当前位置:网站首页>HCIA Basics (1)
HCIA Basics (1)
2022-07-27 02:16:00 【Not smart】
Catalog
Topological structure classification of network
OSI Seven layer reference model
The definition of network
Devices with network connection connect network terminal devices through transmission media , Share resources 、 Information transmission platform
Topological structure classification of network
Star topology
Star structure is a center , Multiple sub nodes . It has a simple structure , Easy to connect , Management and maintenance are relatively easy , And it's scalable . The network latency is small , Low transmission error . There is no fault in the center , Generally, there is no problem with the network . Central failure , The network goes wrong , At the same time, the sharing ability is poor , The utilization rate of communication line is not high .
Bus topology
Bus topology all devices are connected to one connecting medium . The bus structure requires a small number of cables , The cable length is short , Easy wiring and maintenance . Multiple nodes share a transmission channel , High channel utilization . But don't find diagnostic trouble .
Ring topology network
A ring topology network is one in which nodes form a closed loop . Fewer workstations , Saving equipment . Of course , This leads to a node problem , The network will go wrong , And it's hard to diagnose the fault .
Tree topology
Tree topology evolved from bus topology , Shaped like an inverted tree , The top is the root , There are branches below the root , Each branch can also be branched , The tree root receives the data sent by each site , Then broadcast to the whole network . Good expansion , Easy to diagnose errors , But the requirements for the root are high .
Network topology
The most widely used , Its advantage is that it is not affected by bottleneck problems and failure problems , One day the line went wrong , Can do other lines , But it's too complicated , The high cost .
The role of the switch
1、 Provide port density ( Inherited HUB The role of )
2、 Based on data identification and retransmission , It realizes theoretically infinite transmission distance
3、 Based on data recognition 、 Store and forward , Solved the problem of conflict
4、 be based on MAC Address recognition 、 Record 、 Inquire about , Realize unicast communication
How the switch works
The switch works in the media access control layer , Identify and convert current to binary , After the data current enters the switch , The switch first recognizes it as a layer-2 binary , Then identify the source in the data frame mac Address , Record the local MAC In the address table ,(MAC Record each MAC Corresponding interface ), Then focus on the target in the data frame MAC Address , Then query the local MAC Is there any record in the table , If there are records , Only record based interface unique forwarding ( unicast ), If there is no record, flooding will occur .
notes : Flooding means that in addition to the access interface of flow , All other interfaces copy out .
What routers do
1、 Interconnection between different networks
2、 Cut off the broadcast domain
3、 Choose the path for the data it carries --- Route selection
How routers work
When the packet enters the router , First check the target IP Address , Then query the local routing table , If there are records in the table , take Unconditional Forward as recorded , If there is no record , The traffic will be discarded .
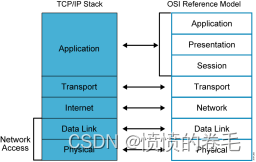
OSI Seven layer reference model
application layer : Input and output of abstract language , Encode abstract language .
The presentation layer : Convert the encoding to binary ( code decode encryption Decrypt )
The session layer : Application internal address , Distinguish between sessions in the program Find out -- establish -- maintain -- Terminate the conversation
Transport layer :1. Provide port numbers to distinguish different services ( Static port number 1---1023 Dynamic port number 1024---65535 Special port number 0--- Represents all port numbers --- Network programming uses ) 2. Data segmentation ( suffer MTU Limit )3. Provide reliable transmission --TCP/UDP
The network layer :Internet agreement --IP ( Addressing Addressing according to IP Address for logical addressing )
Data link layer : according to MAC Address for physical addressing (LLC Logical link control layer MAC Media access control layer )
The physical layer : Define the electrical voltage 、 Optical characteristics , The interface specification
TCP/IP agreement

TCP/IP The agreement refers to OSI Architecture of .OSI The model has seven layers , But it's more complicated , So in TCP/IP Agreement , They are reduced to four levels
(1) application layer 、 The presentation layer 、 The services provided by the three layers of conversation layer are not very different , So in TCP/IP Agreement , They are merged into a hierarchy of application layers
(2) Because the transport layer and network layer are very important in the network protocol , So in TCP/IP In the protocol, they are regarded as two independent levels
(3) Because the contents of the data link layer and the physical layer are not much different , So in TCP/IP In the protocol, they are merged in a layer of the network interface layer .
Encapsulation of data

application layer : Raw data is converted into binary data
Transport layer : Binary data is divided into small data segments , And package TCP Head ( Data segment )
(TCP The key information of the head – Port number )
The network layer : The data from the transport layer is encapsulated IP Head ( Data packets )
(IP The key information of the head –IP Address )
Data link layer : The data from the network layer is encapsulated MAC Head ( Data frame )
(MAC The key information of the head –MAC Address )
The physical layer : The bit stream composed of binary data is transformed into electrical signal and transmitted in the network ( Bit stream )
TCP
TCP: Transmission control protocol -- Connection oriented reliable transport protocol
After completing the basic work of the transport layer , It also needs to further ensure the reliability of transmission
Connection oriented : adopt TCP Three handshakes of establish an end-to-end virtual link
Reliable transmission :4 A reliable mechanism -- confirm 、 Retransmission 、 Sort 、 Flow control ( The sliding window )

UDP
UDP: user datagram protocol -- Non connection oriented unreliable transport protocol
Only the basic work of transmission is completed --- piecewise 、 Port number

URL
URL(Uniform Resource Locator) Uniform resource locator , It's the computer Web Network related terms , It means web address . Our Internet world is made up of many URL form , It can also be said that URL To show .
URL It's made up of three parts : The resource type 、 Host domain name where resources are stored 、 Resource file name .
DNS
DNS It's the domain name system (Domain Name System) For short , On the Internet as domain names and IP A distributed database with address mapping , It can make it easier for users to access the Internet , Instead of remembering what can be read directly by the machine IP Address .
Domain name resolution process :
(1) After entering the domain name , First find the domain name server corresponding to your host , The domain name server first looks up the data in its own database .
(2) without , Search the superior domain name server , By analogy
(3) Up to the root domain name server , I'm sure I can find this domain name IP Address
(4) The domain name server itself does some caching , Compare the domain name you have visited with the corresponding IP The address is cached , Can speed up the search process
IPv4 Address
IPv4 Address by 32 Bit binary structure , Expressed in dotted decimal , With global uniqueness ( Public address )
Public address :
A class ---C class
A:8 Bit network bit ,24 Bit host bit composition .0.0.0.0-127.255.255.255. 0-127
B:16 Bit network bit ,16 Host location . 128.0.0.0-191.255.255.255
C:24 Bit network bit ,8 Host location .192.0.0.0-223.255.255.255
D Class or E class :
D: Multicast address . 224.0.0.0-239.255.255.255.
E: Reserved address , Not yet used . 240.0.0.0-255.255.255.255
Private address :10.0.0.0-10.255.255.255 172.16.0.0-172.31.255.255 192.168.0.0-192.168.255.255
VLSM: By extending the length of the subnet mask , From the original host bit to the network bit , Realize the segmentation of a network number into multiple . Every new subnet , There will be fewer hosts , Add network number , Reduce the number of users in each network number , Increase the number of network segments
CIDR: No inter domain routing -- Take phase parity , Go to different places , Logically synthesize multiple network numbers into one
- Subnet summary -- After summary , The mask of the summary network segment is longer than the main class
- HYPERNET -- After summary , The mask of the summary network segment is shorter than the main class mask
Static routing
Static routing , It is the route added by the network administrator for the router by manual configuration . The popular saying is : The network administrator tells the router through manual configuration :“ You want to reach your destination X, The data packet needs to be transferred from the interface Y Throw it out for the next jump Z.
[r1]ip route-static 192.168.3.0 24 192.168.2.2
( Target segment ) ( Next jump )
Loopback interface
stay TCP/IP The middle loop device is a virtual network interface realized by software , It is not associated with any hardware . meanwhile , It can be used in experimental environment , Analog connection PC User interface of terminal , To reduce the actual equipment cost demand .
[r1]interface LoopBack ?
<0-1023> LoopBack interface number( Available range of loopback interface )
[r1]interface LoopBack 0
[r1-LoopBack0]ip address 1.1.1.1 24
Default route
A route that does not limit the destination , Represents all network segments , Router When looking up the table, you are querying all local direct connections 、 static state 、 If there is still no reachable path after dynamic routing , Use this entry .
[r1]ip route-static 0.0.0.0 0.0.0.0 192.168.1.1
( Next jump )
Floating static
A special static routing , Go to the same destination network segment through configuration , But static routes with different priorities , In order to ensure a higher priority route in the network , That is, when the main route fails , Provide backup routing . Under normal circumstances , The backup route will not appear in the route table .
[r1]ip route-static 100.100.100.0 24 13.1.1.2 preference ?
INTEGER<1-255> Preference value range( Priority range )
[r1]ip route-static 100.100.100.0 24 13.1.1.2 preference 61
边栏推荐
- Realize data interaction between two apps through fileprovider
- 6.29 众安暑期测开实习一面
- [explain C language in detail] takes you to play with loop structure (for_while_do while)
- 6.30滴滴面经(一面+二面)
- STM32入门教程第二讲
- TIM输出比较——PWM
- IS指标复现 文本生成图像IS分数定量实验全流程复现 Inception Score定量评价实验踩坑避坑流程
- 6.29 Zhong'an Summer Internship
- [reprint] NVIDIA hardware and the accuracy mode supported by each hardware
- Text to image论文精读GR-GAN:逐步细化文本到图像生成 GRADUAL REFINEMENT TEXT-TO-IMAGE GENERATION
猜你喜欢

Solution: various error reports and pit stepping and pit avoidance records encountered in the alchemist cultivation plan pytoch+deeplearning (II)
![[explain C language in detail] takes you to play with loop structure (for_while_do while)](/img/d9/75053297873a5b5458514e7f557cdc.png)
[explain C language in detail] takes you to play with loop structure (for_while_do while)

Js九九乘法表
TCP的三次握手与四次断开
HCIA Basics (1)

2022 latest live broadcast monitoring 24-hour monitoring (III) analysis of barrage in live broadcast room
![[reprint] GPU compute capability table](/img/7c/87be1131f52f21fe080c36f0834467.png)
[reprint] GPU compute capability table

2022最新直播监控24小时监控(三)直播间弹幕解析

初识C语言(1)

定时器中断实验
随机推荐
a元素的伪类
[FPGA tutorial case 30] DDS direct digital frequency synthesizer based on FPGA -- frequency accuracy analysis with MATLAB
Text to image论文精读SSA-GAN:基于语义空间感知的文本图像生成 Text to Image Generation with Semantic-Spatial Aware GAN
2022 latest Tiktok live broadcast monitoring (II) streaming media download in live broadcast room
C语言——赋值运算符、复合的赋值运算符、自增自减运算符、逗号运算符、条件运算符、goto语句、注释
mgre的全连和星型拓扑实验
HCIA动态路由OSPF实验
解决方案:Win10如何使用bash批处理命令
Text to image论文精读RAT-GAN:文本到图像合成中的递归仿射变换 Recurrent Affine Transformation for Text-to-image Synthesis
TIM输出比较——PWM
三种能有效融合文本和图像信息的方法——特征拼接、跨模态注意、条件批量归一化
最新C语言入门与进阶 -史上最全最详细的C语言教程!! 第一节-总览C语言概括
Solution: various error reports and pit stepping and pit avoidance records encountered in the alchemist cultivation plan pytoch+deeplearning (II)
TCP的三次握手与四次断开
Es specify user name and password when instantiating resthighlevelclient
[reprint] GPU compute capability table
动态路由ofps协议配置
STM32_HAL_SUMMARY_NOTE
2022最新直播监控24小时监控(三)直播间弹幕解析
Text to image paper intensive reading rat-gan: recursive affine transformation for text to image synthesis