当前位置:网站首页>Introduction of network security research direction of Shanghai Jiaotong University
Introduction of network security research direction of Shanghai Jiaotong University
2022-07-04 11:14:00 【loveCC_ orange】
I haven't updated my blog for a long time , Because we also need to operate official account , Other words , Even now school begins , Have been writing before NP Things to learn , Now? NP There is little time to watch , So blog is basically stopped . however , I feel I should pick it up , Continue to update , On the one hand, it is to communicate with partners in related majors , On the other hand, I force myself to study . Now it's almost a month since school starts . Next, if there is no accident , It should be updated frequently . however , Today's article , It's not about technology , It's when I was sorting out my mobile photo album today , I found that I took a lot of introductions of some research directions at the tutor selection meeting at the beginning of school , Take it out and tidy it up today , It can help the young friends who want to take the Internet Security exam of Jiaotong University next , Learn about the Network Security College of Jiaotong University in advance . Of course , I may not say everything , You can refer to the official website of the school of network security of Jiaotong University .
Overview of Network Security College of Jiaotong University
- 2000 Founded in , It is the first college established network security talent training base in China
- 2016 In, it was renamed the College of Cyberspace Security
- 2019 Countries approved in “ First class network security college ”
- The first level discipline of Cyberspace Security in China ( Soft science ranking ,2019 year 10 month )
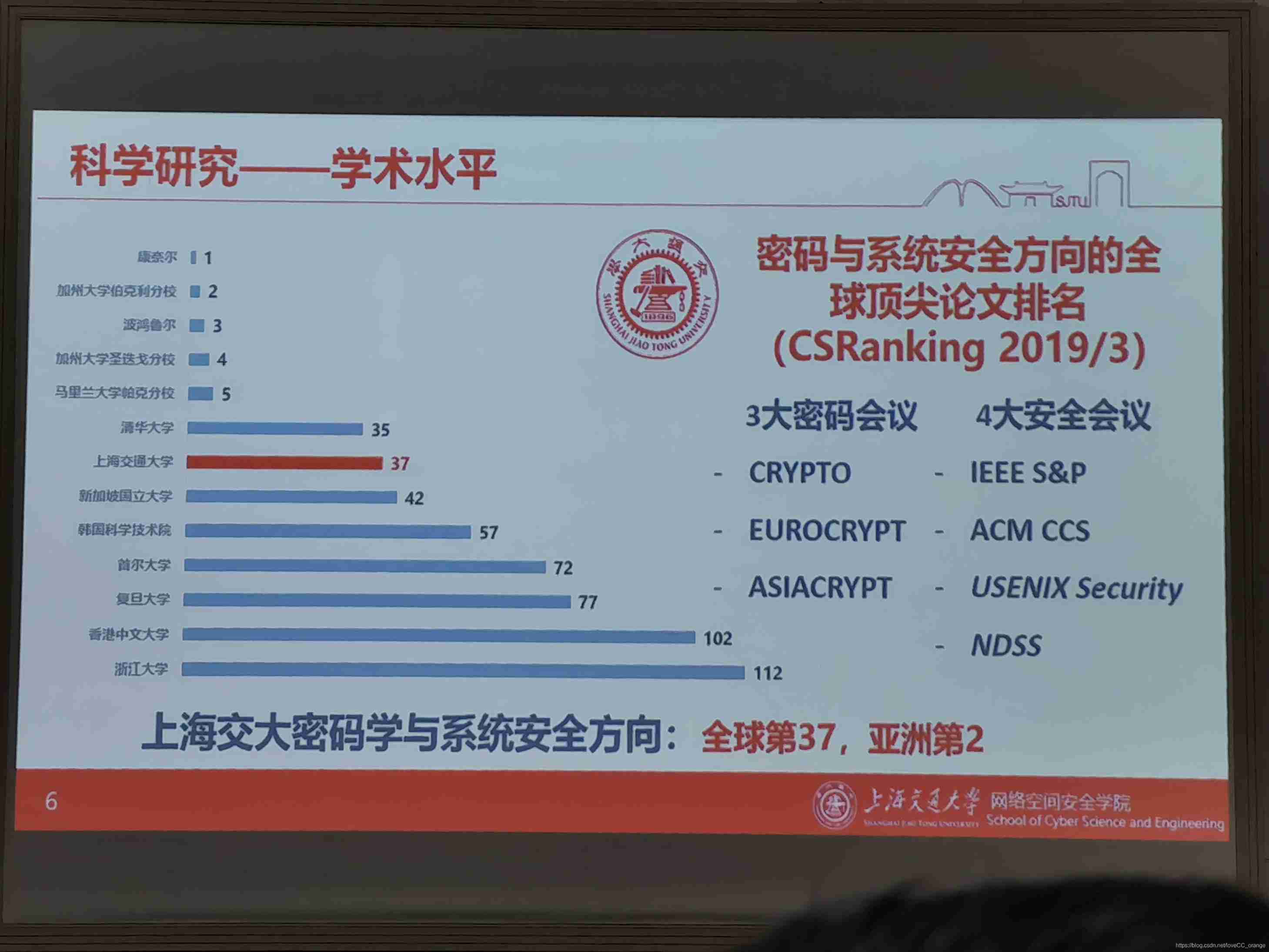
Research direction
- Blockchain and financial security
- Big data security
- Software and system security
- AI security
- Network security defense
- Cryptography science and Engineering
Laboratory Introduction
- Password and Computer Security Laboratory ( Professor gudawu is responsible for )
Research directions include :- cryptography
- software security
- Hardware security
- Network security
- Cryptanalysis and big data security laboratory ( Professor qiuweidong is responsible for )
Research directions include :- cryptanalysis / Cryptographic Engineering
- Intelligent analysis of image and video multimedia / Natural scene text processing technology
- AI Security and privacy protection
- Financial big data analysis
- Internet Measurement Technology
- Network and system security laboratory ( Professor Xue Zhi is responsible for )
Research directions include :- Network Penetration Testing Technology
- Vulnerability mining and analysis
- System security defense technology
- Safety assessment and risk assessment
- Internet Content Security Technology
- Mobile and Internet of things Security Laboratory ( Researcher Wu Yue is responsible for )
Research directions include :- after 5G Mobile communication security
- Internet of vehicles security
- Internet of things security
- Industrial control network security
- Satellite network security
- Information security and Cognition Laboratory ( Professor jiangxinghao is responsible for )
Research directions include :- Intelligent analysis and recognition technology of digital content
- Digital content Forensics Technology
- Intelligent detection technology for image countermeasure data
- Video steganography and steganalysis
- Internet of vehicles information security detection technology
- Artificial Intelligence Security Research Laboratory ( Professor liugongshen is responsible for )
Research directions include :- The application of artificial intelligence in security field : Malicious code detection, etc
- The security of AI itself : Including deep learning framework security 、 Data model security 、 Learning algorithm security, etc
- Network and system security laboratory ( Professor Li Xiaoyong is responsible for )
Research directions include :- Massive data storage system
- Big data analysis of security events
- Cloud computing and container technology
- Threat Intelligence Analysis Technology
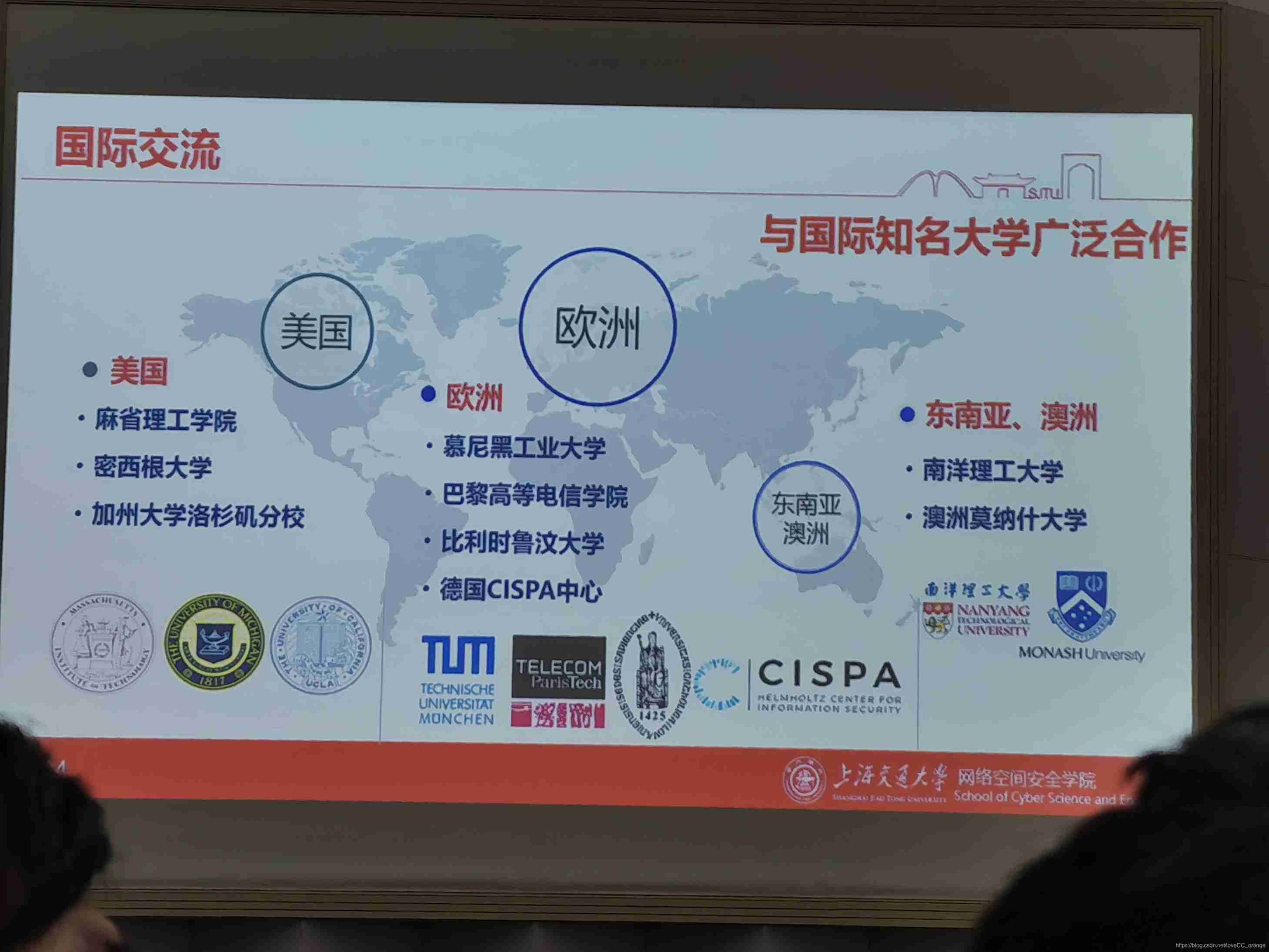

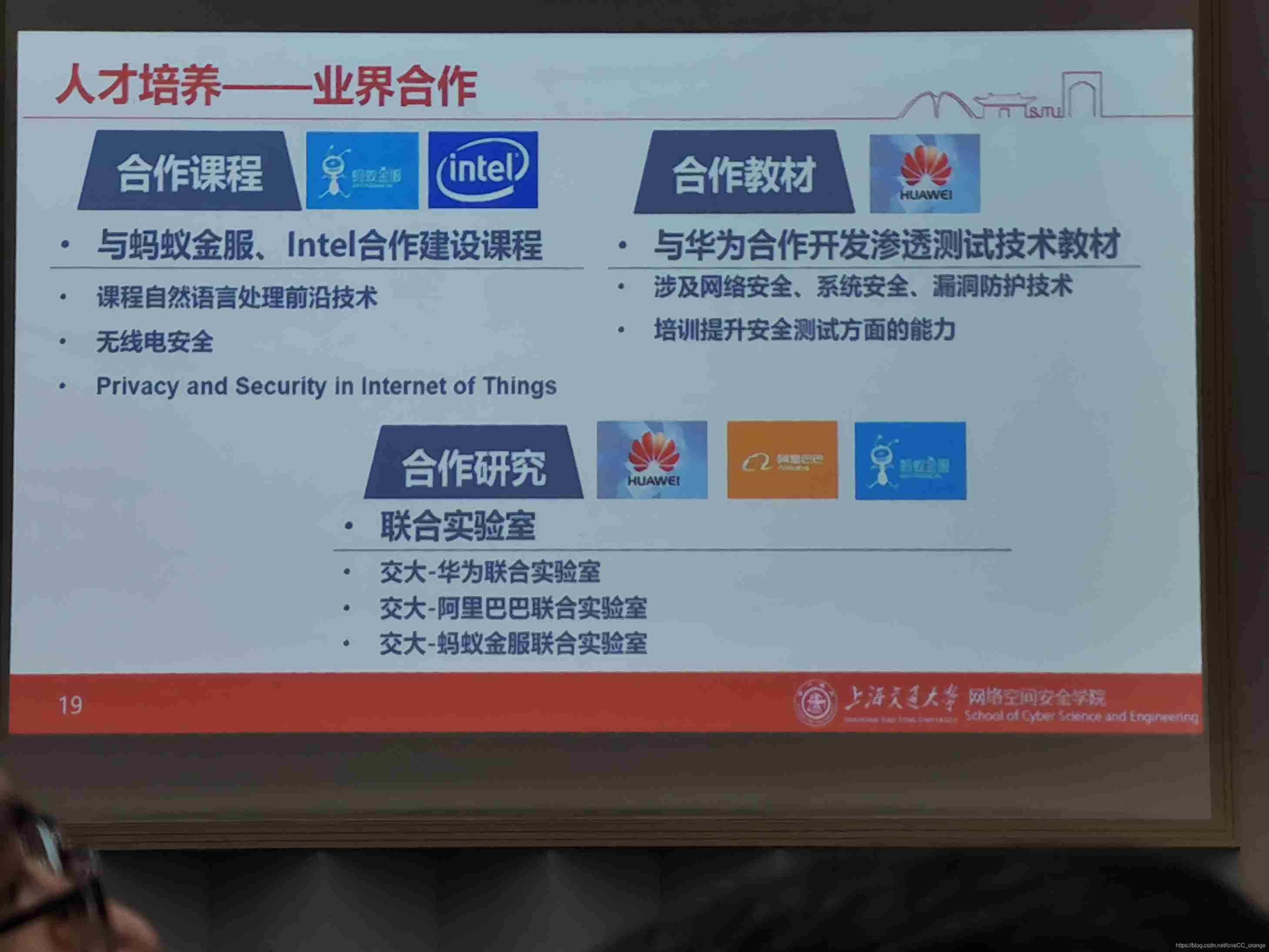
Academy of Cyberspace Security Science and Technology

This research institute is 19 year 5 In June, a research institute was separated from the original network security college , He just said , However, when recruiting students for the exam, they are recruited according to the network security college , I didn't know there was such a research institute when I applied for the exam , This has no effect on the registration , It doesn't affect your choice of tutor , It's just a research institute in name ...

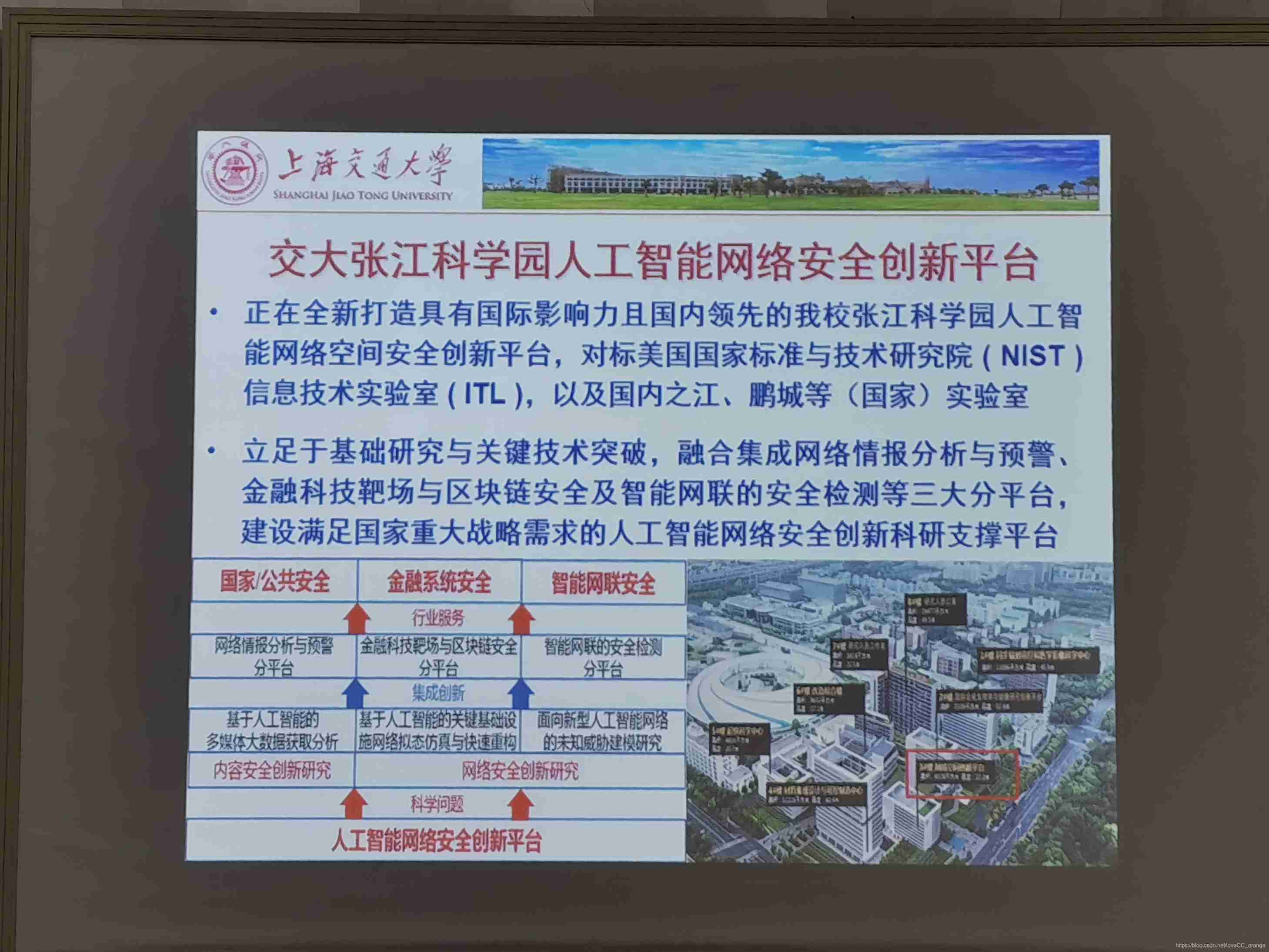
This is a base of Jiaotong University Network in Zhangjiang , It is said that it will be put into use by the end of this year , It is possible that the younger students of network security who will enter school next year may go to Zhangjiang to do scientific research , Maybe , It's just possible ... I don't know the specific situation . We are still on the main campus this year , That is, Minhang . I personally feel that Minhang is better , Infrastructure is more complete , Zhang Jiang's words , It may be more like the Institute of the Chinese Academy of Sciences , Not the environment I like too much . But the accommodation conditions , It must be better , After all, the new building , The place is also more spacious , The dormitory here is really small ..
边栏推荐
- re. Sub() usage
- QQ get group settings
- QQ get group information
- Canoe - description of common database attributes
- Simple understanding of string
- Safety testing aspects
- Four sorts: bubble, select, insert, count
- Simple understanding of seesion, cookies, tokens
- Iterator generators and modules
- Post man JSON script version conversion
猜你喜欢
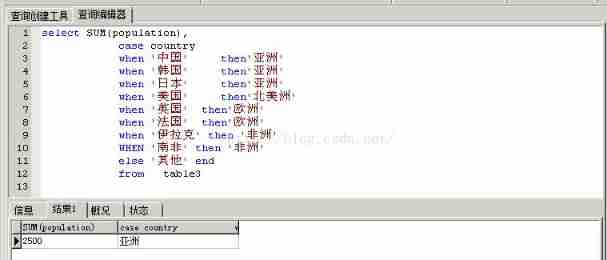
Usage of case when then else end statement
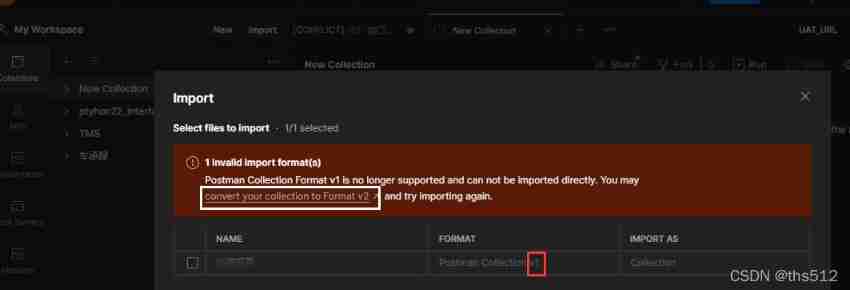
Post man JSON script version conversion
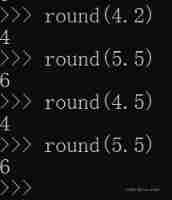
Global function Encyclopedia
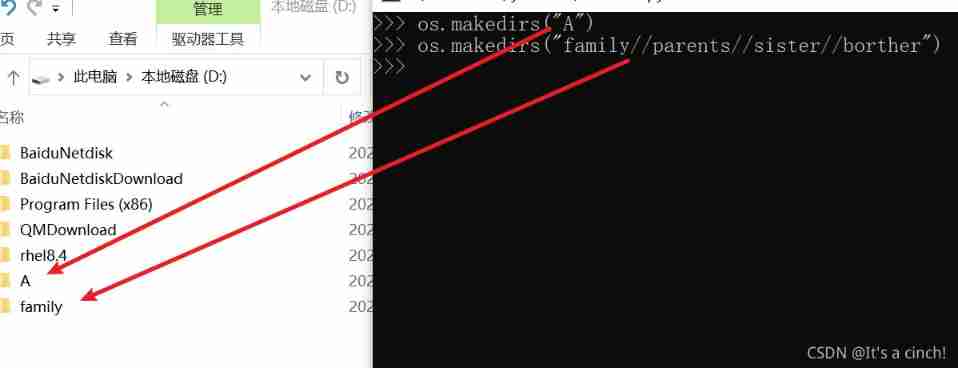
Properties and methods of OS Library
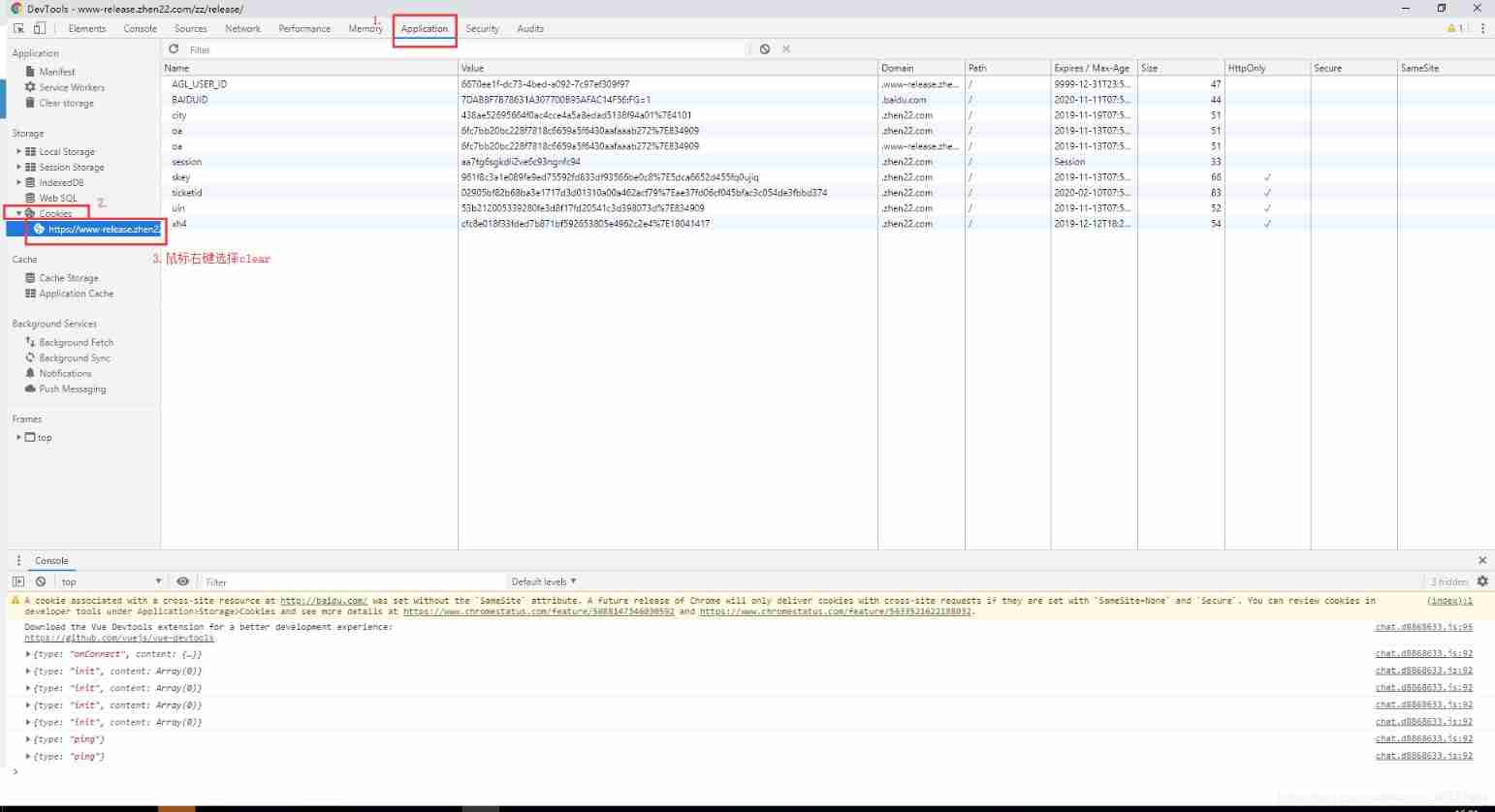
F12 clear the cookies of the corresponding web address
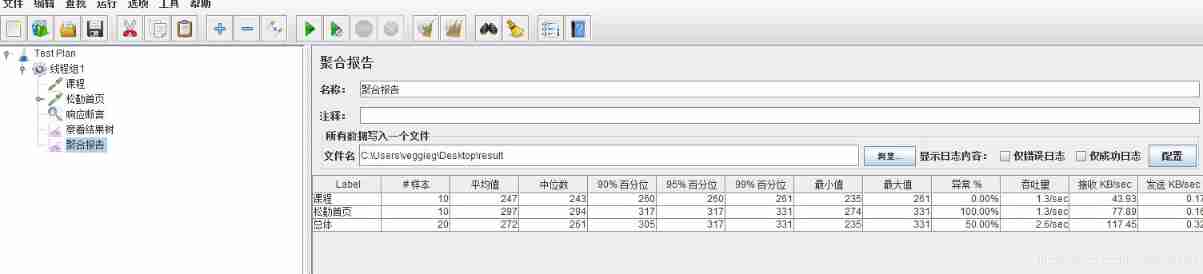
JMeter Foundation

2022 AAAI fellow release! Yan Shuicheng, chief scientist of sail, and Feng Yan, Professor of Hong Kong University of science and technology, were selected
Elevator dispatching (pairing project) ④
Oracle11g | getting started with database. It's enough to read this 10000 word analysis
Automatic translation between Chinese and English
随机推荐
Some tips on learning database
[advantages and disadvantages of outsourcing software development in 2022]
Installation of ES plug-in in Google browser
SSH原理和公钥认证
Aike AI frontier promotion (2.14)
Day7 list and dictionary jobs
本地Mysql忘记密码的修改方法(windows)[通俗易懂]
DNS hijacking
Software testing related resources
VPS installation virtualmin panel
F12 clear the cookies of the corresponding web address
2022 ape circle recruitment project (software development)
OSI seven layer reference model
Regular expression
Take advantage of the world's sleeping gap to improve and surpass yourself -- get up early
Canoe - the third simulation project - bus simulation - 2 function introduction, network topology
Performance test method
Terms related to hacker technology
thread
Supercomputing simulation research has determined a safe and effective carbon capture and storage route