当前位置:网站首页>Safety testing aspects
Safety testing aspects
2022-07-04 10:49:00 【weixin_ thirty-four million three hundred and twenty-two thousa】
What are the three elements of information security ?
confidentiality (Confidentiality)、 integrity (Integrity) And usability (Availability) It is the three cornerstones of information security .
1) confidentiality : Ensure that information is not disclosed to unauthorized users .
2) integrity : Ensure that the message is transmitted from the real sender to the real recipient , It has not been added by illegal users in the process of transmission 、 Delete 、 Replacement, etc .
3) Usability : Ensure that authorized users can access data timely and reliably .
except CIA Outside , There are also some attributes that are required to be achieved , Such as controllability (Controllability) And non repudiation (Non-Repudiation). But the three elements of information security are confidentiality 、 Integrity and availability , Can't change
What is decompilation :
Computer software reverse engineering (Reverse engineering) Also known as computer software restore engineering , It refers to the target program through the software of others ( For example, executable programs ) Conduct “ Reverse analysis 、 Research ” Work , To deduce the ideas used by other people's software products 、 principle 、 structure 、 Algorithm 、 Treatment process 、 Design elements such as operation method , In some specific cases, the source code may be derived . Decompile as a reference when developing software , Or directly used in their own software products
Mobile decompiler :【APKTool】【jadx】
【APKTool】
apktool It's mainly used in reverse apk file . It can decode resources , And they can be rebuilt after modification . It can also perform some automated tasks , For example, build apk
apktool function :
1) Decode the resource into its original form ( Include resources.arsc,class.dex,9.png and xml)
2) Repackage the decoded resources into apk/jar
3) Organize and deal with projects that depend on framework resources APK
4)Smali debugging
5) Perform automated tasks
【jadx】
jadx It is a reverse APK File tool , Sometimes we need to analyze the mobile terminal penetration test personnel APK File source code to view APK The logic of the file and finding relevant sensitive information , And that's where we need to use it jadx decompile
The difference between penetration test and safety test :
1. Starting point difference
Penetration test -》 So the successful intrusion system , The starting point is to prove that the system has security problems 【 prove 】
Security testing -》 Therefore, it is not the starting point to find all possible security risks of the system 【 Find out 】
2. Visual differences
Penetration test -》 It is to look at and think about problems from the perspective of attackers
Security testing -》 It is to think from the perspective of guardians , Try to find all potential security risks that may be exploited by attackers , And guide them to repair
3. Coverage differences
Penetration test -》 Only select a few points as the test target
Security testing -》 It is a complete test after analyzing the system architecture and finding out all possible attack interfaces of the system
4. Cost differences
Penetration test -》 The investment of time and manpower is relatively small
Security testing -》 The function of the system is required 、 Analyze the technology adopted by the system and the architecture of the system , Need to invest more time and manpower
5. Solution differences
Penetration test -》 Unable to provide targeted solutions
Security testing -》 I will analyze the causes of problems from the perspective of developers , Provide more effective solutions
边栏推荐
- Article publishing experiment
- Evolution from monomer architecture to microservice architecture
- Using SA token to solve websocket handshake authentication
- [Galaxy Kirin V10] [server] KVM create Bridge
- Write a thread pool by hand, and take you to learn the implementation principle of ThreadPoolExecutor thread pool
- Fundamentals of database operation
- Latex arranges single column table pictures in double column format articles
- 183 sets of free resume templates to help everyone find a good job
- Dynamic memory management
- OSPF summary
猜你喜欢
Collection of practical string functions
20 minutes to learn what XML is_ XML learning notes_ What is an XML file_ Basic grammatical rules_ How to parse
XMIND installation
What is an excellent architect in my heart?
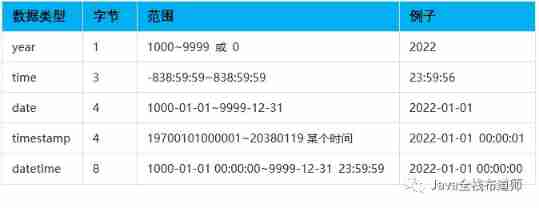
Basic data types of MySQL

TS type gymnastics: illustrating a complex advanced type
From programmers to large-scale distributed architects, where are you (2)
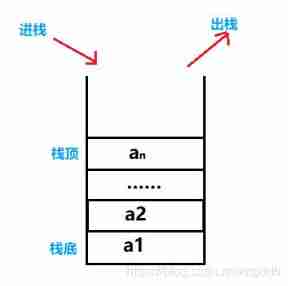
C language - stack
Personal thoughts on the development of game automation protocol testing tool
Unittest+airtest+beatiulreport combine the three to make a beautiful test report
随机推荐
Online troubleshooting
Dynamic memory management
Day06 list job
system design
[Galaxy Kirin V10] [desktop] cannot add printer
2、 Operators and branches
[Galaxy Kirin V10] [server] KVM create Bridge
Two way process republication + routing policy
Jemeter script recording
Aike AI frontier promotion (2.14)
MFC document view framework (relationship between classes)
Basic function exercises
OSPF summary
Quick sort (C language)
20 minutes to learn what XML is_ XML learning notes_ What is an XML file_ Basic grammatical rules_ How to parse
[Galaxy Kirin V10] [server] system startup failed
RHCE day 3
[Galaxy Kirin V10] [desktop and server] FRP intranet penetration
Talk about scalability
PHP programming language (1) - operators