当前位置:网站首页>The detailed installation process of Ninja security penetration system (Ninjitsu OS V3). Both old and new VM versions can be installed through personal testing, with download sources
The detailed installation process of Ninja security penetration system (Ninjitsu OS V3). Both old and new VM versions can be installed through personal testing, with download sources
2022-07-04 12:09:00 【Black zone (rise)】
I thought there was only a new version vm15 To install and successfully start the Ninja system ,
But my vm12 It can also be installed and successfully started
Mirror download link :( Image source :https://blog.csdn.net/qq_35258210/article/details/115457883)
https://pan.baidu.com/s/1CAw9ztIUhCZgydNWHHWINg
password : a33b
This article is more detailed and suitable for novices , about vm Less frequently used .
First step :
vm Create a new virtual machine in
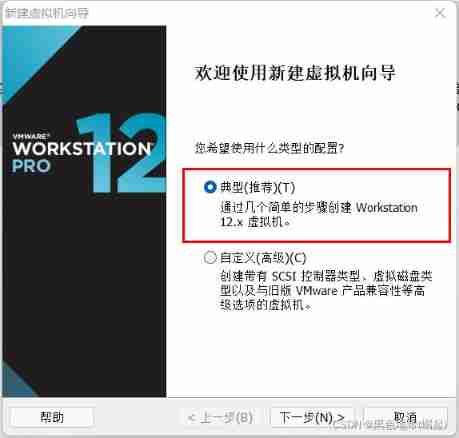
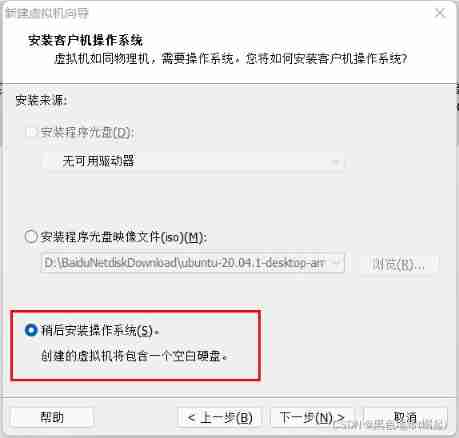
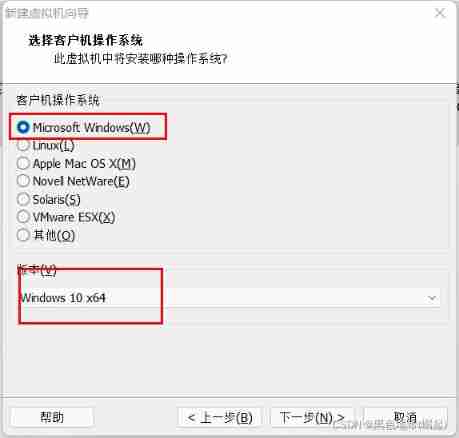
Name yourself , Then choose the location you want to install , It is best to unify the location of virtual machines , Convenient for future sorting
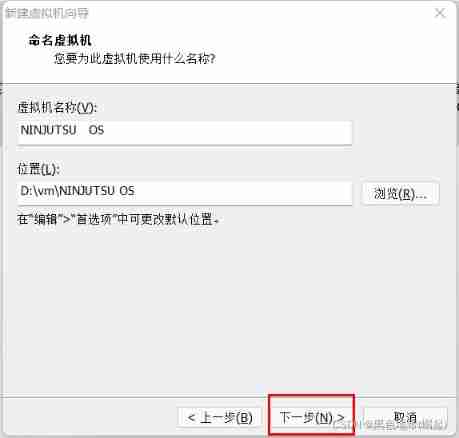
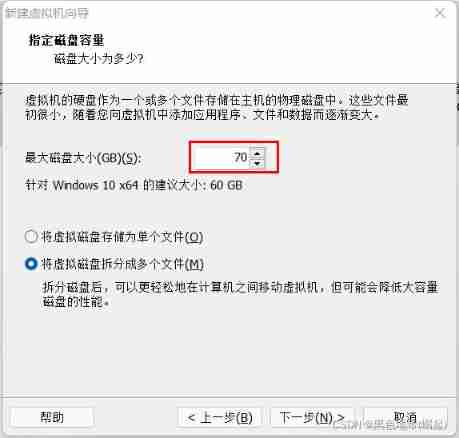
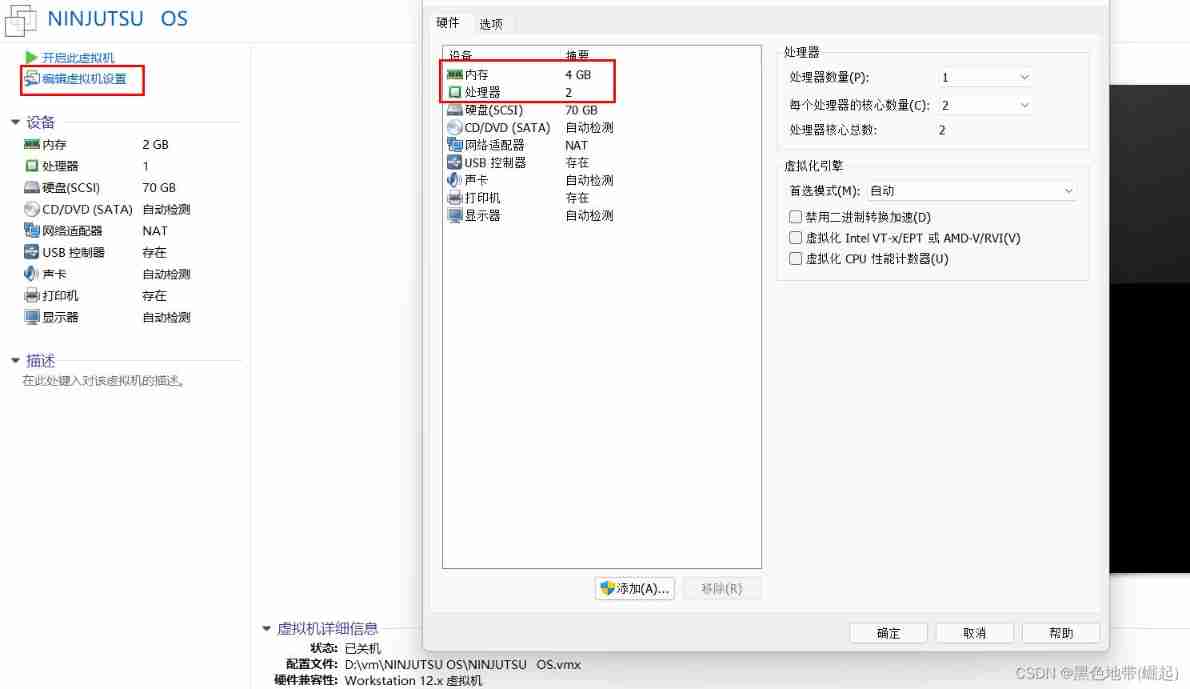
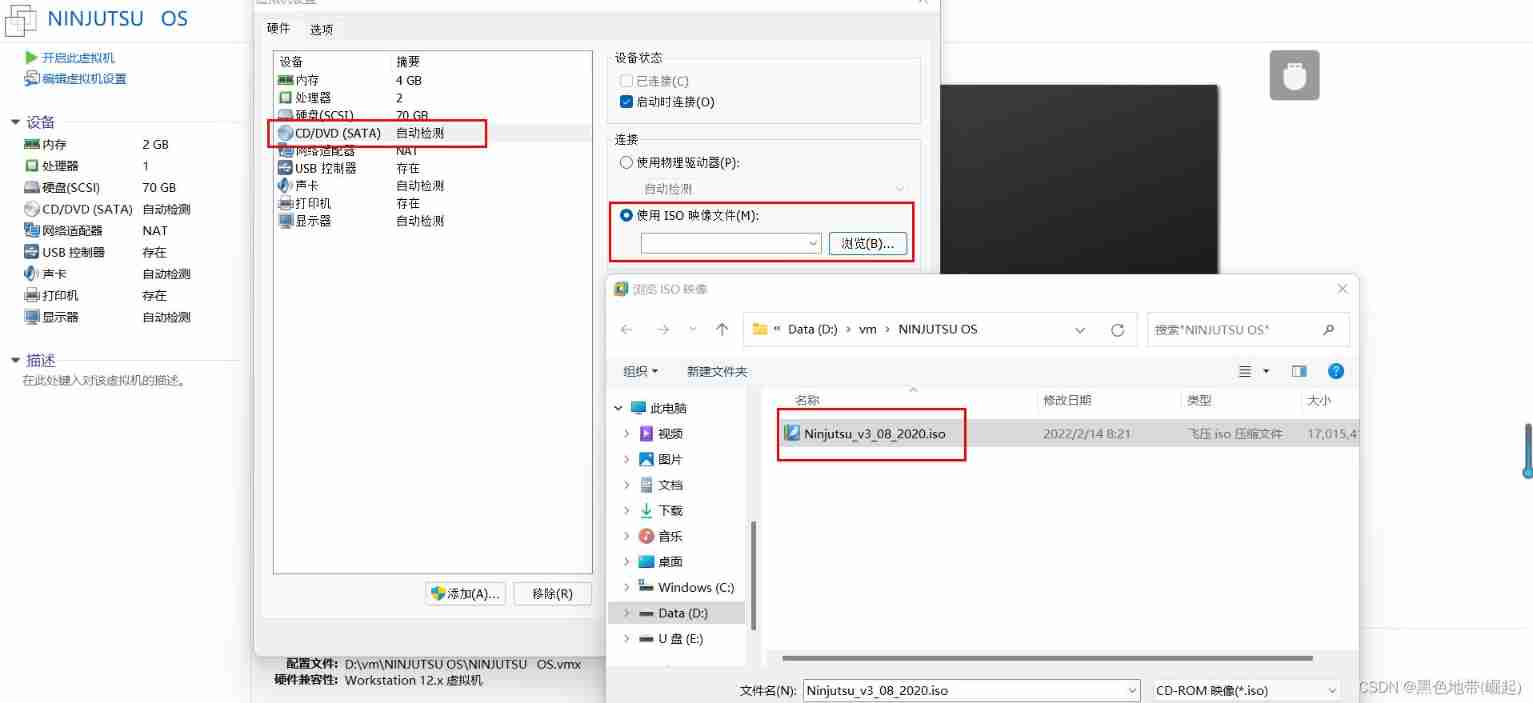
The second step :
System installation
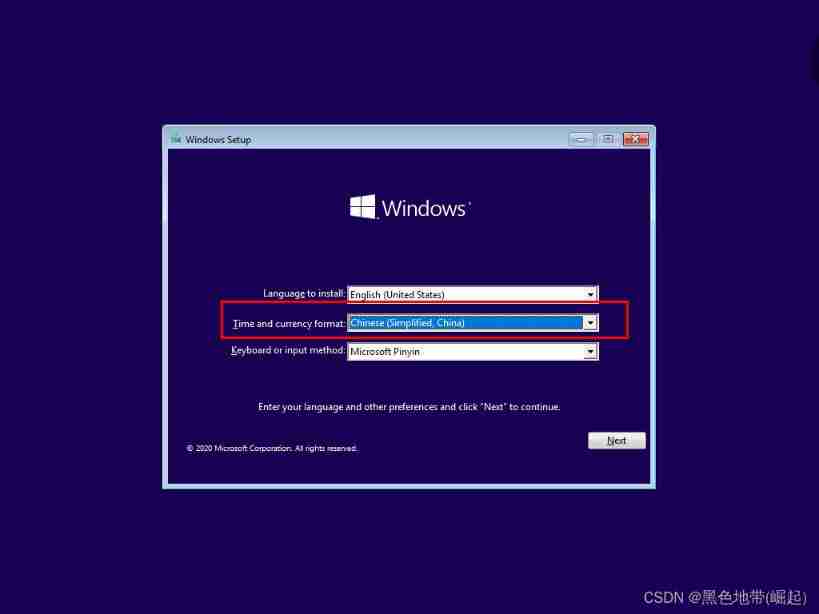
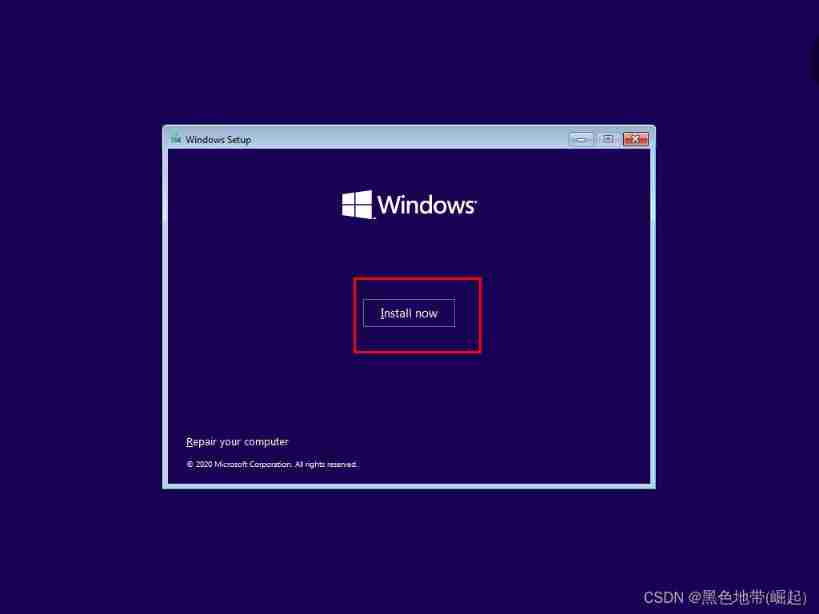
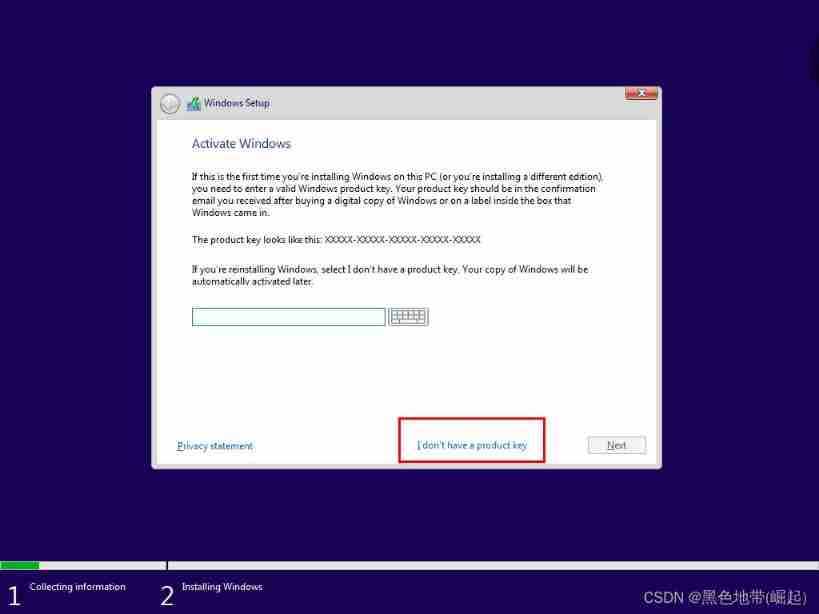
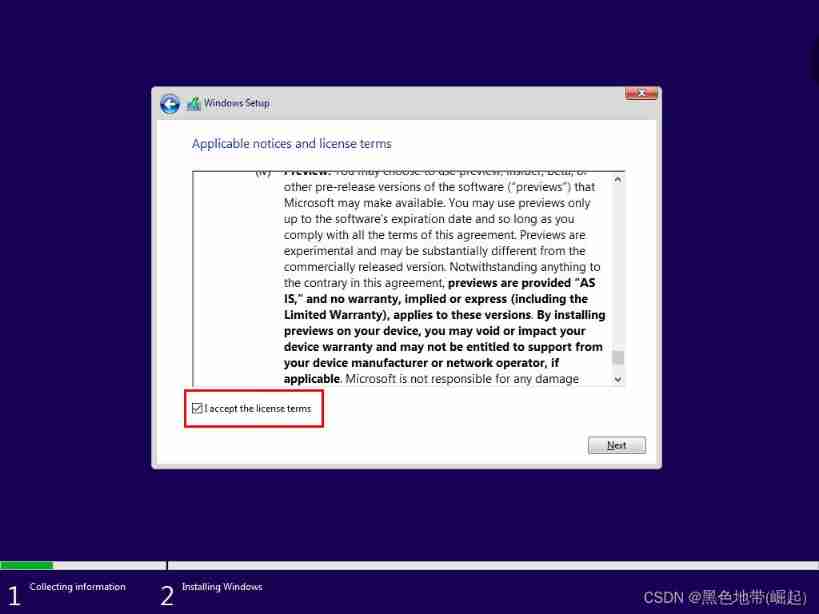
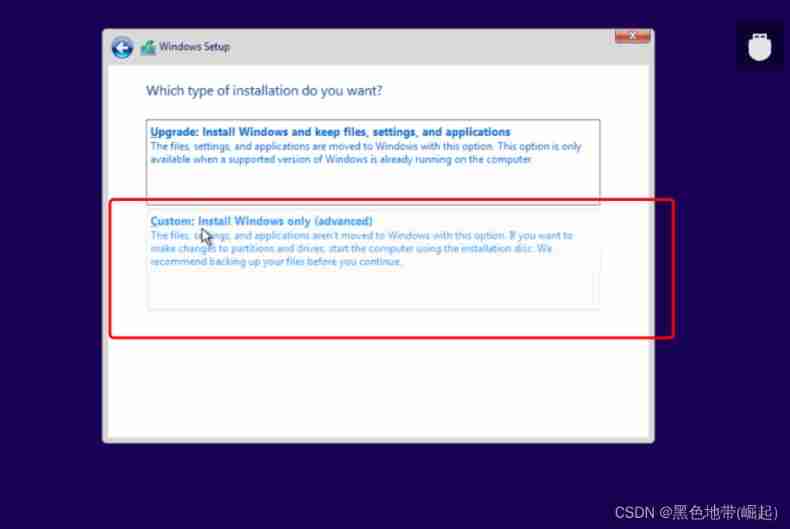
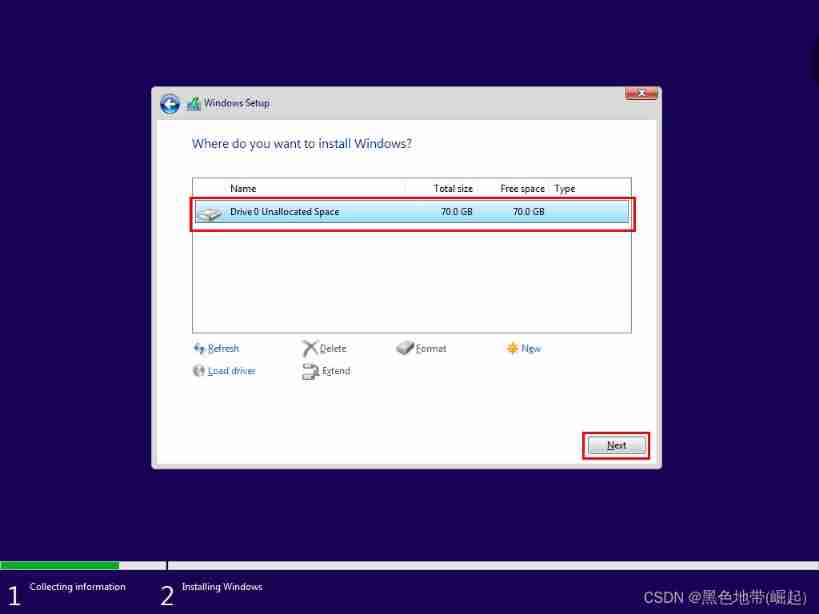
Wait for the installation to complete
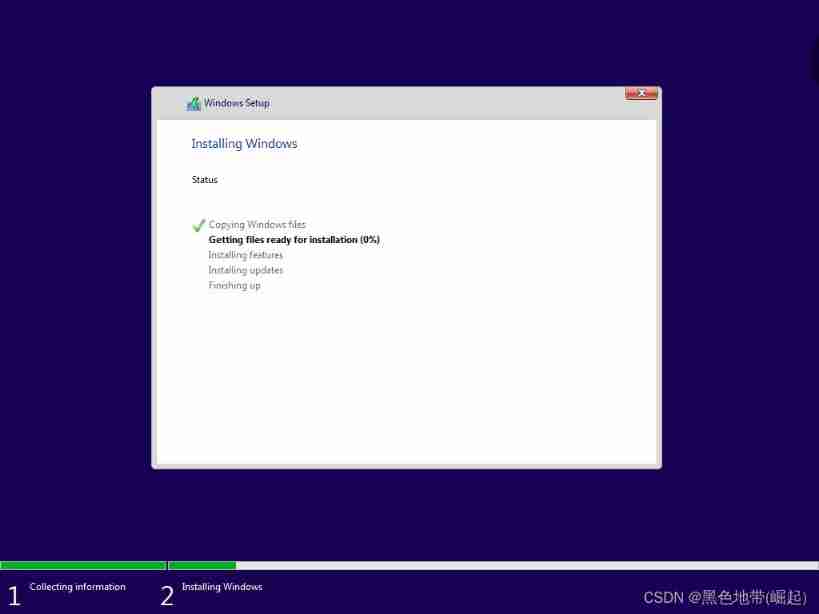
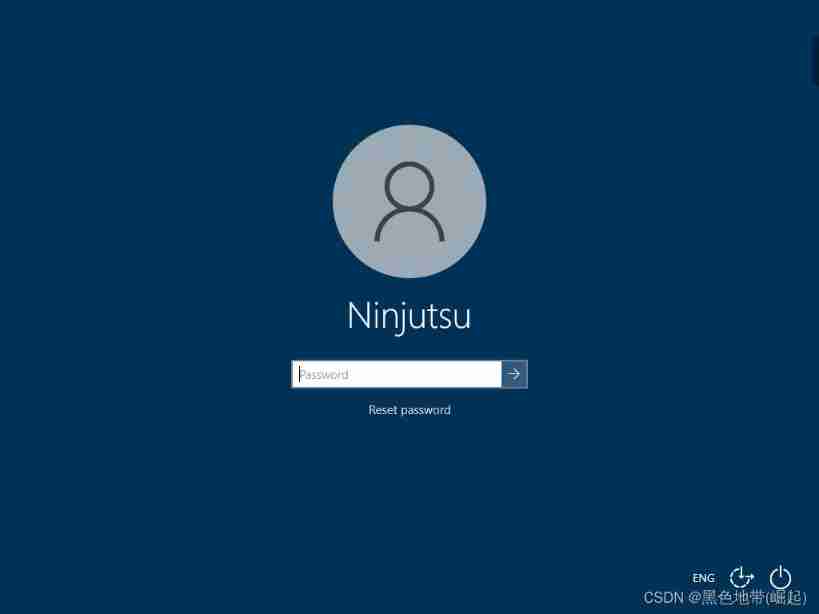
After installation , Unlock code toor

The third step :
Install the Chinese language pack
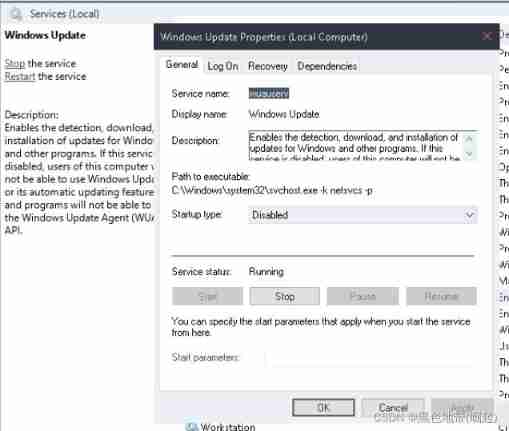
win+R Input services.msc Enter key

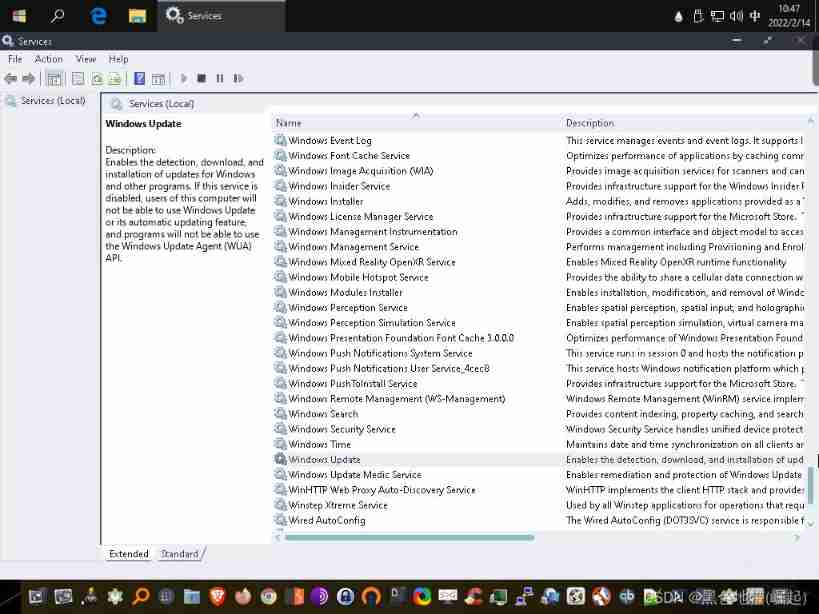
find windows update, double-click , Select the second one and click apply, Click again start, Point again ok
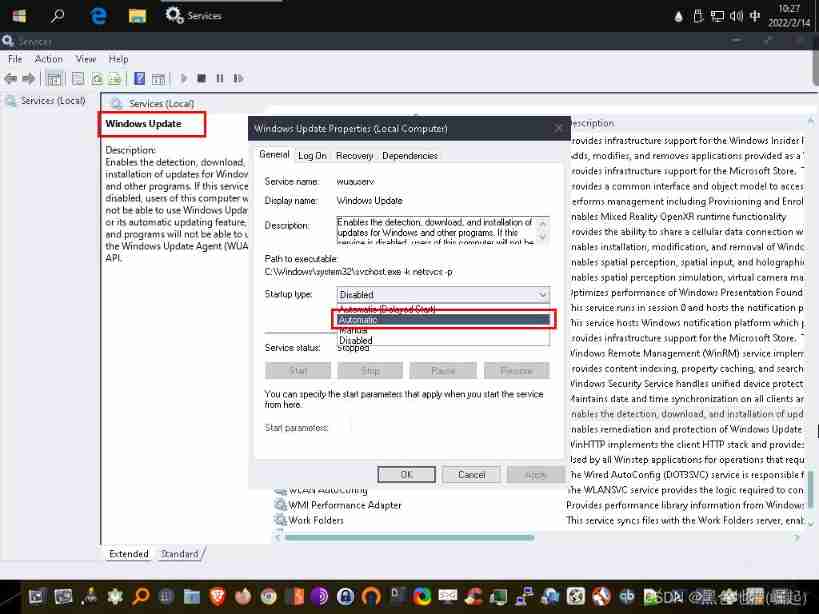
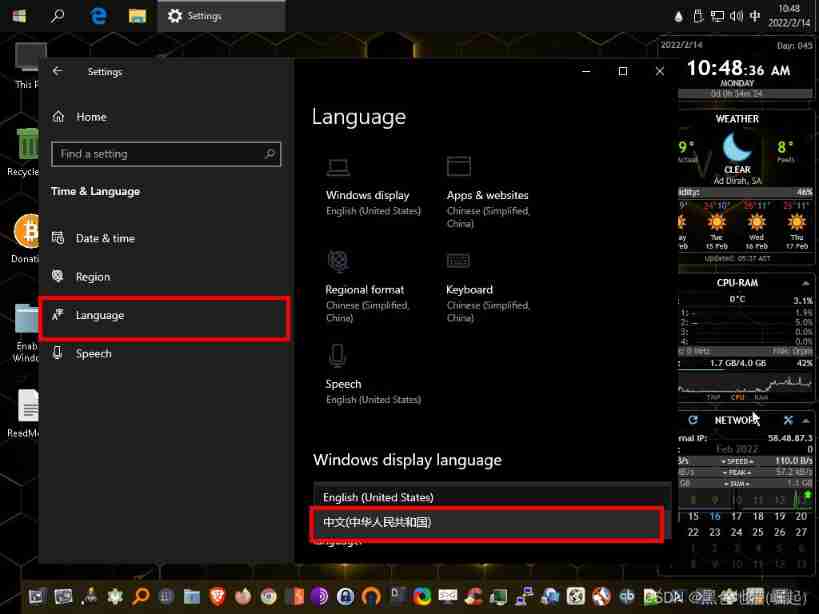
Find the language setting page in the setting interface 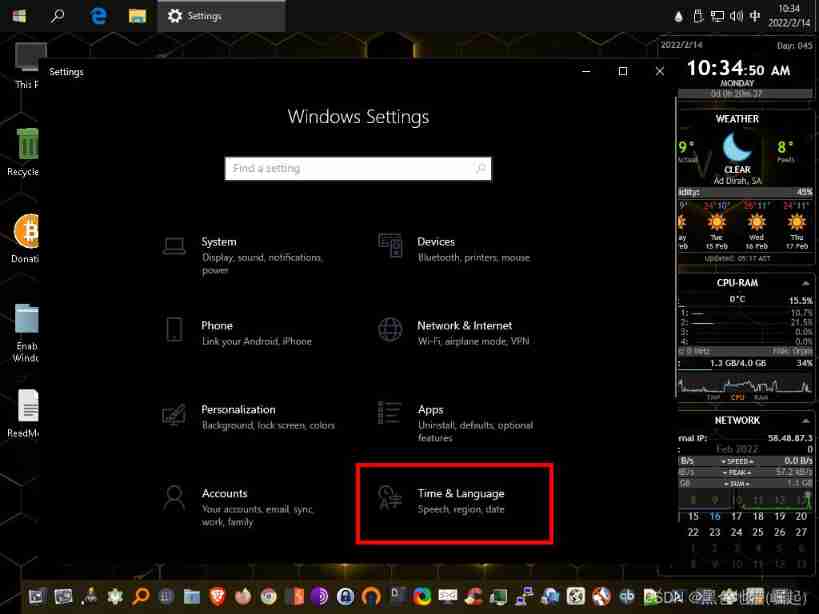
If you do not choose Chinese when installing the system
Just add a language ( Skip this step if you have chosen )
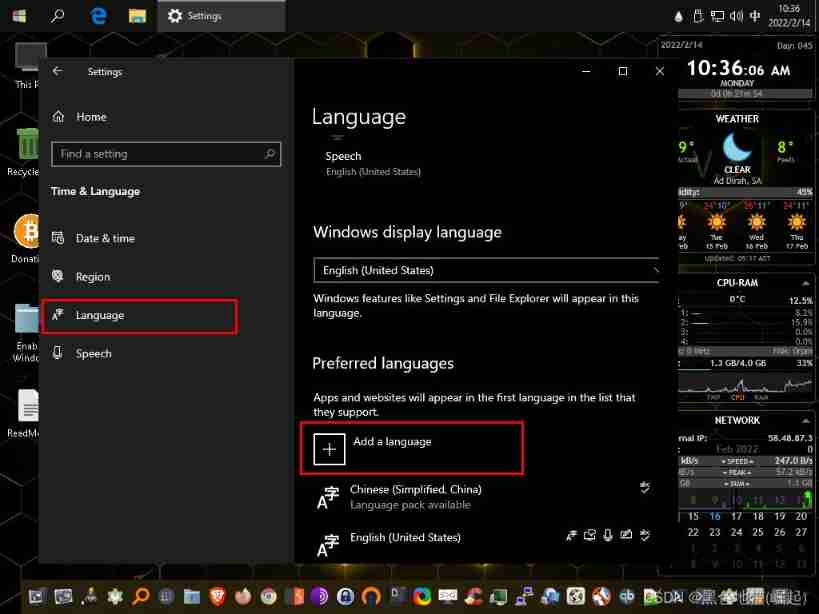
options Options 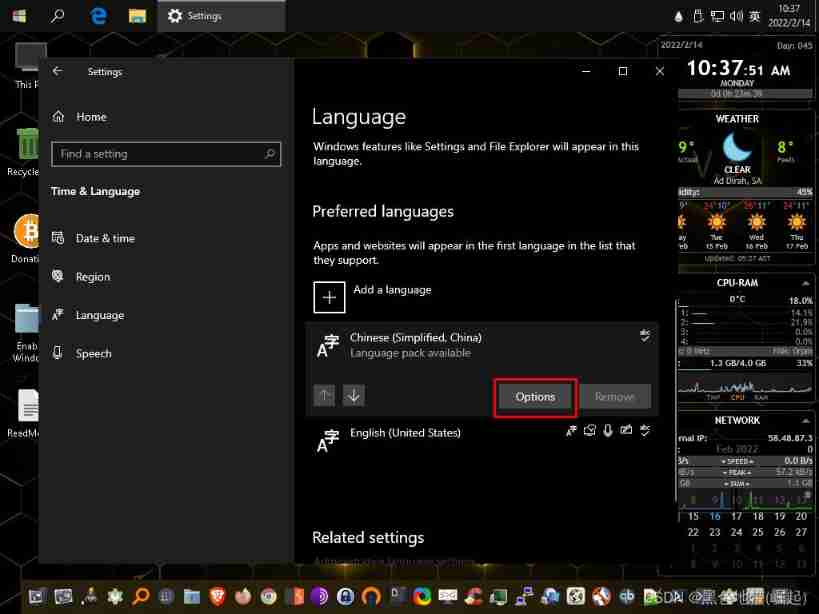
Click to download
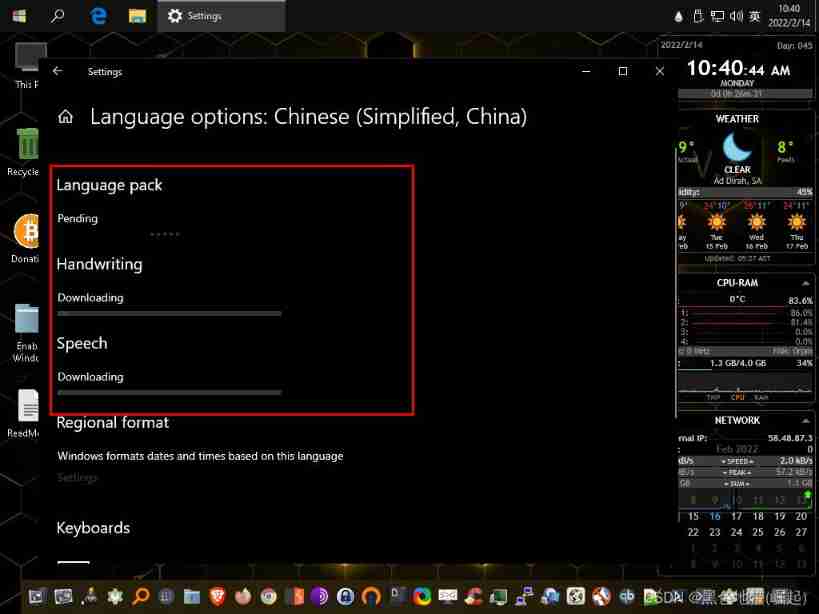
Close the system update after downloading , Select the last click apple, Click again OK, Again stop
Enter the language setting interface , Choose Chinese
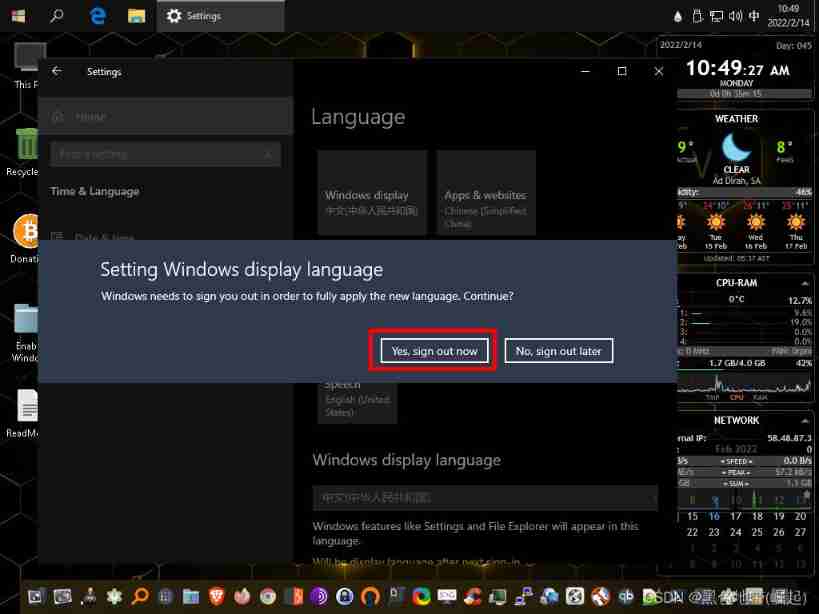
After selection , Just re-enter ok 了
边栏推荐
- Summary of Shanghai Jiaotong University postgraduate entrance examination module firewall technology
- Global function Encyclopedia
- Map container
- Anti clockwise rotation method of event arrangement -- PHP implementation
- Sys module
- Clion configuration of opencv
- Experiment 7. IPv6
- Games101 Lesson 8 shading 2 Notes
- QQ set group information
- The frost peel off the purple dragon scale, and the xiariba people will talk about database SQL optimization and the principle of indexing (primary / secondary / clustered / non clustered)
猜你喜欢
![[the way of programmer training] - 2 Perfect number calculation](/img/fd/4bb8560f601daddaa8895f20215be4.jpg)
[the way of programmer training] - 2 Perfect number calculation
netstat

Some summaries of the 21st postgraduate entrance examination 823 of network security major of Shanghai Jiaotong University and ideas on how to prepare for the 22nd postgraduate entrance examination pr
Method of setting default items in C # ComboBox control code
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 6](/img/38/51797fcdb57159b48d0e0a72eeb580.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 6
How to create a new virtual machine

Application of slice

Here, the DDS tutorial you want | first experience of fastdds - source code compilation & Installation & Testing

The frost peel off the purple dragon scale, and the xiariba people will talk about database SQL optimization and the principle of indexing (primary / secondary / clustered / non clustered)
13、 C window form technology and basic controls (3)
随机推荐
Entitas learning [iv] other common knowledge points
Recommend a cool geospatial data visualization tool with low code
QQ group administrators
array_ The contains() function uses
Awk getting started to proficient series - awk quick start
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 8
Simple understanding of seesion, cookies, tokens
Enter the smart Park, and change begins here
Anti clockwise rotation method of event arrangement -- PHP implementation
About the use of URL, href, SRC attributes
Guava ImmutableSet. Builder source code analysis, shift original code, complement code, reverse code review
Sys module
Summary of Shanghai Jiaotong University postgraduate entrance examination module -- cryptography
Reptile learning 4 winter vacation learning series (1)
. Does net 4 have a built-in JSON serializer / deserializer- Does . NET 4 have a built-in JSON serializer/deserializer?
Review of week 278 of leetcode II
QQ get group settings
Method of setting default items in C # ComboBox control code
How to judge the advantages and disadvantages of low code products in the market?
Possible to restore a backup of SQL Server 2014 on SQL Server 2012?