当前位置:网站首页>[project training] JWT
[project training] JWT
2022-06-12 01:15:00 【par_ ser】
JSON Web Tokens are an open, industry standard RFC 7519 method for representing claims securely between two parties.
The above is jwt Introduction to the official website of , Simply speaking , Use jwt, Can safely transmit information ,jwt Can be verified . In our system ,jwt Mainly used to authorize .
jwt structure
JWT It's made up of three parts , Namely Header、Payload、Signature, Use points in the middle to separate .
JWT The first part It's the head part , It's a description JWT Metadata Json object , Usually as follows .
{
"alg": "HS256",
"typ": "JWT"
}
alg Property indicates the algorithm used for signature , The default is HMAC SHA256( Written as HS256),typ Property indicates the type of token ,JWT Token is uniformly written as JWT.
Last , Use Base64 URL The algorithm will JSON Object to string save .
JWT The second part yes Payload, Also a Json object , In addition to containing the data to be transmitted , There are seven default fields to choose from .
Namely ,iss: The issuer 、exp: Due time 、sub: The theme 、aud: user 、nbf: Not available until 、iat: Release time 、jti:JWT ID Used to identify the JWT.
JWT The third part It's a signature . This is how it was generated , First, you need to specify a secret, The secret Save only in the server , Make sure that other users don't know . And then use Header The specified algorithm pair Header and Payload Calculate , Then you get a signature hash . That is to say Signature.
jwt advantage
Talking about jwt, We often follow the traditional session Scheme comparison ,jwt One obvious advantage of is statelessness , Generally speaking , That is, the server does not need to be specific to each ” Sign in “ Users to store additional information for user authorization . Sent out jwt You don't need to know what it is , It only needs to be parsed according to the established parsing method .( But statelessness is not as beautiful as you think , It also brings many problems , For example, without introducing additional measures , To make a jwt I'm afraid it's difficult to fail , It means , Even if the user logs out , If jwt It's not time to expire , You can still access the interface normally with it )
Besides ,jwt There are other advantages : It has fundamentally prevented CSRF attack (jwt Not like the front end cookie So transparent , You can take jwt Put it in header Carry and send out ), Suitable for mobile applications ( Do not rely on cookie..), Easy to achieve single sign on, etc .
Add dependency
<dependency>
<groupId>io.jsonwebtoken</groupId>
<artifactId>jjwt</artifactId>
<version>0.9.0</version>
</dependency>Create a tool class
Further , To make it easier for us to create jwt, You can define a tool class ( Methods can be defined as follows )
public static String createJWT(String subject, Long ttlMillis,String decodeKey) {
JwtBuilder builder = getJwtBuilder(subject, ttlMillis, getUUID(),decodeKey);// Set expiration time
return builder.compact();
}
private static JwtBuilder getJwtBuilder(String subject, Long ttlMillis, String uuid, String decodeKey) {
SignatureAlgorithm signatureAlgorithm = SignatureAlgorithm.HS256;
SecretKey secretKey = generalKey(decodeKey);
long nowMillis = System.currentTimeMillis();
Date now = new Date(nowMillis);
if(ttlMillis==null){
ttlMillis=JwtUtil.JWT_TTL;
}
long expMillis = nowMillis + ttlMillis;
Date expDate = new Date(expMillis);
return Jwts.builder()
.setId(uuid) // Unique ID
.setSubject(subject) // The theme It can be JSON data
.setIssuer("wodeqianming") // Issuer
.setIssuedAt(now) // The issuance of time
.signWith(signatureAlgorithm, secretKey) // Use HS256 Symmetric encryption algorithm signature , The second parameter is the secret key
.setExpiration(expDate); // Expiration time
}边栏推荐
- In depth description of Weibull distribution (2) meaning of parameters and formulas
- Data visualization big screen - big screen cloud minimalist user manual
- A knowledge map (super dry goods, recommended collection!)
- Virtual human appears on the stage of the Winter Olympic Games, connecting elements of the meta universe
- Lambda中间操作limit
- Lambda termination operation foreach
- 【项目实训】jwt
- Article 3: Design of multifunctional intelligent trunk following control system | undergraduate graduation project - [defense ppt]
- jmeter 性能测试用 csv,这个坑有些扯蛋
- websocket服务器实战
猜你喜欢
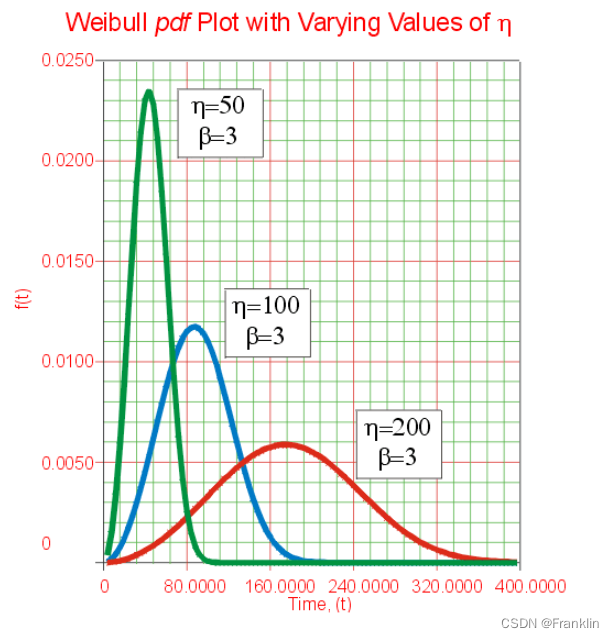
Weibull Distribution韦布尔分布的深入详述(2)参数和公式意义

How can functional tests be quickly advanced in one month? It is not a problem to clarify these two steps

'virtue and art' in the field of recurrent+transformer video recovery
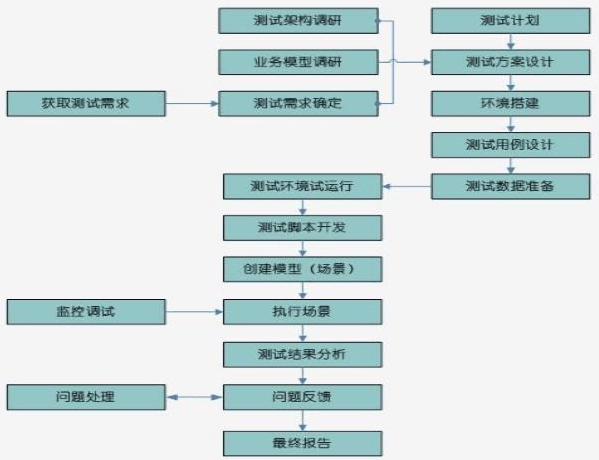
给你一个项目,你将如何开展性能测试工作?

大厂测试员年薪30万到月薪8K,吐槽工资太低,反被网友群嘲?
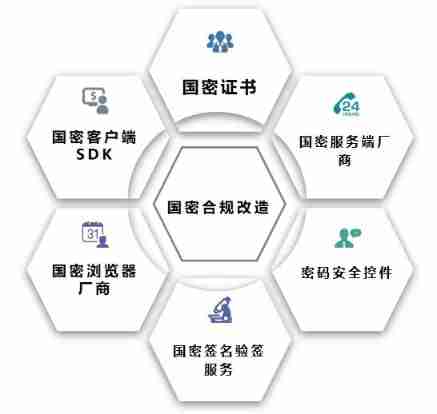
In the field of enabling finance, the transformation of state secrets makes security compliance more solid

Module 8 - Design message queue MySQL table for storing message data

How to guarantee industrial control safety: system reinforcement

Building circuits on glass
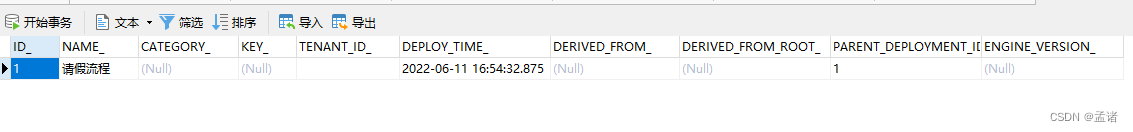
flowable 工作流
随机推荐
Lambda中间操作distinct
I worked as a software testing engineer in a large factory and wrote "one day's complete workflow"
In depth description of Weibull distribution (1) principle and formula
【项目实训】校验注解
Elementary OJ problem of binary tree
一文get,最容易碰上的接口自动化测试问题汇总
Component introduction - large screen cloud minimalist user manual
Defect detection, introduction to Halcon case.
Set up NFT blind box mall system | customized development of NFT mall software
[answer] should the role with one end of the reflexive association be called "current version"
Article 3: Design of multifunctional intelligent trunk following control system | undergraduate graduation project - [defense ppt]
I'm fired because I can only test basic functions····
Lambda中间操作map
Global and Chinese medical styrene block copolymer industry prospect research and investment planning proposal report 2022-2028
C language multidimensional array and pointer - learning 24
Analysis report on operation trends and development strategies of global and Chinese plastic adhesive industry 2022-2028
The CSV used for JMeter performance test is bullshit
Go out with a stream
中创专利|中国5G标准必要专利达1.8万项,尊重知识产权,共建知识产权强国
2022-06-11:注意本文件中,graph不是邻接矩阵的含义,而是一个二部图。 在长度为N的邻接矩阵matrix中,所有的点有N个,matrix[i][j]表示点i到点j的距离或者权重, 而在二部