当前位置:网站首页>JMeter correlation technology
JMeter correlation technology
2022-07-04 10:47:00 【dijiaye1】
Association overview
Regular expressions
() The enclosed part is to be extracted .
. Match any string
+ Once or more
? Don't be greedy , Stop after first match found
Regular expression extractor
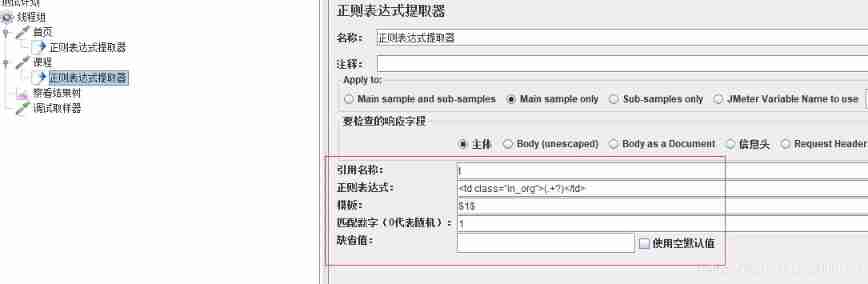
Parameters - details
Quote name : It's the variable name , Call to use ${name}
Regular expressions :() Brackets indicate the value you want
Templates :$$ Indicates the value obtained by using the regular expression template , There is only one regular general filling 1, namely $1$
Match the Numbers : Match to multiple values and take the number :-1 All ,0 Represents random ,1 Represents the first ,2 Represents the second
The default value : If this doesn't match , Define a default value for him
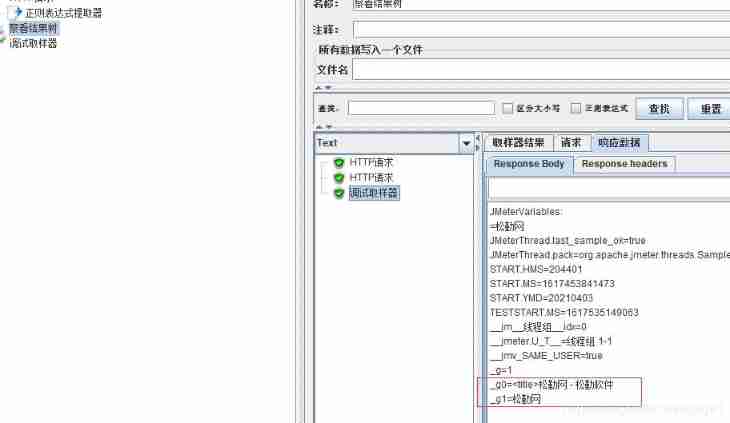
Case one
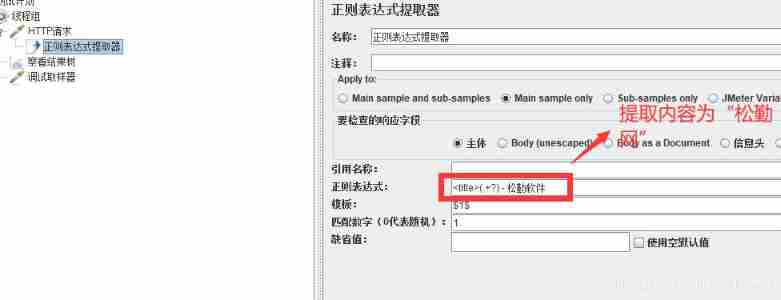
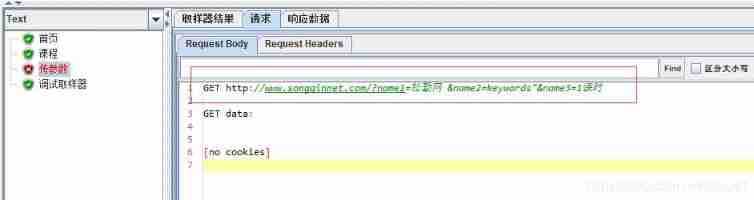
In the picture above g0 For combination ,g1 Bit single variable
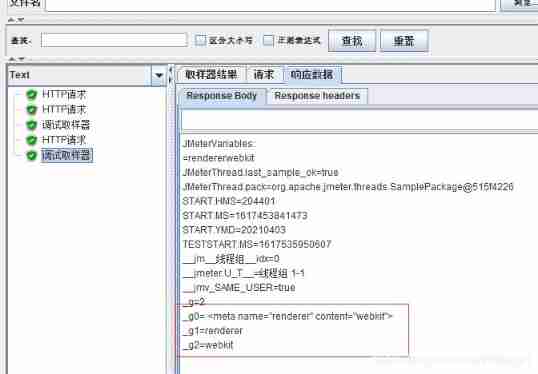
The second case
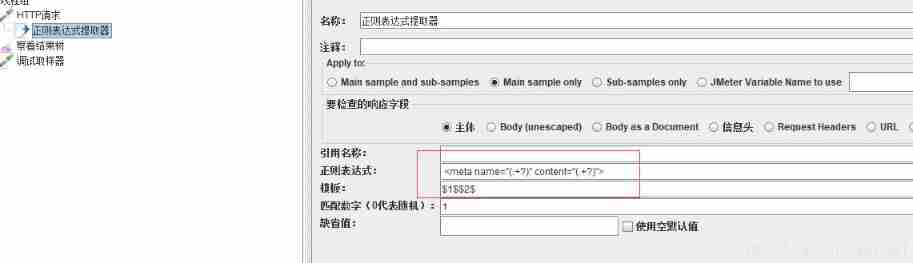
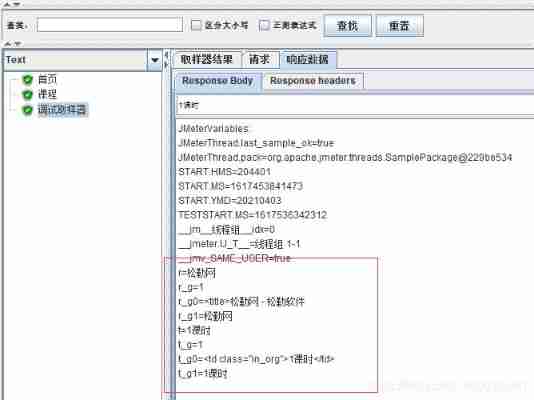
The third case , If there are two requests
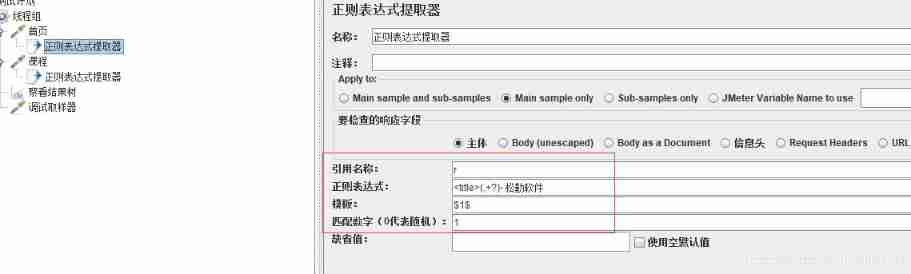
The fourth situation : The ginseng
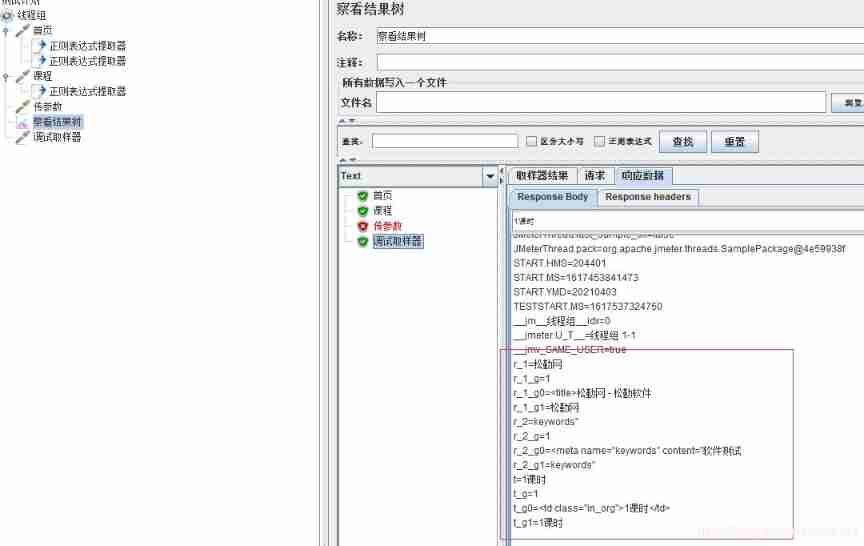
As shown in the figure above , Three regular variables , Respectively r_1、r_2、t, Write these three variables into the parameters of the parameter transfer request respectively .
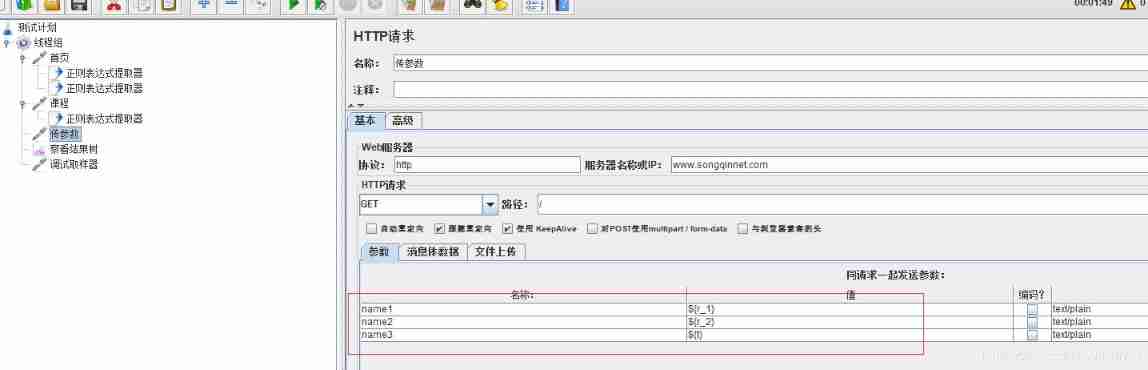
Practical cases
边栏推荐
- The bamboo shadow sweeps the steps, the dust does not move, and the moon passes through the marsh without trace -- in-depth understanding of the pointer
- Es entry series - 6 document relevance and sorting
- 如果不知道這4種緩存模式,敢說懂緩存嗎?
- Write a program to judge whether the two arrays are equal, and then write a similar program to compare the two vectors.
- Iterator generators and modules
- OSPF comprehensive experiment
- Network connection (II) three handshakes, four waves, socket essence, packaging of network packets, TCP header, IP header, ACK confirmation, sliding window, results of network packets, working mode of
- [Galaxy Kirin V10] [server] system partition expansion
- 51 data analysis post
- Latex arranges single column table pictures in double column format articles
猜你喜欢
Rhcsa learning practice
C language - stack
Architecture introduction
Realsense of d435i, d435, d415, t265_ Matching and installation of viewer environment
Three schemes of ZK double machine room
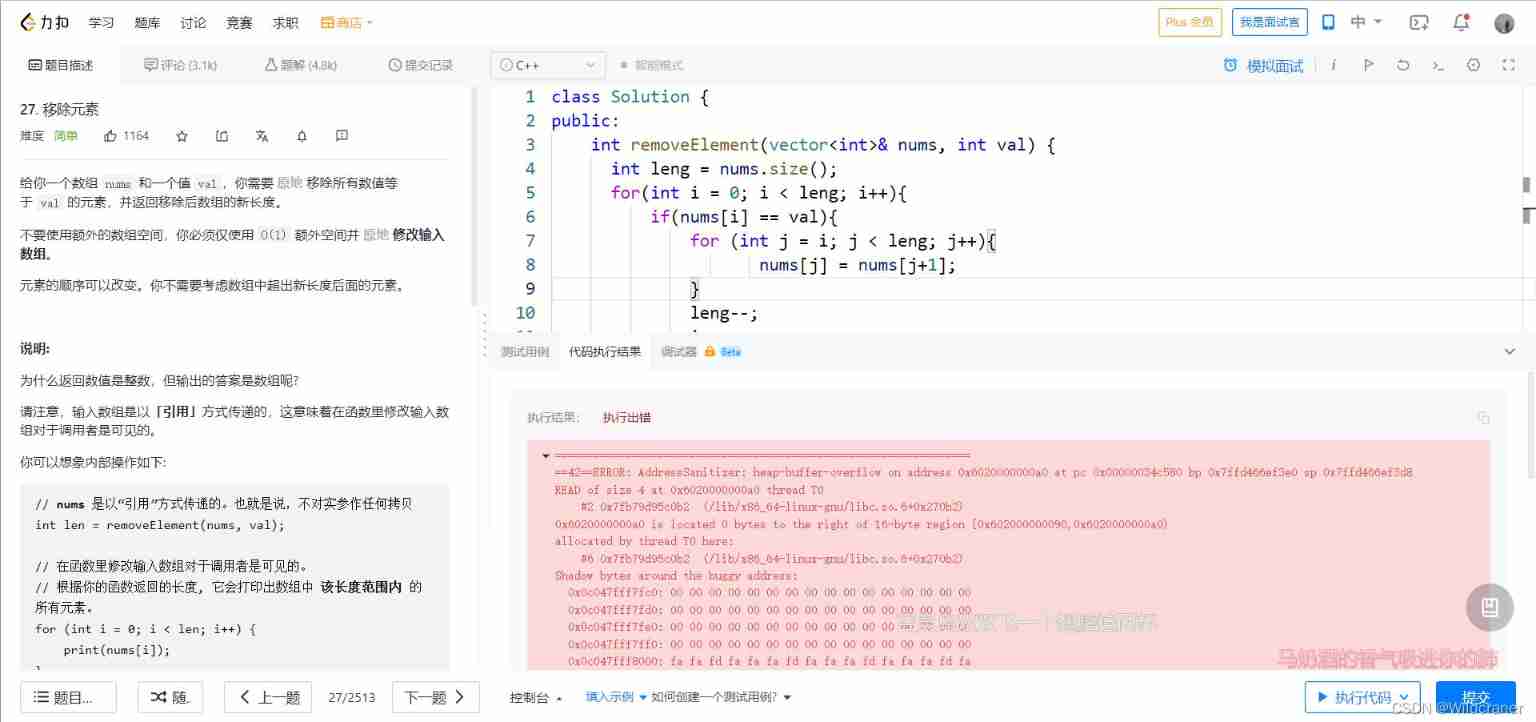
Debug:==42==ERROR: AddressSanitizer: heap-buffer-overflow on address
Si vous ne connaissez pas ces quatre modes de mise en cache, vous osez dire que vous connaissez la mise en cache?
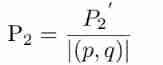
Latex error: missing delimiter (. Inserted) {\xi \left( {p,{p_q}} \right)} \right|}}
![[Galaxy Kirin V10] [server] set time synchronization of intranet server](/img/f8/0847314029930840c91bce97ccd961.jpg)
[Galaxy Kirin V10] [server] set time synchronization of intranet server
![[Galaxy Kirin V10] [desktop] build NFS to realize disk sharing](/img/72/5e725a44a50f152b477a4b2907a2d0.jpg)
[Galaxy Kirin V10] [desktop] build NFS to realize disk sharing
随机推荐
Dynamic memory management
Debug:==42==ERROR: AddressSanitizer: heap-buffer-overflow on address
Development guidance document of CMDB
Hidden C2 tunnel -- use of icmpsh of ICMP
Deepmind proposed a Zuan AI, which specially outputs network attack language
Regular expression
Recursive method to achieve full permutation (C language)
When I forget how to write SQL, I
Huge number (C language)
Jianzhi offer 04 (implemented in C language)
2022 ape circle recruitment project (software development)
Learning XML DOM -- a typical model for parsing XML documents
Write a program that uses pointers to set all elements of an int array to 4.18: 0.
Knapsack problem and 0-1 knapsack problem
If you don't know these four caching modes, dare you say you understand caching?
[Galaxy Kirin V10] [server] system partition expansion
From programmers to large-scale distributed architects, where are you (I)
Common system modules and file operations
Dictionaries and collections
Network connection (II) three handshakes, four waves, socket essence, packaging of network packets, TCP header, IP header, ACK confirmation, sliding window, results of network packets, working mode of