当前位置:网站首页>Derivation of decision tree theory
Derivation of decision tree theory
2022-07-03 19:51:00 【「 25' h 」】
Decision tree
Information gain


ID3 Algorithm spanning tree
- C4.5 Algorithm and ID3 The location difference is ID3 It's information gain ,C4.5 According to the information gain ratio


Pruning of trees
Loss function

Pruning algorithm


CART The generation of binary tree
Regression tree generation

Classification tree generation


CART Tree pruning
α Introduction and understanding of parameters

Pruning algorithm process

边栏推荐
- Parental delegation mechanism
- BOC protected alanine zinc porphyrin Zn · TAPP ala BOC / alanine zinc porphyrin Zn · TAPP ala BOC / alanine zinc porphyrin Zn · TAPP ala BOC / alanine zinc porphyrin Zn · TAPP ala BOC supplied by Qiyu
- 03 -- QT OpenGL EBO draw triangle
- Chapter 2: 4-digit Kaplan number, search even digit Kaplan number, search n-digit 2-segment sum square number, m-digit ingenious square number without 0, specify the number to form a 7-digit square nu
- Part 28 supplement (XXVIII) busyindicator (waiting for elements)
- 第二章:基于分解的求水仙花数,基于组合的求水仙花数, 兰德尔数,求[x,y]内的守形数,探求n位守形数,递推探索n位逐位整除数
- The simplicity of laravel
- 7. Data broker presentation
- 2022 - 06 - 30 networker Advanced (XIV) Routing Policy Matching Tool [ACL, IP prefix list] and policy tool [Filter Policy]
- Detailed and not wordy. Share the win10 tutorial of computer reinstallation system
猜你喜欢

01 - QT OpenGL display OpenGL window
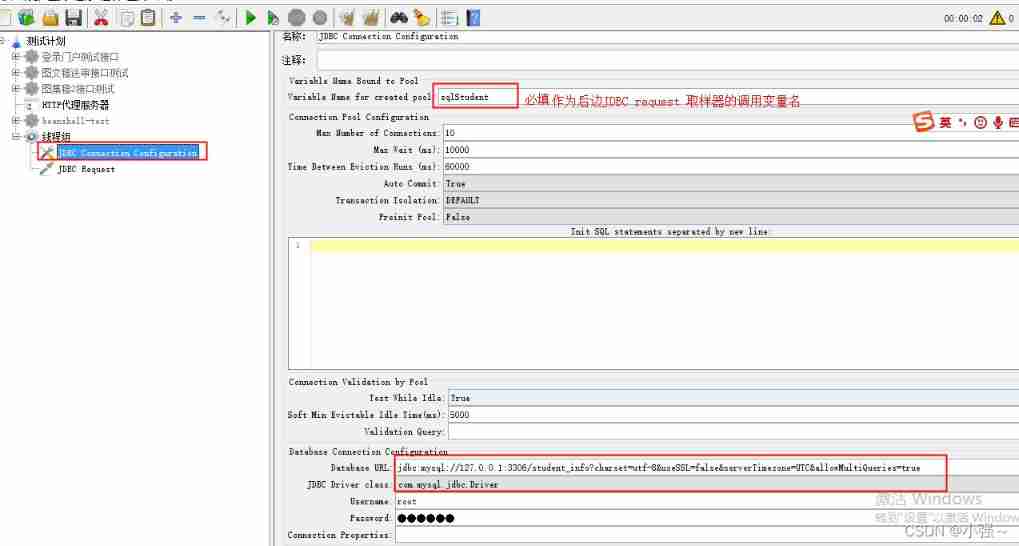
JMeter connection database

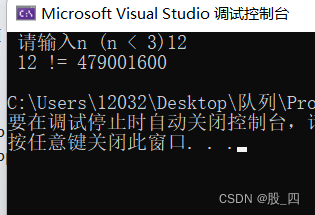
第一章:拓广同码小数和s(d, n)
第一章:求n的阶乘n!

Octopus online ecological chain tour Atocha protocol received near grant worth $50000
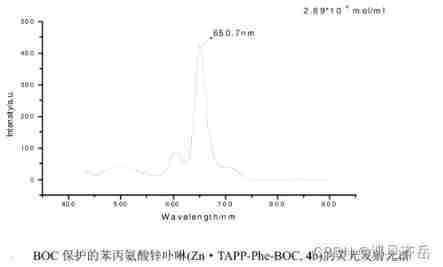
BOC protected phenylalanine zinc porphyrin (Zn · TAPP Phe BOC) / iron porphyrin (Fe · TAPP Phe BOC) / nickel porphyrin (Ni · TAPP Phe BOC) / manganese porphyrin (Mn · TAPP Phe BOC) Qiyue Keke
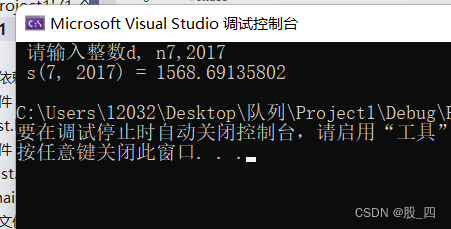
Chapter 1: simplify the same code decimal sum s (D, n)
Native table - scroll - merge function
Explore the internal mechanism of modern browsers (I) (original translation)

2022-07-02 advanced network engineering (XV) routing policy - route policy feature, policy based routing, MQC (modular QoS command line)
随机推荐
BUUCTF
2022-06-27 advanced network engineering (XII) IS-IS overhead type, overhead calculation, LSP processing mechanism, route revocation, route penetration
Explore the internal mechanism of modern browsers (I) (original translation)
Octopus online ecological chain tour Atocha protocol received near grant worth $50000
第二章:4位卡普雷卡数,搜索偶数位卡普雷卡数,搜索n位2段和平方数,m位不含0的巧妙平方数,指定数字组成没有重复数字的7位平方数,求指定区间内的勾股数组,求指定区间内的倒立勾股数组
Sparse matrix (triple) creation, transpose, traversal, addition, subtraction, multiplication. C implementation
Chapter 2: find the classical solution of the maximum Convention and the least common multiple of a and B, find the conventional solution of the maximum Convention and the least common multiple of a a
Chapter 2: find the box array, complete number in the specified interval, and improve the complete number in the specified interval
PR 2021 quick start tutorial, how to create new projects and basic settings of preferences?
Leetcode 1189. Maximum number of balloons (special character count)
IP address is such an important knowledge that it's useless to listen to a younger student?
Native table - scroll - merge function
Use unique_ PTR forward declaration? [repetition] - forward declaration with unique_ ptr? [duplicate]
FAQs for datawhale learning!
Geek Daily: the system of monitoring employees' turnover intention has been deeply convinced off the shelves; The meta universe app of wechat and QQ was actively removed from the shelves; IntelliJ pla
10 smart contract developer tools that miss and lose
IPv6 experiment
2022-06-27 网工进阶(十二)IS-IS-开销类型、开销计算、LSP的处理机制、路由撤销、路由渗透
5- (4-nitrophenyl) - 10,15,20-triphenylporphyrin ntpph2/ntppzn/ntppmn/ntppfe/ntppni/ntppcu/ntppcd/ntppco and other metal complexes
Xctf attack and defense world crypto master advanced area olddriver