当前位置:网站首页>[vulnhub shooting range] impulse: lupinone
[vulnhub shooting range] impulse: lupinone
2022-07-03 21:04:00 【Starry`Quan】
Environmental preparation
Download the image and import it to vmware, There's nothing to say 
Found that the title has been given ip Address
attack IP Address :192.168.2.16
Drone aircraft IP The address is :192.168.2.17
information gathering
Use nmap Scan host information 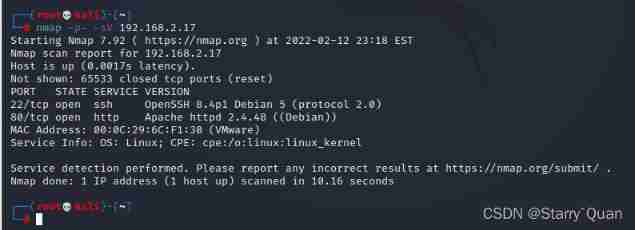
It's found that the target machine is only open ssh Follow http, Let's visit his website first 
There's only one picture , Looking at the source code, there is nothing good to find
It's beginning to penetrate
Let's scan his website directory 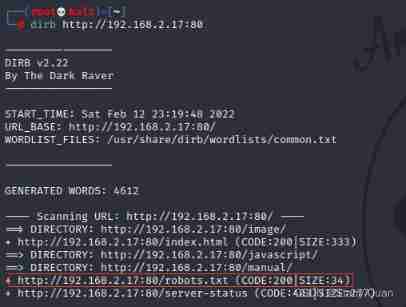
Found to have robots.txt, Let's visit , Found to have ~myfiles Folder 
We visited and found 404, But we look at the source code and find 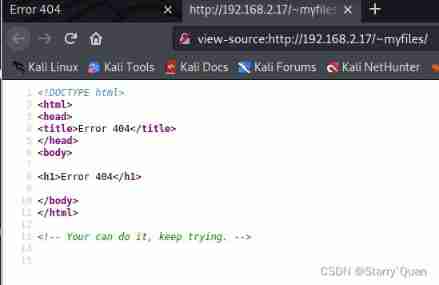
Let's keep trying , It just implies that we have other folders , We use wfuzz Scan it. 
Found to have ~secret file , Let's visit 
Hello Friend, Im happy that you found my secret diretory, I created like this to share with you my create ssh private key file,
Its hided somewhere here, so that hackers dont find it and crack my passphrase with fasttrack.
I’m smart I know that.
Any problem let me know
Your best friend icex64
Hello friend , I'm glad you found my secret directory , I created it like this , To share my ssh Private key file ,
It's hidden somewhere here , So hackers won't find it , Use the fast channel to crack my password .
I'm smart , That's true. .
Come to me if you have any questions
Your best friend icex64
Here are two messages , One is user name icex64 There is also a hidden file
Use wfuzz No result after scanning 
Guess there may be a suffix , Let's change to ffuz This tool sweeps , This tool can choose its own suffix
ffuf -u "http://192.168.2.17/~secret/.FUZZ" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e .txt,.pub,.html,.bak -mc 200
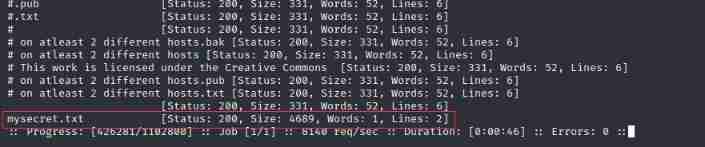
Swept out a file , Let's visit 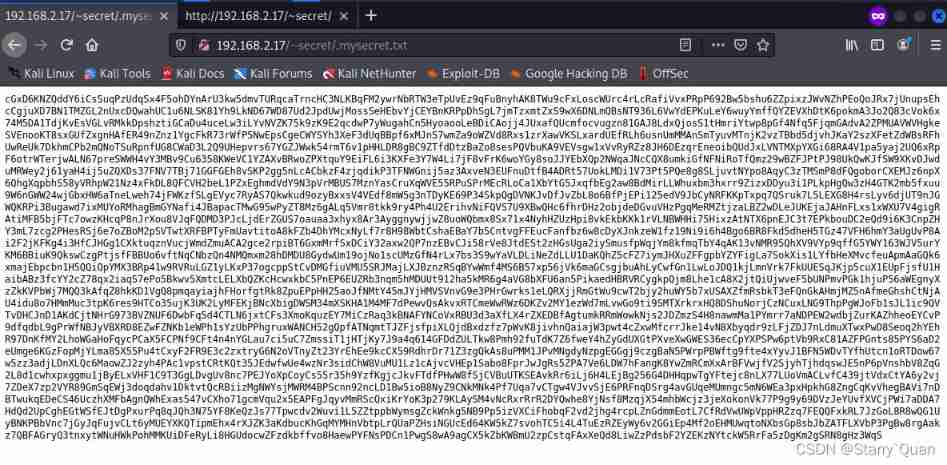
It's a bunch of random code , Look like base encryption , Let's go straight to base Family bucket Decrypt one by one
Find out base58 It can be solved 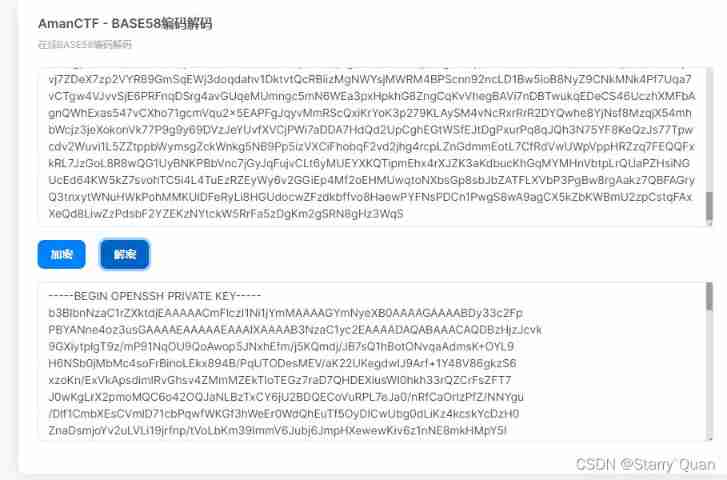
So now we have ssh The private key
Use ssh2john Generate a password book , And then use john Blow it up , You can get the password 
Before ~secret The document has asked us to use fasttrack Dictionary to explode
Its hided somewhere here, so that hackers dont find it and crack my passphrase with fasttrack.
john --wordlist=/usr/share/wordlists/fasttrack.txt passwd.txt
Find the password 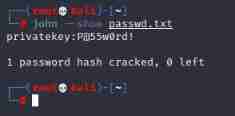
We log in with the user name we were told before ssh, Be careful , First assign the key file to 600 jurisdiction , Permission is too high to log in 
home There is the first one in the directory flag file 
Raise the right
Let's first look at what files this user can run
Found that you can run one python file 
Look at the python file , Found that it quoted webbrowser modular , Let's go to the python See if you can modify this module under the directory , Let it return a shell
It can be edited , We'll use it again arsene The user runs this python file , You can get his permission 
Let's see what it can run 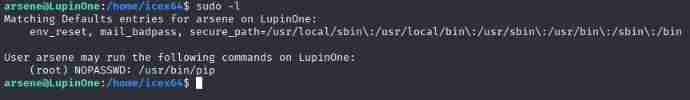
Found that he can run pip command , We directly Baidu pip Raise the right Method 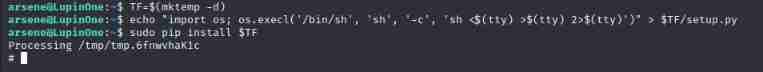
Successful acquisition root jurisdiction , And then check out root.txt You can get flag 了 
That's the end of the experiment
边栏推荐
- Reinforcement learning - learning notes 1 | basic concepts
- Deep search DFS + wide search BFS + traversal of trees and graphs + topological sequence (template article acwing)
- Memory analyzer (MAT)
- 内存分析器 (MAT)
- C 10 new feature [caller parameter expression] solves my confusion seven years ago
- Install and use Chrony, and then build your own time server
- How to handle wechat circle of friends marketing activities and share production and release skills
- MySQL——数据库备份
- Borui data and Sina Finance released the 2021 credit card industry development report
- Kubernetes abnormal communication network fault solution ideas
猜你喜欢

MySQL——索引

Such as the visual appeal of the live broadcast of NBA Finals, can you still see it like this?

From the behind the scenes arena of the ice and snow event, see how digital builders can ensure large-scale events
【愚公系列】2022年7月 Go教学课程 002-Go语言环境安装

MySQL master-slave synchronization principle

Install and use Chrony, and then build your own time server
thrift go

如临现场的视觉感染力,NBA决赛直播还能这样看?

不同业务场景该如何选择缓存的读写策略?
Line segment tree blue book explanation + classic example acwing 1275 Maximum number
随机推荐
[Tang Laoshi] C -- encapsulation: member variables and access modifiers
强化學習-學習筆記1 | 基礎概念
leetcode-540. A single element in an ordered array
Rhcsa third day notes
In 2021, the global revenue of syphilis rapid detection kits was about US $608.1 million, and it is expected to reach US $712.9 million in 2028
浅析 Ref-NeRF
LabVIEW training
Rhcsa third day operation
Cannot load driver class: com. mysql. cj. jdbc. Driver
Last week's content review
鹏城杯 WEB_WP
Gee calculated area
Nmap and masscan have their own advantages and disadvantages. The basic commands are often mixed to increase output
Study diary: February 14th, 2022
Is flush account opening and registration safe and reliable? Is there any risk?
Haven't expressed the artifact yet? Valentine's Day is coming. Please send her a special gift~
设计电商秒杀系统
2022 safety officer-c certificate examination and safety officer-c certificate registration examination
Install and use Chrony, and then build your own time server
Introduction to golang garbage collection