当前位置:网站首页>Top ten information security principles
Top ten information security principles
2022-06-10 23:53:00 【InfoQ】
- Defense in depth
- Application PDCA Model
- The minimum authority rule
- White list mechanism
- Fail safely
- Avoid hiding to achieve security
- The network intrusion detection system is deployed at the network boundary , Analyze network traffic , Identify intrusion .
- The host intrusion detection system is deployed on the server , By analyzing file integrity 、 Network connection activities 、 Process behavior 、 Log string matching 、 Document characteristics, etc , Identify whether an intrusion is taking place , Or determine whether an intrusion has occurred .
- Don't trust infrastructure
- It's safe to deliver by default
边栏推荐
- This article introduces you to j.u.c's futuretask, fork/join framework and BlockingQueue
- Before we learn about high-performance computing, let's take a look at its history
- Yuntu says that every successful business system cannot be separated from apig
- 【LaTex】latex VS Code snippets(代码片段)
- Data and information resource sharing platform (VIII)
- 判等问题:如何确定程序的判断是正确的?
- vtk. VTP download in JS
- Six procurement challenges perplexing Enterprises
- LabVIEW get IMAQ get last event coordinates
- OpenVP*整合ldap認證
猜你喜欢

Serial port missing in Ni Max in LabVIEW
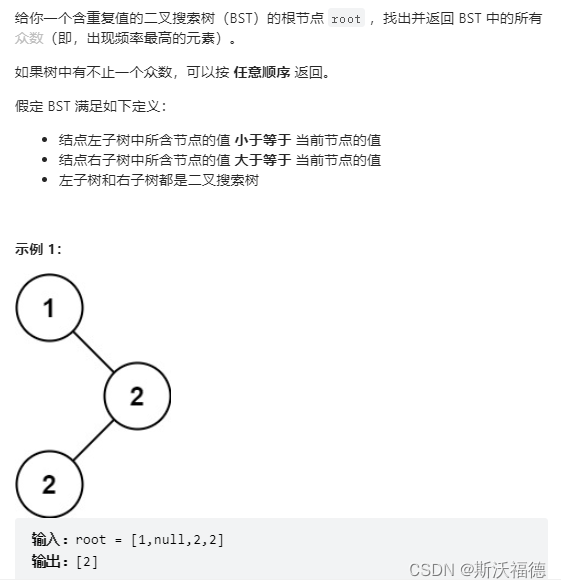
LeetCode 501 :二叉搜索樹中的眾數

LabVIEW锁相环(PLL)

300 questions on behalf of the first lecture on determinant
自制APP连接OneNET---实现数据监控和下发控制(MQTT)

【数学】【连续介质力学】流体力学中的对称张量、应变张量和应力张量

What Fiddler does for testing

IGBT and third generation semiconductor SiC double pulse test scheme

LabVIEW和VDM提取色彩和生成灰度图像
![[paper sharing] pata: fuzzing with path aware Taint Analysis](/img/f6/627344c5da588afcf70302ef29d134.png)
[paper sharing] pata: fuzzing with path aware Taint Analysis
随机推荐
[new version] new pseudo personal homepage v2.0- starze V Club
Fiddler simulates low-speed network environment
LabVIEW中创建毫秒时间标识
vtk. VTP download in JS
宝塔计划任务Shell脚本定时删除某各目录下所有文件【记录】
The data file insurance CSV contains 1338 observations, that is, the registered beneficiaries of the insurance plan and the characteristics that represent the characteristics of patients and the total
What is the workflow of dry goods MapReduce?
Postgraduate entrance examination English vocabulary unit1
Unity script cannot display Chinese comments of C # source code or the script created by vs does not have comments of C # source code
LabVIEW 禁止其他可多核心处理的应用程序在所有核心上执行
Four ways to add names to threads in the thread pool
[untitled]
LabVIEW确定控件在显示器坐标系中的位置
LabVIEW prohibits other multi-core processing applications from executing on all cores
Why many new websites are not included by search engines
The time (in minutes) required for a group of workers to cooperate to complete the assembly process of a part are as follows:
LabVIEW pictures look bright or dark after being cast from 16 bits to 8 bits
30 | how to reset the consumer group displacement?
Build TAR model using beersales data set in TSA package
iframe框架自适应大小/全屏显示网页框架的方法