当前位置:网站首页>Network byte order
Network byte order
2022-07-04 02:10:00 【Soy sauce;】
Network byte order description
TCP/IP Provisions of the agreement , Network data stream should adopt big end byte order , That is, low address, high byte . For example, in the previous section UDP Segment format , Address 0-1 yes 16 Bit source port number , If the port number is 1000(0x3e8), Address 0 yes 0x03, Address 1 yes 0xe8, That is, the first 0x03, Reissue 0xe8, this 16 The bit in the buffer of the sending host should also be a low address memory 0x03, Highland site storage 0xe8. however , If the sending host is small endian , this 16 Bits are interpreted as 0xe803, instead of 1000. therefore , Send the host to 1000 Byte order conversion is required before filling in the send buffer . similarly , If the receiving host is in small end byte order , Receive 16 The source port number of bit also needs to be converted into byte order . If the host is big endian , No conversion is required for sending and receiving . Empathy ,32 Bit IP The address should also consider the network byte order and host byte order .
In order to make the network program portable , Make the same C The code can run normally after compiling on both big end and small end computers , You can call the following library functions to do network byte order and host byte order conversion .
Network big end , Small end of host
Network and host byte order conversion function – Data are all addresses
#include <arpa/inet.h>
uint32_t htonl(uint32_t hostlong); Host to network , Long
uint16_t htons(uint16_t hostshort); Network to host , short
uint32_t ntohl(uint32_t netlong); Network to host , Long
uint16_t ntohs(uint16_t netshort); Network to host , short
h Express host,n Express network,l Express 32 Bit long integers ,s Express 16 Bit short integer .
If the address of the host is small endian , These functions do the corresponding large and small conversion of parameters, and then return , If the host is big endian , These functions don't convert , Return the parameters as they are .
Dot decimal string conversion function
#include <arpa/inet.h>
int inet_pton(int af, const char *src, void *dst);// Hexadecimal string to big end 
const char *inet_ntop(int af, const void *src, char *dst, socklen_t size);// Big end to hexadecimal string


Support IPv4 and IPv6
Reentrant function
among inet_pton and inet_ntop Not only can it be converted IPv4 Of in_addr, You can also convert IPv6 Of in6_addr.
So the function interface is void *addrptr.
Code
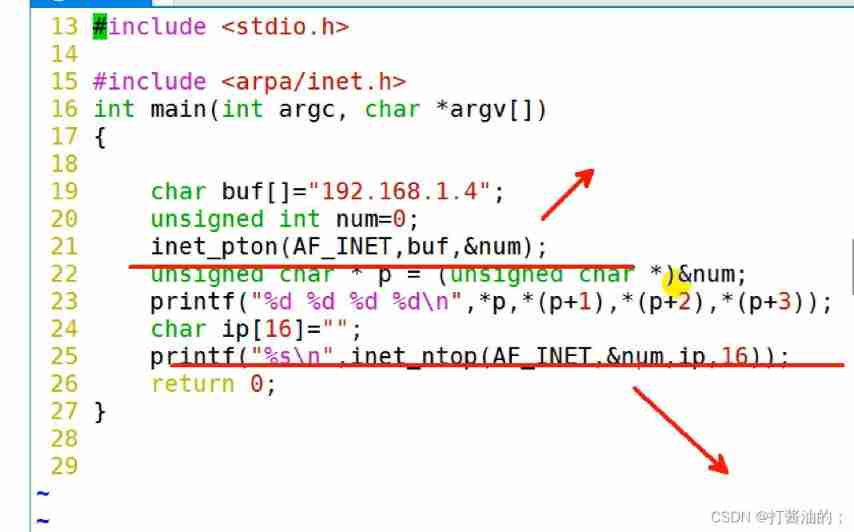
#include <stdio.h>
#include <arpa/inet.h>
int main(int argc, char *argv[])
{
char buf[]="192.168.1.4";
unsigned int num=0;
inet_pton(AF_INET,buf,&num);
unsigned char * p = (unsigned char *)#
printf("%d %d %d %d\n",*p,*(p+1),*(p+2),*(p+3));
char ip[16]="";
printf("%s\n",inet_ntop(AF_INET,&num,ip,16));
return 0;
}
边栏推荐
- The requests module uses
- Pesticide synergist - current market situation and future development trend
- Customize redistemplate tool class
- What are the main investment products of bond funds and what are they
- JVM performance tuning and practical basic theory - medium
- Yyds dry goods inventory hand-in-hand teach you the development of Tiktok series video batch Downloader
- Properties of binary trees (numerical aspects)
- Take you to master the formatter of visual studio code
- When tidb meets Flink: tidb efficiently enters the lake "new play" | tilaker team interview
- [Yugong series] February 2022 attack and defense world advanced question misc-84 (MySQL)
猜你喜欢

Small program graduation project based on wechat examination small program graduation project opening report function reference
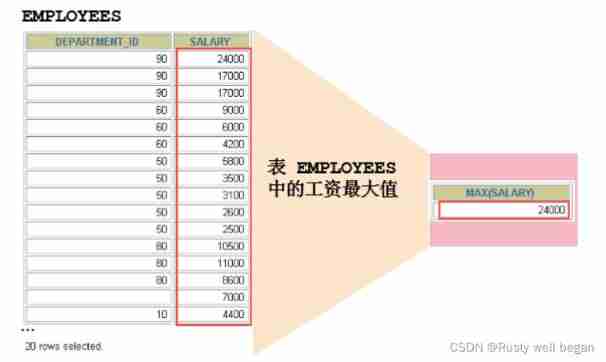
Mysql-15 aggregate function
![Setting function of Jerry's watch management device [chapter]](/img/0b/8fab078e1046dbc22aa3327c49faa7.jpg)
Setting function of Jerry's watch management device [chapter]
![Jerry's watch listens to the message notification of the target third-party software and pushes the message to the device [article]](/img/8b/ff062f34d36e1caa9909c8ab431daf.jpg)
Jerry's watch listens to the message notification of the target third-party software and pushes the message to the device [article]

Override and virtual of classes in C #

MySQL advanced (Advanced) SQL statement (I)

LeetCode226. Flip binary tree

On Valentine's day, I code a programmer's exclusive Bing Dwen Dwen (including the source code for free)
Douban scoring applet Part-3

A fan summed up so many interview questions for you. There is always one you need!
随机推荐
Properties of binary trees (numerical aspects)
Yyds dry goods inventory hand-in-hand teach you the development of Tiktok series video batch Downloader
Meta metauniverse female safety problems occur frequently. How to solve the related problems in the metauniverse?
Sword finger offer 14- I. cut rope
中電資訊-信貸業務數字化轉型如何從星空到指尖?
Feign implements dynamic URL
MySQL advanced (Advanced) SQL statement (I)
In yolov5, denselayer is used to replace focus, and the FPN structure is changed to bi FPN
Bacteriostatic circle scanning correction template
MySQL advanced SQL statement (1)
LeetCode226. Flip binary tree
Override and virtual of classes in C #
JVM performance tuning and practical basic theory - medium
When the watch system of Jerry's is abnormal, it is used to restore the system [chapter]
Small program graduation project based on wechat video broadcast small program graduation project opening report function reference
Pesticide synergist - current market situation and future development trend
Basic editing specifications and variables of shell script
Méthode de calcul de la connexion MSSQL de la carte esp32c3
When tidb meets Flink: tidb efficiently enters the lake "new play" | tilaker team interview
在尋求人類智能AI的過程中,Meta將賭注押向了自監督學習