当前位置:网站首页>Uva536 binary tree reconstruction tree recovery
Uva536 binary tree reconstruction tree recovery
2022-07-04 12:25:00 【Harmful Poems】
Enter the sequence of preorder traversal and middle order traversal of a binary tree , Output its post order traversal sequence .
#include<bits/stdc++.h>
using namespace std;
string preorder,inorder;
void postorder(string pre,string in){
if(pre.size() <= 0){
return ;
}
int len = 0;
len = in.find(pre[0]);
postorder(pre.substr(1,len),in.substr(0,len));
postorder(pre.substr(len+1).in.substr(len+1));
cout<<pre[0];
}
int mian(){
while(cin>>preorder>>inorder){
postorder(preorder,inorder);
cout<<endl;
}
return 0;
}
#include<bits/stdc++.h>
using namespace std;
string preorder,inorder;
void postorder(int l1,int l2,int n){
if(n <= 0){
return ;
}
int len = 0;
int len = inorder.find(preorder[l1]) - l2;
postorder(l1+1,l2,len);
postorder(l1+len+1,l2+len+1,n-len-1);
cout<<preorder[l1];
}
int mian(){
while(cin>>preorder>>inorder){
int len = preorder.size();
postorder(0,0,len);// Preamble start subscript , Middle order start subscript , length
cout<<endl;
}
return 0;
}
边栏推荐
- Global function Encyclopedia
- Classification and application of AI chips
- A few words explain redis cache penetration, breakdown, avalanche, and redis sentinel
- Xshell's ssh server rejected the password, failed to skip publickey authentication, and did not register with the server
- MySQL advanced (Advanced) SQL statement
- Source code analysis of the implementation mechanism of multisets in guava class library
- C language compilation process
- About the use of URL, href, SRC attributes
- Lecture 9
- Day01 preliminary packet capture
猜你喜欢

Star leap plan | new projects are continuously being recruited! MSR Asia MSR Redmond joint research program invites you to apply!

OSI seven layer model & unit
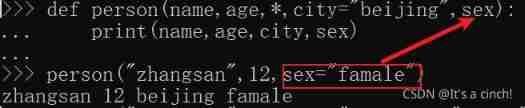
Function parameters (positional parameters, default value parameters, variable parameters, named keyword parameters, keyword parameters)
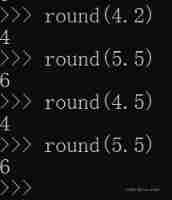
Global function Encyclopedia
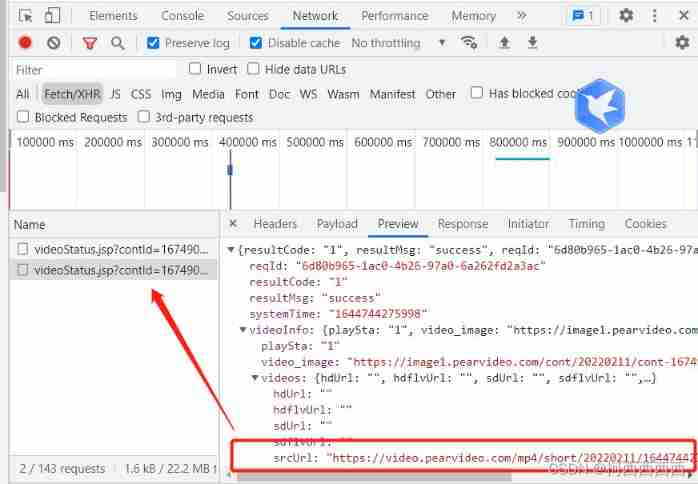
Reptile learning winter vacation series (2)
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 22](/img/e0/21367eeaeca10c0a2f2aab3a4fa1fb.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 22
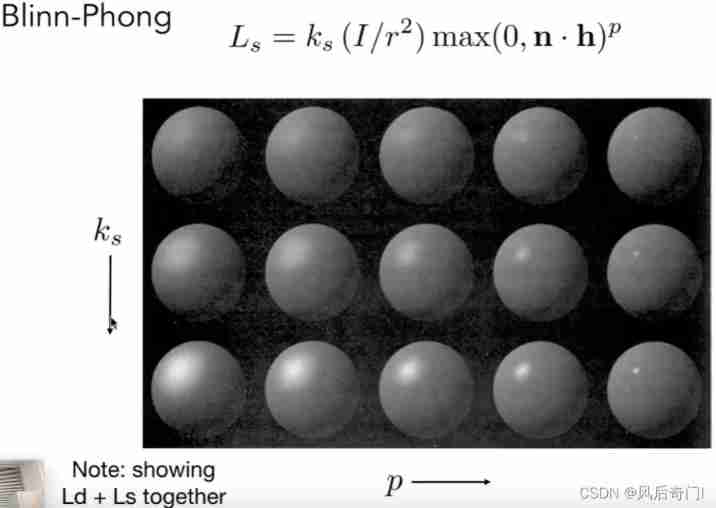
Games101 Lesson 8 shading 2 Notes
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 5](/img/68/4f92ca7cbdb90a919711b86d401302.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 5
os. Path built-in module
Source code analysis of the implementation mechanism of multisets in guava class library
随机推荐
(August 9, 2021) example exercise of air quality index calculation (I)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 11
. Does net 4 have a built-in JSON serializer / deserializer- Does . NET 4 have a built-in JSON serializer/deserializer?
LxC shared directory addition and deletion
Azure solution: how can third-party tools call azure blob storage to store data?
Force buckle 142 Circular linked list II
What if the chat record is gone? How to restore wechat chat records on Apple Mobile
Dos and path
Entitas learning [iv] other common knowledge points
Review of week 278 of leetcode II
C language compilation process
In 2022, financial products are not guaranteed?
priority_ queue
Exness: positive I win, negative you lose
Bottom Logic -- Mind Map
French Data Protection Agency: using Google Analytics or violating gdpr
Common built-in modules
Local MySQL forget password modification method (Windows) [easy to understand]
(August 10, 2021) web crawler learning - Chinese University ranking directed crawler
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 8