当前位置:网站首页>“蔚来杯“2022牛客暑期多校训练营2 D.[Link with Game Glitch] 二分答案+SPFA判环
“蔚来杯“2022牛客暑期多校训练营2 D.[Link with Game Glitch] 二分答案+SPFA判环
2022-07-26 01:23:00 【HeartFireY】
D.Link with Game Glitch
题目分析
有 m m m个配方,每个配方可以使用 k × a i k \times a_i k×ai个 b i b_i bi种原料生成 k × c i k \times c_i k×ci个 d i d_i di种原料。现在要求在 k k k上乘一个权值 w w w,使得所有配方间不存在可以循环生成无限物品的局面。要求最大化 m m m。
显然要生成无限物品,需要存在一个环且沿该环生成一轮得到的物品数目比原来更多,即为环上满足所有的边有 k ( c [ i ] − a [ i ] ) > 0 k(c[i] - a[i]) > 0 k(c[i]−a[i])>0即为 k c [ i ] a [ i ] > 1 k\frac{c[i]}{a[i]} > 1 ka[i]c[i]>1。
由于可能存在多个环,我们只需要保证最大环不会循环生成即可。显然可以二分答案来做。
Code
#include <bits/stdc++.h>
//#pragma gcc optimize(2)
#define double long double
#define endl '\n'
using namespace std;
const int N = 2e3 + 10, MOD = 1e9 + 7;
const double EPS = 1e-8;
struct node{
int v; double w; };
vector<node> g[N];
int n, m, cnt[N];
double dis[N];
bitset<N> vis;
bool check(double x){
queue<int> q;
x = -log(x);
vis.set();
memset(dis, 0, sizeof(dis));
memset(cnt, 0, sizeof(cnt));
for(int i = 1; i <= n; i++) q.emplace(i);
while(q.size()){
int u = q.front(); q.pop();
vis.reset(u);
for(auto nxt : g[u]){
int v = nxt.v;
double w = nxt.w;
if(dis[v] > dis[u] + w + x){
dis[v] = dis[u] + w + x;
cnt[v] = cnt[u] + 1;
if(cnt[v] > n) return true;
if(!vis[v]){
q.emplace(v);
vis.set(v);
}
}
}
}
return false;
}
inline void solve(){
cin >> n >> m;
for(int i = 1; i <= m; i++){
int a, b, c, d; cin >> a >> b >> c >> d;
g[b].emplace_back(node{
d, -log((1.0 * c) / a)});
}
double l = 0, r = 1;
for(int i = 1; i <= 300; i++){
double mid = (l + r) / 2;
if(check(mid)) r = mid;
else l = mid;
}
cout << l << endl;
}
signed main(){
ios_base::sync_with_stdio(false), cin.tie(0);
cout << fixed << setprecision(12);
int t = 1; //cin >> t;
while(t--) solve();
return 0;
}
边栏推荐
- B - Krypton Factor(dfs+回溯法)
- Kubernetes Pod启动流程
- 2022年最新北京建筑八大员(材料员)模拟考试试题及答案
- Tutorial on principles and applications of database system (055) -- MySQL query (XVII): usage of mathematical functions
- [software development specification II] prohibited item development specification
- What should I do when my blog is attacked by hackers?
- Handler消息机制-FWK层
- 数据库系统原理与应用教程(057)—— MySQL 练习题
- FreeBSD bNXT Ethernet driver source code reading record 2:
- Web middleware log analysis script 3.0 (shell script)
猜你喜欢

Two stage submission and three stage submission

PtGui pro12 vertical line correction

8、学习MySQL 创建数据表

Detailed explanation of rest assured interface testing framework

zeromq浅析
Leetcode537. 复数乘法(可以,已解决)

What should I do when my blog is attacked by hackers?
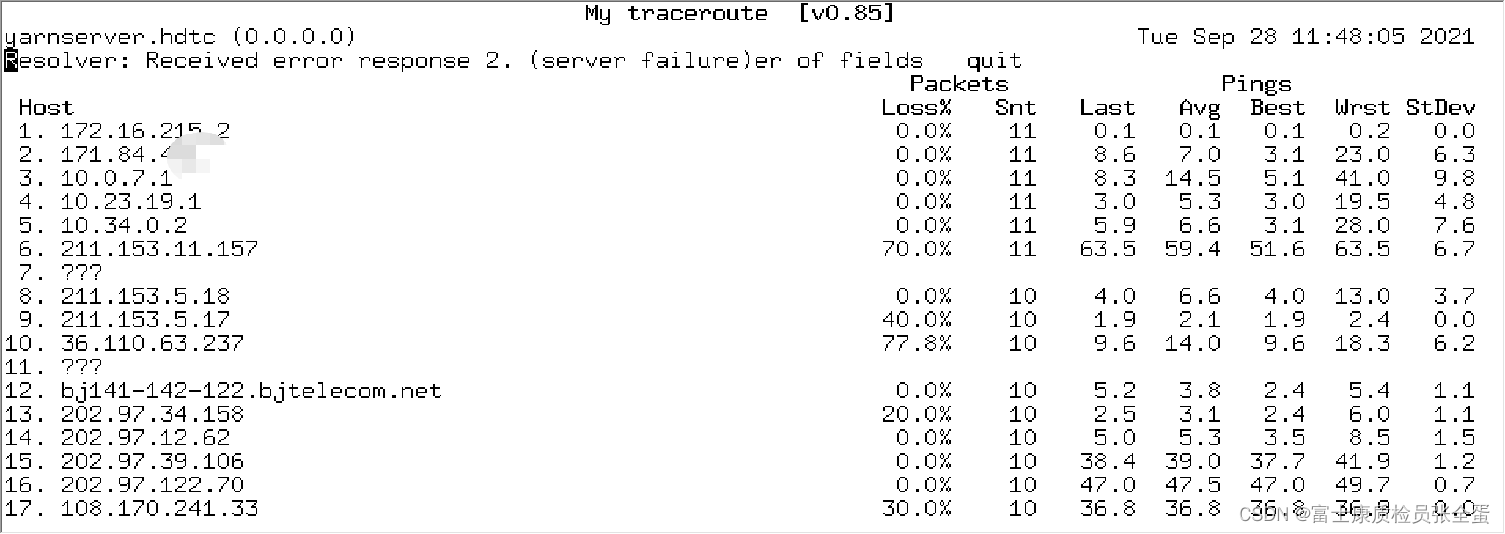
Network performance evaluation tool ping/mtr

网络性能评估工具 ping/mtr

如何获取广告服务流量变现数据,助力广告效果分析?
随机推荐
Docker高级篇-Mysql主从复制
数据库系统原理与应用教程(054)—— MySQL 查询(十六):日期时间型函数的用法
Arthas watch command to view the properties of objects in the array
TV software burning
Zombie's treasure test (enumeration)
Is it safe to buy funds on e fund? Professional answers
[secsha concept] large and small end
Zombie‘s Treasure Chest(枚举)
Game thinking 17: Road finding engine recast and detour learning II: recast navigation grid generation process and limitations
Linear relationship between vectors
2022年最新北京建筑八大员(材料员)模拟考试试题及答案
[go] how to control the maximum number of concurrent processes
B - Krypton Factor(dfs+回溯法)
电视机软件烧录
FastJson 处理泛型
The application and principle of changing IP software are very wide. Four methods of dynamic IP replacement are used to protect network privacy
Tencent employees' salary: the real 985 graduation salary, do you think I can be saved? Netizen: daily salary?
Leetcode537. Complex multiplication (yes, solved)
数据库系统原理与应用教程(057)—— MySQL 练习题
Handler消息机制-FWK层