当前位置:网站首页>Vulhub vulnerability recurrence 72_ uWSGI
Vulhub vulnerability recurrence 72_ uWSGI
2022-07-06 05:19:00 【Revenge_ scan】
One 、 CVE-2018-7490_ uWSGI PHP Directory traversal vulnerability
Preface
uWSGI Is a Web Application server , It has achieved WSGI、uwsgi and http Such agreement , And support to run various languages through plug-ins .
Vulnerability Details
uWSGI 2.0.17 Previous PHP plug-in unit , There is no right way to deal with `DOCUMENT_ROOT` testing , So that users can pass `..%2f` To cross directories , Read or run `DOCUMENT_ROOT` Files outside the directory .
Vulnerability environment
shooting range :192.168.4.10_Ubuntu
Run flawed uWSGI The server :
#docker-compose up -d
After completion of operation , visit `http://your-ip:8080/` You can see phpinfo Information , explain uwsgi-php The server has run successfully .
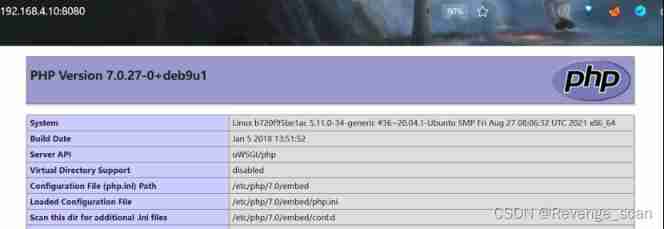
Loophole recurrence
visit `http://your-ip:8080/..%2f..%2f..%2f..%2f..%2fetc/passwd`, Successfully read file :
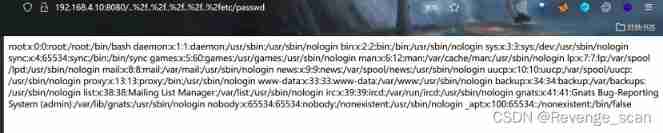
Two 、 uWSGI Unauthorized access vulnerability
Preface
uWSGI Is a Web Application server , It has achieved WSGI、uwsgi and http Such agreement , And support to run various languages through plug-ins , Usually used to run Python WEB application .uwsgi In addition to the name of the application container , It and Fastcgi Something like that , It's also the front end server A communication standard with the back-end application container . at present nginx,apache Also support uwsgi The protocol forwards requests by proxy .
Vulnerability Details
uWSGI Support through magic variables (Magic Variables) Dynamically configure the backend Web application . If its port is exposed , An attacker can construct uwsgi Data packets , And specify magic variables `UWSGI_FILE`, Application `exec://` The protocol executes arbitrary commands .
Reference link :
- https://github.com/wofeiwo/webcgi-exploits/blob/master/python/uwsgi-rce-zh.md
- https://xz.aliyun.com/t/3512
- https://uwsgi-docs.readthedocs.io/en/latest/Vars.html
Vulnerability environment
Execute the following command to start nginx+uwsgi Environmental Science :
#docker-compose up -d
After the environment starts , visit `http://your-ip:8080` You can view one Web application , Its uwsgi Exposure to the 8000 port .
Loophole recurrence
Use [poc.py](poc.py), Carry out orders `python poc.py -u your-ip:8000 -c "touch /tmp/success"`:
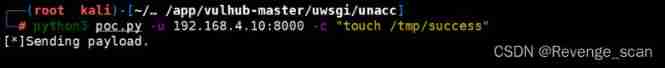
perform `docker-compose exec web bash` Into the container , so `/tmp/success` Has successfully executed :

边栏推荐
- Review of double pointer problems
- Three.js学习-光照和阴影(了解向)
- 01. 开发博客项目之项目介绍
- Implementing fuzzy query with dataframe
- js Array 列表 实战使用总结
- 图数据库ONgDB Release v-1.0.3
- Vulhub vulnerability recurrence 67_ Supervisor
- GAMES202-WebGL中shader的编译和连接(了解向)
- Fluent implements a loadingbutton with loading animation
- C Advanced - data storage (Part 1)
猜你喜欢
GAMES202-WebGL中shader的编译和连接(了解向)
Vulhub vulnerability recurrence 69_ Tiki Wiki
Vulhub vulnerability recurrence 71_ Unomi
你需要知道的 TCP 三次握手
Postman manage test cases
Implementing fuzzy query with dataframe
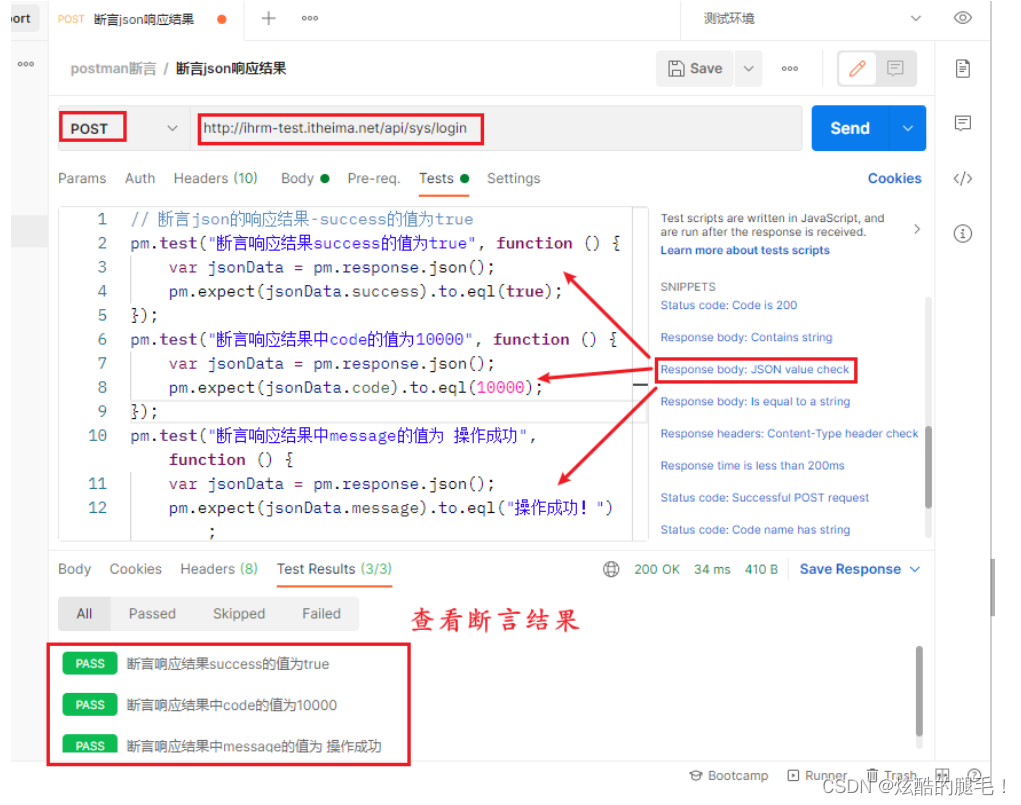
Postman assertion
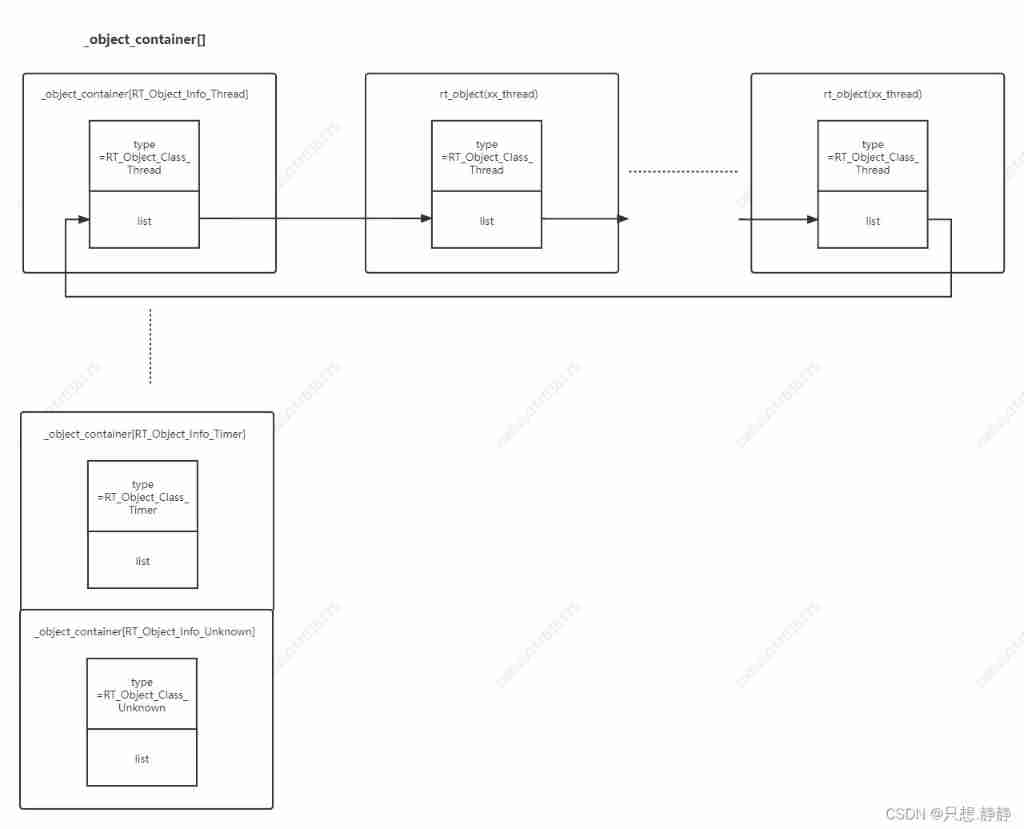
RT thread analysis - object container implementation and function
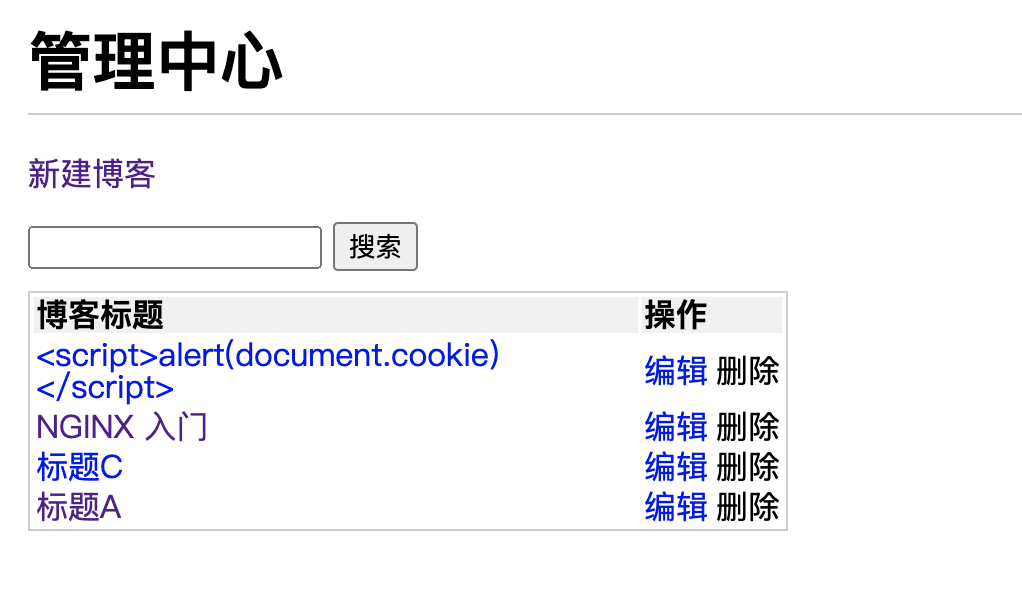
05. 博客项目之安全

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
随机推荐
Tetris
Three.js学习-光照和阴影(了解向)
SQLite queries the maximum value and returns the whole row of data
Ad20 is set with through-hole direct connection copper sheet, and the bonding pad is cross connected
2022 half year summary
C AES encrypts strings
[leetcode16] the sum of the nearest three numbers (double pointer)
02. 开发博客项目之数据存储
What are the advantages of the industry private network over the public network? What specific requirements can be met?
Solution of QT TCP packet sticking
Easy to understand I2C protocol
03. 开发博客项目之登录
Extension of graph theory
ByteDance program yuan teaches you how to brush algorithm questions: I'm not afraid of the interviewer tearing the code
js Array 列表 实战使用总结
[noip2009 popularization group] score line delimitation
Codeforces Round #804 (Div. 2)
Codeforces Round #804 (Div. 2) Editorial(A-B)
Simple understanding of interpreters and compilers
Postman pre script - global variables and environment variables