当前位置:网站首页>How to do well in enterprise system vulnerability assessment
How to do well in enterprise system vulnerability assessment
2022-07-27 14:48:00 【ManageEngine Zhuohao】

As an overall plan IT Administrators , Are you always paying attention to the server 、 Workstations and staff computers 、 Notebook system security ? Are you always paying attention to the new security events and system vulnerability information on the Internet ? In daily work, I have been defending against network attacks and repairing system vulnerabilities , But I am worried about the security loopholes that appear at any time , This is because there is no effective and systematic way to find and repair vulnerabilities .
IT Administrators should keep abreast of the latest system dynamics , Find the focus of attention to system vulnerabilities , Complete safety management tasks in a timely and efficient manner .
What is vulnerability assessment
Vulnerability assessment , Or more accurately, vulnerability analysis , It is to identify according to the risks that security risks bring to your enterprise , The process of evaluation and classification , So that you can accurately handle security issues , Reduce risks in time . Vulnerability assessment is an active means for system security , You can find those vulnerabilities that are more likely to be exploited , In this way, the most serious loopholes can be quickly repaired , So as not to cause loss .
Why do you need a vulnerability assessment tool
According to the latest Forrester Global Security Survey ,“ In the past year , Yes 49% Of enterprises have suffered one or more attacks , And software vulnerability is the biggest factor causing these damages .” In recent years , System vulnerabilities are proliferating . Tens of thousands of security vulnerabilities are discovered every year , This highlights the importance of vulnerability assessment of enterprises .
The reality is cruel , No security team has the resources or time to manually address each vulnerability . Even if you intend to do so , We should also solve the most serious problems first . Because not all vulnerabilities pose the same threat to the enterprise . You need a vulnerability assessment tool that can provide the required vulnerability background information , Learn about possible and unexploited vulnerabilities , In this way, you can solve emergency vulnerabilities first .
How to evaluate security vulnerabilities
Most vulnerability assessment tools provide common indicators , Such as severity rating and general vulnerability scoring system (CVSS) Level to assess security vulnerabilities . however , We should really understand the risks brought by vulnerabilities , You need to master the following list based on these indicators :
- Whether the vulnerability has been publicly disclosed
- How long has this vulnerability been latent in your terminal
- How easy is it to exploit this vulnerability
- Whether the manufacturer has released a patch for this vulnerability
- Whether you can extract meaningful processing from the scanned data
- If there is no patch , Do you have a temporary fix
therefore , It's not just scanning for vulnerabilities , We should also be able to conduct vulnerability assessment , Be able to master all the information in the above list .
Vulnerability assessment tools
Vulnerability Manager Plus The design principle of vulnerability management is :“ Pinpoint , prioritizing , Fix vulnerability ”.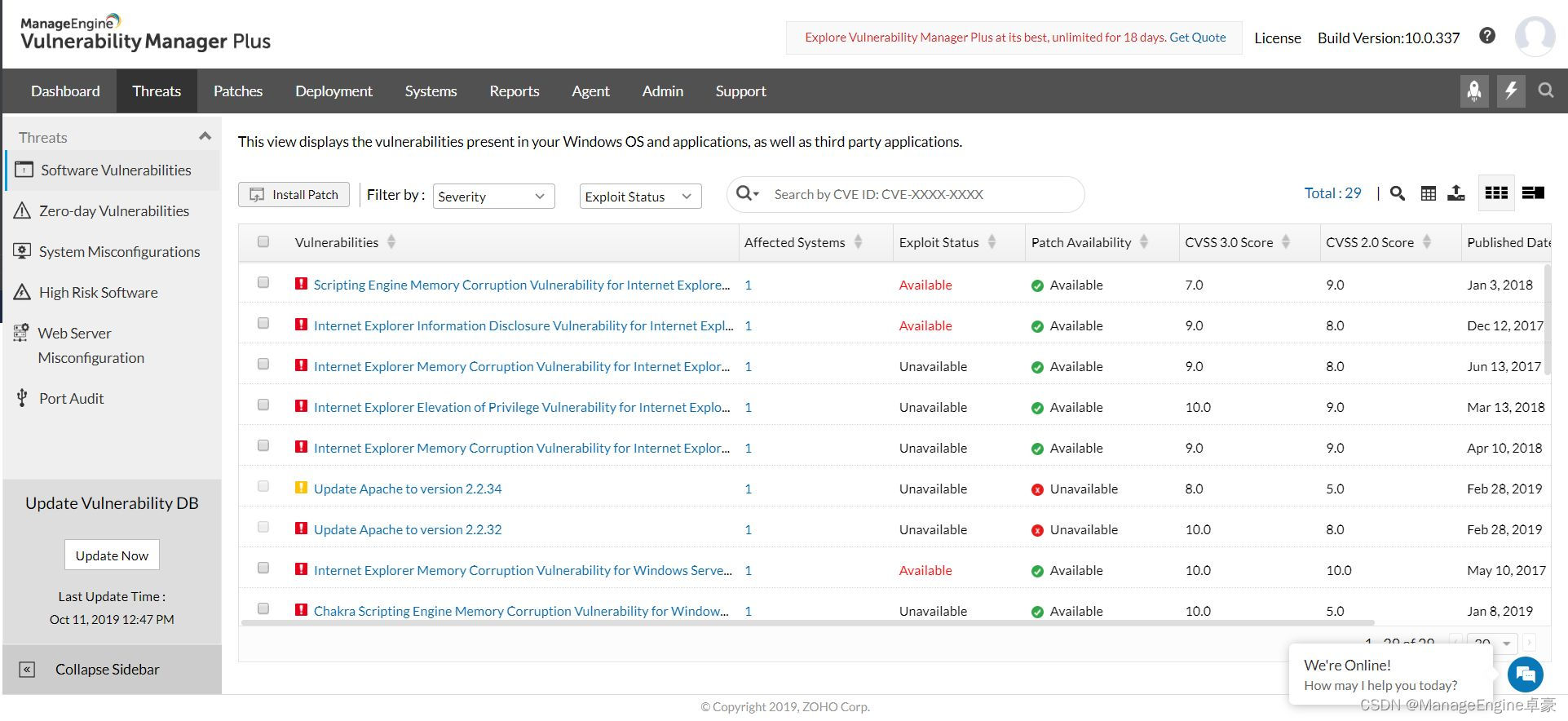
Vulnerability assessment steps 
Eliminate blind spots
Eliminating blind spots is the key to effectively evaluate vulnerabilities . Automatically discover assets in active directories and workgroup assets . Once new assets are added to the network , Will be discovered .
Continuous monitoring
When performing a manual or scheduled vulnerability scan , You may not be able to take measures in time . Whenever a new device or software enters your network , Your enterprise will face new vulnerabilities . You need to continuously monitor and identify vulnerabilities . Use agent-based scanning , Every time 90 Check the terminal for new vulnerabilities every minute .
Vulnerability assessment dashboard
The vulnerability dashboard is IT Administrators provide a clear view , Let you focus on the most worrying place .
Vulnerability severity summary 
Don't ignore the importance of severity level ; They are common vulnerability risk assessment criteria . Vulnerability severity summary helps you track the number of vulnerabilities at each severity level that need to be addressed , So as to better see how many key vulnerabilities remain .
Zero Day vulnerability 
Security vulnerability assessment One of the most critical aspects of is how the vulnerability assessment tool effectively enables you to understand Zero Day vulnerabilities . Zero Day vulnerability is the easiest target for hackers , Because before suppliers can release patches to fix vulnerabilities , Zero Day vulnerability has been known to the public or exploited by the opposition , Therefore, it is crucial to ensure that they are not buried by trivia .Vulnerability Manager Plus And the zero day count chart provides you with a view of zero day vulnerabilities in the network , So you can recognize them immediately , And repair it or use alternative mitigation measures , While waiting for the patch from the server vendor .
Vulnerability time matrix 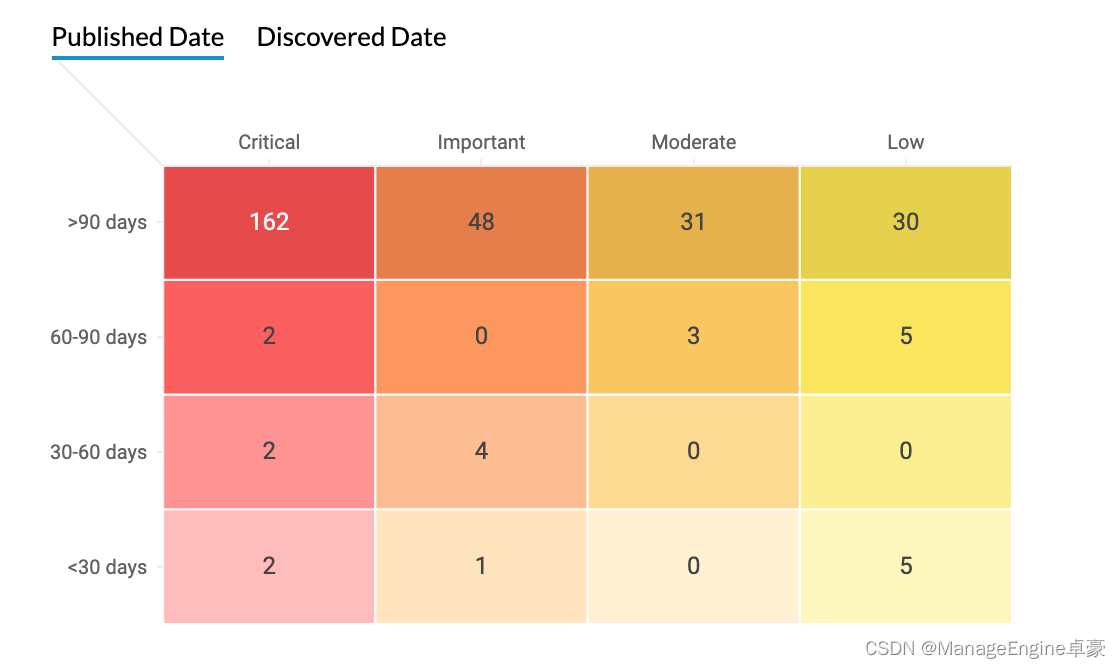
Speaking of vulnerability repair , Time is very important . In recent years , The time from vulnerability release to vulnerability exploitation code disclosure is greatly shortened . The longer you wait , The longer the network is attacked .
Critical vulnerabilities can often be exploited automatically without any user interaction , Therefore, these loopholes must be solved immediately , Important loopholes should be 30 Repair within days , Low level vulnerabilities should be 90 Repair within days .
High priority vulnerability
This is what you should focus on ! Manage the list of vulnerabilities that are on the verge of being exploited . The list considers various risk factors , For example, the difficulty of vulnerability exploitation , severity , Time and patch availability . This form can help you ensure that no key factors are missed in the vulnerability assessment process .
Bug repair
By automatically associating vulnerabilities with their patches , You can immediately deploy patches to priority vulnerabilities . A separate patch management module is also provided , Used to set the regular patch plan . For zero day vulnerabilities , Provides a temporary solution .
边栏推荐
- 文献翻译__基于自适应全变差L1正则化的椒盐图像去噪
- 「游戏引擎 浅入浅出」4.1 Unity Shader和OpenGL Shader
- Timestamp of AAC, h264, etc
- Redis
- spark job 使用log4j appender 追加日志到本地文件或者mysql
- @Detailed explanation of repository
- 动态规划——股票买卖5
- 通过VN1630/VN7640的I/O功能来确认电源设置电压的时间精确度
- 2022 Niuke multi School II_ E I
- [cache series] completely solve the problems of cache avalanche, breakdown and penetration
猜你喜欢

Redis

@What happens when bean and @component are used on the same class?
Docker实践经验:Docker 上部署 mysql8 主从复制

DirectX 入门知识

【ManageEngine】什么是SIEM

Toward fast, flexible, and robust low light image enhancement cvpr2022

Simple encapsulation steps of request data request of uniapp

腾讯二面:@Bean 与 @Component 用在同一个类上,会怎么样?
![Detailed explanation of Telnet remote login AAA mode [Huawei ENSP]](/img/48/dd0fa3c494c45f604b7a93c707b808.png)
Detailed explanation of Telnet remote login AAA mode [Huawei ENSP]

这年头谁还不会抓包,WireShark 抓包及常用协议分析送给你!
随机推荐
How to deploy open source Siyuan privately
SkyWalking分布式系统应用程序性能监控工具-中
Research on Chinese idiom metaphorical knowledge recognition and relevance based on transfer learning and text enhancement
【论文精读】Grounded Language-Image Pre-training(GLIP)
Toward Fast, Flexible, and Robust Low-Light Image Enhancement(实现快速、灵活和稳健的弱光图像增强)CVPR2022
Summary of basic knowledge of C language
JS什么是声明提前?函数与变量声明提前的先后顺序(执行上下文铺垫篇)
数据库使用psql及jdbc进行远程连接,不定时自动断开的解决办法
「游戏引擎 浅入浅出」4.1 Unity Shader和OpenGL Shader
Getting started for beginners: build your own blog with WordPress
log4j2 jdbc appender
Hdu4496 d-city [concurrent search]
SLAM综述阅读笔记四:A Survey on Deep Learning for Localization and Mapping: Towards the Age of Spatial 2020
Document translation__ Salt and pepper image denoising based on adaptive total variation L1 regularization
codeforces 1708E - DFS Trees
lc marathon 7.26
@What happens when bean and @component are used on the same class?
printf函数缓冲区问题
codeforces 1708E - DFS Trees
文献翻译__基于自适应全变差L1正则化的椒盐图像去噪