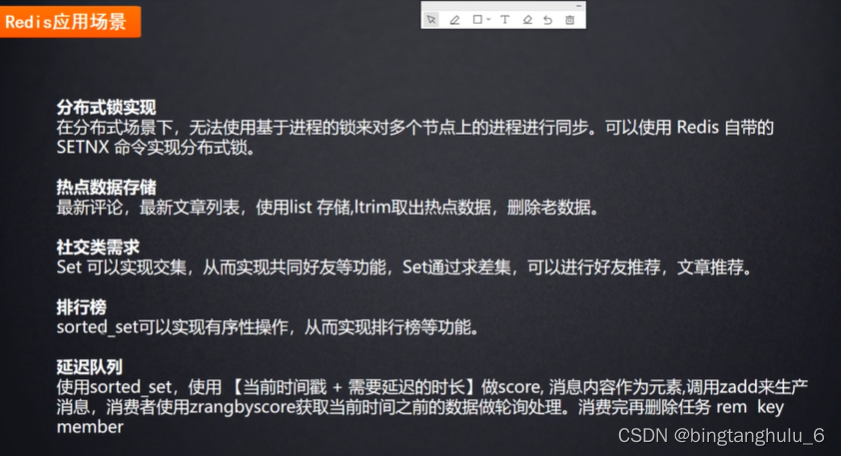
2.redis Application scenarios
3. data structure
3.1 string
redis All of them are k-v structure ,key At the bottom, it's all string structure ,value Yes string,hash,set,sorted set,list etc. .
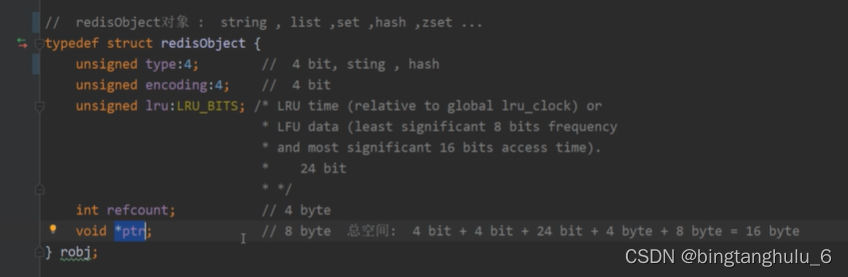
among string The data structure in is as follows ,3.2 Previously, there were only three parameters len( Character length ),free( Free space ),buf[]( Storage variable )
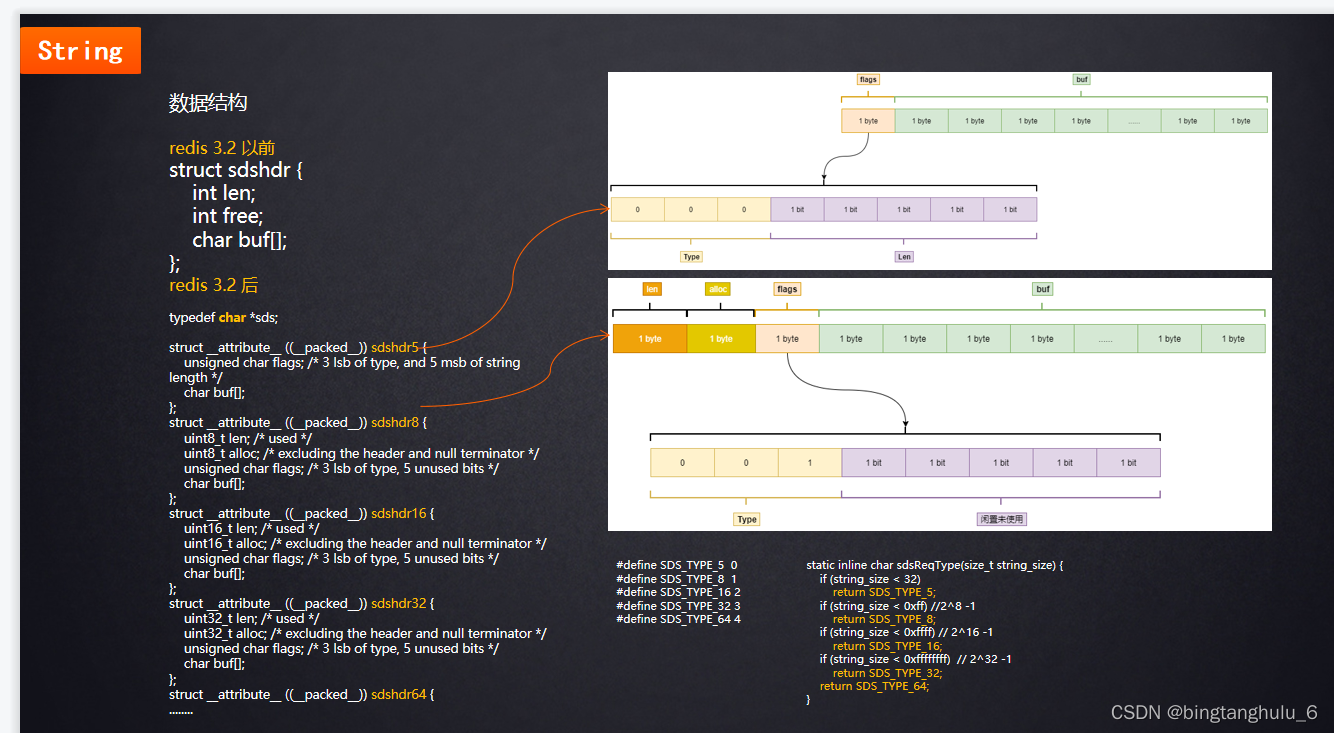
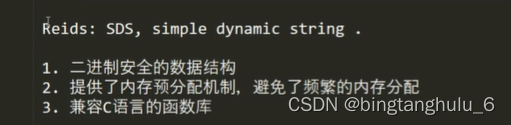
redis in string Three characteristics of strings
1. Binary secure data structures
c Language in string str='xxx\0'; The structure of string is represented by a \0 For the end .
2. Provides a memory pre allocation mechanism , Avoid frequent memory allocation
Provide capacity expansion mechanism , Algorithm :(len+addlen)*2
3. compatible C Language function library .
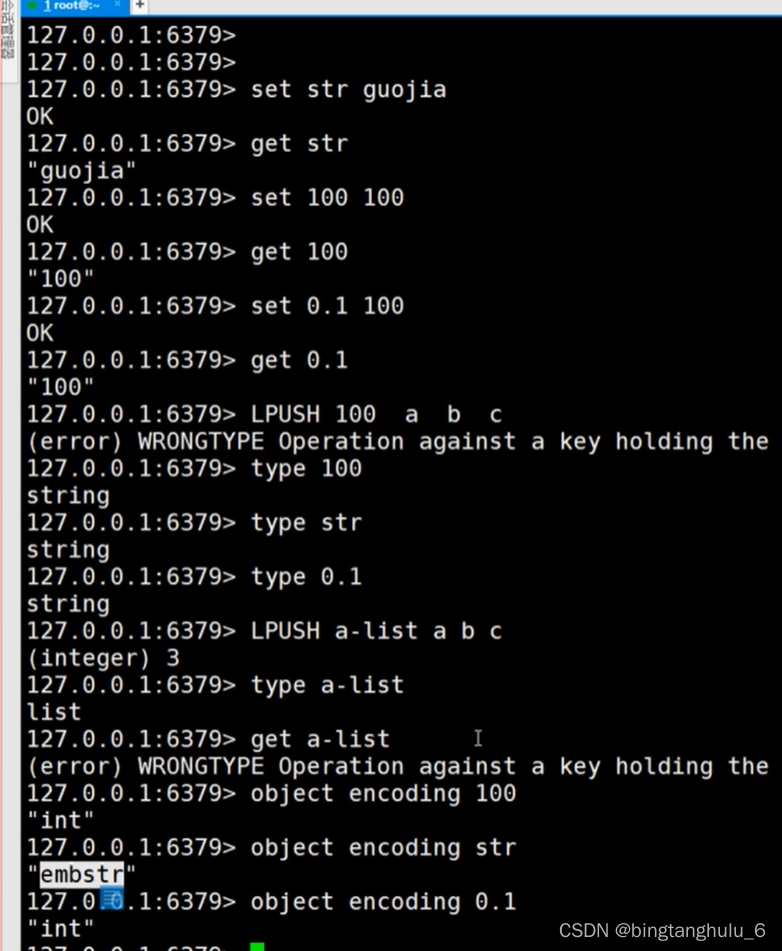
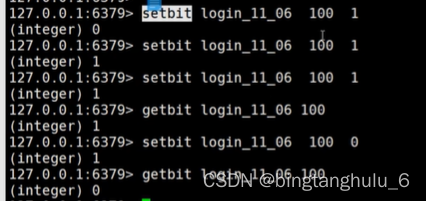
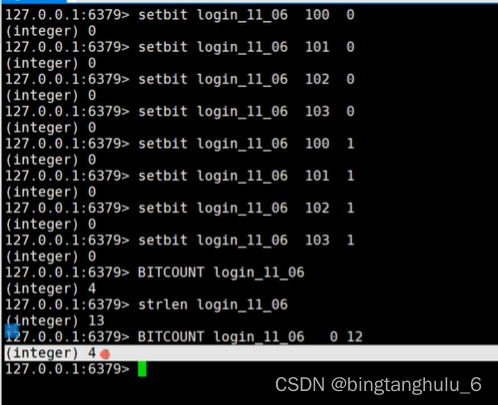
bitmap Bottom use string,string The maximum length that a string can represent 512M.
The following figure shows the statistics of weekly live users
边栏推荐
- SAP feature description
- Redhat7.4 configure Yum software warehouse (rhel7.4)
- ROS安装报错 sudo: rosdep:找不到命令
- Cronab log: how to record the output of my cron script
- Analysis of postman core functions - parameterization and test report
- 2022 Alibaba Android advanced interview questions sharing, 2022 Alibaba hand Taobao Android interview questions
- 进程间通信(IPC):共享内存
- Linear table - abstract data type
- RPC protocol details
- 泰山OFFICE技术讲座:由行的布局高度,谈绘制高度的高度溢出、高度缩水(全网首发)
猜你喜欢

android中常见的面试题,2022金九银十Android大厂面试题来袭

视频自监督学习综述

Web3.0时代来了,看天翼云存储资源盘活系统如何赋能新基建(下)
Case sharing | integrated construction of data operation and maintenance in the financial industry
Why can't Bi software do correlation analysis? Take you to analyze

2022年阿里Android高级面试题分享,2022阿里手淘Android面试题目

如何快速进阶自动化测试?听听这3位BAT大厂测试工程师的切身感想....
Interprocess communication (IPC): shared memory
Mysql database indexing tutorial (super detailed)
Powerful tool for collection processing
随机推荐
Insufficient picture data? I made a free image enhancement software
2022 latest Android interview written examination, an Android programmer's interview experience
How to write good code defensive programming
国内低代码开发平台靠谱的都有哪些?
Tupu software digital twin smart wind power system
Simple query cost estimation
Case sharing | integrated construction of data operation and maintenance in the financial industry
泰山OFFICE技术讲座:由行的布局高度,谈绘制高度的高度溢出、高度缩水(全网首发)
AI Open2022|基于异质信息网络的推荐系统综述:概念,方法,应用与资源
7-1 linked list is also simple fina
瞅一瞅JUC提供的限流工具Semaphore
Benefits of automated testing
Rse2020/ cloud detection: accurate cloud detection of high-resolution remote sensing images based on weak supervision and deep learning
如何快速进阶自动化测试?听听这3位BAT大厂测试工程师的切身感想....
Cronab log: how to record the output of my cron script
lombok @Builder注解
c语言简便实现链表增删改查「建议收藏」
Oracle Chinese sorting Oracle Chinese field sorting
MYSQL中 find_in_set() 函数用法详解
Icml2022 | partial and asymmetric comparative learning of out of distribution detection in long tail recognition