当前位置:网站首页>Research on the security of ognl and El expressions and memory horse
Research on the security of ognl and El expressions and memory horse
2022-07-02 04:24:00 【Domestic giant panda】
First, we study the security of expression engine , Mainly through comparison st2 Of ognl Expression injection and el Expression injection , Let's take a look at the present java Some situations of safety .
1)ognl expression
ognl The expression injection vulnerability mainly lies in st2 On this development framework , Let's first look at the official vulnerability address
https://cwiki.apache.org/confluence/display/WW/Security+Bulletins
remove dos Loophole 、jackson and xstream Loophole 、xss Loophole , The rest is ognl expression rce 了
Then we can read the following article carefully , Security giants have analyzed one by one ognl The mechanism of the vulnerability , Gives a complete summary .
https://www.anquanke.com/post/id/169735
2)el expression
el Expressions are divided into :SimpleEvaluationContext and StandardEvaluationContext, among SimpleEvaluationContext By default, it's safe
2.1) The following link is CVE-2022-22947 Spring Cloud Gateway Fix for expression injection
https://github.com/spring-cloud/spring-cloud-gateway/commit/337cef276bfd8c59fb421bfe7377a9e19c68fe1e
2.2) The following link is CVE-2022-22963 Spring Cloud Function Fix for expression injection
Through the above two examples, we can cure , Where business permits, use SimpleEvaluationContext instead of StandardEvaluationContext perform el expression
2.3) The link below shows ,CVE-2022-22980 spring-data-mongodb Instead of simply using SimpleEvaluationContext
3) Through the above content, we can get a concept , Expression injection is actually much like script injection . In order to increase business efficiency and flexibility, the system can execute any dynamic expression submitted externally , But directly execute external expressions that are not filtered or not strictly filtered , It will lead to safety risks . But when we search for the right el When filtering data of expressions , It is found that we can only search some usage information , Can't find knowledge about security filtering . So we can only summarize by ourselves :
By analyzing the expressions injected into the memory horse , Filtering single quotation marks is a better filtering logic at present
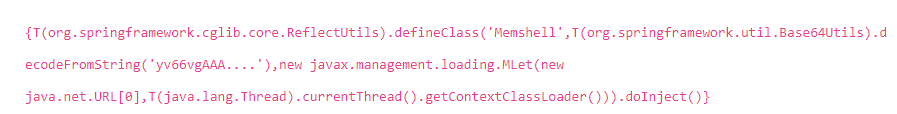
meanwhile spring-data-mongodb The patch of is also implemented in this way
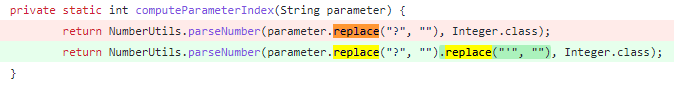
4) To sum up further , The injection of memory horse can depend on :
4.1.1)jndi Inject , In the high version java Remote is not allowed by default in jndi Inject
4.1.2)el expression 、ognl expression
4.1.3)webshell
4.1.4)agent Inject
webshell and agent Involving hard disk writing , This is related to host security products , In this article, we will not analyze . The rest is to focus on the expression engine .
So let's discuss this step , The best way is to use rasp Technical monitoring el Expression and ognl The execution content of the expression , Once the expression length exceeds the threshold, such as 100, be rasp The current expression should be reported and performed once jvm Safety analysis of the whole process .
4.2) The scope of security analysis should include common memory horse related classes
4.2.1)Servlet,Filter,Listener,Tomcat Value Pipe,Spring Controller,Spring Interceptor
( Refer to this article :https://mp.weixin.qq.com/s/HODFJF3NJmsDW2Lcd-ebIg)
4.2.2) The above classes should use hsdb Technology for analysis , prevent agent The injected bytecode is not captured
Refer to this article :https://my.oschina.net/9199771/blog/5529686
4.3) The security analysis should judge whether the common memory horse related classes are abnormal
The system should cache the information of all memory horse related classes after startup , stay jvm During the security analysis of the whole process, the information is used to judge whether the memory horse related classes meet the following conditions :
4.3.1) Related classes exist in memory but not in hard disk
4.3.2) The system adds related classes that do not exist after startup
4.3.3) The bytecode of related classes is inconsistent with that after startup
4.3.4)ast Analyze classes with exceptions
5) adopt source->sink The theory of , We should monitor the behavior function triggered by external input , Yes jvm Targeted verification of integrity , Timely conduct safety audit on the memory horse . If we look at the memory horse problem more extensively 、 Compare upload and write jsp、jspx Of webshell act , We can draw a conclusion :
5.1) Hard disk webshell and agent The horse destroyed the hard disk data 、 Tampered with the application logic , It destroys the logical integrity of the original application ( It is recommended to use tamper proof products for security protection )
5.2) Memory horse destroys the logical integrity of application memory ( It is suggested to pass rasp Product protection )
Finally, thank dada for its technical support
Prohibited reproduced
边栏推荐
- Yolov5网络修改教程(将backbone修改为EfficientNet、MobileNet3、RegNet等)
- Use a mask to restrict the input of the qlineedit control
- LxC limits the number of CPUs
- 第十六周作业
- C language practice - binary search (half search)
- Homework of the 16th week
- Installation and use of blue lake
- Uni app - realize the countdown of 60 seconds to obtain the mobile verification code (mobile number + verification code login function)
- C语言猜数字游戏
- Pytorch---使用Pytorch实现U-Net进行语义分割
猜你喜欢
BGP experiment the next day
Alibaba cloud polkit pkexec local rights lifting vulnerability

Document declaration and character encoding
Sword finger offer II 006 Sort the sum of two numbers in the array
Realizing deep learning framework from zero -- Introduction to neural network
Yolov5网络修改教程(将backbone修改为EfficientNet、MobileNet3、RegNet等)

Opencv learning example code 3.2.4 LUT
Exposure X8标准版图片后期滤镜PS、LR等软件的插件

阿里云polkit pkexec 本地提权漏洞
Force buckle 540 A single element in an ordered array
随机推荐
阿里云polkit pkexec 本地提权漏洞
66.qt quick-qml自定义日历组件(支持竖屏和横屏)
Deep understanding of lambda expressions
Www2022 | know your way back: self training method of graph neural network under distribution and migration
Unit testing classic three questions: what, why, and how?
Free drawing software recommended - draw io
Sorted out an ECS summer money saving secret, this time @ old users come and take it away
【leetcode】74. Search 2D matrix
社交媒体搜索引擎优化及其重要性
Pytoch --- use pytoch to realize u-net semantic segmentation
微信小程序 - 实现获取手机验证码倒计时 60 秒(手机号+验证码登录功能)
Sword finger offer II 006 Sort the sum of two numbers in the array
Pytorch-Yolov5从0运行Bug解决:
Hand tear - sort
Lei Jun wrote a blog when he was a programmer. It's awesome
The original author is out! Faker. JS has been controlled by the community..
【leetcode】34. Find the first and last positions of elements in a sorted array
How to solve the code error when storing array data into the database
The core idea of performance optimization, dry goods sharing
C language: examples of logical operation and judgment selection structure