当前位置:网站首页>2022-06-30 advanced network engineering (XIV) routing strategy - matching tools [ACL, IP prefix list], policy tools [filter policy]
2022-06-30 advanced network engineering (XIV) routing strategy - matching tools [ACL, IP prefix list], policy tools [filter policy]
2022-07-03 19:24:00 【A goose】
Matching tool
ACL( Access control list )
See
Relevant orders supplement
Use time-range Tool set time range
[R1]time-range qyt 8:30 to 17:30 working-day ACL--- Examples of matching time ranges
[R1-acl-basic-2000]rule 5 permit time-range qyt source 1.1.1.1 0 IP-Prefix List(IP The prefix list )
IP The prefix list (IP-Prefix List) Is the network address of the routing entry 、 Mask length as a filter for matching , It can be used when routing protocols publish and receive routes .
differ ACL,IP-Prefix List Can match at the same time IP Address prefix length and mask length , Enhanced the accuracy of matching .

1、ip-prefix-name: Address prefix list name
2、 Serial number : The sequence number of this match in the address prefix list , Match according to the sequence number from small to large
3、 action :permit/deny, The matching mode of the address prefix list is allow / Refuse , Represents a match / Mismatch
4、IP Network segment and mask : The network address matching the route , And limit the number of the first digits of the network address to be strictly matched
5、 Mask range : Match the route prefix length , Matching range of mask length mask-length<=greater-equal-value<=less-equal-value<=32.greater-equal Represents greater than or equal to ,less-equal-value Represents less than or equal to , The minimum value is the mask value set previously , The maximum value is 32. Indicates that the capture set mask value is up to 32 Mask range between .
Strategy tools
Filter-Policy( Filter - Strategy )
Filter-Policy( Filter - Strategy ) It is a very common routing information filtering tool , Be able to receive 、 Release 、 The introduced route is filtered , It can be applied to IS-IS、OSPF、BGP Such agreement .
See
2022-05-25 Advanced network engineering ( 7、 ... and )OSPF- Factors that affect the establishment of neighborhood relations 、 Route revocation 、 Route summary 、 Route filtering 、Silent-Interface、 Message authentication _ Goose blog -CSDN Blog _ospf Message authentication Route aggregation route aggregation is also called route aggregation , That is to aggregate a group of routes with the same prefix into one route , So as to reduce the size of routing table and optimize the utilization of equipment resources , We call this group of routes before convergence as fine routing or detailed routing , The route after aggregation is called aggregation route or aggregation route .OSPF The type of route summary is ABR Execute route summary : Perform route summary for routes between regions . stay ASBR Execute route summary : Perform route summary on the incoming external routes . stay NSSA Area ,ABR It's also execution ASBR A summary of the . It's right 7 After class aggregation, it is converted to 5 class . The relevant orders are in ABR Execute route summary [R1-ospf-1-https://blog.csdn.net/x629242/article/details/124624154#t62022-06-28 Advanced network engineering ( 13、 ... and )IS-IS- Route filtering 、 Route summary 、 authentication 、 influence ISIS The factors of establishing neighborhood relationship 、 Other commands and features _ Goose blog -CSDN Blog IS-IS The protocol and OSPF You can also filter routes , Filter in and out directions respectively . In direction out direction IS-IS The protocol and OSPF Route summary can also be carried out . The level added after the summary indicates the area to be published IS-IS Authentication is an authentication method based on the requirements of network security , By means of IS-IS The authentication field is added in the message to authenticate the message . When the local router receives the message sent by the remote router IS-IS message , If the authentication passwords do not match , Then discard the received message , To achieve the goal of self-protection . Interface authentication : Configure... In the interface view , Yes Level-1 and Level-2 Of Hello Message authentication . District
https://blog.csdn.net/x629242/article/details/125502592#t0 In addition to the above blog posts, you can call the matching tool ACL, You can also call the matching tool IP-Prefix List
for example
[R1]ip ip-prefix qyt index 5 permit 1.1.1.1 24 greater-equal 26 less-equal 30
[R1-ospf-1]filter-policy ip-prefix qyt export Route-Policy( route - Strategy )
Route-Policy It's a strategic tool , be used for Filter routing information , And for the filtered routing information Set routing properties .
One Route-Policy from One or more nodes (Node) constitute , Each node can be a series Conditional statements ( Matching condition ) as well as Execute statement ( Executive action ) Set , These sets are numbered from small to large .
Each node can contain multiple conditional statements . Between multiple conditional statements within a node The relationship is “ And ”, That is, only when all conditional statements are matched can the actions in this node be executed .
The relationship between nodes by “ or ”,route-policy Execute from small to large according to the node number and size , A node in the match will not continue to match downward .
Route-Policy The composition of
One Route-Policy Composed of one or more nodes .
for example
[R1]route-policy qyt permit node 5permit or deny: Appoint Route-Policy The matching mode of nodes is allow or deny .
node: Appoint Route-Policy Node number of . Integer form , The value range is 0~65535.
Each node includes multiple if-match and apply Clause .
for example
[R1-route-policy]if-match ip-prefix qyt
[R1-route-policy]apply cost 10if-match Clause : Define the matching criteria for this node .
apply Clause : Define the operation to be performed on the matched route .
notes :Route-Policy Can be Filter-Policy call
边栏推荐
- ActiveMQ的基础
- Simulation scheduling problem of SystemVerilog (1)
- UE source code analysis: uccharactermovementcomponent - rootmotion
- 第一章:求所有阶乘和数,大奖赛现场统分程序设计,三位阶乘和数,图形点扫描,递归求n的阶乘n!,求n的阶乘n!,舍罕王失算
- 第二章:求a,b的最大公约与最小公倍数经典求解,求a,b的最大公约与最小公倍数常规求解,求n个正整数的的最大公约与最小公倍数
- Luogu-p1107 [bjwc2008] Lei Tao's kitten
- 第一章:三位阶乘和数,图形点扫描
- FBI warning: some people use AI to disguise themselves as others for remote interview
- 2022-06-25 网工进阶(十一)IS-IS-三大表(邻居表、路由表、链路状态数据库表)、LSP、CSNP、PSNP、LSP的同步过程
- 第二章:求长方体数组,指定区间内的完全数,改进指定区间内的完全数
猜你喜欢
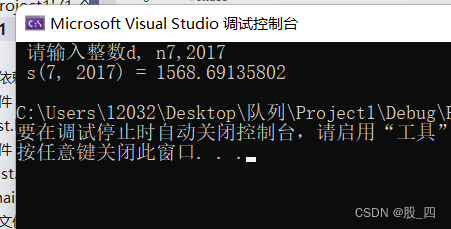
第一章:简化同码小数和s(d, n)

If the warehouse management communication is not in place, what problems will occur?
![[proteus simulation] a simple encrypted electronic password lock designed with 24C04 and 1602LCD](/img/51/209e35e0b94a51b3b406a184459475.png)
[proteus simulation] a simple encrypted electronic password lock designed with 24C04 and 1602LCD
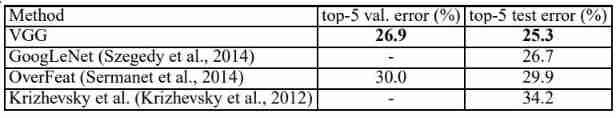
Thesis study - 7 Very Deep Convolutional Networks for Large-Scale Image Recognition (3/3)

【数学建模】基于matlab船舶三自由度MMG模型【含Matlab源码 1925期】

2022-06-30 网工进阶(十四)路由策略-匹配工具【ACL、IP-Prefix List】、策略工具【Filter-Policy】
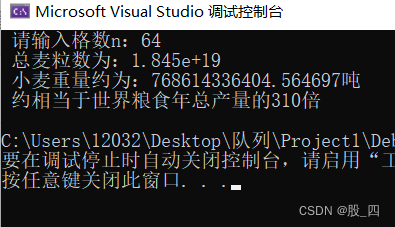
第一章: 舍罕王失算

FBI警告:有人利用AI换脸冒充他人身份进行远程面试
![[optics] dielectric constant calculation based on MATLAB [including Matlab source code 1926]](/img/cb/ee696d5a7d6bef96fe0db89e8478ed.jpg)
[optics] dielectric constant calculation based on MATLAB [including Matlab source code 1926]

东数西算拉动千亿产业,敢啃“硬骨头”的存储厂商才更有机会
随机推荐
Flutter network and data storage framework construction-b1
Free year-end report summary template Welfare Collection
Cross compile opencv with contrib
Zhang Fei hardware 90 day learning notes - personal records on day 2, please see my personal profile / homepage for the complete
Webrtc[41] - Analysis of the establishment process of webrtc transmission channel
PR FAQ: how to set PR vertical screen sequence?
Chapter 1: recursively find the factorial n of n!
第一章:求n的阶乘n!
Yolov3 network model building
During MySQL installation, the download interface is empty, and the components to be downloaded are not displayed. MySQL installer 8.0.28.0 download interface is empty solution
Summary of learning materials and notes of Zhang Fei's actual combat electronics 1-31
Chapter 1: find the factorial n of n!
Compared with 4G, what are the advantages of 5g to meet the technical requirements of industry 4.0
2022.2.14 Li Kou - daily question - single element in an ordered array
Zhang Fei hardware 90 day learning notes - personal record on day 5. Please see my personal profile / homepage for the complete record
Leetcode 1189. Maximum number of balloons (special character count)
Zhang Fei hardware 90 day learning notes - personal record of day 3, please see my personal profile / homepage for the complete
2022-06-25 网工进阶(十一)IS-IS-三大表(邻居表、路由表、链路状态数据库表)、LSP、CSNP、PSNP、LSP的同步过程
Analyse du Code du planificateur ego bspline Section Optimizer (1)
What does a really excellent CTO look like in my eyes