当前位置:网站首页>Example of peanut shell inner net penetration
Example of peanut shell inner net penetration
2022-07-03 20:12:00 【Issue is FW】
Intranet through
Local services , The Internet cannot be accessed directly ( Not in a LAN , There is no public network on this machine ip)
The port mapping from external network to internal network is realized through intranet penetration technology , To realize external network access and internal network service .
Tools
There are many tools for intranet penetration , Peanut shells are used here Official website
Download peanut shells

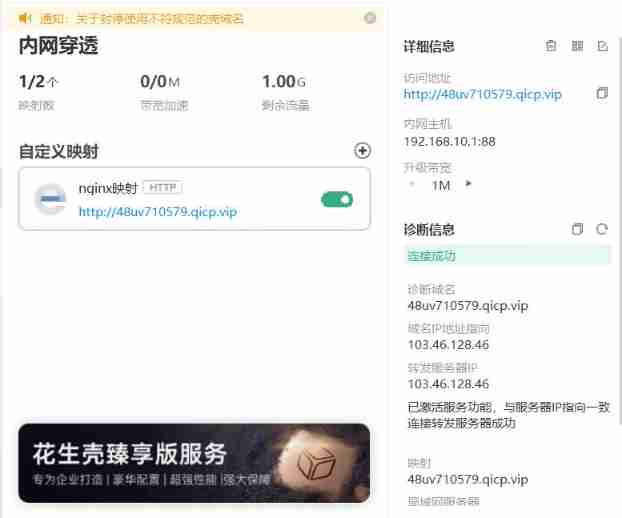
Click intranet penetration , The following configuration

Select http bar , There's a charge 6 6 6 Soft girl coin
Write your own intranet host and port , My service is 88 88 88 Port is optional 88 88 88
Save later , The connection is successful
test
For example, it is used here java Do a test
@GetMapping(value = "/")
public String Hello() {
return "Hello,cl ";
}
Local access

Extranet access

边栏推荐
- The 29th day of force deduction (DP topic)
- Today's work summary and plan: February 14, 2022
- Upgrade PIP and install Libraries
- 2.4 conversion of different data types
- Sparse matrix (triple) creation, transpose, traversal, addition, subtraction, multiplication. C implementation
- 2.7 format output of values
- Bright purple crystal meso tetra (4-aminophenyl) porphyrin tapp/tapppt/tappco/tappcd/tappzn/tapppd/tappcu/tappni/tappfe/tappmn metal complex - supplied by Qiyue
- Global and Chinese market of speed limiter 2022-2028: Research Report on technology, participants, trends, market size and share
- Vscode reports an error according to the go plug-in go get connectex: a connection attempt failed because the connected party did not pro
- Leetcode daily question solution: 540 A single element in an ordered array
猜你喜欢
FPGA 学习笔记:Vivado 2019.1 工程创建

2022-06-25 advanced network engineering (XI) IS-IS synchronization process of three tables (neighbor table, routing table, link state database table), LSP, cSNP, psnp, LSP

Typora charges, WTF? Still need support
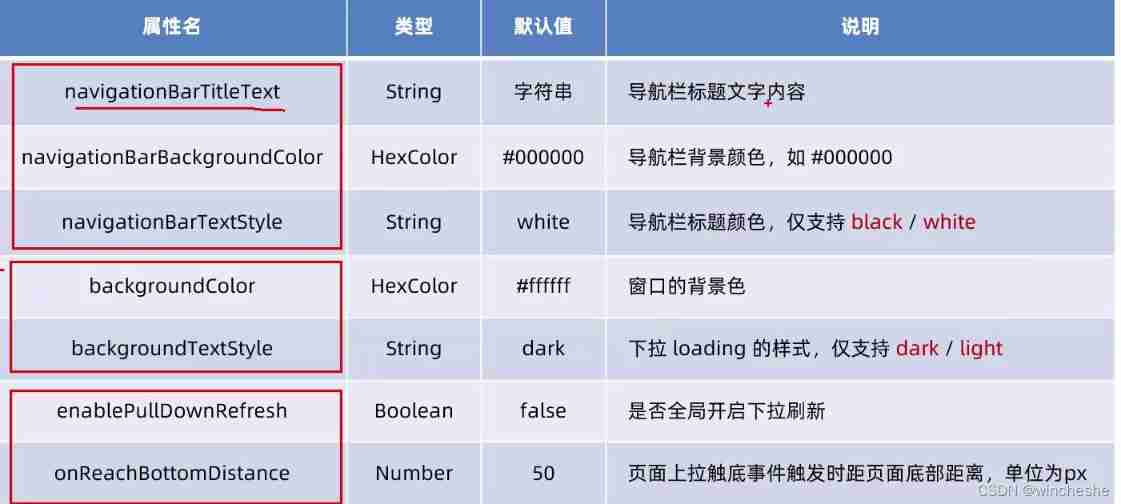
Wechat applet quick start (including NPM package use and mobx status management)
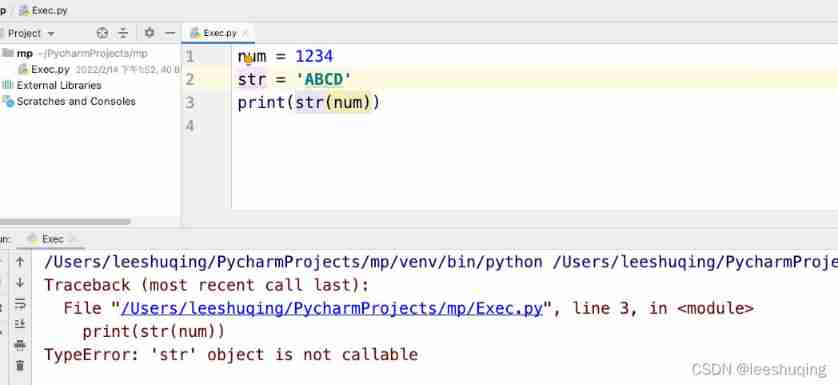
2.5 conversion of different data types (2)

JMeter plug-in installation

Make a simple text logo with DW

Battle drag method 1: moderately optimistic, build self-confidence (1)
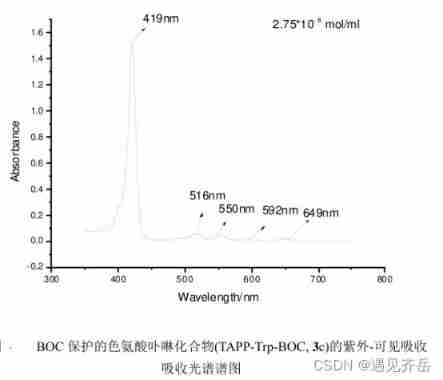
BOC protected tryptophan porphyrin compound (TAPP Trp BOC) Pink Solid 162.8mg supply - Qiyue supply
Phpstudy set LAN access
随机推荐
The 29th day of force deduction (DP topic)
11-grom-v2-04-advanced query
【leetcode】1027. Longest arithmetic sequence (dynamic programming)
kubernetes集群搭建efk日志收集平台
Global and Chinese market of speed limiter 2022-2028: Research Report on technology, participants, trends, market size and share
Global and Chinese market of micro positioning technology 2022-2028: Research Report on technology, participants, trends, market size and share
Nacos usage of micro services
4. Data binding
Plan for the first half of 2022 -- pass the PMP Exam
44. Concurrent programming theory
5- (4-nitrophenyl) - 10,15,20-triphenylporphyrin ntpph2/ntppzn/ntppmn/ntppfe/ntppni/ntppcu/ntppcd/ntppco and other metal complexes
Initialization and instantiation
Make a simple text logo with DW
Titles can only be retrieved in PHP via curl - header only retrieval in PHP via curl
2.4 conversion of different data types
5. MVVM model
Kubernetes cluster builds efk log collection platform
AI enhanced safety monitoring project [with detailed code]
Professional interpretation | how to become an SQL developer
Explore the internal mechanism of modern browsers (I) (original translation)