当前位置:网站首页>C language: bubble sort
C language: bubble sort
2022-06-25 08:45:00 【zbossz】
#define _CRT_SECURE_NO_WARNINGS
#include <stdio.h>
#define N 10
void Bubble_Sort(int* a,int i,int j,int t)
{
for (i = 0;i < N - 1;i++)
{
for (j = 0;j < N - i - 1;j++)
{
if (a[j] > a[j + 1])
{
t = a[j];
a[j] = a[j + 1];
a[j + 1] = t;
}
}
}
}
int main()
{
int i=0, j=0, t=0, a[N];
printf(" Please enter %d It's an integer :",N);
for (i = 0;i < N;i++)
scanf("%d", &a[i]);
Bubble_Sort(a,i,j,t);
for (i = 0;i < N;i++)
printf("%d ", a[i]);
printf("\n");
return 0;
}
flag In order to reduce the number of cycles of the constant sequence , To maximize efficiency .
such as 1111111111 This sequence , Just go in 10 Secondary cycle .
If not flag, I'll go in 100 Secondary cycle . The efficiency is greatly reduced .
边栏推荐
- 微信小程序_7,项目练习,本地生活
- 软件工程复习题
- Nips 2014 | two stream revolutionary networks for action recognition in videos reading notes
- 开户券商怎么选择?在线开户是安全么?
- Prepare these before the interview. The offer is soft. The general will not fight unprepared battles
- Word2vec, phrases, phraser, keyedvectors commonly used in gensim
- 4 reasons for adopting "safe left shift"
- To achieve good software testing results, it is a prerequisite to build a good testing environment
- tp5与tp6的区别是啥呀?
- Find the nearest common ancestor (Sword finger offer) of two nodes in the binary tree (search tree)
猜你喜欢

wav文件(波形文件)格式分析与详解

Exchange:管理日历权限

Scanpy (VII) spatial data analysis based on scanorama integrated scrna seq

About i/o -- the relationship between memory and CPU and disk

How to analyze the coupling coordination index?
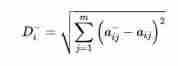
How to calculate the positive and negative ideal solution and the positive and negative ideal distance in TOPSIS method?

The city chain technology platform is realizing the real value Internet reconstruction!

Home server portal easy gate

声纹技术(六):声纹技术的其他应用

Getting to know the generation confrontation network (11) -- using pytoch to build wgan to generate handwritten digits
随机推荐
进击的技术er,遇见实习岗位信息
IC研发常用英文术语缩写
Exchange: manage calendar permissions
How to analyze the grey prediction model?
城鏈科技平臺,正在實現真正意義上的價值互聯網重構!
wav文件(波形文件)格式分析与详解
Can I grant database tables permission to delete column objects? Why?
RTOS 多线程下hardfault问题总结
紧急行政中止令下达 Juul暂时可以继续在美国销售电子烟产品
Is there no risk in the security of new bonds
初识生成对抗网络(12)——利用Pytorch搭建WGAN-GP生成手写数字
声纹技术(六):声纹技术的其他应用
Measure the current temperature
Hyper-v:hyper-v generation 1 or generation 2 virtual machines
故障:Outlook 收发邮件时的 0x800CCC1A 错误
Software engineering review questions
Hyper-v:Hyper-v 第 1 代或第 2 代虚拟机
SharePoint:SharePoint Server 2013 与 ADRMS 集成指南
声纹技术(一):声纹技术的前世今生
On which platform is it safe to buy shares and open an account? Ask for sharing