当前位置:网站首页>PKCs 5: password based cryptography specification version 2.1 Chinese Translation
PKCs 5: password based cryptography specification version 2.1 Chinese Translation
2022-07-04 12:16:00 【Johnny Zhou】
PKCS#5 Password based encryption specification V2.1
Abstract :
This document provides suggestions for implementing password based encryption , Including key derivation functions 、 Encryption scheme 、 Message verification scheme and ASN.1 Grammar recognition technology .
This document is RSA Laboratory public key cryptography standard (PKCS) In the series PKCS #5 v2.1 Reprint of . adopt RFC Release , Change control is transferred to IETF.
The document is also abolished RFC 2898.
Memo status
This document is not Internet Standard tracking specification ; It was published to provide information .
This document is IETF (Internet Engineering Task Force) Products . It represents the IETF Group consensus . It has been subjected to public scrutiny , And has been approved by the Internet Engineering Steering Group (IESG) Approved for publication . Not all classics IESG Approved documents can be used for any level of Internet Standards ; See RFC 7841 The first 2 section .
About the current status of this document 、 Any errata and information on how to provide feedback , Available at
http://www.rfc-editor.org/info/rfc8018.
Table of contents Catalog
1 Introduction Introduce
2 Notations Symbol
3 Overview summary
4 Salt and Iteration count Salt And the number of iterations
4.1 Salt
4.2 Iteration Count The number of iterations
5 Key Derivation Functions Key derivation function
5.1. PBKDF1
5.2 PBKDF2
6 Encryption Schemes Encryption scheme
6.1. PBES1
6.1.1. PBES1 Encryption Operation PBES1 Encryption operation
6.1.2. PBES1 Decryption Operation PBES1 Decryption operation
6.2. PBES2
6.2.1. PBES2 Encryption Operation PBES2 Encryption operation
6.2.2. PBES2 Decryption Operation PBES2 Decryption operation
7. Message Authentication Schemes Message authentication scheme
7.1. PBMAC1
7.1.1. PBMAC1 Generation Operation PBMAC1 Build operation
8. Security Considerations Safety precautions
1 Introduction Introduce
This document provides suggestions for implementing password based cryptography , Including the following aspects :
Key derivation function
Encryption scheme
Message authentication scheme
ASN.1 Grammar recognition technology
These suggestions are intended to be widely used in computer and communication systems , Therefore, it has considerable flexibility . They are especially used to protect sensitive information , Such as pkcs# 8 [PKCS8] [RFC5958] The private key . It is expected that application standards and implementation profiles based on these specifications may include additional constraints .
2 Notations Symbol
C Ciphertext , A byte string
c Iteration count , A positive integer
DK Derived key , A string in bytes
dkLen The byte length of the derived key , A positive integer
EM Encoded message , A string in bytes
Hash As described below Hash function
hLen The byte length of the output of the pseudo-random function , A positive integer
l The block length of the derived key , As a positive integer
IV Initialization vector , Byte unit string
K Encryption key , Byte unit string
KDF Key derivation function
M news , Byte unit string
P password , Byte unit string
PRF The pseudo-random number function described below
PS Fill string , Byte unit string
S Salt random number , Byte unit string
T Message verification code , Byte string
T_1, …, T_l, U_1, …, U_c In the middle , Byte string
01, 02, …, 08 The byte value is 1,2,…, 8
\xor Bitwise exclusive or of a two byte string
|| || Byte body length operator
|| Connector
<i…j> Substring extraction operator : Extract bytes from I To j,0 <= I <= j.
3 Overview summary
In many public key encryption applications , User security ultimately depends on one or more secret text values or passwords .
however , Because the password is not a key directly applicable to any traditional cryptographic system , Therefore, the password needs some processing before it can be used to perform encryption operations . Besides , Because passwords are usually selected from a relatively small space , Therefore, special care should be taken in the process , To prevent search attacks .
Another cryptology method based on password is to construct relatively expensive key derivation Technology , Thus increasing the cost of exhaustive search . One method is to include iteration counting in the key derivation Technology , Indicates how many times an underlying function of the derived key should be iterated . Moderate number of iterations ( such as 1000 Time ) It is unlikely to be a burden to the legitimate party when calculating the key , But it will be a great burden for opponents .
Salt And iteration count constitute PKCS #5 v2.0 The basis of password based encryption in , It is also used for various encryption operations . therefore , The password based key derivation defined here is password 、Salt And iteration counting function , The last two numbers need not be kept secret .
Through password based key derivation function , Password based encryption and message authentication schemes can be easily defined . stay PKCS #5 v2.0 in , The password based encryption scheme here is based on an underlying conventional encryption scheme ,
among , The key of the conventional scheme comes from the password . Similarly , Password based message authentication scheme is a conventional scheme based on the bottom . This two-tier approach modularizes password based technology , Because they can be based on underlying technology .
It is hoped that the password based key derivation function can find other applications besides the encryption and message authentication schemes defined here . for example , One possibility is to derive a set of keys through the application of a key derivation function , Instead of deriving each key from a function in each individual application . The key in the collection will be obtained as a substring output by the key derivation function . In session oriented protocols , This method can be used as part of key establishment . Another application is password checking , Where the output of the key derived function is stored ( as well as Salt And iteration count ), So that the password can be verified later .
Throughout the document , A password is considered to be a byte string of arbitrary length , The interpretation of its text string is unspecified . However , For interoperability , It is recommended that applications follow some general text coding rules .
ASCII and UTF-8 [RFC3629] There are two possibilities .(ASCII yes UTF-8 Subset .)
Although the choice of password is beyond the scope of this document , But the guidelines that have been released [NISTSP63] May be taken into account .
4 Salt and Iteration count Salt And the number of iterations
because Salt And iteration counting are the core of the technology defined in this article , Therefore, further discussion is necessary .
4.1 Salt
In password based cryptography ,Salt Traditionally, it is used to generate a set of keys corresponding to a given password , according to Salt Randomly select one of the keys . Derive functions by applying keys KDF Select a key in the set , Such as
DK = KDF (P, S)
among DK Is derived key ,P Is password ,S by salt.
There are two advantages :
1. It is difficult for the opponent to calculate all the keys corresponding to the password dictionary in advance , Even the most likely key . for example , If salt The length is 64 position , Then each password will have up to 2^64 Key . therefore , After performing password based operations and knowing the password salt after , Opponents can only search for passwords .
2. The same key is unlikely to be selected twice . Again , According to the birthday paradox , If Salt yes 64 Bit length , Between keys “ Collision ” The probability will not become significant , Until about 2^32 Key generation . The fact that conflicts are unlikely to occur solves some problems of interaction between multiple uses of the same key that may occur when using some encryption and authentication technologies .
In password based encryption , The party that encrypts the message can ensure , Just choose a large one when deriving the encryption key from the password 、 Random enough salt, These benefits can be realized . The party that generates the message authentication code can obtain this guarantee in a similar way .
However , The party that decrypts the message or verifies the message verification code cannot confirm that it is provided by the other party Salt It's actually randomly generated . for example ,Salt It may be copied from another password based operation , The purpose is to use the interaction between multiple uses of the same key . for example , Suppose two legitimate parties exchange encrypted messages , The encryption key is a 80 A key , Derived from a with some Salt Shared password . Opponents can get information from encryption , And provide it to one party , Like it's a 40 Bit key . If one party discloses the use 40 Result of bit key decryption , The other party may be able to solve 40 A key . stay 40 The bit key is 80 In the case of the first half of the bit key , Opponents can easily find 80 The remainder of the bit key 40 position .
To guard against such attacks , Or you should carefully analyze the interaction between multiple uses of the same key , or salt It should contain data that clearly distinguishes between different operations . for example ,salt There may be an extra 、 Non random bytes , Used to specify that the derived key is used for encryption 、 Message authentication , Or for other operations .
Based on this , Recommend the following Salt choice :
1. If you don't pay attention to the interaction between multiple users using the same key ( Or key prefix ) Password encryption and authentication technology support for a given password , Then randomly generated Salt The specific format of may not be required by Salt The receiver checks . It should have at least 8 Bytes (64 position ) Long .
2. otherwise ,Salt It should contain data that clearly distinguishes between different operations and different key lengths , There is another at least 8 Byte long random part , receive Salt The party should check or regenerate the data . for example ,salt There can be an extra non random byte , Used to specify the purpose of the derived key . perhaps , It can be an encoding that specifies the structure of details about the derived key , For example, encryption or authentication technology , And serial numbers between different keys derived from passwords . The specific format of the additional data is left to the application .
Be careful : If the random number generator or pseudo-random generator is not available , Used to generate salt( Or its random part ) A deterministic alternative to is for passwords and messages to be processed M Apply password based key derivation functions . for example ,Salt You can calculate and derive functions with a key S = KDF (P、M). This method is not recommended if the message M It belongs to a small message space ( for example ,“ yes ” or “ no ”), however , Since then, there may only be a few Salt.
4.2 Iteration Count The number of iterations
Iteration counting is usually used to increase the cost of generating keys from passwords , Therefore, it will also increase
The difficulty of the attack . Mathematically speaking ,c The number of iterations will increase the security strength of the password log2 position , To resist attempt based attacks , Such as brute force cracking or dictionary attack .
Choosing a reasonable value for the iteration count depends on the environment and the specific situation , And it varies by application . This document follows FIPS special publications 800-132 [NISTSP132] Recommendations made in
As long as the user can accept the time required to generate the key with the entered password , The number of iterations should be as large as possible .[… The recommended minimum number of iterations is 1000 Time . For particularly critical keys , Or for very powerful systems , Or user perceived performance is not a critical system ,10,000,000 The iteration count of may be appropriate .
5 Key Derivation Functions Key derivation function
The key derivation function generates a derived key from the basic key and other parameters . In a password based key derivation function , The basic key is the password , Other parameters are salt Value and iteration count , As the first 3 Section .
The main application of the password based key derivation function defined here is in the 6 Encryption scheme of section and and section 7 The message authentication scheme in section . Of course, you can also use other applications , Therefore, these functions can be defined independently .
This section specifies two functions :PBKDF1 and PBKDF2.PBKDF2 Recommended for new applications ;PBKDF1 Only compatible with existing applications , Not recommended for new applications .
A typical application of the key derivation function defined here may include the following steps :
1. choice salt S And iteration count c, As the first 4 Section .
2. Is derived key dkLen Select the length in bytes .
3. Apply the key derivation function to the password 、Salt、 Iteration count and key length , To generate a derived key .
4. Output derived keys .
Any number of keys can be changed salt Then derived from the password , As the first 3 Section .
5.1. PBKDF1
PBKDF1 Use hash function MD2 [RFC1319]、MD5 [RFC1321] or SHA-1 [NIST180] To derive the key . The length of the derived key is limited by the length of the hash function output ,MD2 and MD5 by 16 Bytes ,SHA-1 by 20 Bytes .PBKDF1 And PKCS# 5 v1.5 [PKCS5_15] The key derivation process in is compatible .
because PBKDF1 The generated key may not be large enough for some applications , So it is only recommended to be compatible with existing applications .
PBKDF1 (P, S, c, dkLen)
Options: Hash underlying hash function
Input: P password, an octet string
S salt, an octet string
c iteration count, a positive integer
dkLen intended length in octets of derived key, a positive integer, at most 16 for MD2 or MD5 and 20 for SHA-1
Output: DK derived key, a dkLen-octet string.
Steps:
- If dkLen > 16 for MD2 and MD5, or dkLen > 20 for SHA-1, output “derived key too long” and stop.
- Apply the underlying hash function Hash for c iterations to the concatenation of the password P and the salt S, then extract the first dkLen octets to produce a derived key DK:
T_1 = Hash (P || S) ,
T_2 = Hash (T_1) ,
…
T_c = Hash (T_{c-1}) ,
DK = T_c<0…dkLen-1>
3. Output the derived key DK.
5.2 PBKDF2
PBKDF2 Apply a pseudo-random function ( See Appendix B.1 An example of ) To derive the key . The length of the derived key is basically borderless .( However , The maximum effective search space of the derived key may be limited by the structure of the underlying pseudo-random function . See Appendix for details B.1.) For new applications , It is recommended to use PBKDF2.
PBKDF2 (P, S, c, dkLen)
Options: PRF underlying pseudorandom function (hLen denotes the length in octets of the
pseudorandom function output)
Input: P password, an octet string
S salt, an octet string
c iteration count, a positive integer
dkLen intended length in octets of the derived
key, a positive integer, at most (2^32 - 1) * hLen
Output: DK derived key, a dkLen-octet string
Steps:
1. If dkLen > (2^32 - 1) * hLen, output “derived key too long” and stop.
2. Let l be the number of hLen-octet blocks in the derived
key, rounding up, and let r be the number of octets in the
last block:
l = CEIL (dkLen / hLen)
r = dkLen - (l - 1) * hLen
Here, CEIL (x) is the “ceiling” function, i.e., the smallest integer greater than, or equal to, x.
3. For each block of the derived key apply the function F
Defined below to the password P, the salt S, the iteration count c,and the block index to compute the block:
T_1 = F (P, S, c, 1),
T_2 = F (P, S, c, 2),
…
T_l = F (P, S, c, l),
where the function F is defined as the exclusive-or sum of the
first c iterates of the underlying pseudorandom function PRF
applied to the password P and the concatenation of the salt S
and the block index i:
F (P, S, c, i) = U_1 \xor U_2 \xor … \xor U_c
where
U_1 = PRF (P, S || INT (i)),
U_2 = PRF (P, U_1),
…
U_c = PRF (P, U_{c-1}).
Here, INT (i) is a four-octet encoding of the integer i,
most significant octet first.
4. Concatenate the blocks and extract the first dkLen octets to produce a derived key DK:
DK = T_1 || T_2 || … || T_l<0…r-1>
5. Output the derived key DK.
Be careful : function F The construction of the model follows “ Belts and slings ” Methods . iteration U_i Will recursively calculate , To eliminate the parallelism of opponents ; They are exclusive , To reduce the worry that recursive values degenerate into a small set .
6 Encryption Schemes Encryption scheme
In symmetry settings , The encryption scheme consists of encryption operation and decryption operation , The encryption operation key encrypts the message to generate a ciphertext , The key with the same decryption operation decrypts the ciphertext recovery message . In password based encryption scheme , The password is the password .
The typical application of password based encryption scheme is a private key protection method , The message contains private key information , Such as PKCS#8. The encryption scheme defined here will be the appropriate encryption algorithm in this context .
This section specifies two scenarios :PBES1 and PBES2.PBES2 Suitable for new applications ;PBES1 Only for compatibility with existing applications , Not recommended for new applications .
6.1. PBES1
PBES1 Combined with the PBKDF1 function ( chapter 5.1) And the underlying block cipher , The block password should be DES [NIST46] or RC2 [RFC2268]
Recommended PBES1 Just for compatibility with existing applications , Because it only supports two underlying encryption schemes , The key size of each scheme (56 or 64 position ) It may not be large enough for some applications .
6.1.1. PBES1 Encryption Operation PBES1 Encryption operation
PBES1 The encryption operation of includes the following steps , Use the password P For messages M To encrypt , Generating ciphertext C:
1. choice 8 Bytes of Salt S And iteration count c, As the first 4 Section .
2. take PBKDF1 Key derivation function ( The first 5.1 section ) Apply to passwords P、Salt S And iteration count c, Generate a length of 16 Derived key of bytes DK:
DK = PBKDF1 (P, S, c, 16)
3. The derived key DK Split into DK The first eight bytes of the encryption key K And initialization vector composed of the last eight bytes IV:
K = DK<0…7>,IV = DK<8…15>
4. take M And fill string PS Connect , Form a coded message EM:
EM = M || PS
Fill string PS By value 8-(||M|| mod 8), Number of bytes 8-(||M|| mod 8) form . Fill string PS One of the following statements will be satisfied :
PS = 01, if ||M|| mod 8 = 7;
PS = 02 02, if ||M|| mod 8 = 6;
…
PS = 08 08 08 08 08 08 08 08, if ||M|| mod 8 = 0.
The octet length of the encoded message will be 8 Multiple , And the message can be explicitly recovered from the encoded message M.( This fill rule comes from RFC1423 [RFC1423].)
5. Encrypt encoded information EM With the underlying block password (DES or RC2) stay CBC Mode encryption key and initialization vector K IV Produce ciphertext C, about DES, It should be treated as a key 64 position K Coded 56 position , Key with parity bit ignored ( see [NIST46]). about RC2,“ Valid key bits ” Should be 64 position .
6. Output ciphertext C.
Salt S And iteration count c It can be passed to the party performing decryption in the algorithm identifier value ( See appendix A.3).
6.1.2. PBES1 Decryption Operation PBES1 Decryption operation
PBES1 The decryption operation of includes the following steps , Decrypt password P Ciphertext under C, Recover message M:
1. Get eight syllable Salt S And iteration count c.
2. take PBKDF1 Key derivation function ( The first 5.1 section ) Apply to password P、 salt S And iteration count c, Generate a length of 16 Derived key of bytes DK:
DK = PBKDF1 (P, S, c, 16)
3. The key to be exported DK Split into DK The first eight bytes of the encryption key K And initialization vector composed of the last eight bytes IV:
K = DK<0…7>,IV = DK<8…15>
4. Decrypt the ciphertext C With the underlying block password (DES or RC2) stay CBC Encryption key in mode K And initialization vectors IV Coding information recovery . If the byte length of the ciphertext C No 8 Multiple , Output “ Decryption error ” And stop .
5. The encoded message EM Separate into messages M And fill string PS: EM = M || PS
6. Output the recovered message M:
6.2. PBES2
PBES2 Combined with a password based key derivation function , For this version PKCS #5, It should be PBKDF2(5.2 section ), And an underlying encryption scheme ( See Appendix for example B.2). The key length and any other parameters of the following encryption scheme depend on the scheme .
For new applications , It is recommended to use PBES2
6.2.1. PBES2 Encryption Operation PBES2 Encryption operation
PBES2 The encryption operation of includes the following steps , Apply the selected key derivation function KDF And the selected underlying encryption scheme , Use the password P For messages M To encrypt , Generating ciphertext C:
1. choice salt S And iteration count c, As the first 4 Section .
2. Select the length in bytes for the derived key of the encryption scheme dkLen.
3. Apply the selected key derivation function to the password P、 salt S And the number of iterations c, The generation length is dkLen Derived key of bytes DK: DK = KDF (P, S, c, dkLen)
4. Use the underlying encryption scheme to derive the key DK Next, encrypt the message M, Generating ciphertext c( This step may involve the selection of parameters , Such as initialization vector and filling , Depends on the underlying solution ).
5. Output encrypted message C.
Salt S、 Iteration count c、 Key length dkLen、 The identifier of the key derivation function and the underlying encryption scheme can be passed to the party performing decryption with the value of the algorithm identifier ( See Appendix A.4).
6.2.2. PBES2 Decryption Operation PBES2 Decryption operation
PBES2 The decryption operation of includes the following steps , Decrypt password P Ciphertext under C, Recover message M:
1. Get what you need for the operation Salt S.
2. Get the iteration count of the key derivation function c.
3. Obtain the key length in bytes for the derived key of the basic encryption scheme dkLen.
4. Apply the selected key derivation function to the password P、Salt S And the number of iterations c, The generation length is dkLen Derived key of bytes DK: DK = KDF (P, S, c, dkLen)
5. With derived key DK The low-level encryption scheme under C To decrypt , Recover message m. If the decryption function outputs “ Decryption error ”, The output “ Decryption error ” And stop .
6. Output recovery message M.
7. Message Authentication Schemes Message authentication scheme
The message authentication scheme includes MAC (message authentication Code) Generate operations and MAC Verify operation , among MAC The generate operation generates a... From the message according to a key MAC, MAC The verification operation uses the same key to verify the message . In password based message authentication scheme , The key is the password .
This section only introduces one scheme :PBMAC1.
7.1. PBMAC1
PBMAC1 Combined with a password based key derivation function , For this version PKCS #5, The function should be PBKDF2( The first 5.2 section ), And an underlying message verification scheme ( See Appendix B.3 Example in ). The key length and any other parameters of the message authentication scheme depend on the scheme .
7.1.1. PBMAC1 Generation Operation PBMAC1 Build operation
PBMAC1 Of MAC The generation operation includes the following steps , The password is P The news of M To deal with , Generate message verification code T, Apply the selected key derivation function KDF And the selected underlying message verification scheme :
1. choice salt S And iteration count c, As the first 4 Section .
2. Select the key length in bytes for the derived key of the underlying message authentication function dkLen.
3. Apply the selected key derivation function to the password P、Salt S And the number of iterations c, The generation length is dkLen Derived key of bytes DK:
4. With derived key DK The bottom message authentication scheme under M To deal with , Verification message verification code T.
5. If the message verification code is verified , The output “ correct ”; Others output “ Incorrect ”.
8. Security Considerations Safety precautions
The security that password based cryptography can provide is usually limited , Especially for those methods that can perform offline password search as defined in this document . although salt The use of and iteration count will increase the complexity of the attack ( Please refer to the first 4 Section ), But the proper choice of password is necessary , And relevant guidelines should be considered ( for example ,[NISTSP63]). Equally important is when storing passwords , Protect the password .
Usually , For different purposes , Different keys should be derived from the password , To minimize the possibility of accidental interaction . For password based encryption using a single algorithm , A random Salt It is enough to ensure that different keys will be generated . In some cases , As the first 4 Section , structure Salt be necessary . therefore , In the choice Salt Value should be taken into account in 4 Recommendations in Section .
of MD2 [RFC1319] Information on safety precautions , Please see the [RFC6149];MD5 [RFC1321], see [RFC6151];SHA-1 [NIST180] See [RFC6194].
边栏推荐
- VPS installation virtualmin panel
- Possible to restore a backup of SQL Server 2014 on SQL Server 2012?
- [Chongqing Guangdong education] National Open University spring 2019 2727 tax basis reference questions
- The frost peel off the purple dragon scale, and the xiariba people will talk about database SQL optimization and the principle of indexing (primary / secondary / clustered / non clustered)
- Force buckle 142 Circular linked list II
- Local MySQL forget password modification method (Windows) [easy to understand]
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 7
- Test question bank management system - database design [easy to understand]
- World document to picture
- thread
猜你喜欢
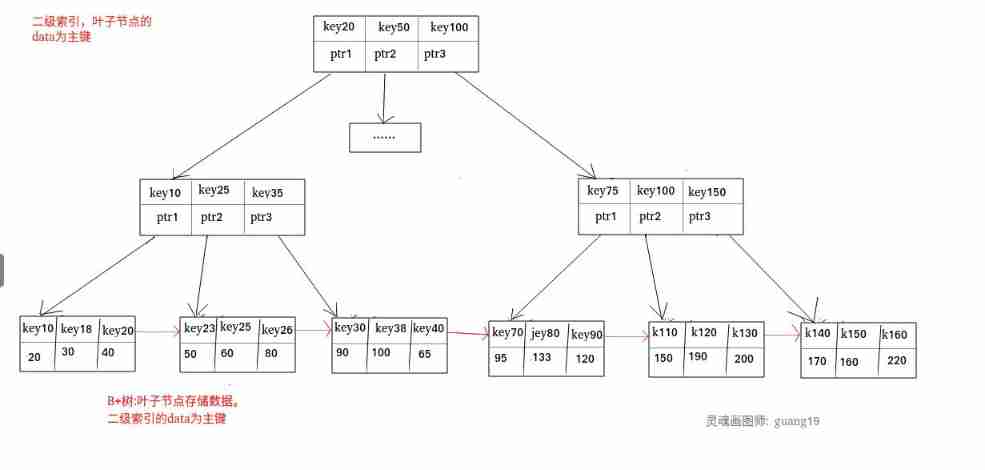
MySQL advanced review
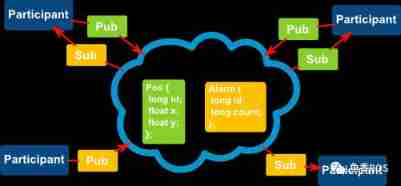
DDS-YYDS
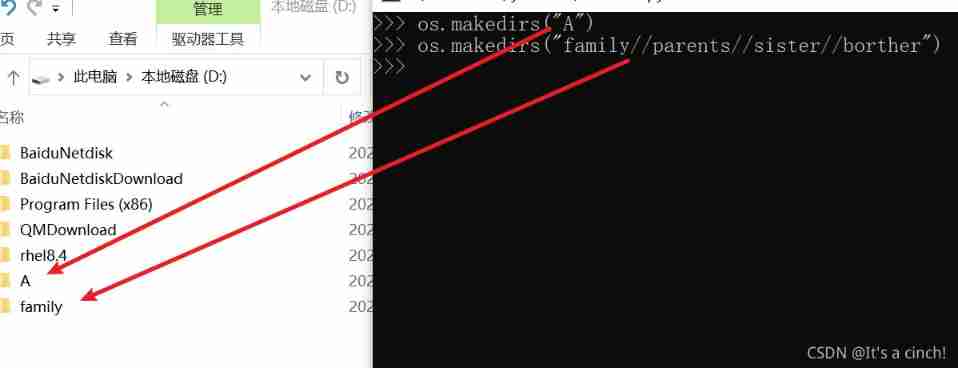
Properties and methods of OS Library
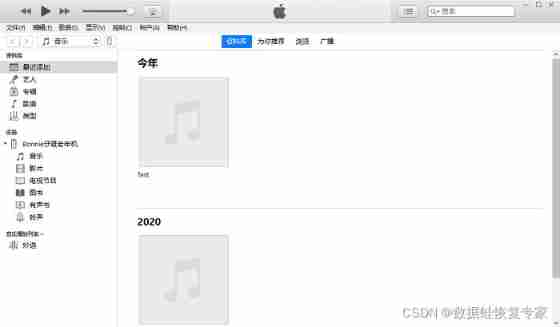
What if the chat record is gone? How to restore wechat chat records on Apple Mobile
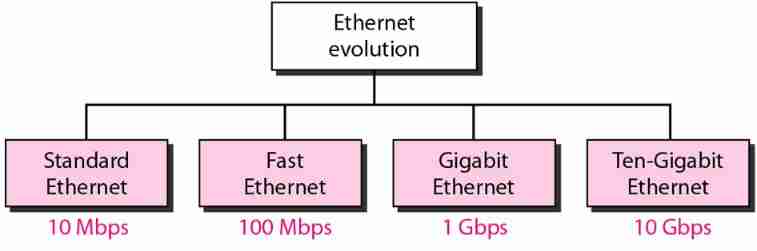
Data communication and network: ch13 Ethernet
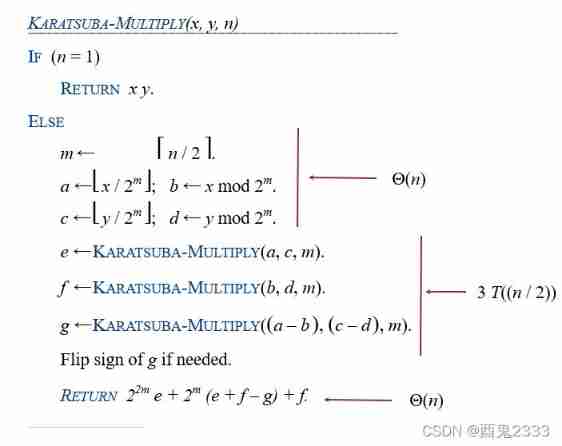
Lecture 9
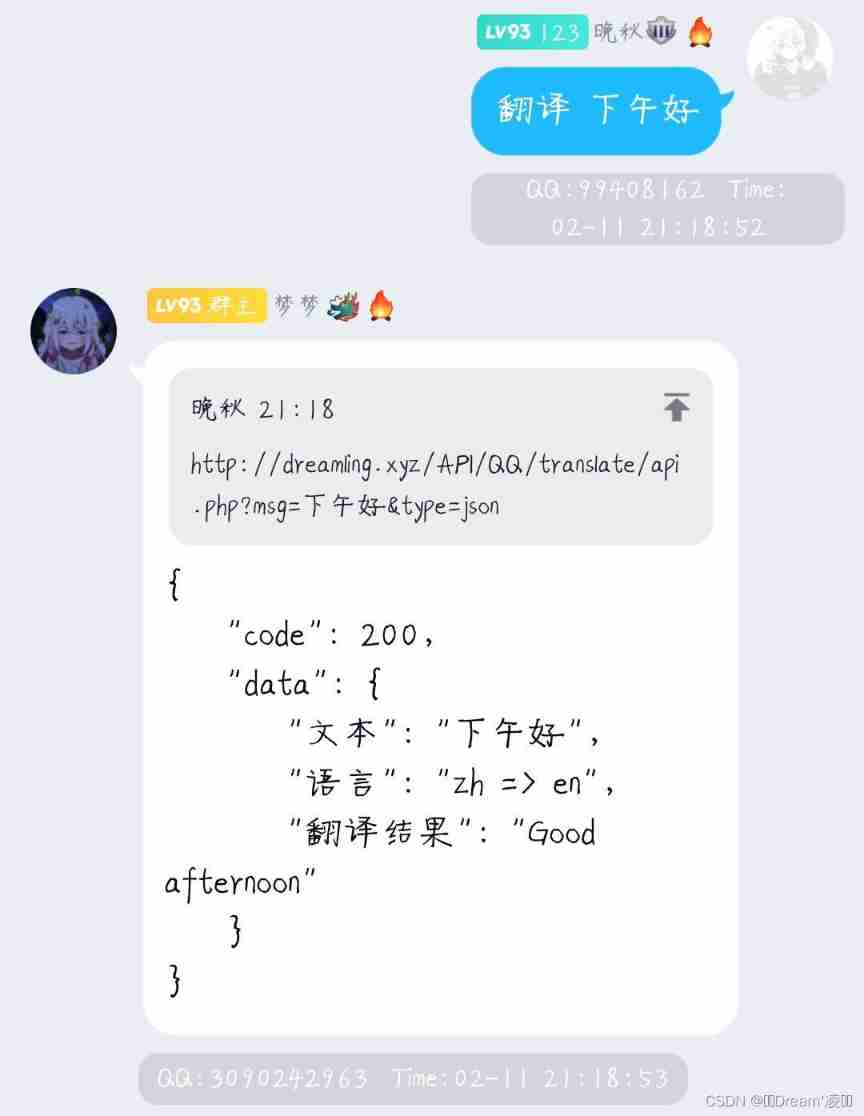
Automatic translation between Chinese and English
(August 10, 2021) web crawler learning - Chinese University ranking directed crawler

2021-08-09
Force buckle 142 Circular linked list II
随机推荐
Source code analysis of the implementation mechanism of multisets in guava class library
(2021-08-20) web crawler learning 2
How to judge the advantages and disadvantages of low code products in the market?
Local MySQL forget password modification method (Windows) [easy to understand]
Application of slice
DVC use case (VI): Data Registry
Summary of Shanghai Jiaotong University postgraduate entrance examination module -- cryptography
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 8
Alibaba cloud server connection intranet operation
Install freeradius3 in the latest version of openwrt
Process communication and thread explanation
SAP ui5 date type sap ui. model. type. Analysis of the display format of date
Awk getting started to proficient series - awk quick start
priority_ queue
How to disable debug messages on sockjs stomp - how to disable debug messages on sockjs Stomp
QQ get group link, QR code
Enter the smart Park, and change begins here
Anti clockwise rotation method of event arrangement -- PHP implementation
TCP fast retransmission sack mechanism
Lvs+kept highly available cluster