当前位置:网站首页>Design and common methods of test case documents
Design and common methods of test case documents
2022-07-04 10:45:00 【A little boy who studies hard】
Principles for writing test case documents
- Of use cases Clarity
Clear description .
Result only . - Of use cases Representative
It can represent and cover all kinds of reasonable and unreasonable .
It can represent and cover all kinds of legal and illegal .
Can represent and cover all kinds of boundaries and cross-border . - The result of the use case Decidability
That is to say, the correctness of test execution results can be determined .
Each test case should have the corresponding expected results .
Black box test method
- Equivalence class division – Classify the test conditions :
Equivalence class division : Put all the possible input data , That is, the input field of the program is divided into several parts ( A subset of ) Equivalence class , Then select a few representative data from each subset / Equivalence classes as test cases .
It is mainly divided into effective equivalence classes ( positive , No mistake. ) Invalid equivalence class ( negative , Throw an error )
Case study : Wechat sends red envelope :0.01——200
analysis :
1: To test the function of normal transmission : Effective equivalence class :0.01-200
2: To test exception sending , Close to the user's use scenario : Invalid equivalence class :1、 Less than 0.01 2、 Greater than 200:0-200.01
The above is the equivalence classification
3: When there are too many tests , Choose the combined boundary value method : Exactly equal to / Greater than / Values less than the range , As test data
Tap hidden needs :
1: The red envelope amount must be a number
2: Red envelope input cannot exceed two decimal places
3: The red envelope amount cannot be blank
4: The red envelope amount cannot be negative and 0
The test case : Equivalent valid class
Use case design description Test data Cover equivalence class ( The main points of : Effective equivalence classes cover as many effective equivalence classes as possible with one use case )
The selection of invalid equivalence classes is opposite to that of valid equivalence classes ( A column covers only one )
Case summary : WeChat Lucky Money , Email registration
Boundary value analysis – Test for critical conditions ( This kind of method is often used in combination with the equivalence class division ):
The principle is to take values on the boundary of conditions or ranges , According to the specific situation , Take respectively equal to 、 a little bigger than 、 Slightly less than the condition or range value .
It's mainly : Two point method , Three point method , Four point method
Common boundary value situations :
The cursor is at the top left of the screen 、 The bottom right position ;
The first and last lines of the report ;( Two point method )
The first and last of the array elements ;( Two point method )
The second part of the cycle 0 Time , First and penultimate 2 Time 、 Count down for the first time ( Four point method )A false assumption – Based on empirical intuition, the calculation is wrong :
According to intuition or Experience Speculate on various errors that may exist in the program , Thus there are Write targeted test cases to check these errors .
Higher requirements for the ability of testers .
characteristic :
Highly subjective
Compared with the test set generated by other methods , Easier to find defectsCause and effect diagram – A combination of multiple test conditions :
Cause and effect diagrams are suitable for combinations with various input conditions , And there is a certain restrictive relationship between various conditions
The advantages of cause and effect diagram ∶
1. The combination of input conditions is fully considered , Sufficient coverage of the combination .2. Ultimately, each use case covers multiple input scenarios , It is helpful to improve the test efficiency .
3. During the design process , The constraints between input conditions are considered , Avoid invalid use cases , The effectiveness of use cases is high .
4. Be able to get the expected output of each test item at the same time
shortcoming ∶
1. When there are many inputs of the tested characteristics , The scale of the decision table will be very large .
2. The constraints between inputs cannot effectively distinguish whether the input really needs to be combined , It will cause the input that does not need combination test to be combined , Thus producing use case redundancy .Scene analysis – Design different scenarios according to business processes :
Scenario analysis is applicable to many process branches , The logic is more complicated , Conditions 、 There are many functional requirements under special circumstances .
You can use the flow chart to sort out the flow lines and test them one by one , If the development is not provided, you need to paint by yourself , If provided, it can generally be found in the requirements specification .Output domain coverage : Overwrite all outputs , Regardless of input
There are valid and invalid rules for visible parameters in the requirements interface , Unlimited input conditions , There are output constraints , We need to push the input backward from the output according to the business ,
1. Ask the developer or find out all the output results according to the code
2. Check whether the written test case covers all the output results , If there are test cases that are not covered, supplement the test cases
3. Backward deduce the test case steps and test data according to the output resultsInput domain coverage : Overwrite all inputs , Regardless of the output , Related to equivalent class boundary value method
Anomaly analysis : When testing, we must test the abnormal conditions ( Abnormal operation 、 Analyze the faults caused by software and hardware defects ), power failure , Abnormal condition of network disconnection , Design test cases based on this .
Mainly for testing the system Fault tolerance 、 Fault recovery capability To test .
Simply put, it means that the system breaks down artificially , Then check the fault recovery capability of the system .
On the other hand , Abnormal test for the system ( Did you do something you shouldn't do ) Also through anomaly analysis and other means .Exploratory testing : most , No requirements, no use cases , Information is not complete , Pit , Or test according to your own experience , Try to test the system function
State migration
Orthogonal experiment
Decision table
边栏推荐
- Latex insert picture, insert formula
- How to quickly parse XML documents through C (in fact, other languages also have corresponding interfaces or libraries to call)
- Using Lua to realize 99 multiplication table
- Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 1
- The future education examination system cannot answer questions, and there is no response after clicking on the options, and the answers will not be recorded
- Tables in the thesis of latex learning
- TS type gymnastics: illustrating a complex advanced type
- Write a program to judge whether the two arrays are equal, and then write a similar program to compare the two vectors.
- [testing theory] thinking about testing profession
- MFC document view framework (relationship between classes)
猜你喜欢
Use the data to tell you where is the most difficult province for the college entrance examination!
VI text editor and user rights management, group management and time management
Realsense of d435i, d435, d415, t265_ Matching and installation of viewer environment

Huge number multiplication (C language)
183 sets of free resume templates to help everyone find a good job
Si vous ne connaissez pas ces quatre modes de mise en cache, vous osez dire que vous connaissez la mise en cache?

BGP ---- border gateway routing protocol ----- basic experiment
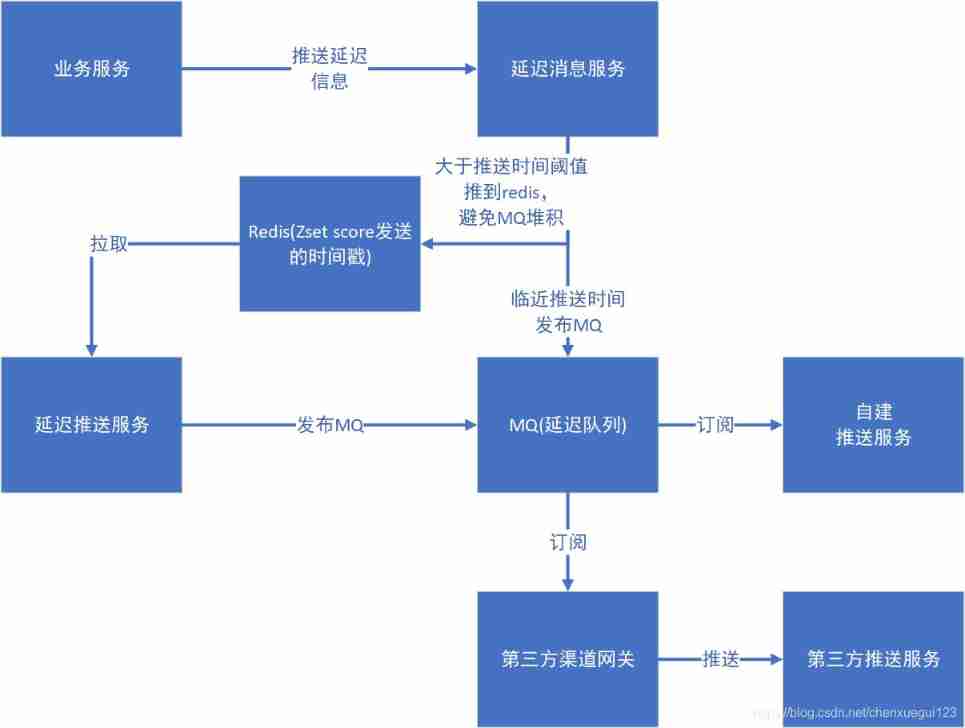
Delayed message center design
![[Galaxy Kirin V10] [server] set time synchronization of intranet server](/img/f8/0847314029930840c91bce97ccd961.jpg)
[Galaxy Kirin V10] [server] set time synchronization of intranet server

Article publishing experiment
随机推荐
[Galaxy Kirin V10] [desktop] cannot add printer
/*Rewrite the program, find the value of the element, and return the iterator 9.13: pointing to the found element. Make sure that the program works correctly when the element you are looking for does
Online troubleshooting
Student achievement management system (C language)
From programmers to large-scale distributed architects, where are you (2)
leetcode1-3
[Galaxy Kirin V10] [server] system startup failed
Reprint: summation formula of proportional series and its derivation process
MFC document view framework (relationship between classes)
Realsense d435 d435i d415 depth camera obtains RGB map, left and right infrared camera map, depth map and IMU data under ROS
[Galaxy Kirin V10] [server] KVM create Bridge
Rhsca day 11 operation
leetcode1229. Schedule the meeting
Leetcode48. Rotate image
Latex insert picture, insert formula
Seven examples to understand the storage rules of shaped data on each bit
Using SA token to solve websocket handshake authentication
DCL statement of MySQL Foundation
From programmers to large-scale distributed architects, where are you (I)
Snake (C language)