当前位置:网站首页>Database auditing - an essential part of network security
Database auditing - an essential part of network security
2022-08-03 01:34:00 【Operations have XiaoDeng @】
Performing database log analysis allows you to audit all access to confidential or sensitive corporate data stored in the database.Auditing database logs can also enhance your internal security framework by answering questions about who changed critical data, when, and more.Database auditing can also help you meet increasingly demanding compliance requirements.
Log Analysis
1. EventLog Analyzer - comprehensive database auditing software
EventLog Analyzer implementation:
- Comprehensive management: EventLog Analyzer centrally collects database events from the entire network, provides rich reports for database auditing, account management and other user changes, server security reports, etc., alerts you to important events in real time and securely archives logs.
- Database activity monitoring: Monitor all user activities in the database, database transactions (including DDL and DML statements), etc.
- Database Server Log Monitoring: This tool provides information on server activity, user logins and logouts, account and permission changes in the database server through in-depth database server log analysis..
- Database Security Monitoring: Monitor the database for any common attack patterns to strengthen database security.Get instant alerts on any targeted attacks, such as SQL injection, and detailed reports on such attacks to aid incident investigation.
- In-depth Analysis: This tool facilitates deeper analysis by providing database server log analysis reports such as top and trend reports.This helps you better understand database server activity and get more value from the logs.
 EventLog Analyzer
EventLog Analyzer
Second, MS SQL server predefined reports
EventLog Analyzer's predefined Microsoft SQL Server reports and alerts cover:
- DDL Activities: Structure-level database changes, such as database creation.
- DML Activities: Functional level activities such as data access and modification.
- Account changes: new user creation, password changes, etc.
- Server activity: server startup, shutdown, creation of server-level objects (such as server audit and server audit specification objects), and server trends.Learn more
- Security Attacks: Common types of attacks such as SQL injection and denial of service attacks.

MS SQL Server
Three, Oracle database predefined reports
EventLog Analyzer's predefined Oracle database reports and alerts cover:
- Database Activities: All database user activities, such as creating tables and databases, executing procedures, etc.Learn more
- Account Management: Create and change profiles, roles, etc.
- Server activity: successful and failed server logins, startups and shutdowns, etc.
- Security Reports: Reports of common attacks such as SQL injection and denial of service.
边栏推荐
猜你喜欢
合并两个excel表格工具
Kubernetes 进阶训练营 网络
# DWD层及DIM层构建## ,220801 ,
js基础知识整理之 —— 获取元素和命名规范
![Yocto系列讲解[实战篇]85 - 制作ubi镜像和自动挂载ubifs文件系统](/img/96/beb34ce07f1e4c0fe932359e42e5c6.png)
Yocto系列讲解[实战篇]85 - 制作ubi镜像和自动挂载ubifs文件系统

CAS:1445723-73-8,DSPE-PEG-NHS,磷脂-聚乙二醇-活性酯两亲性脂质PEG共轭物
js基础知识整理之 —— 闭包
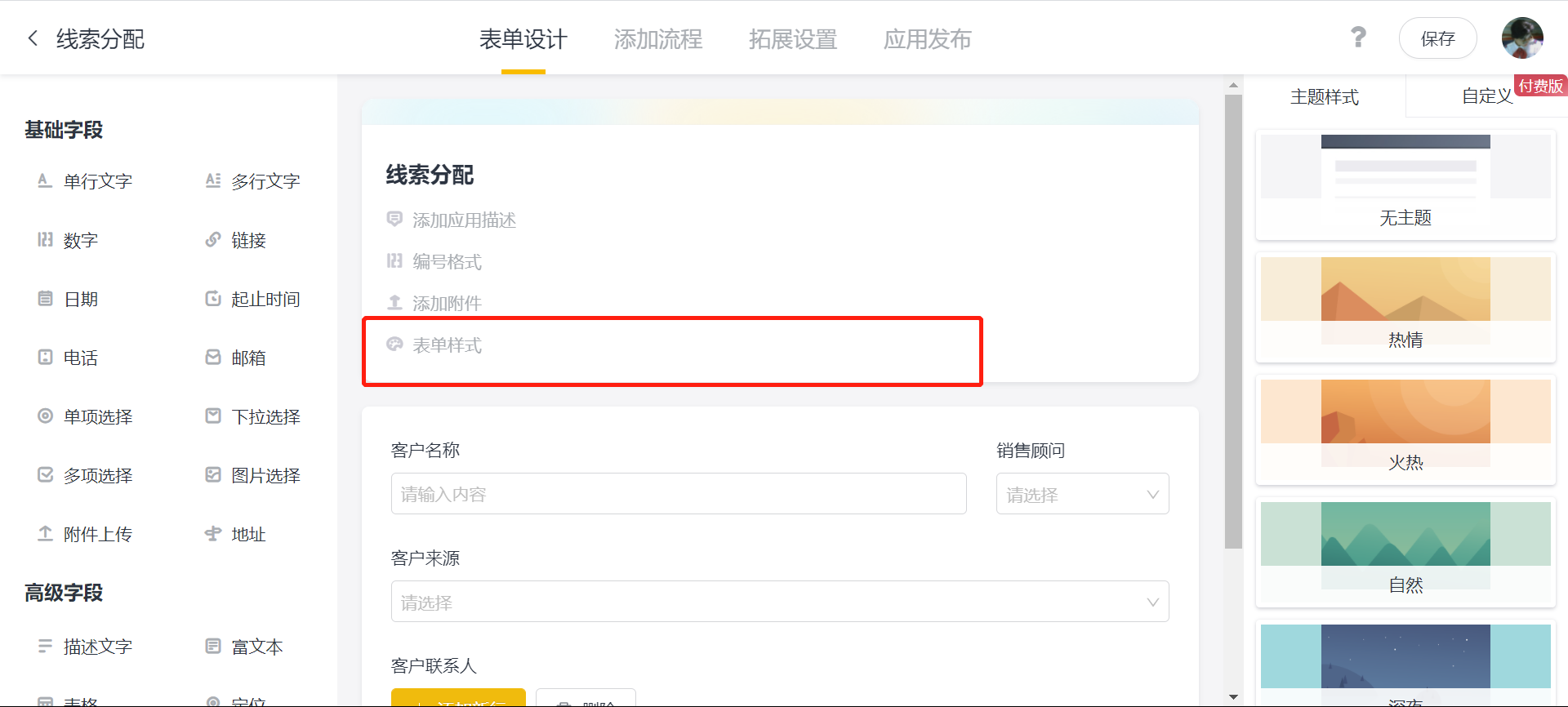
无代码开发平台表单样式设置步骤入门课程
The latest real software test interview questions are shared. Are you afraid that you will not be able to enter the big factory after collecting them?
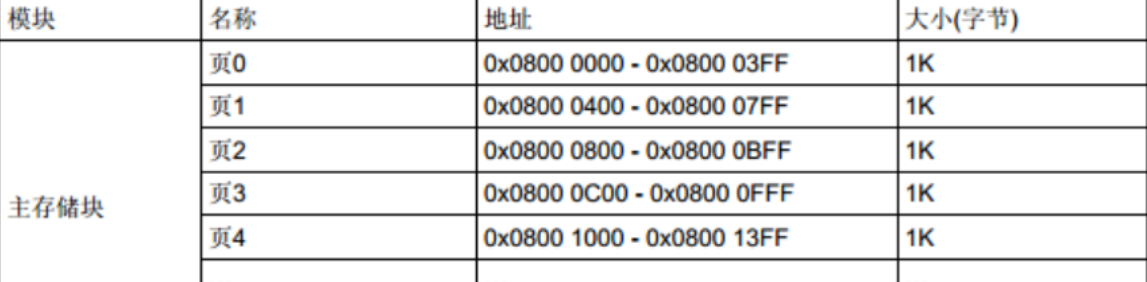
基于STM32的FLASH读写实验含代码(HAL库)
随机推荐
No code development platform data ID introductory tutorial
resubmit 渐进式防重复提交框架简介
Jmeter二次开发实现rsa加密
测试人生 | 阿里实习 90 天:从实习生的视角谈谈个人成长
markdown语法
图像识别从零写出dnf脚本关键要点
CAS:1445723-73-8,DSPE-PEG-NHS,磷脂-聚乙二醇-活性酯两亲性脂质PEG共轭物
d合并json
记一次mysql查询慢的优化历程
脂溶性胆固醇-聚乙二醇-叠氮,Cholesterol-PEG-Azide,CLS-PEG-N3
Jmeter secondary development to realize rsa encryption
Controller层代码这么写,简洁又优雅!
Apache Doris 1.1 特性揭秘:Flink 实时写入如何兼顾高吞吐和低延时
21天学习挑战赛(1)设备树的由来
R语言自学 1 - 向量
2022中国眼博会,山东眼健康展,视力矫正仪器展,护眼产品展
resubmit 渐进式防重复提交框架简介
无代码开发平台表单样式设置步骤入门课程
一文读懂 Web 3.0 应用架构
The CTF command execution subject their thinking
 EventLog Analyzer
EventLog Analyzer