当前位置:网站首页>extendible hashing
extendible hashing
2022-06-27 06:29:00 【honky-tonk_ man】
Preface
First, what is an extensible hash (Extendible Hashing)?
We usually use hash It's all static hash, For example, a number wants to be deposited into hash In the table , Go first hash function , Then save it into the corresponding hash In the table , Pay attention to this hash The table is a static , Its size is fixed at the beginning of creation , As we store more and more data ,hash The watch is getting slower and slower , The conflict rate is also increasing , We'd better maintain hash The number of elements in the table accounts for hash 70% of the capacity of the meter , In this way, the conflict rate can be kept low , At this point, we use dynamic hash, That is, our extensibility hash
Scalable hash structure
Scalable hash Yes 2 Kinds of structure , Namely
- directory: Is an extensible array , Each array element stores a bucket The pointer to ,directory Each element has a unique id, This id interesting , Is a binary number
- bucket: As long as this is hash All the watches , Used to store hash Table data , In other words, more than one bucket form hash surface
- global depth: This thing and directory It matters , because directory Each array element of the has a unique id, This id It's binary bit Composition e.g 1,11,011, and global depth On behalf of you directory id There is one bit, Like our global depth by 3, So it corresponds to directory id At most 111, explain directory id At most 7, That is to say, at most 8 Array elements
- local depth: and global almost , however local depth It's corresponding to bucket,local depth Always less than or equal to global depth
About bucket, When one bucket The number of elements in exceeds the specified number , here bucket There will be divisions (bucket splitting)
About Directory, When bucket Split up ,directory It will happen expansion
Scalable hash The process of
Our traditional static hash The process is hash Function directly stores the value in the corresponding bucket, But in extensibility hash in , First pass through hash The function is stored in Directory in , Again by directory Pointing to corresponding bucket, The specific process is as follows
To be analyzed hash Of key The type of , May be int, May be string, May be float wait , Suppose our key Namely int Type digital 49
take key Convert to binary form ,49 Convert to binary to 110001
check global depth , hypothesis global depth by 3
Select corresponding directory, How to choose ? our 49 Binary for 110001 altogether 6 position , and global depth by 3, It only needs 3 position , At this point we intercept 110001 The last three 001 As directory id
Start positioning to the corresponding bucket in
Start inserting elements , Again check bucket whether overflow
7. If overflow, And Corresponding bucket Of local depth be equal to global depth Add one to all , And then again hash overflow Of bucketBe careful global depth Adding one will add a lot of elements , At this point, we need to point these extra array elements to local depth Less than global depth Of bucket On
- If overflow And the corresponding bucket Of loacl depth Greater than global depth, Only the corresponding bucket Of local depth Add one and re hash This overflow Of bucket that will do
Reference from 1
https://www.geeksforgeeks.org/extendible-hashing-dynamic-approach-to-dbms/ ︎
边栏推荐
- 日期 数据库日期 字符串 之间互相转换
- LeetCode 0086.分隔链表
- Cloud-Native Database Systems at Alibaba: Opportunities and Challenges
- Assembly language - Wang Shuang Chapter 8 two basic problems in data processing - Notes
- 观测电机转速转矩
- 1317. convert an integer to the sum of two zero free integers
- [QT dot] realize the watchdog function to detect whether the external program is running
- IDEA一键生成Log日志
- Dev++ environment setting C language keyword display color
- Once spark reported an error: failed to allocate a page (67108864 bytes), try again
猜你喜欢

427-二叉树(617.合并二叉树、700.二叉搜索树中的搜索、98. 验证二叉搜索树、530.二叉搜索树的最小绝对差)

我对于测试团队建设的意见

The restart status of the openstack instance will change to the error handling method. The openstack built by the container restarts the compute service method of the computing node and prompts the gi
JVM object composition and storage
Free SSH and telnet client putty

Quick realization of Bluetooth ibeacn function
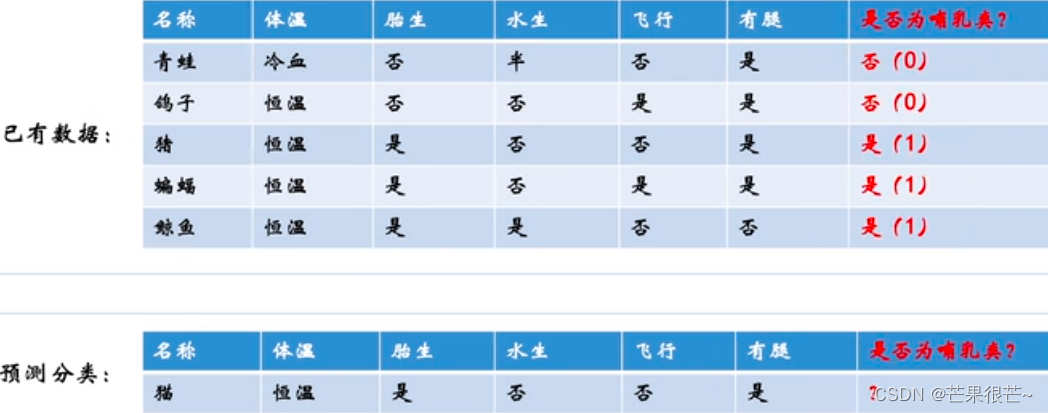
Distribution gaussienne, régression linéaire, régression logistique

建模竞赛-光传送网建模与价值评估

matlab GUI界面仿真直流电机和交流电机转速仿真
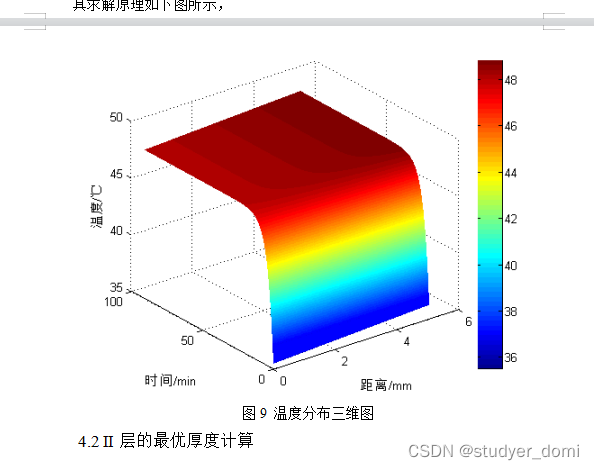
2018年数学建模竞赛-高温作业专用服装设计
随机推荐
Assembly language - Wang Shuang Chapter 11 flag register - Notes
Cloud-Native Database Systems at Alibaba: Opportunities and Challenges
Block level elements & inline elements
Ahb2apb bridge design (2) -- Introduction to synchronous bridge design
【养成系】常用正则表达式
JVM调优思路
Gaussian distribution, linear regression, logistic regression
One year's experience of technical personnel in Entrepreneurship
高斯分布Gaussian distribution、线性回归、逻辑回归logistics regression
Maxcompute SQL 的查询结果条数受限1W
使用 WordPress快速个人建站指南
How to check the frequency of memory and the number of memory slots in CPU-Z?
Proxy reflect usage details
研究生数学建模竞赛-无人机在抢险救灾中的优化应用
el-select多个时,el-select筛选选中过的值,第二个el-select中过滤上一个选中的值
1317. convert an integer to the sum of two zero free integers
openresty使用文档
yaml文件加密
记一次Spark报错:Failed to allocate a page (67108864 bytes), try again.
快速实现单片机和手机蓝牙通信