当前位置:网站首页>LeetCode226. Flip binary tree
LeetCode226. Flip binary tree
2022-07-04 01:26:00 【Qingshan's green shirt】
LeetCode226. Flip binary tree
List of articles
1. problem

2. Ideas
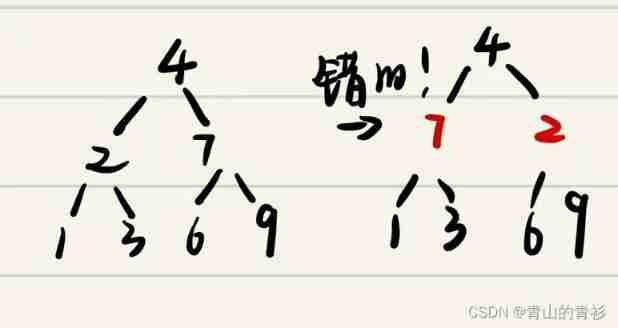
The overall idea is to flip the left and right children of each node , So we need to traverse the binary tree . The focus is on how to traverse the binary tree !
Before the order 、 In the following order 、 Sequence is OK , No middle order , Because some nodes will be exchanged twice !
The next preface is an example :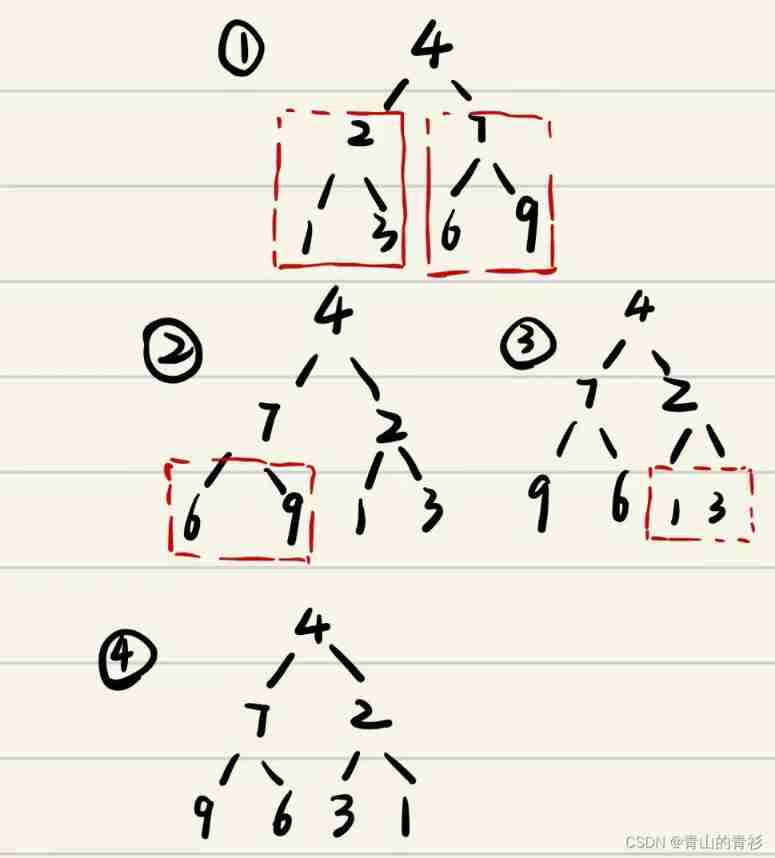
3. Code implementation
(1) recursive
class Solution {
public:
TreeNode* invertTree(TreeNode* root) {
//1. Termination conditions
if(root==NULL) return NULL;
//2. Exchange left and right nodes
TreeNode* tmp=root->left;
root->left=root->right;
root->right=tmp;
//3. Traverse the left and right subtrees
invertTree(root->left);
invertTree(root->right);
return root;
}
};
Be careful :
The code of the exchange node is :
TreeNode* tmp=root->left; root->left=root->right; root->right=tmp;
Or use swap function !!!
swap(root->left, root->right);
Error code :
This is wrong !
Only the values of some two nodes are exchanged , Without completely inverting the entire subtree !TreeNode *tmpNode = new TreeNode();// Create a new nodetmpNode->val = root->right->val;// Exchange valueroot->right->val = root->left->val;root->left->val = tmpNode->val;
For example, the first step is completed , It becomes as shown in the figure below :
(2) iteration
class Solution {
public:
TreeNode* invertTree(TreeNode* root) {
stack<TreeNode*>st;
if(root == NULL) return root;
st.push(root);// The root node is in the stack !
while(!st.empty())// Stack is not empty
{
TreeNode* node = st.top();// The pointer points to the top node of the stack // in
st.pop();// Out of the stack
swap(node->left, node->right);
if(node->right) st.push(node->right);// The right son enters the stack !( Empty nodes do not stack )
if(node->left) st.push(node->left);// Left son into the stack !( Empty nodes do not stack )
}
return root; // The stack is empty. , end
}
};
边栏推荐
- MySQL -- Introduction and use of single line functions
- Future源码一观-JUC系列
- 关于 uintptr_t和intptr_t 类型
- ThinkPHP uses redis to update database tables
- Cloud dial test helps Weidong cloud education to comprehensively improve the global user experience
- 7.1 学习内容
- AI 助力艺术设计抄袭检索新突破!刘芳教授团队论文被多媒体顶级会议ACM MM录用
- Summary of JWT related knowledge
- 51 single chip microcomputer timer 2 is used as serial port
- GUI 应用:socket 网络聊天室
猜你喜欢

51 MCU external interrupt
Audio resource settings for U3D resource management
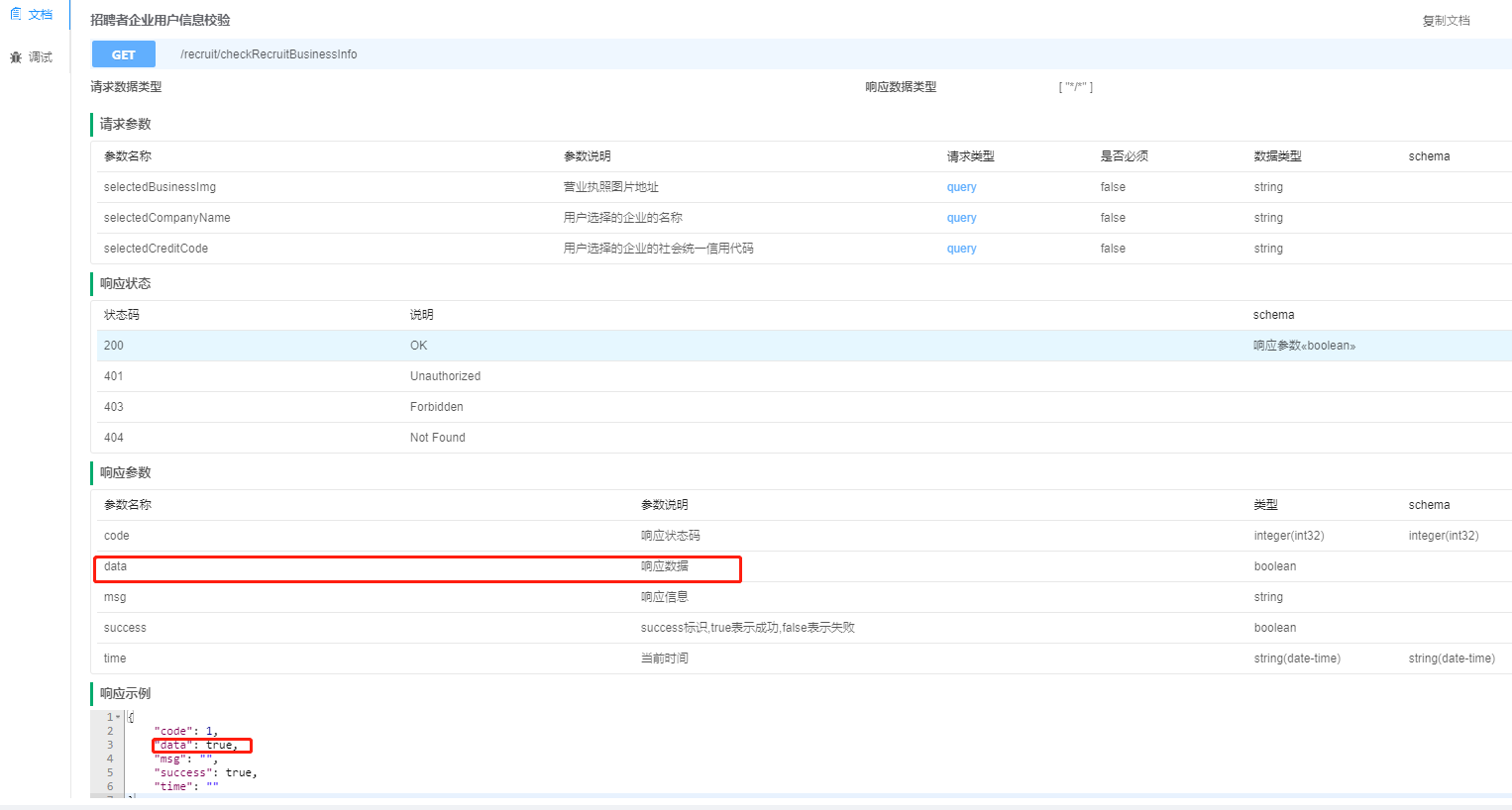
swagger中响应参数为Boolean或是integer如何设置响应描述信息
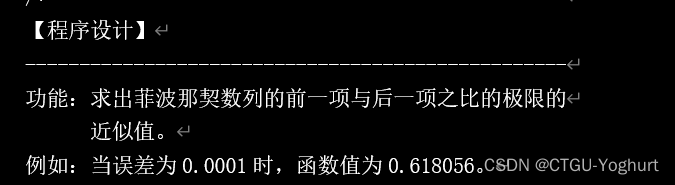
Function: find the approximate value of the limit of the ratio of the former term to the latter term of Fibonacci sequence. For example, when the error is 0.0001, the function value is 0.618056.
Install the pit that the electron has stepped on

Windos10 reinstallation system tutorial

A-Frame虚拟现实开发入门

How to use AHAS to ensure the stability of Web services?

Technical practice online fault analysis and solutions (Part 1)

String hash, find the string hash value after deleting any character, double hash
随机推荐
How can enterprises optimize the best cost of cloud computing?
Gauss elimination method and template code
Decompile and modify the non source exe or DLL with dnspy
Mongodb learning notes: command line tools
Ka! Why does the seat belt suddenly fail to pull? After reading these pictures, I can't stop wearing them
Function: find the sum of the elements on the main and sub diagonal of the matrix with 5 rows and 5 columns. Note that the elements where the two diagonals intersect are added only once. For example,
It's OK to have hands-on 8 - project construction details 3-jenkins' parametric construction
Idsia & supsi & usi | continuous control behavior learning and adaptive robot operation based on Reinforcement Learning
Future源码一观-JUC系列
Meta metauniverse female safety problems occur frequently, how to solve the relevant problems in the metauniverse?
How to use AHAS to ensure the stability of Web services?
51 MCU external interrupt
Sequence list and linked list
Summary of common tools and technical points of PMP examination
Long article review: entropy, free energy, symmetry and dynamics in the brain
Skku| autonomous handover decision of UAV Based on deep reinforcement learning
Day05 表格
关于 uintptr_t和intptr_t 类型
基于.NetCore开发博客项目 StarBlog - (14) 实现主题切换功能
1-Redis架构设计到使用场景-四种部署运行模式(上)