当前位置:网站首页>SSH principle and public key authentication
SSH principle and public key authentication
2022-07-04 11:02:00 【Brother Xing plays with the clouds】
Establishment process
ssh utilize rsa Asymmetry of encryption , Share a communication key that only the two of them know , Through this communication key , They will communicate later .
The client receives the public key of the server , Encrypt the communication key generated by yourself and send it to the server , The server decrypts with private key , At this time, the two use symmetric key communication ;
Key and algorithm negotiation phase
The specific steps are as follows :
(1)
The server The end and the client respectively send algorithm negotiation messages to the opposite end , The message contains a list of public key algorithms supported by itself 、 List of encryption algorithms 、MAC(Message Authentication Code, Message verification code ) Algorithm list 、 Compression algorithm list, etc .
(2)
The server The end-to-end and client-side can get the final algorithm according to the list of algorithms supported by the opposite end and the local end . Any algorithm negotiation fails , Will result in The server The algorithm negotiation process between the client and the client failed , The server Will disconnect from the client .
(3)
Server side and client side utilization DH In exchange for (Diffie-Hellman Exchange) Algorithm 、 Host key peer parameters , Generate session key and session ID, And complete the authentication of the client to the server .
Go through the above steps , The server and the client get the same session key and session ID. For subsequent data transmission , Both sides will use the session key for encryption and decryption , Ensure the safety of data transmission . conversation ID To identify a SSH Connect , At the certification stage , conversation ID It will also be used in the authentication process at both ends .
Authentication phase
SSH Two authentication methods are provided :
1 password authentication
utilize AAA(Authentication、Authorization、Accounting, authentication 、 Authorization and billing ) Authenticate the identity of the client . The client sends a message to the server password Authentication request , Encrypt the user name and password and send them to the server ; The server decrypts the information and gets the clear text of the user name and password , Verify the legitimacy of user name and password through local authentication or remote authentication , And return the message of authentication success or failure . If the remote authentication server requires the user to conduct password authentication twice , Then a prompt message will be carried in the authentication response message sent to the server , The prompt information is transmitted to the client through the server , Output by the client and ask the user to enter a specified type of password again , When the user submits the correct password and successfully passes the authentication of the authentication server , The server will return the message of successful authentication .
2 publickey authentication
Using digital signature to authenticate the client . at present , It's available on the device RSA and DSA Two public key algorithms realize digital signature . The client send contains the user name 、 Public key and public key algorithm publickey Authentication request to the server . The server checks the validity of the public key , If it's not legal , Then send the failure message directly ; otherwise , The server uses digital signature to authenticate the client , And return the message of authentication success or failure .
The second level is key based security authentication
You need to rely on the key , That is, you have to create a pair of keys for yourself , And put the public key on the server to be accessed . If you want to connect to SSH Server , The client software will make a request to the server , Request security verification with your key . After the server receives the request , First look for your public key in your home directory on this server , Then compare it with the public key you sent . If the two keys are the same , The server is encrypted with a public key “ inquiry ” And send it to the client software . Client software received “ inquiry ” Then you can decrypt it with your private key and send it to the server . In this way , You have to know the password of your key . however , Compared with the first level , The second level does not need to send passwords over the network . The second level not only encrypts all transmitted data , and “ A middleman ” This kind of attack is impossible ( Because he doesn't have your private key ). But the entire login process may require 10 second , But compared to the way you enter your password 10 Seconds is not long
ssh Public key authentication uses this feature . Each server and client has its own public key and key . For the sake of illustration , These symbols will be used below .
Ac Client public key
Bc Client key
As Server public key
Bs Server key
Before certification , The client needs to transfer the public key in some way Ac Log on to the server .
The certification process is divided into two steps :
1 session key (session key) Generate
The client requests to connect to the server , Server will As Send to client .
The server generates the session ID(session id), Set to p, Send to client .
The client generates the session key (session key), Set to q, And calculate r = p xor q.
The client will r use As To encrypt , The result is sent to the server .
The service is used Bs To decrypt , get r.
Server run r xor p Arithmetic , get q.
So far, both the server and the client know the session key q, Future transmissions will be q encryption .
2 authentication
The server generates random numbers x, And use Ac Generate results after encryption S(x), Send to client
Client side usage Bc Decrypt S(x) obtain x
Client computing q + x Of md5 value n(q+x),q For the session key obtained in the previous step
Server computing q + x Of md5 value m(q+x)
The client will n(q+x) Send to the server
Server comparison m(q+x) and n(q+x), If the two are the same, the authentication is successful
边栏推荐
- Write a program to define an array with 10 int elements, and take its position in the array as the initial value of each element.
- [advantages and disadvantages of outsourcing software development in 2022]
- /*Write a loop to output the elements of the list container in reverse order*/
- unit testing
- Hidden C2 tunnel -- use of icmpsh of ICMP
- [Galaxy Kirin V10] [desktop] login system flash back
- Function introduction of canbedded component
- VPS安装Virtualmin面板
- CAPL: on sysVar_ Update difference on sysvar
- [Galaxy Kirin V10] [server] FTP introduction and common scenario construction
猜你喜欢
![[Galaxy Kirin V10] [server] NFS setup](/img/ed/bd7f1a1e4924a615cb143a680a2ac7.jpg)
[Galaxy Kirin V10] [server] NFS setup

Huge number multiplication (C language)

TS type gymnastics: illustrating a complex advanced type
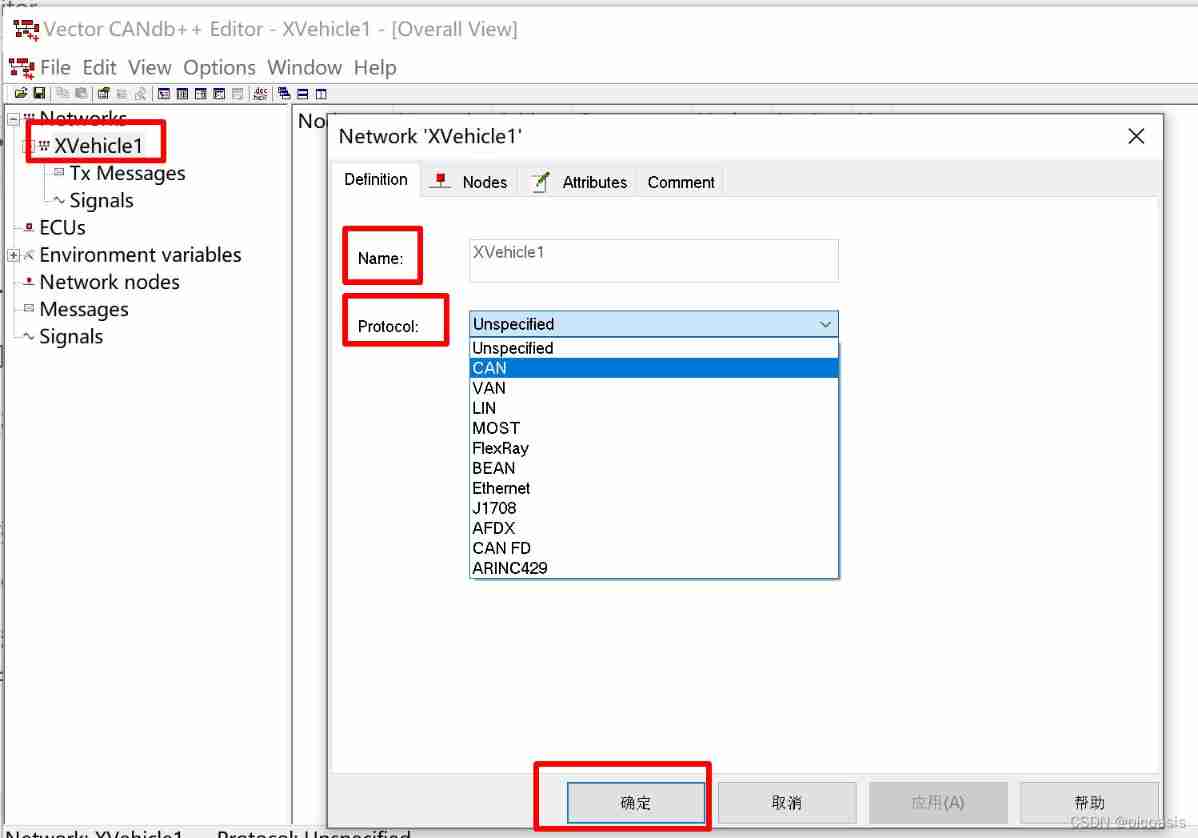
Canoe - the second simulation project -xvihicle1 bus database design (operation)
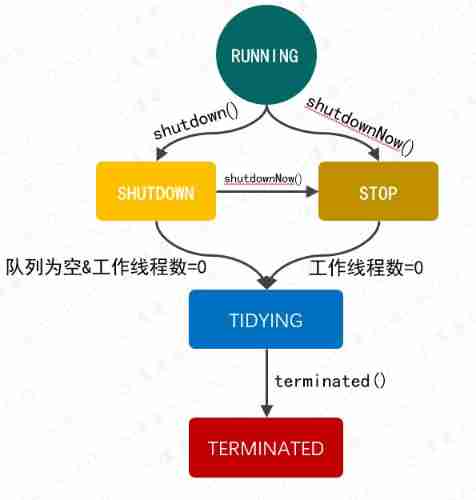
Write a thread pool by hand, and take you to learn the implementation principle of ThreadPoolExecutor thread pool
![[Galaxy Kirin V10] [desktop and server] FRP intranet penetration](/img/54/7d1b8b7b8226e2820635dd04b92d1c.jpg)
[Galaxy Kirin V10] [desktop and server] FRP intranet penetration
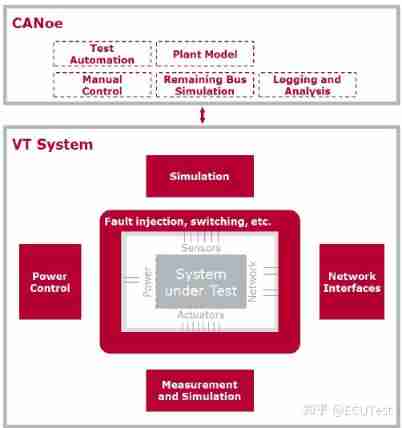
Canoe: what is vtsystem
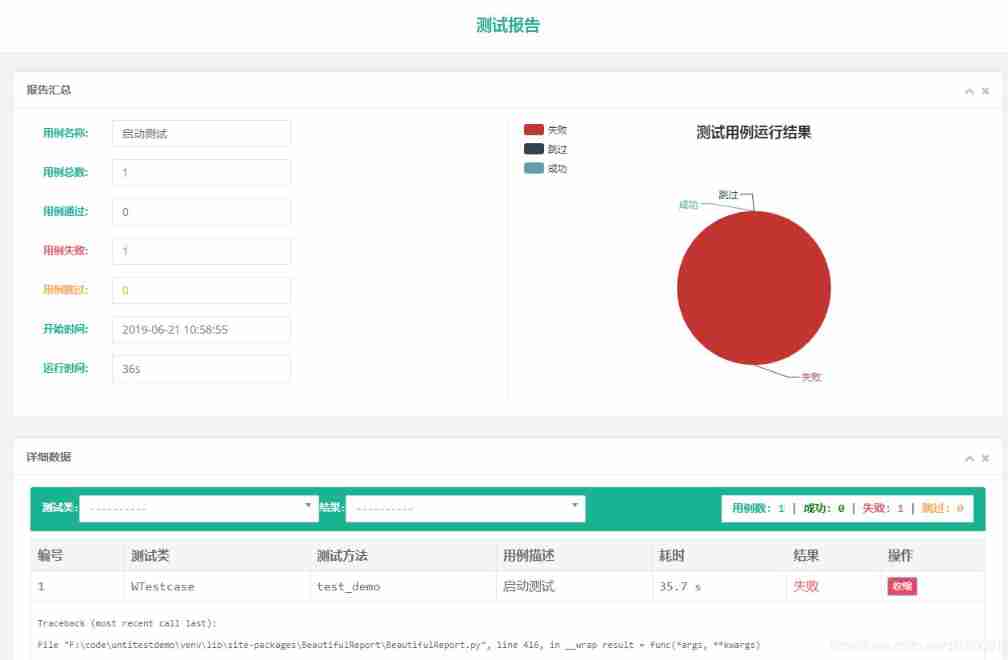
Unittest+airtest+beatiulreport combine the three to make a beautiful test report
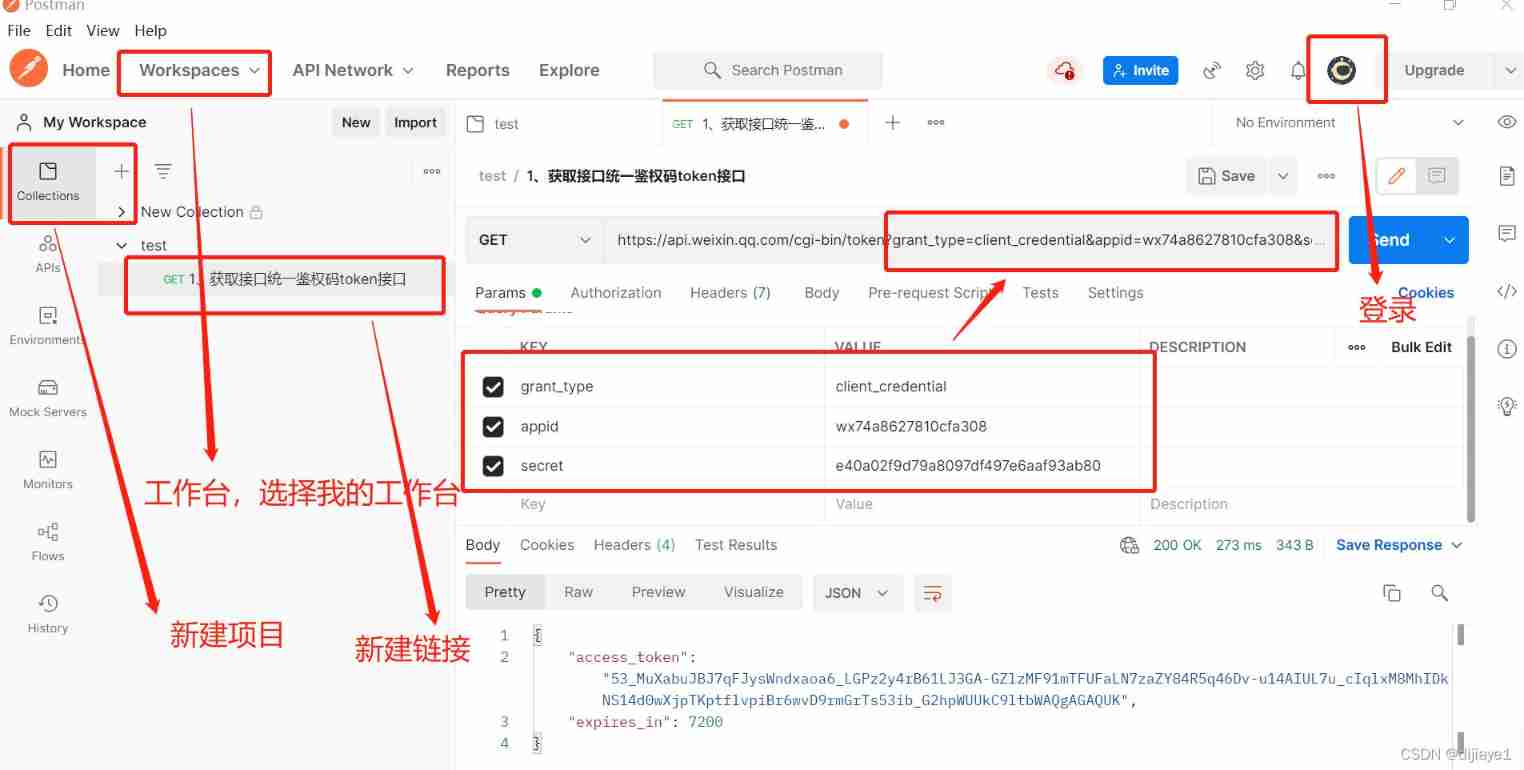
Postman interface test
Elevator dispatching (pairing project) ④
随机推荐
Canoe - description of common database attributes
Performance test method
Write a program that uses pointers to set all elements of an int array to 4.18: 0.
LVS+Keepalived实现四层负载及高可用
VPS安装Virtualmin面板
Aike AI frontier promotion (2.14)
Post man JSON script version conversion
Interview and lecture summary 1
Student achievement management system (C language)
Write a thread pool by hand, and take you to learn the implementation principle of ThreadPoolExecutor thread pool
Canoe-the second simulation project-xvehicle-1 bus database design (idea)
Performance test process
Usage of case when then else end statement
Design and common methods of test case documents
Locust learning record I
Canoe: what is vtsystem
If function in SQL
Failed to configure a DataSource: ‘url‘ attribute is not specified... Bug solution
[Galaxy Kirin V10] [server] soft RAID configuration
/*Write a function to open the file for input, read the contents of the file into the vector container of string class 8.9: type, and store each line as an element of the container object*/