当前位置:网站首页>Basic knowledge of cryptography
Basic knowledge of cryptography
2022-07-02 15:33:00 【Killer is not too cold!】
Cryptography Basics
Symmetric encryption algorithm ( Private key encryption algorithm )
Symmetric encryption : Use the same key for encryption and decryption . It means the key you use to encrypt a piece of content , And the key used for encrypted ciphertext is the same key , This is called symmetric encryption .
Private key password encryption is used .
advantage : Fast encryption and decryption , Ciphertext is compact , Security .
The encryption and decryption process of symmetric encryption is shown in the following figure :

But symmetric encryption has a problem , We use our private key to encrypt plaintext , But how can we give our private key to each other ? Through network transmission, we can indeed transfer our private key information to each other , But it's not safe , Because hackers can get your transmission key through the network .
Famous symmetric encryption algorithm
DES 3DES: DES The key length of the algorithm is 56 position ,3DES The algorithm is to enlarge the length of the key by three times, that is 168,DES The algorithm has great delay , Cannot be used for wireless / Voice and video encryption
AES: AES The algorithm uses 128 position ,192 Bit or 256 Bit length key ,3DES Alternative encryption technology , High software and hardware efficiency , Can be used for wireless / Voice and video encryption
RC series (RC2,RC4,RC5): RC2 encryption algorithm , Key length is variable ,RC2 The speed of computing is faster than DES fast , Software implementation RC2 Than DES Three times faster ,RC2 Is it better than DES Security depends on the length of the key it uses
IDEA: IDEA International data encryption algorithm , The grouping length is 64 position , The key length is 128 position
CAST
Blowfish: Key length is variable , Security can be adjusted by changing the key length , Suitable for encryption where the key does not change frequently , It is not applicable to the case that the key needs to be changed frequently
DES Algorithm framework diagram :
Asymmetric encryption algorithm ( Public key encryption algorithm )
Public key encryption appeared later than private key encryption , Private key encryption uses the same key to encrypt and decrypt information , Public key encryption uses two keys , A key is used to encrypt information , Another key is used to decrypt information .
In asymmetric encryption algorithm, public key is used to encrypt , Private key used to decrypt .
The workflow of asymmetric encryption algorithm is shown in the following figure :
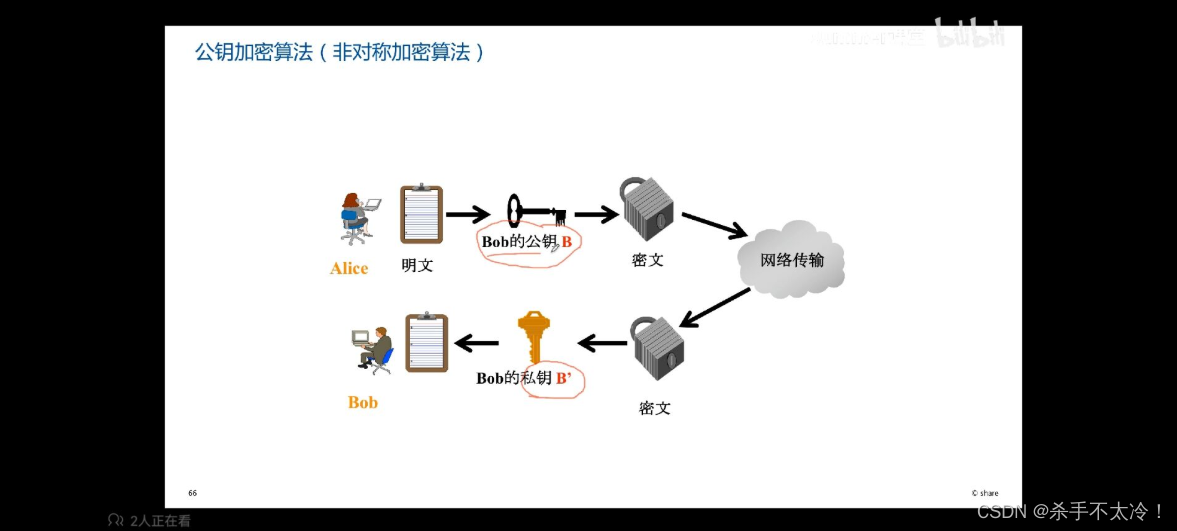
** Characteristics of asymmetric encryption algorithm :** The private key needs to be saved safely ( Not transmitted over the network ), Public key disclosure , Encryption speed is slow , Ciphertext is not compact , It can be combined with symmetric encryption .
Common asymmetric encryption algorithms :
RSA: The key length is 512~4096bit Between , Security is based on the difficulty of factoring large prime numbers .RSA Compared with software DES slow 100 times ,RSA Its main functions are encryption , Digital signature and key exchange ( Encryption hash , secret key )
The sender encrypts with the public key of the receiver , Then transmit the ciphertext to the receiver , Finally, the receiver decrypts with its own private key .
DSA:
ECC: This is the encryption algorithm of bitcoin .
Three uses of public key encryption algorithm :
encryption / Decrypt
digital signature : The sender signs the message with its private key , The receiver verifies the signature of the other party with the public key of the other party
key exchange : Both parties negotiate the session key
digital signature
First of all, what is digital signature , What is the process of digital signature ? Here's the picture :
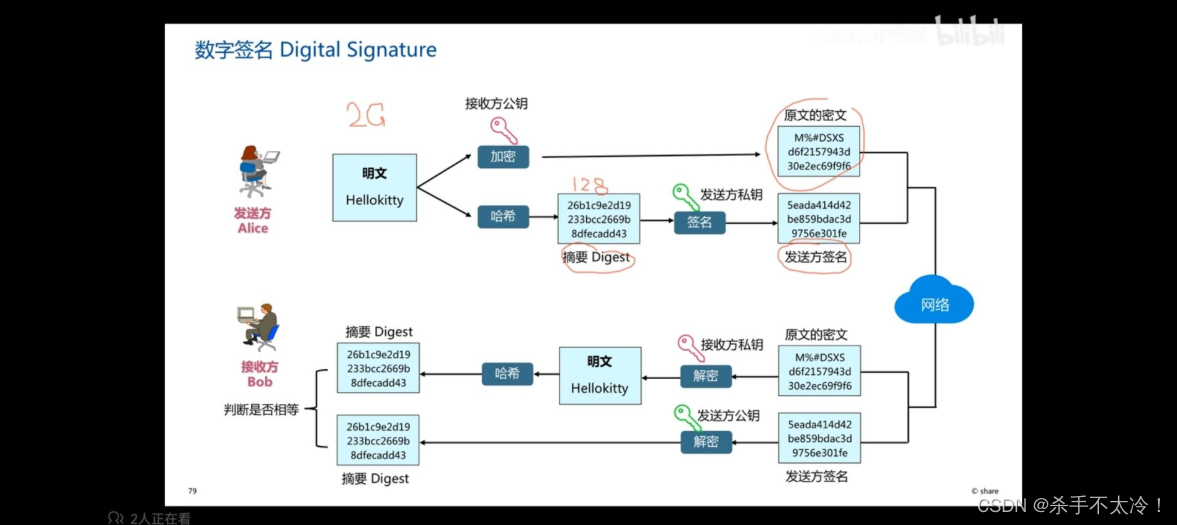
First , The sender encrypts the plaintext into ciphertext , Then a segment of abstract in plaintext will be encrypted into ciphertext Abstract , Then the sender will send the ciphertext and the abstract ciphertext of the original text to the receiver , The abstract ciphertext of the original text is actually the signature of the sender . But in the process of our transmission through the network , Our ciphertext and signature may be tampered with by hackers , So how do we judge whether it has been tampered with ? After receiving the ciphertext , Decrypt the ciphertext into plaintext , Then get the plaintext digest by hashing . Then the receiver decrypts the abstract ciphertext , It will be parsed into a clear text summary . Finally, compare these two plaintext abstracts
Are they the same? , If the same, pass .
In fact, on the whole , The receiver needs to check whether the signature in the ciphertext is the same as the signature sent by the sender , If it is the same signature , Then this data is safe and has not been tampered with , Otherwise , This data has been tampered with during network transmission .
Digital certificates and CA
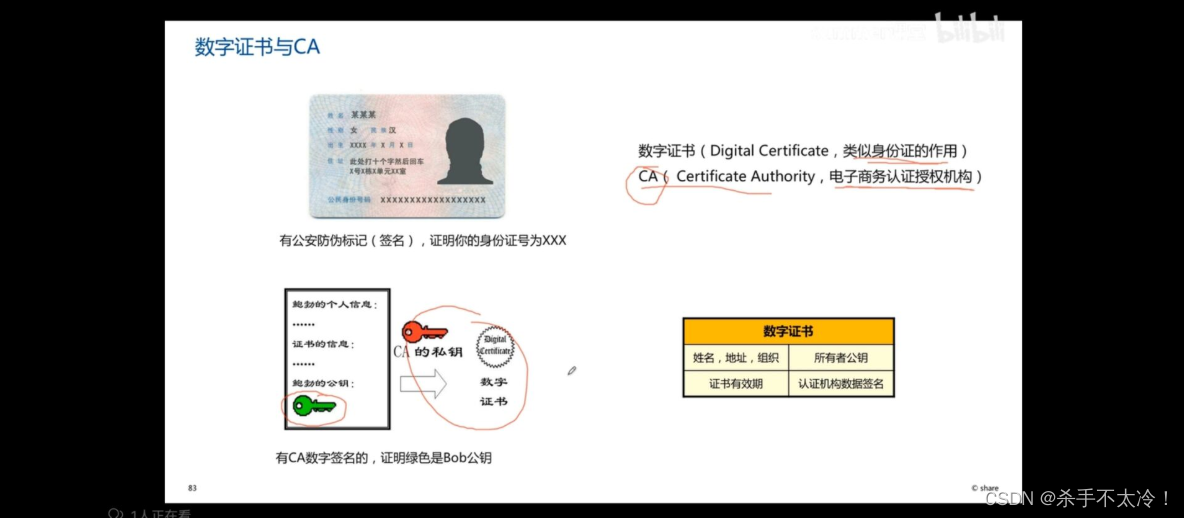
Let's start with a question , How can you be sure that the public key you use when encrypting is the public key of the receiver ? Here's the picture :

Digital certificates can be used to prove .
digital certificate (Digital Certificate, Similar to the role of ID card ),CA(Certificate Authority, E-commerce certification authority ).
The public key we want to prove plus CA The private key of the authority can generate a digital certificate , The information contained in this digital certificate is name , Address , organization , Owner public key , The certificate is valid for , Certification authority data signature . Here's the picture :
The specific style of digital certificate is shown in the following figure :

Merchant API certificate
Merchant API certificate , It was applied by the merchant , Contains the merchant number of the merchant , Corporate name , Public key information .
Merchant API Certificate is actually CA A certificate issued by an authority that can represent the information of the merchant .
Merchant API Certificates are like our ID cards , It is issued by the public security organ , Certificate with our citizen information on it .
Merchant API Private key
Merchants apply for merchants API On certificate , A merchant private key will be generated , And save the file in the local certificate folder apliclient_key.pem in . The private key can also be obtained from the merchant's p12 Export from certificate . Please take good care of your merchant private key file , Don't expose the private key file in public , Upload to Github, Write in the client code .
Wechat payment platform certificate
Wechat payment platform certificate refers to the certificate applied by wechat payment , Including wechat payment platform logo , Certificate of public key information . Merchants can use the public key in the platform certificate for signature verification .
Declare the certificate used by the certificate serial number
In some cases , You will need to update key pairs and certificates . In order to ensure that the replacement process does not affect API Use , Request and answer HTTP The head includes Certificate serial number , To declare the key pairs and certificates used for signing or encryption .
- Merchant signature use Merchants private key , The certificate serial number is included in the request HTTP The head of the Authorization Of serial_no
- Wechat payment signature use Wechat payment platform private key , The certificate serial number is included in the reply HTTP The head of the Wechatpay-Serial
- When merchants submit sensitive information Wechat payment platform public key encryption , The certificate serial number is included in the request HTTP The head of the Wechatpay-Serial
API v3 secret key
To ensure safety , Wechat payment in Callback notice and Platform certificate Download interface , The key information is AES-256-GCM encryption .API v3 The key is a symmetric key used in encryption .
边栏推荐
猜你喜欢
Bing. Com website

自定义异常

I made an istio workshop. This is the first introduction

NBA player analysis
Solve the problem of frequent interruption of mobaxterm remote connection

Guangzhou Emergency Management Bureau issued a high temperature and high humidity chemical safety reminder in July
Redux——详解
21_ Redis_ Analysis of redis cache penetration and avalanche

Build your own semantic segmentation platform deeplabv3+

Leetcode skimming -- incremental ternary subsequence 334 medium
随机推荐
03_线性表_链表
Mavn builds nexus private server
06_栈和队列转换
folium,确诊和密接轨迹上图
19_ Redis_ Manually configure the host after downtime
Markdown tutorial
Data analysis thinking analysis methods and business knowledge - business indicators
SQL transaction
How does the computer set up speakers to play microphone sound
02_ Linear table_ Sequence table
04. Some thoughts on enterprise application construction after entering cloud native
面对“缺芯”挑战,飞凌如何为客户产能提供稳定强大的保障?
Party History Documentary theme public welfare digital cultural and creative products officially launched
Redux——详解
03.golang初步使用
03_線性錶_鏈錶
02.面向容器化后,必须面对golang
There are 7 seats with great variety, Wuling Jiachen has outstanding product power, large humanized space, and the key price is really fragrant
Equipped with Ti am62x processor, Feiling fet6254-c core board is launched!
12_ Redis_ Bitmap_ command

