当前位置:网站首页>Web security - CSRF (token)
Web security - CSRF (token)
2022-07-03 04:31:00 【the zl】
CSRF And Token
Token: token , and Session,Cookie equally , It's all identity ,Token It usually exists in URL and Cookie in
Token effect :
1, Prevent forms from being submitted repeatedly
The server receives the Token after , If and Session Same value in , At this time, the client session Medium Token Will update
2, prevent CSRF( Cross station request attack )
give an example :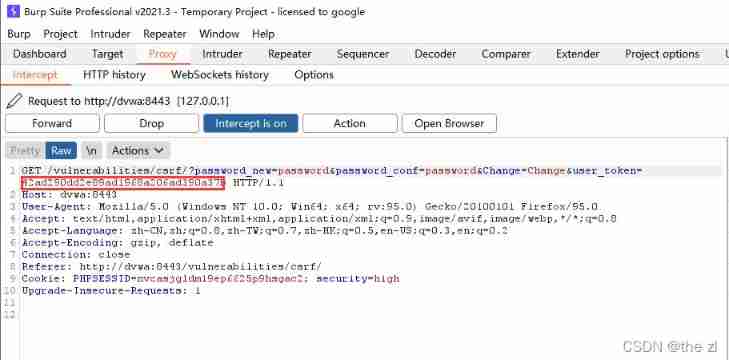
Tectonic CSRF, because Token Why , So the attack failed 

Token Production process :
When the client requests the server page , The server will generate a random number Token Store in Session in , It will also session Send to client ( Generally by construction hidden), The next time a client submits a request ,Token It will be submitted to the server along with the form .
边栏推荐
- Redraw and reflow
- [set theory] set concept and relationship (true subset | empty set | complete set | power set | number of set elements | power set steps)
- [fxcg] market analysis today
- 2022-02-12 (338. Bit count)
- FFMpeg example
- Small program animation realizes the running lantern and animation object
- 2022 electrician (Advanced) examination papers and electrician (Advanced) examination skills
- 2022 registration of G2 utility boiler stoker examination and G2 utility boiler stoker reexamination examination
- Php+mysql registration landing page development complete code
- Classes in TS
猜你喜欢
vulnhub HA: Natraj
Contents of welder (primary) examination and welder (primary) examination in 2022

Two drawing interfaces - 1 Matlab style interface

Joint set search: merge intervals and ask whether two numbers are in the same set
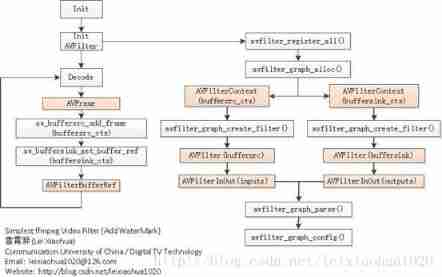
FFMpeg filter

Fcpx template: sweet memory electronic photo album photo display animation beautiful memory

Employee attendance management system based on SSM

Function introduction of member points mall system

I've been in software testing for 8 years and worked as a test leader for 3 years. I can also be a programmer if I'm not a professional

When using the benchmarksql tool to preheat data for kingbasees, execute: select sys_ Prewarm ('ndx_oorder_2 ') error
随机推荐
Kingbasees plug-in KDB of Jincang database_ database_ link
[set theory] ordered pair (ordered pair | ordered triple | ordered n ancestor)
Which Bluetooth headset is cost-effective? Four Bluetooth headsets with high cost performance are recommended
redis 持久化原理
Youdao cloud notes
Summary of training competition (Lao Li's collection of questions)
How do you use lodash linking function- How do you chain functions using lodash?
How to retrieve the password for opening word files
[fxcg] market analysis today
Prefix and (continuously updated)
Xrandr modifier la résolution et le taux de rafraîchissement
AWS VPC
Classes in TS
PostgreSQL database high availability Patroni source code learning - etcd class
有道云笔记
Priv app permission exception
Employee attendance management system based on SSM
sd卡数据损坏怎么回事,sd卡数据损坏怎么恢复
Arthas watch grabs a field / attribute of the input parameter
Kubernetes source code analysis (I)