当前位置:网站首页>(6) Web security | penetration test | network security encryption and decryption ciphertext related features, with super encryption and decryption software
(6) Web security | penetration test | network security encryption and decryption ciphertext related features, with super encryption and decryption software
2022-07-02 13:04:00 【Black zone (rise)】
Super encryption and decryption tool :
link :https://pan.baidu.com/s/1lmi8bF5N5_cIYT6QG99TDQ
Extraction code :hj12
Many common web addresses are encrypted , prevent sql Inject
Analysis of common encryption and coding algorithms
MD5,SHA,AES, Base number , Time stamp ,URL,BASE64,Unescape,DES etc.
Understand the characteristics of conventional encryption algorithms
Length digits , Character law , The code analysis , Search for, etc
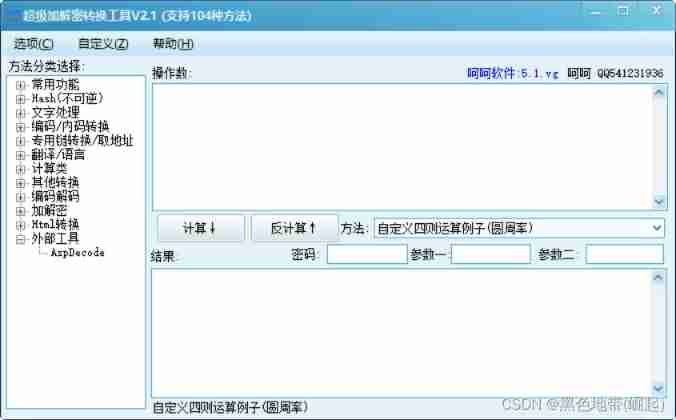
md5 encryption ( Default 32 position , Irreversible )
After encryption is 16 Bit or 32 A character , It consists of letters and numbers , Letters are case sensitive , Theoretically, it cannot be decrypted , Unless we crack it violently
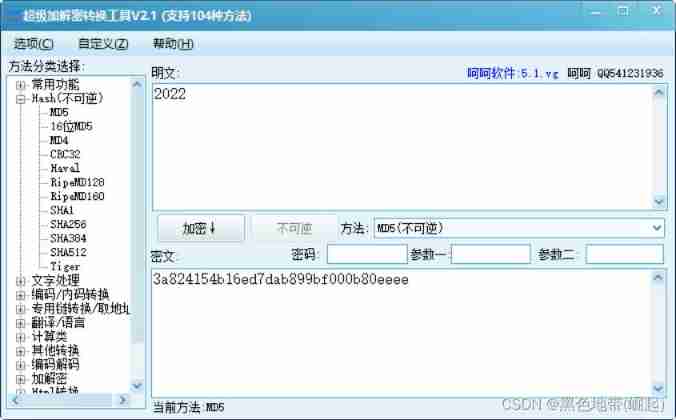
SHA encryption
SHA-1 The encrypted ciphertext is 40 Characters , And it is composed of numbers and letters

SHA256 64 Character composition
SHA384 96 Character composition
SHA512 128 Character composition
(1 The letters seem to be lowercase , I don't know if I haven't encrypted enough )
AES encryption
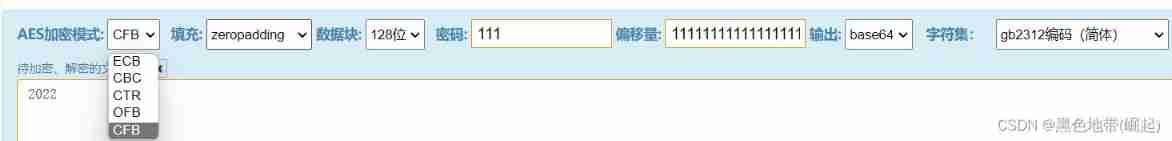
The larger the number of data blocks , More output
128 position base64 Output 24 position hex Output 32 position
192 position base64 Output 32 position hex Output 48 position
Time stamp
Time stamp (Unix timestamp) Transformation tool - Online tools (tool.lu)

URL encryption
The code is characterized by a string % Two character style .
URL The encoding is a character ascii The hexadecimal of the code , Then you need to add “%”.
for example “\”, its ascii Code is 92,92 The hexadecimal of is 5c, therefore “\” Of URL The encoding is %5c.

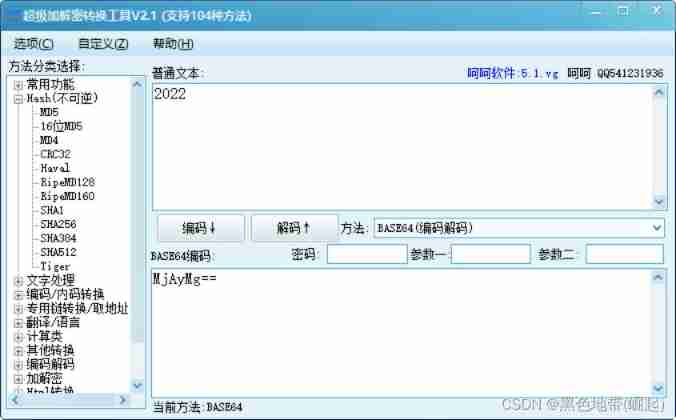
BASE64
The length characteristic of ciphertext string is 4 Integer multiple . The symbolic value of string can only be A-Z, a-z, 0-9, +, /, = total 65 Of the characters , And = If it appears, it must appear at the end .
Analysis of common encryption forms and algorithms
Direct encryption , belt salt, With the code , With offset , Band number , Band mode , With interference , Custom combination, etc
Common decryption methods
enumeration , Custom reverse algorithm , Reversible ( Is to use various tools )
边栏推荐
- About asp Net MVC project in local vs running response time is too long to access, the solution!
- Js2day (also i++ and ++i, if statements, ternary operators, switch, while statements, for loop statements)
- 8A 同步降压稳压器 TPS568230RJER_规格信息
- PXE installation UOS prompt NFS over TCP not available from 10 x.x.x
- 正确遍历EntryList方法
- 堆 AcWing 839. 模拟堆
- Js10day (API phased completion, regular expression introduction, custom attributes, filtering sensitive word cases, registration module verification cases)
- What data types does redis have and their application scenarios
- 百款拿来就能用的网页特效,不来看看吗?
- Tencent three sides: in the process of writing files, the process crashes, and will the file data be lost?
猜你喜欢

移动式布局(流式布局)

完全自主可控三维云CAD:CrownCAD便捷的命令搜索,快速定位所需命令具体位置。
C#运算符

Day4 operator, self increasing, self decreasing, logical operator, bit operation, binary conversion decimal, ternary operator, package mechanism, document comment

Ali on three sides, it's really difficult to successfully get the offer rated P7

Ali was killed by two programming problems at the beginning, pushed inward again, and finally landed (he has taken an electronic offer)

Linear DP acwing 898 Number triangle

难忘阿里,4面技术5面HR附加笔试面,走的真艰难真心酸
线性DP AcWing 897. 最长公共子序列
Js2day (also i++ and ++i, if statements, ternary operators, switch, while statements, for loop statements)
随机推荐
Sensor adxl335bcpz-rl7 3-axis accelerometer complies with rohs/weee
Variable, "+" sign, data type
阿里发布的Redis开发文档,涵盖了所有的redis操作
Js7day (event object, event flow, event capture and bubble, prevent event flow, event delegation, student information table cases)
Analog to digital converter (ADC) ade7913ariz is specially designed for three-phase energy metering applications
接口测试面试题目,你都会了吗?
Mongodb redis differences
Dijkstra AcWing 850. Dijkstra求最短路 II
线性DP AcWing 902. 最短编辑距离
Js6day (search, add and delete DOM nodes. Instantiation time, timestamp, timestamp cases, redrawing and reflow)
Mui WebView down refresh pull-up load implementation
Direct control PTZ PTZ PTZ PTZ camera debugging (c)
std::vector批量导入快速去重方法
应用LNK306GN-TL 转换器、非隔离电源
Linear DP acwing 895 Longest ascending subsequence
Traverse entrylist method correctly
Typora+docsify quick start
. Net wechat message template push
腾讯三面:进程写文件过程中,进程崩溃了,文件数据会丢吗?
Redis transaction mechanism implementation process and principle, and use transaction mechanism to prevent inventory oversold